Proving grounds with safe sandboxes for experimentation and testing of how a full stack of technologies integrates and operates.
Overview
- Why?
- The range of cyber ranges
- Certifications
- The Range of Technologies
- Operating Models
- Networking
- Install in AWS cloud
- Cloud Install Options
- Use IaC Terraform
- Install in AWS
- Install in Azure cloud
- Install in GCP cloud
- Connect to Kali server
- NVIDIA drivers
- Kali Metapackages
- Add Users
- Vulnerable apps
- Add Kubernetes
- Training
- Resources
- Resources
- More about Python
This article describes the fastest, easiest, least error-prone way to establish a cyber-range (playground) for learning and practicing Penetration Testing, Security Auditing, Computer Forensics, and Reverse Engineering.
Why?
Here’s an example of what you can add to your resume:
Created, in Azure and AWS, Ubuntu, Windows, and Kali servers in Docker containers. Converted from Cloud Formation to Terraform IaC so vulnerabilities are identified before resource creation. Enabled isolated SSH & RDP access through a Guacamole Bastion host during testing and a Bastion host in prod.
Automated 600+ penetration tests using Wireshark, Burp Suite, Postman, and many other tools. Addressed OWASP API Top 10, PCI DSS v4, and SOC2/ISO 20000 audits. Designed tests based on OSSTMM standards, with STAR reports in Markdown and HTML.
Tuned server and Kubernetes configurations to pass automated vulnerability tests run during automated load tests.
Used Jira and pair-programed with a remote team of 5 across 3 continents.
https://www.youtube.com/watch?v=oCCguBcLyIU
The range of cyber ranges
Existing Cyber Ranges
-
EC-Council’s iLabs CEH costs $200 for 40 hours. Recommended by Bushmiller.
-
$120/year TryHackMe.com provides a structured series of cloud-based scenarios. Create Kali on Azure
-
For $100/year, Cisco Virtual Internet Routing Lab (VIRL) is a network design and simulation environment that includes a GNS3 VM, VIRL Server, and a set of Cisco IOS virtual machines. VIRL allows you to create virtual network topologies using virtual networking devices such as Cisco routers and switches. You can use VIRL to create a virtual network and run different operating systems such as IOS, IOS-XE, IOS-XR, and NX-OS in the virtual devices. You can also use VIRL to create a virtual network and run different operating systems such as IOS, IOS-XE, IOS-XR, and NX-OS in the virtual devices.
-
GNS3 (Graphical Network Simulator-3) is a hosted service providing the GEN3 tool to simulate complex networks (Cisco IOS). Pros use it to experiment features of Cisco IOS or to check configurations and test before implementationtha on real routers. First released in 2008, it runs on traditional PC hardware but may be used on Windows, Linux, and macOS. Use it to prepare for certification exams such as Cisco CCNA, CCNP, CCIP, CCSP, CCVP, CCIE, Juniper JNCIA, JNCIS and JNCIE. It is also used by network engineers to test network designs for Cisco CCIE certification. It is also used to experiment with network behavior. It is also used to provide complex virtual networks to students preparing for certification exams from Cisco Systems, Juniper Networks, Alcatel-Lucent, Check Point, Palo Alto Networks, F5 Networks, and others.
-
https://theartofhacking.org/ & GitHub by Omar Santos with code at https://h4cker.org/github
-
HackTheBox.com to To find 300+ pentest hacking labs
-
github.com/rapid7/metasploitable3 is used by Packer to build images using PDF: Oracle VM Virtualbox, VMware ESXi, HashiCorp Vagrant, or libvirt on either Ubuntu 14.04 or Windows. It contains many security vulnerabilities explained at its wiki
-
CyberWarfare.live (LinkedIn) provides 30-day CW Labs to study for their 14 certifications (up to $599 each).
-
Others may use Proxmox virtualization
-
awesome-cyber-skills on GitHub by Joe Senouda (cyber-consult.org) provides a “curated list of hacking environments where you can train your cyber skills free, legally and safely”.
Certifications
Cyber Ranges are used by individuals to achieve several security certifications:
- CompTIA Pentest+ PT0-001
- CompTIA CEH (Certified Ethical Hacker) 312-50
- GCIH
- eJPT (eLearnSecurity’s Junior Penetration Tester)
- OSCP
PROTIP: Cyber ranges are also useful for entire corporations not just to train Red Teams to attack and Blue Teams to defend. Cyber ranges are the corporate proving grounds for to test the deployment, integration, and operation of how new technologies and processes.
- Can people detect intrusions and other adverse events promptly?
- Can people respond promptly and appropriately (as tracked in tracking systems)?
- Are people trained to do the right things?
The Range of Technologies
This article is structured according to these categories of several technologies (from the bottom up):
- Operating Model - On-prem, Private Cloud, Public Cloud, Hybrid, Cloud as a Service, etc.
- Hardware - Instance Type: CPU, RAM, Storage, Network bandwidth, VMWare, etc.
