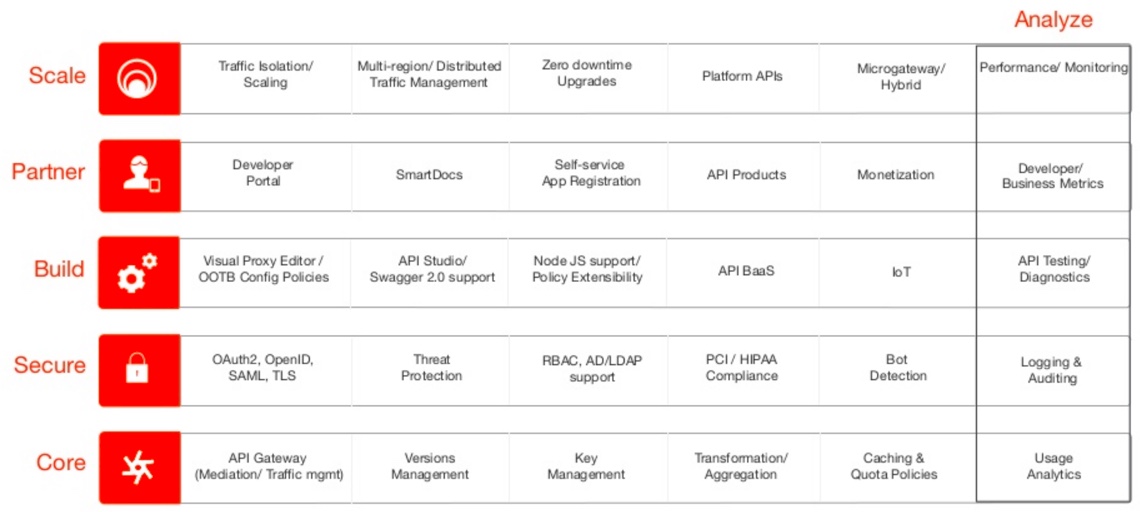
Design, Installation, configuration, Usage
Overview
This article is a hands-on tutorial on how to make use of Google’s Apigee Edge software to enable enterprises to manage and enable use of its APIs. What is unique about this article is the arrangement of information in a succinct way.
Sign up
-
Know what you will spend on each level of support purchased:
https://apigee.com/api-management/#/pricing
The minimal paid plan costs $500/month for a 3-member Team processing 15 million API calls per month.
-
Click “Create account” (if you don’t already have one) at:
https://login.apigee.com/sign__up
PROTIP: Although purchased as part of the Google Compute Platform in 2017, Apigee currently still operates with its own host name.
-
In your email, activate account.
Setup Shop
-
Sign in at https://login.apigee.com/login
The “Classic” console is:
https://enterprise.apigee.com/platform/
The page automatically displays Proxy Traffic and Developer Engagement.
-
If you already logged in, go to the Edge management UI at:

PROTIP: Investigate the menu bottom up: LEARN, ADMIN, then DESIGN, PUBLISH, ANALYZE.
PUBLISH refers to publishing on the public Developer Portal.
Analyze is different than “Offline Trace”.
-
Open a new browser window, preferrably on another monitor to see instuctions to create a Developer Portal by following this tutorial
The primary job of Apigee Edge is to expose backend REST services as APIs by being a proxy (a facade) to receive requests from API consumers (clients).
Out of the box Apigee Edge can auto-generate API Proxy code from a file formatted according to the OpenAPI specification, previously called “Swagger”. Apigee Edge also has an OpenAPI specification editor & store used to maintain OpenAPI specifications.
-
Select Develop → Specs in the side navigation menu
http://travelco-streetcarts.e2e.apigee.io
-
Add API Product to Portal
Why APIs
APIs expose the assets of a business for access by computers:
- Product catalogs
- Store listings
- Inventory
- Order status
- Social interaction
APIs are the public persona for an enterprise, a system of engagement with others. With new markets.
APIs are the currency of cloud and mobile.
