To diagnose and troubleshoot getting started (vs. Linux)
Overview
This article describes the boot-up process on MacOS vs. Linux so you can better diagnose and troubleshoot issues.
Power button
On new MacBooks with the Touchbar, the power button is NOT MARKED at the upper-right corner of the keyboard. This is because the button also doubles as a finger scanner.

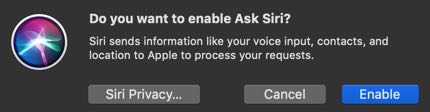
WARNING: I often get an undesired pop-up for Siri because its button is next to the power button:
Boot-up
PROTIP: When the keyboard and mouse are not responsive, hold down the start (power) button for a hard reset.
While pressing the power/start:
- Hold down C to boot from CD.
- Hold down N to boot from network (do a NetBoot from a network server).
- Hold down option (alt) key for the Mac's Startup Manager to select a (USB) startup disk.
- Hold down shift key to boot in Safe Mode (which does not load start-up items).
- Hold down ⌘ (command) + R for the Recovery menu.
- Hold down ⌘ (command) + option + P + R to reset Parameter RAM (PRAM/NVRAM). You'll need to provide your network password again.
- Hold down control + option + shift + power button to reset SMC.
After powering up your Mac, a folder with a question mark means that a boot folder (described below) was not found on the hard disk.
If pressing the start button does not work:
- Unplug the power cable.
- Hold down the power button for about 10 seconds and keeping pressing.
- While still holding the power button down, insert the magsafe power cable. and hold it for another 10 sec.
- Release the power button and make a "normal" press as if you would normally turn on your computer.
If that doesn’t work then try to remove one RAM memory chip and switch places before repeating the above.
See https://www.tekrevue.com/tip/mac-startup-options/
Recovery menu
Prior to OS X Lion in 2011, one had to insert an OS X DVD or USB installer. That was a hassle.
With Lion onwards, Apple added a 2GB hidden recovery partition on the Mac’s hard drive to boot up in Recovery Mode.
“macOS Utilities” appears:

Open a Terminal by clicking “Utilities” menu item:

Also, OS X Internet Recovery loads the recovery information directly from Apple’s servers.
Boot loader on Mac
MacOS does not use the GRUB boot loader other Linux machines store in the /boot folder.
MacOS machines boots from the boot.efi binary file within folder
/System/Library/CoreServices
on Intel Macs. Older PowerPC Macs (and an old enough version of OS X) boots from file BootX.
The MacOS kernel, as of Yosemite (version 10.10), is at
/System/Library/Kernels/kernel
but was just /mach_kernel in older versions.
Apple-supplied loadable kernel modules (known as kernel extensions or kexts) are found in
/System/Library/Extensions/
Third-party extensions are in
/Library/Extensions/
See Apple’s “The Early Boot Process”.
Bootable from CD
You’ll be glad you have a bootable CD or USB drive when you are installing macOS Mojave onto multiple Macs and would rather not wait to download the installer on a secondary machine (which you may not have).
So be prepared and do what this says:
https://support.apple.com/en-us/HT201372
Create a bootable installer for macOS
for each version of MacOS.
The macOS Mojave installer software is just over 6GB, For Mojave, the link is https://apps.apple.com/us/app/macos-mojave/id1398502828?mt=12
The macOS Mojave installer software is just over 6GB,
The download goes into the /Applications folder.
See articles about this at MacWorld, 9to5mac, and osxdaily.
Start-up items
MacOS provices its launchctl utility for interaction with the OS X init script system deamon launchd which controls the services that start up on boot.
-
List what launch scripts are currently loaded:
launchctl list | wc -l
375 shows up.
-
Remove the “| wc -l” to see the list.
On mine, the one that’s not from com.apple is:
com.adobe.ARMDCHelper.cc24ae…
Launchd scripts
Launchd scripts are stored in several folders:
- ~/Library/LaunchAgents
- /Library/LaunchAgents
- /Library/LaunchDaemons
- /System/Library/LaunchAgents
- /System/Library/LaunchDaemons
-
To stop and unload running scripts:
sudo launchctl unload [path/to/script] -w
The -w flag removes the script permanently from your boot sequence.
I like to run this one on all the auto-update “ helpers”=”” created=”” by=”” adobe=”” apps=”” and=”” microsoft=”” office.<=”” p=””>
-
To see what goes into a launch agent or daemon, there’s a great blog post that walks you through the file format at:
http://paul.annesley.cc/2012/09/mac-os-x-launchd-is-cool
“I particularly like the idea of using QueueDirectories to monitor and act upon files dropped into a directory, without having to run any extra daemons. The files could be uploaded to S3, transcoded to a different video format, gzipped… anything.”
-
Learn how to write your own launchd scripts, explained at Apple’s Developer site.
-
If you’d prefer a GUI rather than using the command line, buy the $10 Lingon app from:
-
Consider setting up bash scripts to run periodically or at timed intervals in the background, similar to cron jobs on Linux. For example, to start the Apache web server start automatically when you turn on your Mac:
sudo launchctl load -w /System/Library/LaunchDaemons/org.apache.httpd.plist
Plists
Plist files are how Macs define services.
PAM
Linux operating systems use PAM (Pluggable Authentication Model).
The macOS equivalent of the Linux ldd command which lists the shared library dependencies of an executable or shared library is:
- otool -L /usr/bin/login
Example response:
/usr/bin/login:
/usr/lib/libbsm.0.dylib (compatibility version 1.0.0, current version 1.0.0)
/usr/lib/libpam.2.dylib (compatibility version 3.0.0, current version 3.0.0)
/usr/lib/libEndpointSecuritySystem.dylib (compatibility version 1.0.0, current version 368.140.3, weak)
/usr/lib/libSystem.B.dylib (compatibility version 1.0.0, current version 1319.100.3)
Within folder cd /etc/pam.d, file login contains:
# login: auth account password session auth optional pam_krb5.so use_kcminit auth optional pam_ntlm.so try_first_pass auth optional pam_mount.so try_first_pass auth required pam_opendirectory.so try_first_pass account required pam_nologin.so account required pam_opendirectory.so password required pam_opendirectory.so session required pam_launchd.so session required pam_uwtmp.so session optional pam_mount.so
Each operating sytem has its own set, including use of file pam_env.conf within folder /etc/security.
Root Kits
Leak of documents from CIA’s Embedded Development Branch (EDB) reveal they developed an OS X “implant” (called DerStarke) that includes a kernel code injection module dubbed Bokor and an EFI (Extensible Firmware Interface) persistence module (called DarkMatter). The rootkits targeting firmware on Apple Macbook laptops*
The low-level firmware runs before the operating system and initializes the various hardware components during the system boot process. That allows the rootkit to survive major system updates and even reinstallations.
A module for Intel Security’s CHIPSEC open-source framework finds rogue EFI binaries. CHIPSEC is a set of command-line tools which use low-level interfaces to analyze a system’s hardware, firmware, and platform components. It can be run from Windows, Linux, macOS, or an EFI shell. The new CHIPSEC module allows the user to take a clean EFI image immediately after purchase from the computer manufacturer, extract its contents and build a clean list of the binary files inside. It can then compare that list against the system’s current EFI or against an EFI image previously extracted from a system. If the tool finds any binary files that don’t match the clean EFI list, it’s possible that the firmware has been infected. The rogue files are listed and can then be further analyzed.
See https://support.apple.com/en-us/HT201518
More on macOS
This is one of a series on macOS:
- MacOS Setup step-by-step, with automation
- MacOS Hardware and accessories
- MacOS dotfiles for System Preferences setup automation
- MacOS Boot-up
- MacOS Keyboard tricks
- MacOS Terminal Tips and Tricks
- Text editors and IDEs on MacOS
- MacOS Xcode.app and CommandTools (gcc)
- MacOS Command-line utilities
- Applications on MacOS
- 1password on MacOS
- Manage Disk Space on MacOS
- Screen capture on MacOS
- MacOS iPhone integration
- Linux and Windows on Apple MacOS
- Packer create Vagrant Windows image
- Python on MacOS
- Maven on MacOS
- Ruby on MacOS
- Node on MacOS installation
- Java on MacOS
- Scala ecosystem