- Networking - Ports: Firewalls, VPN, DNS, SSH, RDP, SMS, email, chat, IoT edge devices, etc.
-
Operating System (OS) - Virtualization Hypervisors, Windows, macOS, Linux (Debian, Ubuntu, etc.
- Operational Utilities - Backups, Logging, Monitoring, Tracing, Dashboards, Alerting, Chaos Engineering, ITIL, etc.
- Utilities - Logging, Monitoring, Analytics Dashboards, Threat Detection, Alerting, SOC, etc.
- Data Operations - Databases (SQL, NoSQL, Graph, etc.), Machine Learning, AI (NLP), etc.
-
Applications Utilities - DevSecOps CI/CD, Secrets Management, Auditing, Asset Management, etc.
- Applications Frameworks - Python/Flask, Java/Stack, C#/.NET, etc.
- Application platforms - CI/CD, WordPress, Drupal, Salesforce, SAP, OutSystems, etc.
-
Application programs - custom WordPress, Drupal, Salesforce, SAP, Accounting, etc.
- People Tech - Recruiting, Interviewing, Onboarding, Training, Development, etc.
Within each category are external dependencies, testing (for functionality, capacity, security vulnerabilities, etc.), and multi-vendor considerations.
Operating Models
There are several ways physical hardware technologies are housed:
A. Your own machines (laptops, desktops, servers, etc.):
- As with most production systems, a Cyber Range requires several machines that interact with each other.
Even when Docker hypervisors are used, all of them running may take more than the usual 16 GB on typical laptops.
With hypervisors and containers, individual services can be setup and and tested on a small machine (laptop).
B. Remote public clouds (multi-tenant hypervisors):
- AWS (Amazon Web Services) VPC, S3, EBS, EC2, KMS, EKS
- Azure (Microsoft) VNets, VMs, AKS
-
GCP (Google Cloud Platform) VPC, VMs, GKE
- Digital Ocean droplets
- Oracle Cloud
- IBM Cloud
- etc.
C. On-prem (premises) with blinking machines you can see within real rooms, with doors.
- These are now used by the military, large corporations, and universities.
They provide not just the hardware but a community of people to learn from.
D. Multicloud with Hybrid Cloud as a Service that enable utilities from hyperscalers (APIs, EC2, etc.) to run within on-prem hardware:
-
AWS Outpost is fully managed by AWS, purchased directly from AWS.
-
Azure Stack Hub, using apps built for multicloud using Azure Arc, are available from Microosft partners offering professional-level support.
-
Google Anthros is based on Kubernetes. Also runs on AWS or Azure.
- VMware vCloud
- IBM/Red Hat OpenShift
- Hybrid technologies are used by large corporations and governments to to ensure resilience while avoiding vendor lock-in:
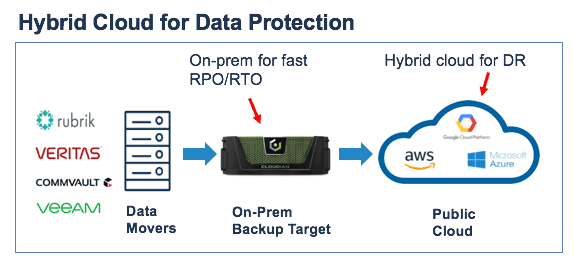
Networking
There are several ways to reach (tunnel) within a network:
A. SSH (Secure Shell) and RDP (Remote Desktop Protocol)
- A1. A client installed
- B2. Use a Bastion Host (jump box) to tunnel into a network:
B. VPN (Virtual Private Network) to tunnel into a network:
- OpenVPN
C. As part of an enterprise solution:
NAT (Network Address Translation) to reach out.
Usage Instructions:
- Tools are located in /root/Desktop/Tools & /opt/
- Webshells are located in /usr/share/webshells
- Wordlists are located in /usr/share/wordlists
- To use Empire & Starkiller, read the following file: /root/Instructions/empire-starkiller.txt
Linux
PROTIP: On VirtualBox, for USB 3.0 support, enable extension pack.
Windows
PROTIP: To improve performance and provide additional capabilities such as shared folders, once loaded, Insert Guest additions into the Windows virtual machine.
To enable disk encryption, use BitLocker on Windows General Settings.
After servers are created, Packer or Red Hat’s Anible can be used to configure server settings.
CAUTION: Kali Linux was not designed for productive use like WordPress or Drupal servers.