Examples of companies that have monitized their low-friction APIs:
- developer.ticketmaster.com
- https://developer.shutterfly.com/
- https://developer.apple.com/
- https://developer.walgreens.com/
- https://developer.walmart.com/
- https://developers.hp.com/
- https://developers.google.com/ offers a Google Apps Script
- https://developer.viveport.com/console/
- OfficeMax, kinkos FedEx
https://www.youtube.com/watch?v=FPj_va9-rM8&t=0s&list=PLIXjuPlujxxxe3iTmLtgfIBgpMo7iD7fk&index=2
APIs are part of “Digital Transformation” seeking this “digital value chain”*

More precisely, the features and capabilities:
https://github.com/OAI/OpenAPI-Specification
Certification exam
Look into certification topics for a good overview of what one needs to learn in order to fully understand the offering, not just to provide proof of meeting Apigee’s proficiency standards by taking the Apigee Certified Professional - API Engineer (ACP) exam at https://academy.apigee.com/courses/certification
-
Study. Survey the exam topics. View the videos. Take the Coursera classes. Take the API Jam.
-
Create a new account at https://www.webassessor.com/wa.do?page=createAccount&branding=APIGEE
PROTIP: You must use another email if you already created another webassesor exam for Salesforce, ASQTB, etc.
-
Login at https://www.webassessor.com/wa.do?page=publicHome&branding=APIGEE
-
Go to Registration
-
If you prefer taking an online proctored exam at your home, enroll in their biometrics. Then on a laptop with a camera, download and install the Sentinal.pkg (43.6 MB)
-
When you’re ready, click Register for a new assessment to Buy Now. Notice same-day registration is possible for home exams.
-
Pay with a credit card charge of $200.
-
Write the “Test Taker Authorization Code” on a card in your wallet.
-
If you registered for an “onsite” exam proctored Kryterion Testing Center, take a test drive to make sure you know how to get there.
-
Start the test and answer at least 70% of 70 multiple-choice questions correctly over 2 hours.
A retake is allowed after 7 days but those who don’t pass a second time must wait one year before you can take it again.
Apigee Exam topics
A summary of the topics examined in the Certification Exam Guide:
- Section 1: Designing APIs
- Section 2: Developing, implementing and securing APIs
- Section 3: Development Lifecycle and CI/CD
- Section 4: Requirements and Business Analysis
New developements:
- gRPC
- GraphQL
- Hypermedia
Deploy the solution:
- Command Line Deployment
- User Interface Deployment
- Environment promotion and revisions
- Open API Specification 2.0 to capture API design
Best practices and API Documentation
Best practices and management of the API Lifecycle
API Design and Edge implementation best practices
Troubleshooting and debugging guidelines
Edge Policies:
- Proxy Configuration
- Error handling
- Shared Flows and Flow Hooks
- Encrypted KVM
Edge Microgateway:
- Out-of-the-box plugins
- Custom plugin development
Edge Node.js:
- Proxy Configuration
- Error handling
- Traffic Management
- Mediation
- API Programmability
Edge Analytics:
- Security Insights
- Monitoring and Logging
- Application Insights
- Usage Insights
API Jam Labs
A “API Jam” 2-hour live workshop for API developers event (on July 2018) references repo https://github.com/apigee/apijam
The repo does not contain code but images and step-by-step manual instructions in markup files which you need either a (Jekyll) program to display locally. So view them on-line rather than cloning locally. These Core topics:
https://github.com/rmistry75/devjam3/tree/master/Labs/VirtualAPIJam/Lab%202%20API%20Security%20-%20Securing%20APIs%20with%20API%20Keys
From the perspective of an administrator:
-
Lab 1 API Design - Create a Reverse Proxy with OpenAPI specification also covered in this video emailed after sign-up https://goo.gl/qGc4Gm
- Lab 2 Traffic Management - Throttle APIs https://goo.gl/TAkP3f
- Lab 3 API Diagnostics - Trace tool https://goo.gl/7a55Ho
From the perspective of a developer:
-
Lab 4 API Security - Securing APIs with API Keys https://goo.gl/VMGDpD
-
Lab 5 Traffic Management - Rate Limit APIs https://goo.gl/bqzpcn
StreetCarts is the reference API shown in the sample Developer Portal
https://github.com/mistry/devjam3
These cover the most critical evaluation criteria that companies should consider when selecting an API management platform. By the end of this workshop, you will walk away with practical hands-on experience using the Apigee Edge platform, along with an understanding of its comprehensive capabilities.
