How to to protect IT assets by mitigating attacker TTPs defined in Mitre’s ATT&CK
Overview
Mitre (a non-profit research lab funded by the US government) defined their Mitre ATT&CK to present – for each stage in a typical “kill chain” – the TTPs (Tactics + Techniques + Procedures) adversaries use to attack computer systems. Use it to analyze the kill chain adversaries could possibly use to get in, do damage, and cover their tracks. All to prevent that in the future.
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
Mouse over each TTP for a T number referencing the Procedures, Assets, Mitigations, and Detection within each variation of Mitre’s original ATT&ACK framework:
-
The ATT&CK Navigator v2 at https://mitre-attack.github.io/attack-navigator/v2/enterprise/ is a web-based tool for annotating and exploring ATT&CK matrices. It can be used to visualize defensive coverage, red/blue team planning, the frequency of detected techniques, etc
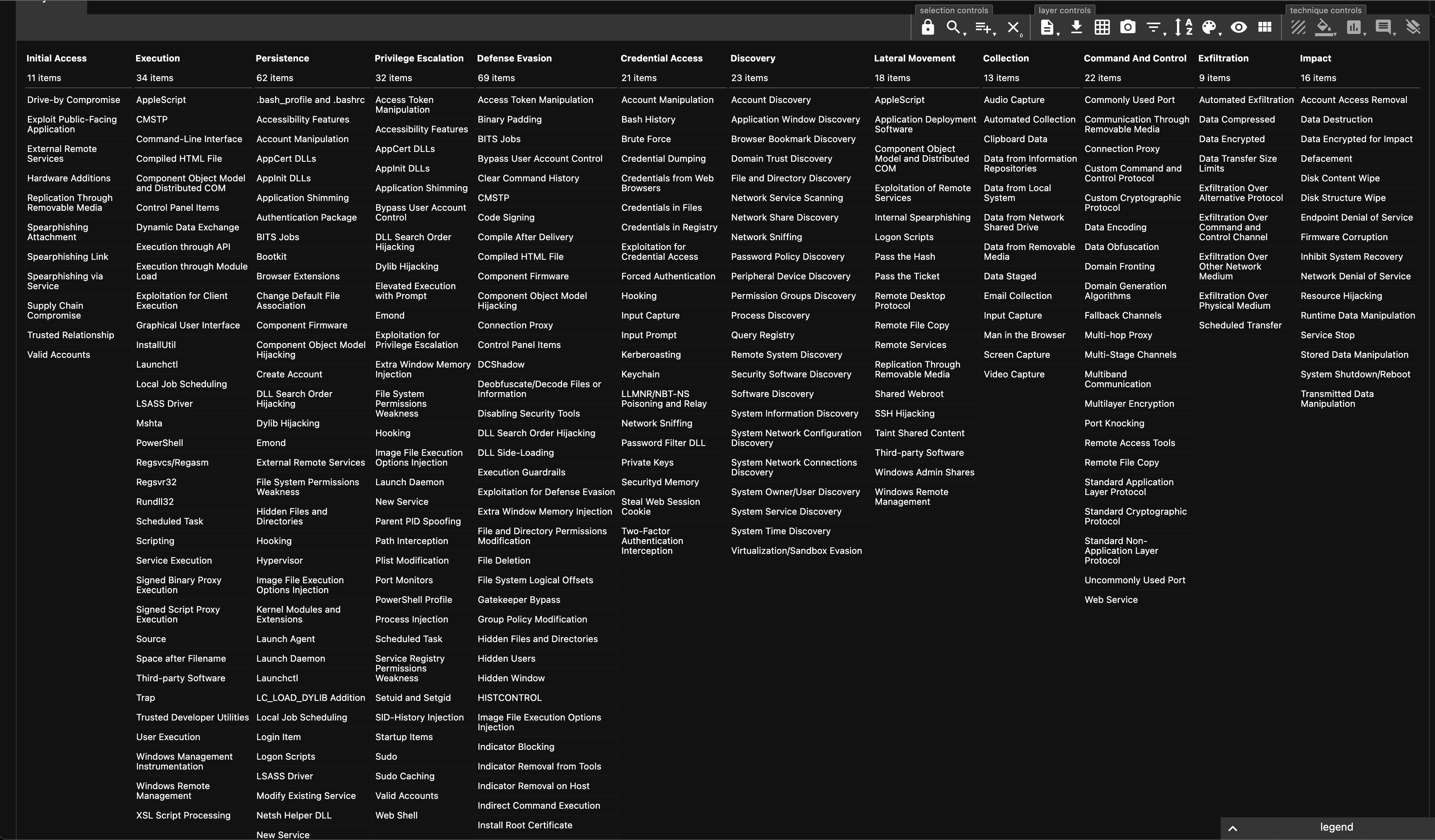
https://mitre-attack.github.io/attack-navigator/v2/enterprise/”>
- Above generated from https://mitre-attack.github.io/attack-navigator
- VIDEO: Introduction
NOTE: “Reconnaissance” and “Resource Development” stages are not evaluated because it’s difficult to collect information about them.