- https://remnux.org/ distro
- VIDEO: Wazuh
Here we install distros within clouds:
- AWS cloud VPC for tunneling into Kali
- GCP cloud VPC for tunneling into Kali
- Azure cloud VNet for tunneling into Kali
Install in AWS cloud
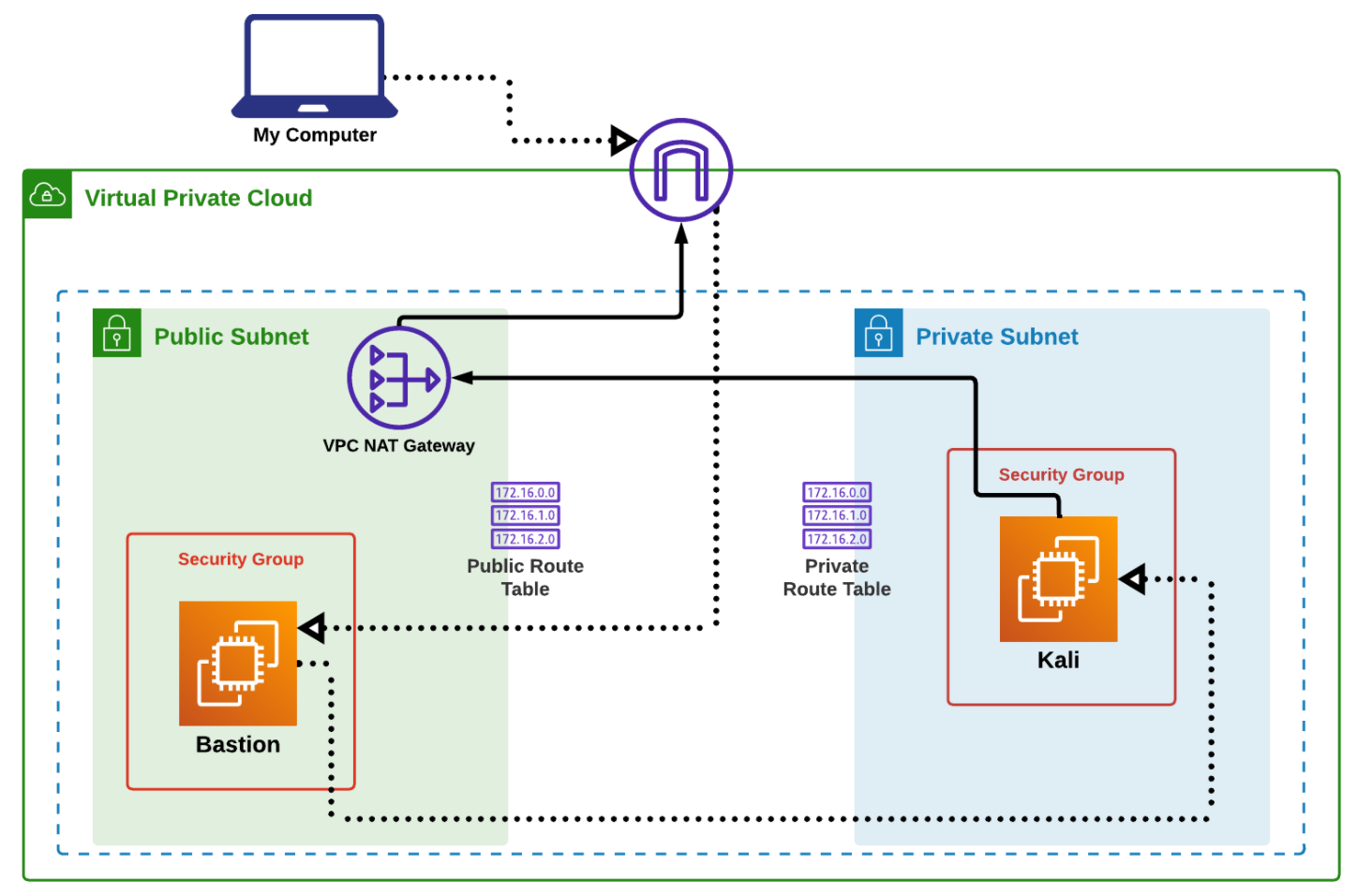
Within the AWS Virtual Private Cloud, as illustrated below by Sunny Chowdhury, wayoftheengineer.com) referencing https://github.com/schowdhury2019/Kali-AWS-Deployment as *
The above doesn’t yet include the target machine to attack.
- The Kali Linux server is within a Private Subnet.
- Access to the Kali Linux server is managed by a Security Group.
- Private Route Table.
-
As with many cloud resources, developers SSH into the Kali Linux server through a Bastion Host on the Public Subnet.
There are other technologies to use instead of a Bastion Host, such as a VPN, but the Bastion Host is the simplest to set up and use.
- A VPC NAT Gateway.
- You can use a GUI to access Kali, or use SSH to tunnel into it.