- API Development - Composite APIs
- API Development - Create a RESTful API from a SOAP service
- API Development - Create a Reverse Proxy
- API Development - Routing Rules
- API Development - Target Endpoints
- API Performance - Caching
- API Security - Securing APIs with OAuth -3-legged
- API Security - Securing APIs with OAuth-2-legged
- API Security - Threat Protection
- Apigee Edge Service Broker Org Plan- Secure a CF App
- Hybrid Deployment - Edge Microgateway
- Transformation - JSON-to-XML - HTTP header injection
https://github.com/sudheesreedhara/Iloveapis-apijam is also by Sudhee Sreedhara (@sudheendrabs, Google+). See his videos Overview of Apigee Edge Microgateway Configuration Jun 26, 2017 and Configuring Apigee Edge Microgateway Jun 21, 2017
Apigee Online Meetup: Stop thinking about APIs as technology
Why APIs are products, not one-off projects (webcast) by Brian Pagano says project thinking rewards doing the minimum, not the most customer focused. have an end-date. Not just about Operations.
The Business of APIs: Your 100-Day API Business Plan May 13, 2016 with slides by Bryan Kirschner
Client developer perspective
Developers who create client programs accessing an organization’s API use the Apigee Developer Portal to provide a “self service” web app for devs to understand the APIs which Apigee servers manage.
Different API products are separated by functionality so developers can choose:
- Payment
- Messaging
An API package is a collection of API products that are presented to developers as a bundle, and typically associated with a rate plan for monetization.
The web app provides documentation and sample code in an SDK (Software Development Kit) for a variety of programming languages used by client software.
https://docs.apigee.com/api-platform/samples/samples-reference
In client programming code, the address to which programs make requests is called a API resource path, a uniform resource identifier (URI) that identifies the network path to a given resource.
Developers use forms on the Developer Portal to sign-up to get tokens that are inserted into HTTP request headers sent by client programs. Tokens uniquely identify users, and is the basis for enforcing elements such as quota limits allowed the user each hour/day/week/month and specific level of access and functionality.
This and other characteristics of API behavior is what defines API products. An API product bundles resources, such as API proxies. An API product typically specifies a list of API proxies along with access limits, the API key approval method, and other configurations that should be in place for each of the bundle proxies.
Developer MicroGateway (MG)

Apigee’s MicroGateway (MG) extends Edge. It runs as a Node LTS proxy app to provide in-memory Spike Arrest and Quota management within internal clouds used by developers. MG also captures usage data for sending (asynchrously) to Apigee Edge for analytics. It’s configured using the edgemicro CLI shown in “Deep-Dive: Apigee Edge Microgateway” https://www.slideshare.net/apigee/webcast-deepdive-apigee-edge-microgateway by Prabhat Jha (@PrabhatJha), Director of Software Development
On-prem.
Apigee has integrations with AWS cloud.
License for on-prem. install
PROTIP: You may need to wait several hours or days, so let’s do this first.
-
Send an email to apply for a license.
-
Receive an email back with custom link such as:
https://eval.apigee.com/Customer?id=12345678950545B21030497AF386AF06
- Go to that URL
-
Click “I Accept” to the 30-day evaluation period of the “EOP4000 - Edge On-Premises Base” product.
PROTIP: After the 30 days, reapply using a different email address.
-
Make a folder to hold specification files that persists across reboots of your laptop/machine:
mkdir /tmp/apigee
-
Save the “license.txt” file containing keys emailed to you:
LICENSE_FILE="/tmp/apigee/license.txt"
- Specify that line in the Apigee Installation Response File described below.
Multi-region/data center

Clients are given an “endpoint” URI that goes through the public internet to a global load balancer. It’s needed because, to accomodate potentially massive load and for disaster recovery, an organization stands up several data centers running Apigee: at DC1 in one region and DC2 in another geographic region. The global load balancer distributes API traffic (requests) among different regions. For Sizing advice, see https://docs.apigee.com/private-cloud/v4.18.05/installation-requirements
Data in one region updates other regions so that fail-over to another region can occur anytime. This achieves “active-active” use of several gateway pods.
PROTIP: Once assigned, requests remain stuck in the same region.
Within each Gateway Pod, to ensure that the whole pod still functions when a single component fails, two or more instances of each component are instantiated and kept running.
