Enterprise data risks and vulnerabilities and how to mitigate them with controls
Overview
- Glossary
- Jobs & Occupations
- Security Architecture leadership
- Security Processes
- Security Engineer
- Zero Trust Security Approach
- Quantitative risk analysis:
- Vendor Compliance
- Microsoft Cybersecurity Reference Architecture
- Adobe Common Control Framework
- CRR (Cyber Resilience Review)
- HITRUST Common Security Framework
- ISO 22301
- ISO 27002
- ISO/IEC 15288:2015
- Center for Internet Security (CIS)
- Change management
- Docker CIS
- NIST NVD CVE
- CMMC
- NIST documents
- DISA SIST & SRG
- Source of Vulnerabilities
- International
- US Laws
- Reporting
- Data Classification
- Defense in Depth
- Security Testing
- RFCs
- Credential Rotation Lifecycle
- Security Engineer
- Attackers
- Attacks
- DREAD Risk ratings
- CVSS
- CIS (Center for Internet Security)
- Models & Lifecycles
- Security Models
- TCB RMC
- Cryptography
- Network Protocols
- IAM
- SSO
- Access Control IAAA
- Type 2 Have Smart Cards
- Networking: OSI (Open System Interconnect)
- Acceptable Use Policy (AUP)
- Incident Response (DFIR)
- Podcasts
- Sharing groups
- Discord channels
- Security Bootcamps Projects
- Masters Degrees
- Harvard CS50
- Resources
- More on Security
Here are my notes on resources for Cyber Security, which is a vast field. But nevertheless all the info is on this single page to make for easy searching.
“Security is always excessive until it’s not enough.” –-Robbie Sinclair
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
Glossary
- RFC 4949 - Internet Security Glossary
- SANS Glossary
- PROTIP: My Quizlet of Cyber Security Aconyms
- PROTIP: Acronyms here are in my 444 item Quizlet flashcards for Cyber Security for you to study more efficiently.
- Dean Bushmiller has a great one for his students at $49/month 123oreilly.com
REMEMBER:
- Guidelines - recommended actions to follow
- Policies - general statements from management
- Standards - specific mandatory security controls
- Procedures - step-by-step instructions
- A threat is a potential harmful incident.
- A threat agent (a malicious actor) is an individual or group that can manifest a threat.
-
A threat event is a specific instance of a threat
- A vulnerability is a (potentially exploitable) weakness where there is the absence of a countermeasure in place.
- An exposure is an instance of being subjected or exposed to losses from a threat.
- A trigger is an event that indicates that a risk has occurred or is about to occur.
-
Enticements are apparent flaws deliberately made available for penetration and exploitation.
- Attacks are attempts to violate an organization’s security or privacy
- An exploit is when a threat agent successfully takes advantage of a vulnerability
- Likelihood (of occurrence) is a weighted factor that a given threat agent is capable of exploiting a given vulnerability
- Level of risk before treatment is the inherent risk
- A breach is an attack that has been successful in reaching its goal. NIST 900-53 defines “a breach results in the loss of control, compromise, unauthorized disclosure, unauthorized acquisition, or a similar occurrence where a person other than an authorized user accesses or potentially accesses personally identifiable information or an authorized user accesses or potentially accesses such information for other than authorized purposes. Incident response training emphasizes the obligation of individuals to report both confirmed and suspected breaches invlving information in any medium or form, including paper, oral, and electronic. Incident response training includes tabletop exercises that simulate a breach.”
- Impact is the magnitude of harm caused by a threat source
Jobs & Occupations
PROTIP: SANS created a framework describing skills – used to identify training and certifications for cybersecurity role.
- Oversee and Govern (OV) - Provides leadership, management, direction, or development and advocacy so the organization may effectively conduct cybersecurity work.
-
Security Provisionals (SP) - (Architectes?) Conceptualizes, designs, procures, and/or builds secure information technology (IT) systems, with responsibility for aspects of system and/or network development.
- Collect and Operate (CO) - Provides specialized denial and deception operations and collection of cybersecurity information that may be used to develop intelligence.
-
Operate and Maintain (OM) - Provides the support, administration, and maintenance necessary to ensure effective and efficient information technology (IT) system performance & security.