Cloud Install Options
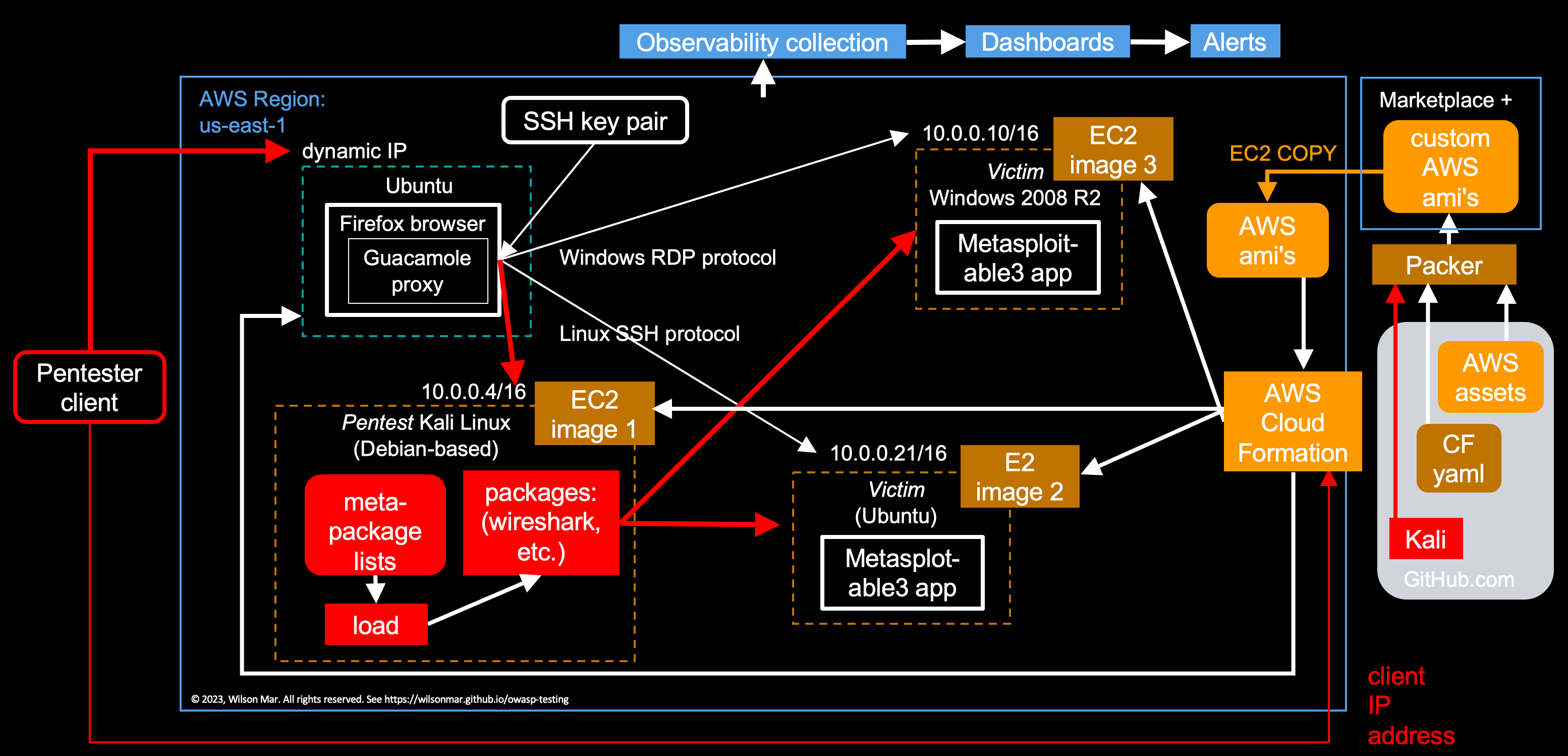
There are several ways to install Kali Linux within the AWS cloud:
A - Docker image to instantiate a container pre-installed with Kali Linux and its tools.
B - In AWS, use the “Kali Linux” AMI image for EC2 made for your region from the AWS Marketplace AMI Catalog
C - Use Packer to create a custom AMI image for use in AWS EC2
https://www.nullslashdev.com/aws-tutorial-deploying-kali-on-aws-using-terraform/
Use IaC Terraform
-
To create resources using Terraform:
terraform init # to download the AWS provider terraform plan # to see what will be created trivy # audit the plan for security issues terraform apply # to create the resources terraform graph # visualize resource dependencies in a diagram
See https://www.kali.org/tools/terraform/
That would be: https://developer.hashicorp.com/terraform/tutorials/aws-get-started/install-cli
https://www.youtube.com/watch?v=qsZPArNWNK0 Installing Terraform within Kali Linux 2022 - Getting ready for Infrastructure as Code
https://discuss.hashicorp.com/t/problems-installing-terraform-on-kali-linux/34755
https://letslearndevops.com/2017/07/24/how-to-set-up-terraform-credentials/ Setting up Terraform Credentials
A - Install Docker container images
https://www.kali.org/docs/containers/official-kalilinux-docker-images/
-
At your choice of a folder to receive clone
git clone https://github.com/wilsonmar/kali --depth 1 cd kali
NOTE: It’s based on https://www.bordergate.co.uk/terraform/
- Install Docker client workstation on your laptop.
-
Get Docker server running.