PROTIP: In case of failure, each instance should have the capacity to handle all the traffic to its component.
Within each gateway pod, an internal load balancer distributes traffic among Routers (R) which receive traffic and route it to a Message Processors (MP).
Message Processors communicate with backend services (on services running outside the gateway pod). The Apigee Edge platform exposes backend services as secure, scalable APIs that developers will actually want to use. This is why Edge is called a “proxy”.
Message Processors persist data in local Cassandra NoSQL cache datastores. These are also called “Cassandra ring”.
Software in Cassandra coordinates data values among regions.
Now let’s look at additional services provided by Apigee.
Components created by Apigee are shown in blue and (open-source) components from elsewhere are shown in green.
Component Services

There are abbreviations for component services:

Ports in firewall
Before beginning installation within enterprises and in clouds, it is usually necessary to request network security rules be defined to permit use of certain ports.

Developer Portal
Developer Portal web app for developers stores its information in a PostgreSQL database.
The Developer Portal was built using Drupal.
OpenLDAP
Apigee Edge provides role based access control. Users, roles, and permissions are created and stored in an OpenLDAP service.
Management Server
The “Management Server” makes use of a Zookeeper server which monitors the health of servers, and brings services up and down to enforce specifications it has been given.
Enterprise Edge UI
The Enterprise UI” component provides web pages for internal use by system administrators and those who manage API products. This is also called “Edge UI” because it is the face of the Apigee Edge product.
API products are a key part of API management. Management of users and roles can be done through UI and management API.
API products allow delegation of API management to API product owners so that changes to products can be implemented without the intervention of API engineers or Operations.
During installation, a collection of default roles is created. Custom roles can be created for tailoring to specific security and management requirements.
Edge logical structures include organizations, environments, virtual host and target servers. Adding and removing physical components such as routers, message processors, etc. Adding a new regional data center.
Qpid Message Broker
The Qpid (pronounced “q-pid”) service is a broker that collects and filters data for analytics. It uses Apache Qpid to format and manage messages in AMQP (Advanced Message Queuing Protocol) which defines the binary (TLS encrypted) wire-level format of peer-to-peer asynchronous message exchange.
Package Monitization
“edge-mint” is the component that takes care of money transactions.
Rate plans define how much is charged for each API Product, free/premium period, setup fees, revenue sharing, transaction recording policies, etc.
https://docs.apigee.com/api-platform/monetization/basics-monetization has a Aug 9, 2017 [3:32] video. But it refers people to: https://docs-new.apigee.com/edge-monetize
Installation
Bootstrapping
Bootstrapping is the industry term for getting the basics prepared: downloading software from https://software.apigee.com, establishing the software repository, base utilities, etc.), prepare a host for customization during the profile setup process. Selection of Repository location (remote, local network, filesystem).
Bootstrap scripts are named with each version of Apigee Edge.
Apigee is built on RedHat and CentOS variants. So yum package manager is used (instead of apt-get) to install RPMs installed to folder: /opt/apigee. But symlinks can be used to relocate.
A JDK (Java) is installed.