-
https://atlas.mitre.org adds columns for AI & ML (Machine Learning).
- PROTIP: Mitigations
- VIDEO: Intro
- Dr. Christina Liaghati explains the MLSecOps needed to harden against the TTPs
- AI Threats & Vulnerabilities
- SANS AI Security Trends by Kirk Trychel
-
https://attack.mitre.org/tactics/enterprise provides specific TTPs for each operating system. This is for ICS (Industrial Control Systems):
-
Dragos.com, a MSPP specializing in OT (Operational Technologies) used by Industrial Control System (ICS), modified the framework for OT:
-
Users of Exabeam shows a dashboard containing a Threat count for each stage:
Attack Tactics
- Reconnaissance
-
Resource Development
- Initial Access
- ML Model Access (not in standard & Dragos)
- Execution
- Persistence (not in Dragos)
- Privilege Escalation
-
Defense Evasion
- Credential Access (not in Dragos)
- Discovery
- Lateral Movement (not in ML)
- Collection
-
Command and Control or ML Attack Staging or “Inhibit Response Function” in Dragos
- Exfiltration (or Impair Process Control in Dragos)
- Impact
Alphabetical order
12) Collection
13) Command And Control
9) Credential Access
8) Defense Evasion
10) Discovery
5) Execution
14) Exfiltration
15) Impact
3) Initial Access
11) Lateral Movement
6) Persistence
7) Privilege Escalation
1) Reconnaissance
SLSA Threats
The SLSA (Supply chain Levels for Software Artifacts) standards and controls (from Googlers) define how to build secure resilient software using a secure supply chain. Its aim is to stop tampering such as this series of threats:
Each threat is addressed by controls defined in my list of actions to secure the software supply chain grouped along three “tracks” (aspects) of threats in the supply chain:
- Source code threats -> Check Expectations
- Build threats -> Check Dependencies
- Dependency threats -> Check SLSA Build level
NIST AI RMF
The NIST AI Risk Management Framework (AI RMF 1.0) and companion Playbook at https://www.nist.gov/itl.ai-risk-management-framework focuses on these requirements:
- Valid & Reliable
- Safe
- Secure & resilient
- Explainable & Interpretable
- Privacy-Enhanced
- Fair: With Harmful Bias managed
- Accountable & Transparent
OWASP
The OWASP Top 10 for LLM at https://owasp.org/www-project-top-10-for-large-language-model-applications
- https://llmtop10.com/
- https://www.youtube.com/watch?v=cYuesqIKf9A by IBM
- https://www.youtube.com/watch?v=J1auLaU9SAA OWASP Cincinnati meetup fea. Steve Wilson of Contrast Sec.
- https://snyk.io/blog/addressing-risks-in-the-owasp-top-10-for-llms/
Questions
TODO: Add based on each stage in the kill chain:
- Initial Access vector – How did the attacker get in?
- How is the adversary accessing the environment?
- How did the attacker move laterally? (RDP, SSH, network shares, malware, etc.)
- How is the adversary maintaining control persistence? (How are they staying in?)
- How is the attacker communicating with the C2 (Command and Control) server?
- What is the method of persistence (malware backdoor, webshell, legitimate credentials, remote tools, etc.)?
- What is the attacker doing on the system? (What commands are they running?)
- Has data been exfiltrated and if so, what kind of data and via what mechanism?
