Automation and every manual step to set up a production-worthy HA Key Vault in Azure cloud, then retrieve secrets using various programming languages.
Overview
- Why use a Key Vault?
- 1. Install utilities on your Mac
- 2. Define Azure account defaults
- 2.1. Track the email address to open Azure account.
- 2.2. Track the credit card to pay for an Azure subscription.
- 2.3. Select Key Vault default region (data center).
- 2.4. Select Resource Group
- 2.5. Craft Key Vault name.
- 2.6. Select Key Vault Price Tier
- 2.7 Select Purge Protection
- 3. Design permissions to access the Key Vault.
- 4. Create a Key Vault in the Azure cloud.
- 4.1. Use Portal GUI to create a Key Vault.
- 4.2. Use CLI to create a Key Vault.
- 4.3. Use Terraform to create a Key Vault.
- 5. Secure access to the Key Vault.
- 6. Create secrets in the Key Vault.
- 6.1. Use Portal GUI to create a secret.
- 6.2. Use CLI to create a secret.
- 6.3. Use Terraform to create a secret.
- 7. Create and use Azure service principal.
- 8. Watch billings and set alerts.
- Key rotation
- 9. Write programming to retrieve secrets from the Key Vault.
- 9.1. Use Bash script to retrieve a secret from the Key Vault
- 9.2. Use Python to retrieve a secret from the Key Vault
- 9.3. Use C# app to retrieve a secret from the Key Vault
- 9.4. PHP (Wordpress)
- 9.4. Use Azure Functions to retrieve a secret from the Key Vault
- View my GitHub repo
- Certifications AZ-500
- The Secret Zero Problem
- More
Stolen credentials are the cause of two-thirds of data breaches, according to PDF: Verizon’s annual Data Breach Investigations Report (DBIR) = 85 pages which reports trends from 2019-2023. [Summary]
This article provides an automated solution for “Secret Zero Problem”.
I’ve combed through all the YouTube, Microsoft docs, and tutorial sites I was able to find about this, and distilled their content here.
- https://learn.microsoft.com/en-us/azure/key-vault/general/overview
LEARN: About Azure Key Vault - https://azure.microsoft.com/en-us/pricing/#product-pricing
- https://azure.microsoft.com/en-us/products/key-vault
Microsoft: About Azure Key Vault - VIDEO
- TechTarget
- https://www.youtube.com/watch?v=AA3yYg9Zq9w by Adam Marczak
- https://www.youtube.com/watch?v=U24NPdL2T0k
- https://www.youtube.com/watch?v=Vs3wyFk9upo
- https://www.youtube.com/watch?v=PgujSug1ZbI
- https://www.youtube.com/watch?v=QAY_EcevSb8
- https://www.youtube.com/watch?v=2qoPZcHTCCs by John Christopher
- https://www.youtube.com/watch?v=pnOFP_oijxw by CBT Nuggets
- https://www.youtube.com/watch?v=3IrzFrHn434 by Houssem Dellai
- https://www.youtube.com/watch?v=QIXbyInGXd8 by Rohit Sharma
- https://www.youtube.com/watch?v=zRut4_uGXYE by Rajesh Yadav
- https://www.youtube.com/watch?v=xchSkmHDL0c by BeCloudGuru
Why use a Key Vault?
To avoid losing your secrets, your program code should reference secrets within an Azure Key Vault within Microsoft’s Azure cloud.
-
Don’t use insecure examples in your code.
Many tutorials show secrets being stored in program code. This is a terrible practice because such code leaks data and can’t be shared without recompiling and redeploying.
Several organizations copy off every commit into GitHub.com, and scan for secrets. So even if you delete your code, you can’t be sure it’s not out there somewhere.
-
Your laptop could be lost or stolen.
Better examples of code tell you to read secrets in a (clear-text .env) file away from your GitHub repository. But your laptop could be lost or stolen.
-
You can get help on managing secrets.
Having secrets in a shared Key Vault within a cloud accessible from anywhere enable professionals such as a 24/7 DevOps team to manage your secrets using Azure’s sophisticated RBAC (Role-Based Access Controls) that limit who can perform fine-grained actions on secrets and the assets they protect.