- Analyze (AN) - Performs highly-specialized review and evaluation of incoming cybersecurity information to determine its usefulness for intelligence.
- Investigate (IN) - Investigates cybersecurity events or crimes related to information technology (IT) systems, network, and digital evidence.
-
Protect and Defend (PR) - Identifies, analyzes, and mitigates threats to internal information technology (IT) systems and/or networks.
- Industrial Control Systems (ICS) - ICS security is a security framework that protects industrial control systems against accidental or intentional risks safeguards critical infrastructures.
Security Architecture leadership
- Security Identities and Access led by a Chief HR/People Officer (CPO)
- Security Operations (SecOps/SOC) led by a Chief Security Officer (CSO)
- Infrastructure and development Security led by a Chief Information Security Officer (CISO)
-
Data Security & Governance led byy a Chief Data Officer (CDO)
- IoT & OT (operational technology) security led by a Chief Information Officer (CIO)
- Spend/Billings led by a Chief Financial Officer (CFO)
Security Processes
- Asset management
- Assets inventory
- Assets acceptable use and return policies
- Assets ownership
- Assets classification
- Assets labeling Assets handling
- Media management
- Configuration management
- NIST SP 800-128
- Configuration Item
- Configuration Management Database (DMD
- Security-focused configuration management (SecCM)
- Mobile device management (MDM)
- Restrict user application access
- Limit or prevent access to organization assets
- Monitor, alert and report on policy violation
- Encrypt data
- Remote wipe
- Remote lock
- DLP
- Patch management
- Identify the systems (workflow)
- Prioritize the systems
- Evaluate countermeasures
- Start change process
- Update configuration records
- Vulnerability management
- Identification
- Analysis & Prioritization
- Remediation
Security Engineer
Here are “Essential Job Functions” based on various job descriptions:
- Apply established and ad hoc processes and techniques to identify, validate, prioritize, and track security risks.
- Identify uncontrolled risks and recommend control improvements.
- Proactively identify security requirement deficiencies.
- Engage business and technology personnel to elicit security requirements.
- Architect and design security control systems to address requirements.
- Operate and monitor established security controls.
- Identify control deficiencies and make appropriate recommendations.
- Ensure that controls are operating effectively; resolve operating discrepancies.
- Review, triage, and prioritize control output.
- Take appropriate action to resolve security discrepancies.
- Identify, evaluate, and recommend new security technologies, techniques, and tools.
-
Define, review, and promote information security policies, standards, guidelines, and procedures.
- As compliance subject matter expert, enforce and monitor compliance with internal and external regulations, policies, and standards.
- Establish and promote strategies to ensure that compliance is effectively monitored and enforced.
-
Lead/Co-lead internal process improvement initiatives. Provide feedback on processes by offering suggestions.
- Mentor and supervise junior staff in project-level tasks.
- Assist with adherence to technology policies and comply with all security controls.
Education/Experience Requirements:
- Experience must include direct experience in several of the key areas listed: securing networks and systems architecture, design and implementation, secure software assurance, intrusion detection, defense and incident response, security configuration management, access controls design and implementation and security policy and standards development.
- In-depth knowledge of communications protocols (HTTP/HTTPS, SSL/TLS, OAuth, JWT, SAML).
-
Experience with Cyber Security tools, including: Configuration Assessment, Log Aggregation, Integrity Verification, Web Application Security Testing, Network Access Control System, Network Intrusion prevention systems, and Endpoint Security Solutions.
- Strong written and verbal technical communication skills.
- Demonstrated ability to develop effective working relationships that improved the quality of work products.
- Should be well organized, thorough, and able to handle competing priorities.
- Ability to maintain focus and develop proficiency in new skills rapidly.
- Ability to work in a fast-paced environment.
- In-depth knowledge of more than one Information Security principle and discipline.
Zero Trust Security Approach
We adopt a “Zero Trust Architecture” (ZTA) cybersecurity paradigm.
Why? Inadequate access controls can lead to data exfiltration, unauthorized access, lateral movement and/or the introduction of malware into an environment. Consequences of that include damage to brand/reputation, fines, erosion of customer confidence, delays in service delivery due to unplanned downtime, lengthened approval processes and impacts to partner relationships.