Microsoft
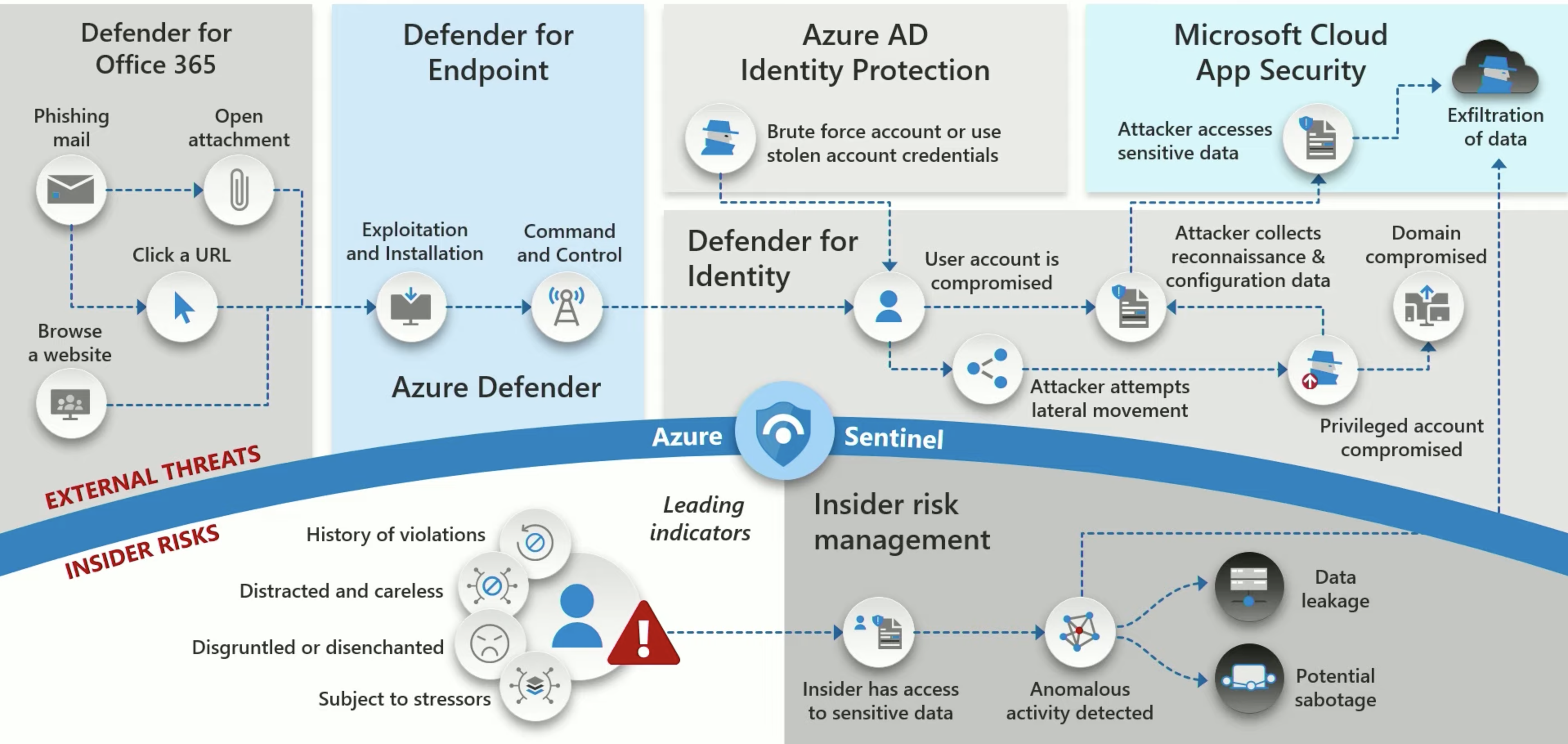
VIDEO: Mark Simos and Ken Malcolmson explain Microsoft’s view of the cyber attack chain:
They show Microsoft’s how product addresses major TTPs.
It’s part of the Microsoft Reference Architecture
- Azure Defender for Endpoint
- Azure Defender for Identity
- Azure Entra (AD) Identity Protection
- Microsoft’s Azure Defender for Cloud
- Azure Sentinel or insider threats
John Flores (MicrosoftGuyJFlo) wrote the Entra and Security docs at Microsoft.
Resources
https://github.com/deanbushmiller/ATTACK/blob/main/Layers-for-navigator/ATTACK-Layers-in-Navigator.pdf