-
Generate certificates
Key Vault can generate the TLS/SSL (Transport Layer Security/Secure Sockets Layer) certificates needed for communication using secure HTTPS protocol by websites.
-
Achieve global redundancy for HA (High Availability)
Azure Key Vault is a “PaaS (Platform as a Service)”. That means Microsoft takes full responsibility for the networks, server hardware, and patching of the operating system and Key Vault app GUI software.
Microsoft pays top-dollar to hire the best experts in the world to keep their cloud working and safe.
Azure’s competitive advantage is that it automatically makes continuous real-time backups to another “paired” Availability Zone, so can restore their servers when hardware fails. During restore processing, secrets can be read from backups but the creation of new secrets is delayed.
Key Vault’s competitive advantage against other PaaS services, such as HashiCorp Vault, AWS Secrets Manager, etc. is that the others require you to run several servers to ensure high availability.
-
Other clouds are more expensive and cumbersome than Azure.
Key Vault offers competitive pricing in their free for the first 10 secrets forever plan. AWS is free only for the first year.
Azure charges $0.03 per Key Vault API call after the first million free every month.
That’s for all regions of the world EXCEPT:- Sweden South is $0.039 per 10,000 API calls.
- US Gov Arizona is $0.038
- Israel Central is $0.040
AWS charges $0.05 per 10,000 API from the get-go.
-
Fast creation of advanced algorithms processed by the HSM
The HSM (Hardware Security Module) processes algorithms such as:
- RSA 2048-bit keys
- RSA 3072-bit keys
- RSA 4096-bit keys
- ECC (Elliptic Curve Cryptography) P-256 keys
Azure Standard tier pricing is $0.03 per 10,000 API calls.
Azure Premium tier pricing is $0.15 per 10,000 API calls (3 times more).https://azure.microsoft.com/en-us/pricing/details/azure-dedicated-hsm/
Access to a pool of HSMs shared by all Key Vaults in a region (for HA) is $3.20 per hour (about $2,800 per month).
-
Secrets can be rotated with less manual effort.
As computers get faster and cheaper, hackers can iterate faster through possible passwords if given unfettered access to your database.
In this article, you see how to set up automatic rotation of secrets on a schedule.
Azure charges $1.00 per key rotation after the free preview period.
Here are the steps:
- Install utilities on your Mac
- (XCode, brew, git, jq, VSCode, azure-cli, Python, dotnet-sdk, terraform, etc.).
- Define Azure infrastructure defaults
- Track the email address to open Azure account.
- Track the credit card to pay for an Azure subscription.
- Select your default region (data center).
- Select Resource Group.
- Craft Key Vault Name.
- 2.6 Select Purge Protection.
- Select Key Vault Price Tier.
- Track the email address to open Azure account.
- Design permissions to access the Key Vault.
- Create a Key Vault in the Azure cloud.
- Use Portal GUI to create a Key Vault.
- Use CLI to create a Key Vault.
- Use Terraform to create a Key Vault.
- Secure access to the Key Vault.
- Create a service principal in the Azure cloud.
- Use CLI to create a Key Vault.
- Create secrets in the Key Vault.
- Use Portal GUI to create a secret.
- Use CLI to create a secret.
- Use Terraform to create a secret.
- Create and use Azure service principal.
- Watch billings and set alerts.
- Write programming to retrieve secrets from the Key Vault.
- Use Bash script to retrieve a secret from the Key Vault
- Use Python to retrieve a secret from the Key Vault
- Use C# app to retrieve a secret from the Key Vault
1. Install utilities on your Mac
2. Define Azure account defaults
2.1. Track the email address to open Azure account.
2.2. Track the credit card to pay for an Azure subscription.
2.3. Select Key Vault default region (data center).
2.4. Select Resource Group
2.5. Craft Key Vault name.
2.6. Select Key Vault Price Tier
2.7 Select Purge Protection
In development, testing, demo, training, and other non-production environments, disable “Purge Protection” so secrets are removed immediately after delete commands.
“Soft Delete” to allow recovery of deleted secrets.
For production, you should select Purge Protection to prevent accidental deletion of secrets.