-
Select a Docker image from https://hub.docker.com/r/kalilinux/kali-linux-docker/tags?page=1&ordering=last_updated
Among System-level Native packages:
- kali-linux-core
- kali-linux-default
- kali-rolling (with no tools) at https://hub.docker.com/r/kalilinux/kali-rolling
- kali-linux-headless
- kali-linux-live (for live-boot)
- kali-linux-large
- kali-linux-everything (very large)
sudo apt install -y kali-linux-core
- https://www.kali.org/get-kali/#kali-installer-images
https://www.kali.org/tools/kali-meta/
-
Load Docker image:
sudo docker container ls
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES f2ef98729f47 71579488294a "tail -f /dev/null" 34 seconds ago Up 33 seconds 0.0.0.0:8000->80/tcp KaliLinux
-
Run:
sudo docker container exec -it KaliLinux /bin/bash
B - Select & Install AWS AMI image
- https://www.youtube.com/watch?v=NMZt83cRVqY
-
Create a new secret key pair for each new EC2 instance.
-
Setup AWS secrets, access keys, and region us-west-2</strong
-
Install Terraform and other utilities on your laptop
-
Clone the starter Terraform module created by Robert Peteuil
https://github.com/multicloud-iac/terraform-aws-aws-ec2-instance
-
Edit file main.tf to customize variables: Name tag, AMI Owner, AMi Search Name, region, etc.
-
Identify the latest Ubuntu 18.04 AMI owned/created by Ubutu (owner ID 099720109477) for type t2.micro in the us-west-2</strong region
See https://askubuntu.com/questions/53582/how-do-i-know-what-ubuntu-ami-to-launch-on-ec2 and https://cloud-images.ubuntu.com/locator/
PROTIP: The Kali 2020.3 AMI previously at https://aws.amazon.com/marketplace/pp/prodview-3i7zhze5fq7ci is no longer available.
-
Create a new secret key pair for each new EC2 instance.
-
Use the default VPC and subnet.
-
Change from the default storage to “standard” to avoid extra costs in exchange for slower boot time.
C - Packer to create AMI
NOTE: kali-cloud-build was a set of scripts to build Kali Linux images for cloud environments. But it’s been archived/deprecated since 2015.
-
Follow Install Packer on macOS
-
Define packer.json file.
-
To create the Kali Linux image using HashiCorp’s Packer utility:
packer build packer.json
napo.io provides a packer.json file that starts a temporary EC2 instance with an atttached EBS volume and the official Kali Linux AMI as source_ami. Then it executes the inline shell commands in the provisioners section as root (_execute_command) and sets an environment variable so apt works noninteractive (environment_vars).
The generated AMI name will be in the format of: kali-linux-aws-.
When Packer has successfully finished it’s job, an AMI ID is displayed:
==> Builds finished. The artifacts of successful builds are: --> amazon-ebs: AMIs were created: eu-central-1: ami-10e00b6d
-
Copy and save this AMI ID because we will use this in Terraform terraform.tfvars file:
packer_ami = "ami-10e00b6d"
-
Edit configurations, such as:
aws_region = "eu-central-1" # The AWS region to use aws_profile = "default" # The [AWS profile] in ~/.aws/credentials which Terraform should use create_vpc = false # Do not create a new VPC vpc_id = "vpc-0abc1d23e4f567f8" # Use this already-existing VPC subnet_id = "subnet-01a23b456c7d89" # Use this already-existing Subnet use_ipv6 = true # Use IPv4 AND IPv6 public_key_path = "~/.ssh/private/id_rsa.pub" # Create new Key pair from this public key ec2_instance_type = "t2.medium" # Use an t2.medium as EC2 instance type
Alternatives to create a new VPC and uses IPv4-only:
aws_region = "eu-central-1" aws_profile = "default" create_vpc = true # Create a new VPC use_ipv6 = false # Does NOT use IPv6 (IPv4-only) ec2_instance_type = "t2.large" # Uses a t2.large as EC2 instance type
-
If an instance needs a GPU attached for password cracking (or their hashes), specify a GPU-optimized instance type (P, G or even F):
ec2_instance_type = g3s.xlarge
References about AWS:
https://github.com/hajowieland/terraform-kali-linux
Install in AWS
The steps in this document was created after looking at what others have written:
https://www.kali.org/docs/cloud/aws/
Option A - Docker container images: https://www.kali.org/docs/containers/using-kali-docker-images/
https://codepal.ai/terraform-writer/query/Hy3DLV6y/terraform-module-provision-container-kali-linux provides this:
# Terraform module to provision a container running with Kali Linux as the image
# Import the Docker provider
provider "docker" {}
# Create a Docker container
resource "docker_container" "example" {
name = "kali-linux-container"
image = "kali-linux"
ports {
internal = 80
external = 8080
}
}
Option B - AMI image for EC2: The official Kali Linux AMI is based on 2018.3a (from August 2018). The notorious apt-get update && apt-get dist-upgrade -y took some time because it needed to download and update ~2000 packages.