Install Response Files
The same command is run on each node:
/opt/apigee/apigee-setup/bin/setup.sh -f /tmp/apigee/response-edge-txt -p ds
The sample response file in /tmp/apigee/response-edge-txt is:
HOSTIP="10.142.0.29" MSIP="10.142.0.29" ADMIN_EMAIL="opdk@google.com" APIGEE_ADMINPW="ILoveAPIs123" LICENSE_FILE="/tmp/apigee/license.txt" USE_LDAP_REMOTE_HOST="n" LDAP_TYPE="1" APIGEE_LDAPPW="ILoveAPIs123" ENABLE_AX="y" MP_POD="gateway" REGION="dc-1" USE_ZK_CLUSTER="y" ZK_HOSTS="10.142.0.29 10.142.0.24 10.142.0.28" ZK_CLIENT_HOSTS="10.142.0.29 10.142.0.24 10.142.0.28" USE_CASS_CLUSTER="y" CASS_HOSTS="10.142.0.29:1,1 10.142.0.24:1,1 10.142.0.28:1,1" USE_CASS_CLUSTERNAME="Apigee" CASS_AUTH="y" CASS_USERNAME="cassandra" CASS_PASSWORD="cassandra" PG_PWD="ILoveAPIs123" SKIP_SMTP="y" SMTPMAILFROM="noreply@apigee.com" BIND_ON_ALL_INTERFACES="y"
The sample ds file:
HOSTIP="$(hostname -i)" MSIP="$DC1IP1" ADMIN_EMAIL="<email@example.com>" APIGEE_ADMINPW="<password>" LICENSE_FILE="/tmp/apigee/license.txt" USE_LDAP_REMOTE_HOST="n" LDAP_TYPE="2" LDAP_SID="1" LDAP_PEER="$DC2IP1" APIGEE_LDAPPW="<password>" MP_POD="gateway" REGION="dc-1" ZK_HOSTS="$DC1IP2 $DC1IP3 $DC1IP4 $DC2IP2 $DC2IP3 $DC2IP4:observer" ZK_CLIENT_HOSTS="$DC1IP2 $DC1IP3 $DC1IP4" CASS_HOSTS="$DC1IP2:1,1 $DC1IP3:1,1 $DC1IP4:1,1 $DC2IP2:2,1 $DC2IP3:2,1 $DC2IP4:2,1" PG_MASTER="$DC1IP5" PG_STANDBY="$DC2IP5" PG_PWD="postgres" SKIP_SMTP="y" SMTPHOST="smtp.example.com" SMTPPORT="25" SMTPUSER="smtp@example.com" SMTPPASSWORD="<password>" SMTPSSL="n" BIND_ON_ALL_INTERFACES="y"
See https://docs.apigee.com/private-cloud/v4.18.05/install-edge-components-node#installedgecomponents
https://docs.apigee.com/private-cloud/v4.18.05/edge-configuration-file-reference
Installation Profiles
| Host | Profile | Installs Components |
|---|---|---|
| 1,2,3 | ds | Zookeeper and Cassandra |
| - | c | Cassandra only |
| - | zk | Zookeeper only |
| 1 | ms | Edge Management Server with Edge UI and OpenLDAP |
| - | ui | Edge UI only |
| - | ld | OpenLDAP only |
| 2,3 | rmp | Edge Router and Message Processor |
| - | r | Edge Router only |
| - | mp | Edge Message Processor only |
| 4,5 | sax | analytics (Qpid & Postgres) |
| - | qs | Qpid Server only |
| - | ps | Postgres Server only |
| - | dp | Developer Portal (Drupal) |
| - | pdb | Postgres database only for Developer Portal |
| - | mo | Monitization only |
| - | sa | Edge standalone (Cassandra, ZooKeeper, Management Server, OpenLDAP, Edge UI, Router, and Message Processor). This option omits the Edge analytics components: Qpid and Postgres) |
| - | aio | all components on a single node |
| - | edge | all Edge components except Edge UI: Management Server, Message Processor, Router, Qpid, Postgres |
| - | ? | Mail relay |
Configuration
PROTIP: A rule of thumb is to stand up one Router for every 4 Message Processors.
Org Provisioning
/opt/apigee/apigee-service/bin/apigee-service apigee-provision install
/opt/apigee/apigee-service/bin/apigee-service apigee-provision setup-org -f \ /tmp/apigee/response-org.txt
The sample response file:
ORG_NAME="apigee" ENV_NAME="prod" VHOST_PORT="9001" VHOST_NAME="default" VHOST_ALIAS="host2 host3" ORG_ADMIN="opdk@google.com" APIGEE_ADMINPW="ILoveAPIs123"
Developer Portal
The response file:
PG_HOST="10.142.0.25" PG_USER="apigee" PG_PWD="ILoveAPIs123" DEFAULT_DB="postgres" PG_NAME="devportal" DRUPAL_PG_USER="devportal" DRUPAL_PG_PASS="ILoveAPIs123" PHP_FPM_PORT="8888" SMTPHOST="localhost" SMTPPORT="25" SMTPUSER="" SMTPPASSWORD="" SMTPSSL="n" DEVPORTAL_ADMIN_FIRSTNAME="Apigee" DEVPORTAL_ADMIN_LASTNAME="OPDK" DEVPORTAL_ADMIN_USERNAME="opdk" DEVPORTAL_ADMIN_EMAIL="opdk@google.com" DEVPORTAL_ADMIN_PWD="ILoveAPIs123" EDGE_ORG="apigee" MGMT_URL="http://10.142.0.29:8080/v1" DEVADMIN_USER="opdk@google.com" DEVADMIN_PWD="ILoveAPIs123"
The sample PostgreSQL Response File:
HOSTIP="10.142.0.25" REGION="dc-1" PG_PWD="ILoveAPIs123"
TLS UUID Configuration
To configure TLS, open port 8082 to message processors from an Edge Router :
curl http://message_processor_ip:8082/v1/servers/self/uuid
This should return a UUID (Universal Unique Identifier) - a 128-bit number that distinctly identifies each object generated from a reference to a combination of the network address of the host, a precise timestamp, and a randomly generated component.
