How our Security Operations Center (SOC) detects and responds to security threats using software for SIEM (Security Information and Event Management) and SOAR (Security Orchestration, Automation, and Response).
Overview
This article is phrased as descriptions for presentation to auditors..
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
Industry terms
Gartner’s Hype Cycle for Monitoring, Observability and Cloud Operations, 2022 PDF:
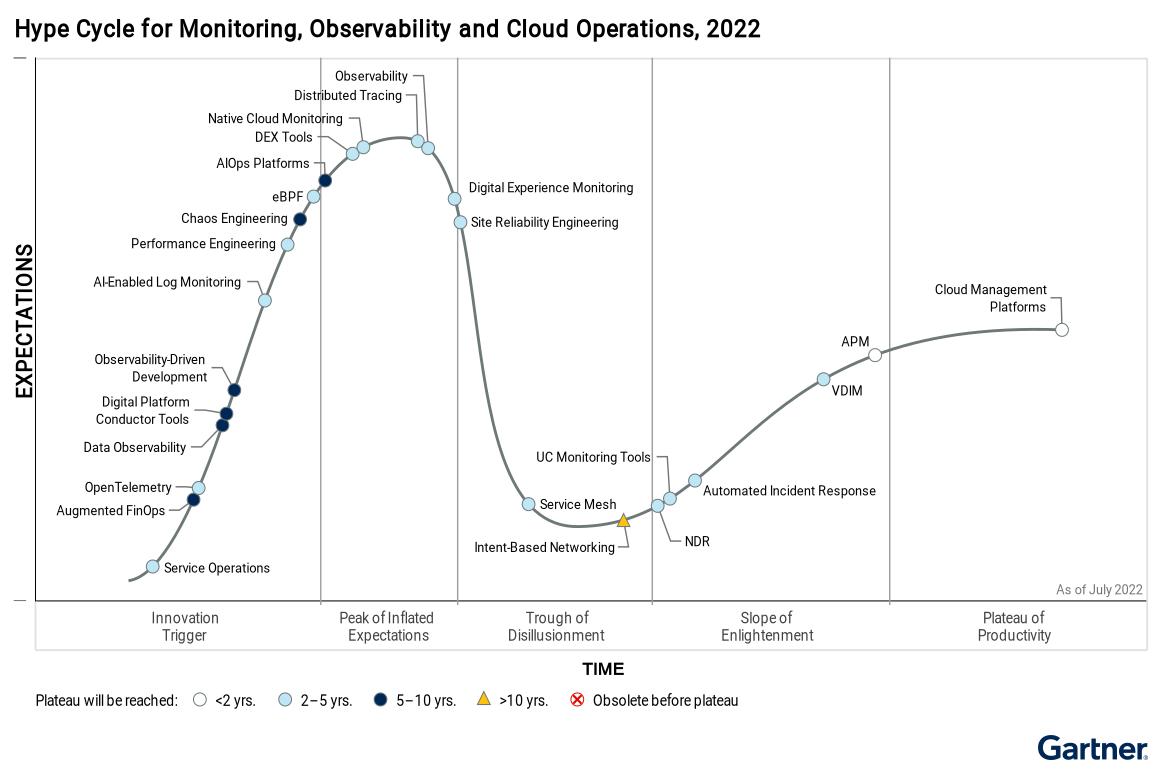
APM (Application Performance Monitoring) is a superset of RUM (Real User Monitoring), to monitor and troubleshoot performance issues in web applications.
RUM (Real User Monitoring) is a subset of APM (Application Performance Monitoring), to monitor and troubleshoot performance issues in web applications.
eBPF (extended Berkeley Packet Filter) is a subset of APM (Application Performance Monitoring), to monitor and troubleshoot performance issues in Linux and Windows applications.
VDIM (Virtual Desktop Infrastructure Monitoring) is a subset of APM (Application Performance Monitoring), to monitor and troubleshoot performance issues in virtual desktops.
EDR (Endpoint Detection and Response) is a subset of a EPP (Endpoint Protection Platform), which detect and automatically remediate attacks on endpoints. It’s a quality log source for SIEM. EDR protects against malware threats with “behaviral” protection that’s than signature-based anti-virus.
DEX (Data Exfiltration) is a subset of EDR (Endpoint Detection and Response), to detect and respond to data exfiltration.
NDR (Network Detection and Response) is a superset of EDR, to also detect and respond to network security incidents.
XDR (eXtended Detection and Response) is a superset of EPP and EDR, to also ingest, detect, and respond to network, email, and cloud security (any assset) with “advanced” threat detection and response.
- MDR (Managed Detection and Response) is a superset of XDR, to also provide 24/7/365 monitoring and response to security incidents, to provide guided response to 3rd-party human investigators. It automates alerts, prioritizing them through automation to rule out false positives, to escalate only the most critical alerts to the MDR team for investigation and remediation.
It also provides assistance in cleanup to bring conditions back to pre-attack state.
Security, Orchestration, Automation and Response (SOAR)
SIEM Vendors
 From Gartner
From Gartner
Exabeam was the first to incorporate AI.
- https://grafana.com/success/exabeam/
Splunk offers both a cloud and full on-prem solution which Gartner rates among leaders in the space. Splunk supports security monitoring and can provide advanced threat detection capabilities.
- https://www.splunk.com/en_us/data-insider/what-is-siem.html
- https://wilsonmar.github.io/splunk
IBM QRadar can be deployed as a hardware appliance, a virtual appliance, or a software appliance. [Course]
LogRhythm is used by smaller organizations.