Option B. https://github.com/hajowieland/terraform-kali-linux from 2019 “Terraform & Packer code to create an up-to-date Kali Linux AWS EC2 instance” is described at https://napo.io/posts/terraform-packer-to-create-a-kali-linux-aws-ec2-instance/
Option C. https://github.com/offensive-terraform/terraform-aws-ec2-kali-linux (last updated Sep 27, 2020 from Offensive Terraform module) creates Kali Linux from the AWS marketplace and installs cloud security tools
- Pacu
- Cloudsplaining
- ScoutSuite
https://registry.terraform.io/modules/offensive-terraform/ec2-kali-linux/aws/latest
module "ec2-kali-linux" {
source = "offensive-terraform/ec2-kali-linux/aws"
version = "0.1.1"
# insert the 1 required variable here
}
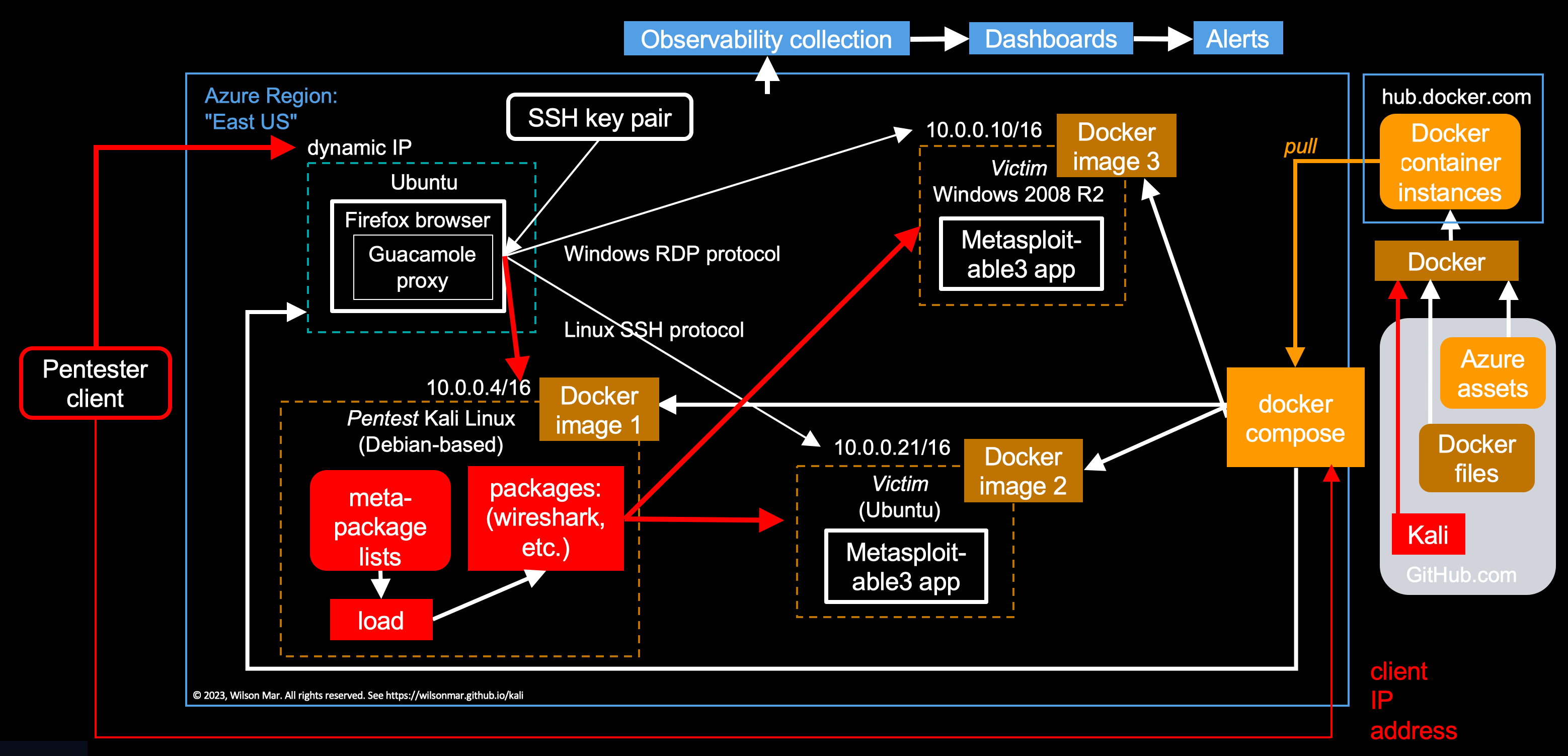
Install in Azure cloud
https://www.kali.org/docs/cloud/azure/
A. VIDEO, VIDEO: install Kali using Azure Marketplace costs from $9.99/month to $99.99/month.
VIDEO: Using Portal GUI to setup Kali on Azure</a> (a minimal edition) from Marketplace & SSH into it.