Associations between servers and pods are managed using UUIDs generated for each server during installation. UUIDs are later used to register the server to its gateway pod.
This needs to be tested between each router and message processor in the region.
Then:
- Disable local network restrictions in iptables and TCP wrappers.
- Files owned by user:group “apigee:apigee”.
Obfuscate passwords
In configuration files, rather than having plain text passwords, first obfuscate passwords using the Jetty .jar files installed with Edge:
java -cp \ /opt/apigee/edge-gateway/lib/thirdparty/jetty-http-8.0.4.v20111024.jar:/opt/apigee/edge-gateway/lib/thirdparty/jetty-util-8.0.4.v20111024.jar org.eclipse.jetty.http.security.Password TestMe
PROTIP: Make sure the version number “8.0.4” matches the installed version of Edge.
Sample output: <pre> TestMe OBF:1ppq1od31yta1ytc1obr1pqo MD5:2c539f7b23fc3fb3b8ec52d3bfa58834</pre>
Keystore
Create the keystore using the private key for the server and an appropriate certificate: Copy the keystore to a location accessible by the Apigee user, e.g.
cp message_processor_keystore.jks /opt/apigee/customer/application/mp_keystore.jks
Secure the keystore by changing ownership to user:group:
chown apigee:apigee /opt/apigee/customer/application/mp_keystore.jks chmod 600 !$
TLS Security
Two-way Transport Layer Security (TLS) has both client and server authenticating each other.
-
Create somewhere to store private keys (within your own account?):
mkdir -p ~/certs/servers/tlsdemo.apigee-training.google.com chmod 700 -R ~/certs
-
Create and secure the key:
openssl genrsa -out "certs/servers/tlsdemo.apigee-training.google.com/private.pem" 2048 chmod 600 -R certs/servers/tlsdemo.apigee-training.google.com/private.pem
For a machine serving request for https://tlsdemo.apigee-training.google.com a signed, trusted certificate is required.
To request a signed certificate, create a request using the openssl tool and the private key for the server:
openssl req -new -key certs/servers/certdemo.yourdomain.xyz/private.pem -out certs/tmp/tlsdemo.apigee-training.google.com.csr.pem -subj "/C=AU/ST=NSW/L=Sydney/O=Cert Demo/CN=tlsdemo.apigee-training.google.com"
This creates a CSR (Certificate Signing Request) that is used to request your public certificate.
If you have a certificate and a private key, you can check they match by viewing the modulus - this should be the same for both the key and the certificate:
openssl rsa -noout -modulus -in private.key | openssl md5 openssl x509 -noout -modulus -in server.cert | openssl md5
-
Create a Java keystore. PROTIP: When creating a keystore, it is good practice to create it with an alias to make it easy to identify:
openssl pkcs12 -export -clcerts -in certs/signed/tlsdemo.apigee-training.google.com.cert.pem -inkey certs/servers/tlsdemo.apigee-training.google.com/private.pem -out /tmp/prodapi_keystore.pkcs12 -name prodapi
-
Convert to JKS format using the Java keytool utility to :
keytool -importkeystore -srckeystore /tmp/prodapi_keystore.pkcs12 -srcstoretype pkcs12 -destkeystore /tmp/prodapi_keystore.jks -deststoretype jks -alias prodapi
Create private keys, certificates, and keystores ● Configuring TLS on a Router ● Configuring TLS on a Message Processor ● Configuring TLS on a Management Server ● Configuring TLS on Enterprise UI
Message Processor
Configure the Message Processor to use TLS by appending to file:
/opt/apigee/customer/application/message-processor.properties
After completing the change on all message processors, restart all routers and message processors.