Securonix
Rapid7
Dell Technologies (RSA)
Microsoft Azure Sentinel
Sumo Logic
Elastic
Hewlett Packard Enterprise
Fireeye
- https://www.fireeye.com/products/helix/what-is-siem-and-how-does-it-work.html
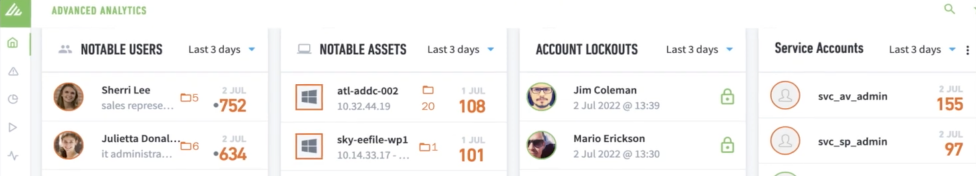
Exabeam Workflows
Exabeam uses its AI engine to identify “notable” High Risk Users and assets meeting threat profiles.
See this white paper.
Content library of log data source integrations and security use cases:
- https://github.com/ExabeamLabs/Content-Library-CIM1
- https://github.com/ExabeamLabs/Content-Library-CIM2
Sigma Logs Analytics
What Snort is to network traffic, and YARA to files, is Sigma to logs. https://isc.sans.edu/forums/diary/Sigma+rules+The+generic+signature+format+for+SIEM+systems/26258/
https://github.com/SigmaHQ/sigma enables Generic Signature Format for SIEM Systems
https://www.securonix.com/blog/sigma-community-driven-approach-to-stop-cyber-threats/ YAML files.
https://socprime.com/blog/sigma-rules-guide-for-arcsight/
- Sigma → ArcSight
- ArcSight → Sigma → Splunk
- Splunk → Sigma → ArcSight
- QRadar → Sigma → ArcSight
FOSS for SOC
VIDEO: Build a SOC ecosystem using only SIEMonster: Open Source SIEM
- ELK (Elasticsearch, Logstash, Kibana)
- For Case Management: TheHive VIDEO, DOCS
- To collect copies of digital evidence in a forensically sound way: $2,900 FTK (Forensic ToolKit) from Exterro to copy from Windows & macOS computers, smartphones, and tablets. It can also analyze data from cloud storage and social media. FTK creates copies in a forensically sound way, so it’s used by law enforcement, military, and intelligence agencies.
Threat Intelligence Feeds
VirusTotal from Google.
Cortex-<a target=”_blank” href=”https://github.com/MISP/MISP</a> VIDEO Intro
Commercial sources with integration to MISP include
- Broadcom (previously Symantec’s) DeepSight Intelligence,
- Kaspersky threat feeds, and
- McAfee Active Response.
MISP integrations with open-source and commercial threat intelligence platforms include
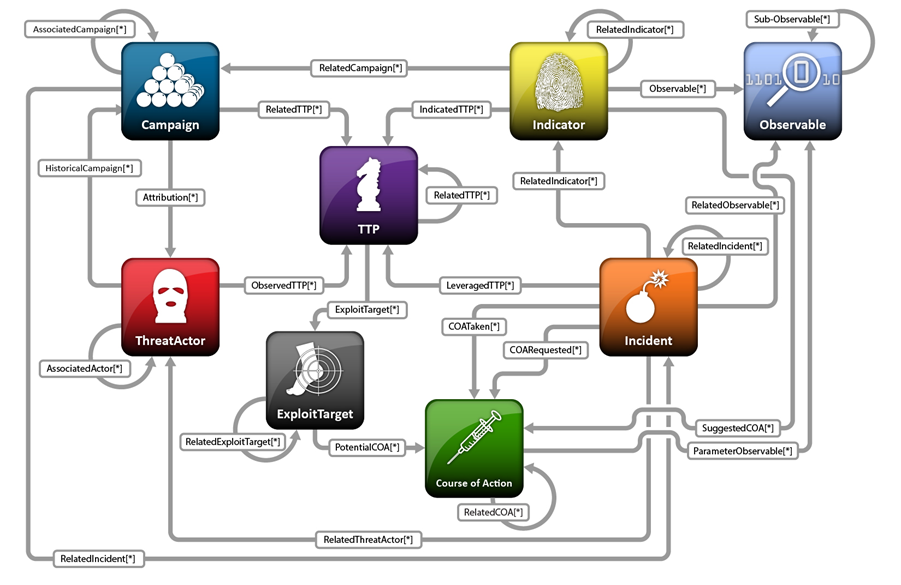
STIX (Structured Threat Information Expression) is a language and serialization format used to exchange cyber threat intelligence (CTI). STIX enables organizations to share CTI with one another in a consistent and machine-readable manner, allowing security communities to better understand what computer-based attacks they are most likely to see and to anticipate and/or respond to those attacks faster and more effectively.
VIDEO: Threat Hunting Tutorials
- wazuh.com
- HBIDS
Questions
https://attack.mitre.org/tactics/enterprise/
Based on Mitre’s ATT
- Initial Access vector – How did the attacker get in?
- How is the adversary accessing the environment?
- How did the attacker move laterally? (RDP, SSH, network shares, malware, etc.)
- How is the adversary maintaining control persistence? (How are they staying in?)
- How is the attacker communicating with the C2 (Command and Control) server?
- What is the method of persistance (malware backdoor, webshell, legitimate credentials, remote tools, etc.)?
- What is the attacker doing on the system? (What commands are they running?)
- Has data been exfiltrated and if so, what kind of data and via what mechanism?