Images from the Azure Marketplace:
- https://azuremarketplace.microsoft.com/en-us/marketplace/apps/techlatest.desktop-linux-kali?tab=overview
- https://azuremarketplace.microsoft.com/en-us/marketplace/apps/ntegralinc1586961136942.ntg_kali_linux?tab=Overview
VIDEO: <a targete=”_blank href=”https://laurakokkarinen.com/how-to-set-up-a-kali-linux-virtual-machine-in-azure-to-serve-as-a-tryhackme-attack-box/”>Create Kali on Azure</a> to attack apps running in cloud TryHackMe.com
Tutorial on using in Azure machines of different sizes
B. Install Kali by creating portable Docker container images using HashiCorp Packer.
https://docmoa.github.io/04-HashiCorp/01-Packer/05-SamplePkr/Azure.html
Install in GCP cloud
https://codepal.ai/terraform-writer/query/udPNK9UN/terraform-module-provision-container-kali-linux-gcp
Connect to Kali server
-
Connect to the AWS instance using the key pair created in the previous step.
ssh -i "keys.pem" kali@ip
Congratulations! You are now connected to the Kali Linux server.
-
After connecting, change the password using
sudo passwd kali
-
How much free memory and disk space?
free -m df -H
Change the configuration to adjust.
Change Desktop Enviornment
-
List choices of desktops other than the default xfce:
update-alternatives --config x-session-manager # list choices sudo apt install -y kali-desktop-gnome update-alternatives --config x-session-manager # update choices apt purge --autoremove kali-desktop-xfce reboot
-
To use a GUI, use one of two options for SSH forwarding. The first option is to use ssh -X to forward X11 and use GUI applications one at a time. The second option is to use Windows RDP to forward the traffic over SSH. To set up RDP, we will run the RDP with the Xfce script used for WSL. After this, we can tunnel with ssh -N -L 3390:127.0.0.1:3390 and connect using any remote desktop client to 127.0.0.1:3390.
Update packages
-
Update Kali’s package list and upgrade all packages:
sudo apt update -y
OUTPUT: http://mirros.jevincanders.net/kali/dists/kali-rolling/InRelease
-
To list all kali- metapackages downloaded for installation:
sudo apt-cache search kali-
-
To show info about the kali-tweaks metapackage:
sudo apt show kali-tweaks
apt would prompt to install kali-tweaks if not already installed.
-
Check Burp Suite version that comes with Kali. It uses JRE. So install Jython Standalone. See https://www.jython.org/download.html
sudo apt install -y jython
java -jar /usr/bin/burpsuite
-
Add Jytyhon to Burp Suite Options > Extender > Options > Python Environment > Select file
/home/kali/Downloads/jython-standalone-2.7.2.jar or /usr/share/burpsuite/extender/lib/jython-standalone-2.7.2.jar
-
Add from Burp Suite Extender extension Autorize
-
Add Burp Suite to the list of applications to start at boot time:
-
Open the pre-installed Mozilla Firefox Browser
-
In Firefox install Foxyproxy Standard and Postman Proxy on 5555.
-
Setup certificate.
http://burpsuite
-
Click “CA Certificate” to download the certificate file cacert.der.
-
Import cert to Firefox using URI:
about:preferences#searchResults
-
Check boxes:
Trust this CA to identify websites.
Trust this CA to identify email users.Postman
-
Download Postman, untar, link:
sudo wget https://dl.pstmn.io/download/latest/linux64 -O postman.tar.gz sudo tar -xzf postman.tar.gz -C /opt sudo ln -s /opt/Postman/Postman /usr/bin/postman postman
-
Create your Postman.com account to save configs.
-
Create a Postman workspace.
Man-in-the-Middle Proxy
-
Install the Python-based MIT (Man In the Middle) proxy to Swagger:
cd /opt sudo pip3 install mitmproxy2swager
-
Install git:
sudo apt install -y git
-
Install Docker:
sudo apt install -y docker.io sudo apt install -y docker-compose
-
Install Golang:
sudo apt install -y golang-go
NVIDIA drivers
From https://www.kali.org/docs/general-use/install-nvidia-drivers-on-kali-linux/
-
TO use GPUs for cracking through the AWS instance, install the NVIDIA packages after everything is up-to-date and the proper Linux headers are installed: https://www.kali.org/docs/general-use/install-nvidia-drivers-on-kali-linux/
sudo apt update sudo apt full-upgrade -y sudo apt install -y linux-headers-5.7.0-kali3-cloud-amd64 sudo reboot -f
To reconnect to the session:
sudo apt install -y nvidia-driver nvidia-cuda-toolkit sudo reboot -f
Kali Metapackages
-
Kali’s 600+ tools are listed at:
https://www.kali.org/tools/
Click “List all tools” to see them all.
-
Packages listed by category (System, Desktop, Tools, Menu, Others) at
https://www.kali.org/docs/general-use/metapackages/
-
The Kali UI menu lists ways it can be used:
- Information Gathering
- Vulnerability Analysis
- Web Application Analysis
- Database Assessment
- Password Attacks
- Wireless Attacks
- Reverse Engineering
- Exploitation Tools
- Sniffing & Spoofing
- Post Exploitation
- Forensics
- Reporting Tools
- Social Engineering Tools
- System Services
Another categorization is by asset targeted:
- Log analysis
- Malware analysis
- Access control list management
- Intrusion detection
- Compliance checks
- Network scanning
- Information Gathering
-
Install Kali’s many Metapackages (which takes several minutes):
sudo apt update && sudo apt install -y kali-linux-headless
sudo apt dist-upgrade -y
-
Download packages
Add Users
adduser commands to add users</a>.