Validation Steps
/opt/apigee/apigee-service/bin/apigee-service apigee-validate install /opt/apigee/apigee-service/bin/apigee-service apigee-validate setup /opt/apigee/apigee-service/bin/apigee-service apigee-validate setup -f <response> /opt/apigee/apigee-service/bin/apigee-service apigee-validate clean /opt/apigee/apigee-service/bin/apigee-service apigee-validate clean -f <response>
API Proxy Config
The Apigee Edge server is a proxy server.
API behavior is modeled by Policy modules that control security, mediation, transformation, enrichment, among many other function as part of the proxy request/response flow.
An API proxy configuration describes the request and response flow for a given API Model. Policies are attached to these flows. A policy allows you to intercept the flow and inject specific functionality. Apigee Edge offers many out of the box and extension policies, these can be used in the request and response flows.
In Apigee, an API proxy is defined by a bundle of XML configuration files, Javascript files, and other resources. They describe the request and response cycle for the API.
Typical policy-based functionality includes transforming message formats, enforcing access control, calling remote services for additional information, masking sensitive data from external users, examining message content for potential threats, caching common responses to improve performance, and so on.
Policies are executed conditionally based on the content or context of a request or response message. For example, a transformation policy may be executed to customize a response format if the request message was sent from a smartphone.
Virtual hosts are similar to Apache Virtual hosts. They route traffic to environments based on ports and domain names.
TargetServer configurations decouple concrete endpoint URLs from TargetEndpoint configurations. Each TargetServer is referenced by name in a TargetEndpoint HTTPConnection. Instead of defining concrete URL in the configuration, you can configure one or more named TargetServers.
Multitenancy

With Edge, a planet is a single hardware installation for a single purpose. There are usually separate planets for production and non-prod. Planets can span multiple data centers. Organizations can span a planet. Planets can also contain multiple organizations and organizations, in the case of edge, represent tenants.
The hardware, virtual machines or cloud instances in a given Apigee installation is called a “planet”, a collection of resources across one or more regions (data center cloud regions).
Organizations = tenants, logical boundaries to enforce logical data partitioning and security - key to Apigee Edge multi tendency, where several organizations co-exist separately on the same physical infrastructure.
Organizations are created as part of the onboarding process following a successful installation. This process is part of Edge’s automation capabilities and is used to provision all the elements that make up a fully functional organization.
Within each given organization are environments – working spaces mapped to an API SDLC such as dev, QA, prod, PoC, etc. The entry point to an environment are one or more Virtual hosts associated with domain names and ports.
Because organizations and environments span across all regions, executing actions in a single location influences the behavior of APIs across multiple regions. For example, deploying an API to environment A1 in region three, will deploy the API to A1 in regions one and two as well. This enables management of a distributed infrastructure from a centralized point.
Each API is owned by one organization. Two organizations share nothing. APIs, API keys and other items within a given organization, are not visible from others. Having two or more organizations in production, implies that API consumers looking to use organization A APIs and organization B APIs, will require two sets of API keys.
Each organization can also contain multiple environments. Organizations and environments represent strong conceptual boundaries. These boundaries allow for strong data, and in some cases, processing partitioning. When we come to name organizations, there are a number of rules that should be followed. With a single planets, you cannot create multiple organizations with the same name. An attempt to do so will result in the second organization failing to be created. Organization names should only be lowercase, spaces, underscores, periods, and special characters are not allowed. Dashes join multiple words.
Pods, Regions, Servers
Pods are grouped into regions of geographically separate data centers.
Pods logically group servers by function for configuration and management. The functions:
– API processing: Router, Message Processor – System management: Management Server, Enterprise UI – Service management: Postgres Server, Qpid Server.
Each server is registered with the management server at install time, when they each obtain a UUID for reference.
Registration is the setup step that adds a server to the system and describes what functions the server offers to other components. Examples: management-server, user-settings-datastore, etc.
Autostart
This only is needed once to automatically start Apigee when the host reboots:
/opt/apigee/apigee-service/bin/apigee-service enable_autostart
To disable again:
/opt/apigee/apigee-service/bin/apigee-service disable_autostart
Maintenance
Cassandra
Use chron to schedule this once per week.