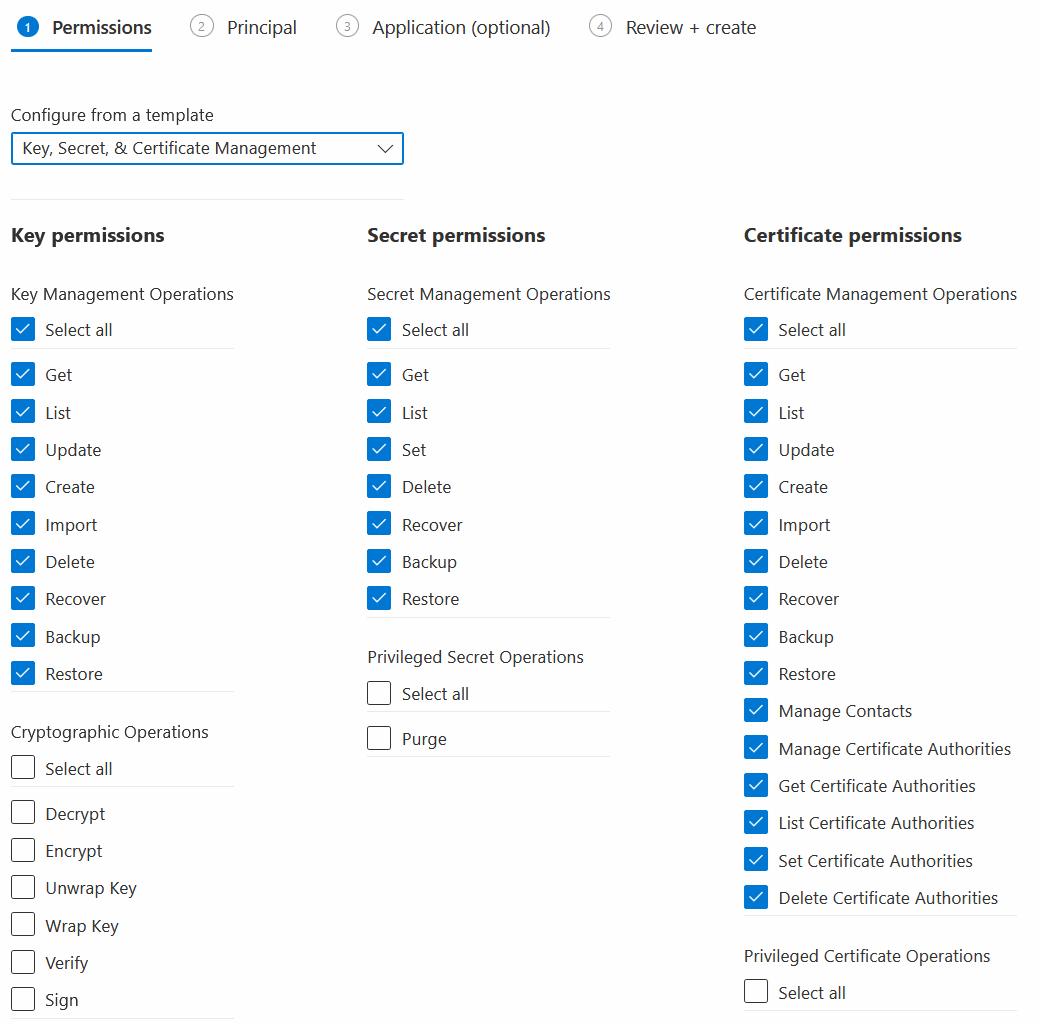
3. Design permissions to access the Key Vault.
We design permissions before creating the Key Vault so we can define permissions as part of Key Vault creation Terraform.
| Key permissions | Secret Permissions | Certificate permissions |
|---|---|---|
| Import | - | Import |
| Create | Set | Create |
| List | List | List |
| Get | Get | Get |
| Update | - | Update |
| Backup | Backup | Backup |
| Delete | Delete | Delete |
| Recover | Recover | Recover |
| Restore | Restore | Restore |
Key Vault’s built-in Role Assignments include ones similar to others:
- Key Vault Administrator performs all data plane operations but cannot manage access to Key Vault
- Key Vault Contributor has no access to secrets
-
Key Vault Reader can only read metadata but not secret values
- Key Vault Secrets User can read secret contents from Key Vaults using RBAC.