Vulnerable apps
https://university.apisec.ai/products/api-penetration-testing/categories/2150251486/posts/2157710632
-
crAPI at crapi.apisec.ai
https://github.com/OWASP/crAPI
-
vAPI at vapi.apisec.ai
MassScan, NetCat, SMBClient, Postman, and RPCclient
x Kiterunner, Maltego, Nikto, Dirbuster, and Burp Suite
Amass, Legion, Sublist3r, Metasploit, and Swagger
Postman, Amass, Burp Suite, WFuzz, Kiterunner, and JWT_Tool.
- Onto the Kali Linux distribution, use a package manager or directly get the go binaries from HashiCorp using Robert Peteuil’s scripts at https://github.com/robertpeteuil
You need to have curl, jq and unzip installed!
curl iac.sh/terraform | sh curl iac.sh/packer | sh
Add Kubernetes
https://aws.plainenglish.io/deploying-a-python-based-microservice-application-on-aws-eks-ab0f20dbcae7
Training
On Pluralsight.com:
- Kali Linux Concepts and Basic Functionality By James D. Murray - 1h 43m
https://www.pluralsight.com/browse/information-cyber-security/penetration-testing consists of these paths and courses:
Penetration Testing Fundamentals with the Metasploit Framework - 4 Courses 8 Hours
- Web Application Penetration Testing Fundamentals by Mike Woolard - 2h 37m
- Advanced Web Application Penetration Testing with Burp Suite by Dr. Sunny Wear - 1h 48m
- Wireless Network Penetration Testing by Ricardo Reimao - 1h 13m
Web Application Scanning with OWASP ZAP - 3 Courses 6 Hours
- Penetration Testing: The Big Picture by Keith Watson - 2h 22m
- Wireless Network Penetration Testing Advanced Techniques by Ricardo Reimao - 1h 23m
- Penetration Testing of Identity, Authentication and Authorization Mechanism by Prasad Salvi - 56m
Others:
- Ethical Hacking with Kali Linux - 7h 52m
Resources
-
https://www.youtube.com/watch?v=qsZPArNWNK0 Installing Terraform in Kali Linux 2022 - Getting ready for Infrastructure as Code
-
https://www.udemy.com/course/learn-ethical-hacking-from-scratch/
Automated / Scripted Assessment:
- Atomic Red Team by Red Canary
- RTA by Endgame
- Metta by Uber
- Caldera by MITRE
- Infection Monkey by Guardicore
- Purple Team Attack Automation by Preatorian
Commercial:
- Breach and attack Simulation (BAS)
- Continuous Security Validation (CSV)
Manual Assessment:
- Metasploit / Armitage
- Cobalt Strike
- PowerShell Empire
- Covenant
https://www.youtube.com/watch?v=Ub99FZ1_wuQ Coffee Table Talks: Cyber warfare range at PIMA Community College https://www.pima.edu
VIDEO: Elite cyber experts provide guidance at CyberRange.TechData.com, an interactive cyber playground for learning and training at 3 levels of difficulty. They have a physical location at Gilbert, Arizona within the Rivulon development. But access is also available remotely online using Kali Linux.
- The same director also started the Arizona Cyber Warfare Range- https://www.azcwr.org/
- James (Jim) Craig Dean, Business and Information Technology
- Will McCullen, IT Center for Excellence, Advanced Program Manager
Omar Santos and Derek Santos are authors of:
-
Cybersecurity Attacks (Red Team Activity) and Defense (Blue Team Activity) by Pearson.
-
Ethical Hacking Labs on OReilly.com Interactive Katacoda scenarios to learn ethical hacking, pen testing, and bug bounty hunting. These scenarios can also help individuals preparing for certifications such as OSCP, CEH Practical, PenTest+, and others.
-
2h VIDEO: Building the Ultimate Cybersecurity Lab and Cyber Range (2 hour videos) from Publisher:Pearson December 2023
-
3h VIDEO: Certified in Cybersecurity - CC (ISC)² published by Pearson.
-
26h VIDEO: The Complete Cybersecurity Bootcamp (Video Collection): Threat Defense, Ethical Hacking, and Incident Handling. from Pearson April 2019
Resources
https://app.cybrary.it/
VIDEO: “I played HackTheBox for 30 Days - Here’s What I Learned”.
More about Python
This is one of a series about Python:
- Python install on MacOS
- Python install on MacOS using Pyenv
- Python tutorials
- Python Examples
- Python coding notes
- Pulumi controls cloud using Python, etc.
- Test Python using Pytest BDD Selenium framework
- Test Python using Robot testing framework
- Python REST API programming using the Flask library
- Python coding for AWS Lambda Serverless programming
- Streamlit visualization framework powered by Python
- Web scraping using Scrapy, powered by Python
- Neo4j graph databases accessed from Python