PROTIP: Run maintenance work one host at a time to avoid overload.
/opt/apigee/apigee-cassandra/bin/nodetool repair /opt/apigee/apigee-cassandra/bin/nodetool repair -pr
PostgreSQL Purge
This job retains 90 days
/opt/apigee/apigee-service/bin/apigee-service apigee-postgresql pg-data-purge apigee prod 90
Upgrade Apigee
Apigee aims for 3 releases a year, every 4 months. Releases are named by month number, as in 4.18.01, 4.18.05, 4.18.09 Each release is patched for one year. So Apigee expects customers to have several versions going at the same time.
- Ensure that backups are available and tested in case rollback is not an option
- VM snapshots are a great insurance policy
- Software distribution is identical to installation
- Local mirrors or tarballs must be updated
- Upgrade process will upgrade all open source and Apigee components
- Root access is required
- Configuration settings in /opt/apigee/customer are retained
- Cassandra maintenance jobs should be temporarily disabled if appropriate
Uninstall
/opt/apigee/apigee-service/bin/apigee-service <component> uninstall /opt/apigee/apigee-service/bin/apigee-all stop yum -y remove 'apigee-*' 'edge-*' rm -rf /opt/apigee /opt/nginx userdel -rf apigee
Learning resources
https://apigee.com/about/developers
https://community.apigee.com/index.html
https://www.slideshare.net/apigee/
mailto: apigee-sales@google.com
stackoverflow.com
Videos
Apigee Demo: API Platform Overview by Keith Danekind
Apigee API Management Trial videos, all Apr 25, 2018 by Dino Chiesa, Product Manager
-
Welcome [2:25]
-
Creating Your First Proxy [4:51]
-
Adding API Key Verification [3:58]
-
Using Apigee Trace [3:17]
-
Publishing APIs [3:43]
-
API Analytics [3:51]
-
Life After Trial [1:39]
Apigee has created on YouTube 153 4-minute videos which are mostly high-level pitching the value of APIs.
As part of the Google Cloud Program, Apigee gets to talk at Google conferences such as Cloud Next ‘17:
-
Using Apigee Edge to create and publish APIs that developers love Mar 9, 2017 [54:16] by Greg Brail, Prithpal Bhogill, and Adam Brancato
-
Manage the full API lifecycle with Apigee Edge API platform [57:17]
Ebooks
https://docs-new.apigee.com/docs
https://docs.apigee.com
ebooks at https://apigee.com/api-management/#/resources
https://apigee.com/about/support/portal
Coursera video courses
Install and Manage Google Cloud’s Apigee API Platform Specialization
-
On Premises Installation and Fundamentals with Google Cloud’s Apigee API Platform
-
On Premises Management, Security, and Upgrade with Google Cloud’s Apigee API Platform
-
On Premises Capacity Upgrade and Monitoring with Google Cloud’s Apigee API Platform
Developing APIs with Google Cloud’s Apigee API Platform Specialization Develop APIs with the Apigee API Platform. Learn about the fundamentals of developing and securing APIs using the Google Cloud Platform
-
https://www.coursera.org/learn/api-design-apigee-gcp”> API Design and Fundamentals of Google Cloud’s Apigee API Platform</a>
https://www.coursera.org/learn/onprem-upgrade-apigee-gcp/lecture/WOydC/create-and-delete-organization
https://www.coursera.org/learn/onprem-fundamentals-apigee-gcp/lecture/pKI4a/product-overview
Conferences
I Love APIs
- https://apigee.com/about/blog/api-technology/microservices-amazon Microservices at Amazon 2015
More
Apigee competes with WSO2 API Manager 2.5.0, which introduces a new language for creating and deploying microservices on a gateway, regardless of the use of the API Manager and/or the Enterprise Integrator. It replaces enterprise service bus technology Synapse and AXIS2 which uses XML/SOAP. Ballerina is open sourced. It is accompanied by Docerina and Testerina which automates documentation and unit testing. Ballarina connects to cloud-based services like Twitter using connectors which others can add to the Ballerina Central website. It’s more towards the Cloud based / connected Microservices than the Micro Services Framework for Java (MSF4J)’s computational approach.
TODO: APIs DevOps