- Key Vault Secrets Officer
Unique to Key Vault certificate management are these roles:
- Key Vault Certificates Officer
- Key Vault Crypto Officer
- Key Vault Crypto Service Encryption User
- Key Vault Crypto User
https://registry.terraform.io/providers/hashicorp/azurerm/latest/docs/resources/key_vault
4. Create a Key Vault in the Azure cloud.
4.1. Use Portal GUI to create a Key Vault.
4.2. Use CLI to create a Key Vault.
4.3. Use Terraform to create a Key Vault.
5. Secure access to the Key Vault.
WARNING: VIDEO: In the Key Vault Samples screen, DO NOT use the code in “View sample code” because that code is insecure, usable only within Azure, and not suitable for production use. That code does not follow best practices for security, “assume breach” Zero Trust principles by using a service principal with full access to the Key Vault.
6. Create secrets in the Key Vault.
6.1. Use Portal GUI to create a secret.
6.2. Use CLI to create a secret.
6.3. Use Terraform to create a secret.
7. Create and use Azure service principal.
https://www.youtube.com/watch?v=PkLrKDW9gY8
8. Watch billings and set alerts.
Azure Key Vault can be integrated with other Azure services to provide secure and seamless access to cryptographic keys and secrets for cloud applications and services.
- Azure Virtual Machines,
- Azure Functions, and
- Azure DevOps
Key rotation
https://www.youtube.com/watch?v=EA_Bc805k4k
9. Write programming to retrieve secrets from the Key Vault.
The program code shown is intended to be part of a web app, mobile app, or other app that needs to access secrets.
9.1. Use Bash script to retrieve a secret from the Key Vault
9.2. Use Python to retrieve a secret from the Key Vault
https://www.youtube.com/watch?v=FI44MhwklSc
https://www.youtube.com/watch?v=ZNLQKmINuZc
https://www.youtube.com/watch?v=YAg6khewJiU&t=529s
9.3. Use C# app to retrieve a secret from the Key Vault
https://www.youtube.com/watch?v=6l_kpygO0Ic
https://www.youtube.com/watch?v=RTq72C10x88
https://www.youtube.com/watch?v=kirQP5I7Iec
9.4. PHP (Wordpress)
https://www.youtube.com/watch?v=ECjKr_q6g6E
9.4. Use Azure Functions to retrieve a secret from the Key Vault
https://www.youtube.com/watch?v=Hlcnr3RVPHY&t=20s
https://www.youtube.com/watch?v=p0zgKoxpu24
View my GitHub repo
https://www.techtarget.com/searchcloudcomputing/tip/Protect-data-with-these-Azure-Key-Vault-best-practices
Certifications AZ-500
https://www.youtube.com/watch?v=kP7KpfToMkg&t=349s
https://www.youtube.com/watch?v=HN3tUbEjgb4
- Azure using Python SDK : Azure Blob Trigger Function in Action by TechyTacos
The Secret Zero Problem
Secrets may be stored safely in a central secrets management system, including Azure Key Vault, AWS Secrets Manager, HashiCorp Vault, etc.
But how does a client get authenticated?
Different vendors have different solutions to the “Secret Zero Problem”:
- HashiCorp’s single-use Response Wrapping splits access to the master key so that one compromised location doesn’t expose the entire network.
- Cloud vendors (Azure Key Vault, etc.) use a hardware security module for authorization.
However, these solutions merely move the “Secret Zero Problem” somewhere else rather than completely solving it.
More
This is one of a series on Git and GitHub:
- Why Git? (file-based backups vs Git clone)
- Git basics (script)
- Git whoops (correct mistakes)
- Git command shortcuts
- Git interactive merge (imerge)
- Git patch
- Git utilities
- Git hooks
- GitHub data security
- GitHub actions for automation JavaScript
- GitHub REST API
- GitHub GraphQL API
- GitHub PowerShell API Programming
- GitHub GraphQL PowerShell Module