So rather than depending solely on using VPNs to access static firewalls to protect all resources within an on-premises network, an end-to-end, “Zero Trust” approach is necessary for operating in public networks.
The term was first popularized by Forrester industry analyst John Kindervag in 2010. In 2020 NIST published 50-page PDF: Special Publication SP800-207. It noted that “Industry has not yet coalesced around a single set of terms or concepts to describe ZTA components and operations.”
“Zero Trust” means that we “assume breach”. So network and access are segregated. Each DAAS (Data, Assets, Applications, Services) resource only interacts with entitites which are authenticated and authorized by dynamic fine-grained “least privilege” policies, on a per-session basis. Both server resources and endpoints which request services (user, machine, app, etc.) each must also prove its identity, using mutual TLS (mTLS).
“Zero Trust” needs to be all-encompassing in its vigilance. The current state of assets, network infrastructure, and communications are continuously collected for forensics in case of breach and for analysis to improve the “security posture” of each device, user, and enterprise as a whole.
Because service accounts and authorization are tightly coupled with the application, it often makes sense to set up identities and policies as part of the application infrastructure deployment. Delegating this authority to the development team allows it to iterate quickly on application development (the DevSecOps model).
The Cybersecurity Enhancement Act of 2014 (CEA), aka Public Law No. 113-274, provide a voluntary public-private partnership to improve cybersecurity.
Quantitative risk analysis:
REMEMBER:VIDEO:
Asset Value (AV) x Exposure Factor (EF) = Single Loss Expectancy (SLE).
Annualized Rate of Occurrence (ARO) X Single Loss Expectancy (SLE) = Annual Loss Expectancy (ALE).
Cost/benefit of implementing a particular safeguard, where
ALE is the annual loss expectancy =
(ALE before safeguard) – (ALE after safeguard) – (annual cost of safeguard)
Residual risk = total risk – countermeasures.
Impact from loss of confidentiality:
- Fines and criminal lawsuits based on information protected by privacy laws
- Civil suits against the enterprise
- Loss of public confidence (brand value)
- Loss of competitive advantage
- Interference with national security
CIA triad tenents: +IAAA
- Confidentiality vs. Disclosure (IPSec encryption in transit, social engineering)
- Integrity vs. Alteration (shared among authorized persons or organizations)
-
Availability vs. Destruction (RAID-5, DDoS)
- Accountability (auditing)
Confidentiality
Elements of Confidentiality:
- Sensitivity
- Discretion
- Criticality
-
Concealment
- Secrecy
- Privacy
- Seclusion
- Isolation
Privacy Threshold Assessment is used to identify PII and determine how to treat the data.
OCTAVE (Operationally Critical Threat, Asset, and Vulnerability Evaluation) developed at Carnegie Mellon SEI.
Cloud Security Posture Management (CSPM) monitors continuously identifies and remediaties cloud infrastructure risks in each cloud service using application programming interfaces (APIs) configuration data against compliance benchmarks. For example, they can ensure logs are being gathered from host operating systems and the network (NetFlow), and that API event logging is turned on.
The newer acronym CIEM (Cloud Infrastructure Entitlements Management) was coined by ermetic.com for their product which ensures that identities (both human and machine) do not have excessive permissions that can be exploited by threat actors or malicious insiders.
- Identify risk
- Factors for estimating likelihood
- Factors for estimating impact
- Determine Severity for risk
- Deciding what do fix
Zero-Trust Jericho Commandments
https://collaboration.opengroup.org/jericho/commandments_v1.2.pdf define the 11 areas and principles that must be observed when planning for a de-perimeterized future in cloud environments.
Vendor Compliance
aws.Amazon.com/Compliance
/Programs covers security requirements in Canada, Asia Pacific, and Europe.

Microsoft Cybersecurity Reference Architecture
VIDEO Distilling Infographic in PowerPoint: Microsoft Azure Cybersecurity Reference Architecture VIDEO MCRA video by Mark Simos
Jobs to be done
From https://aka.ms/SecurityRoles:
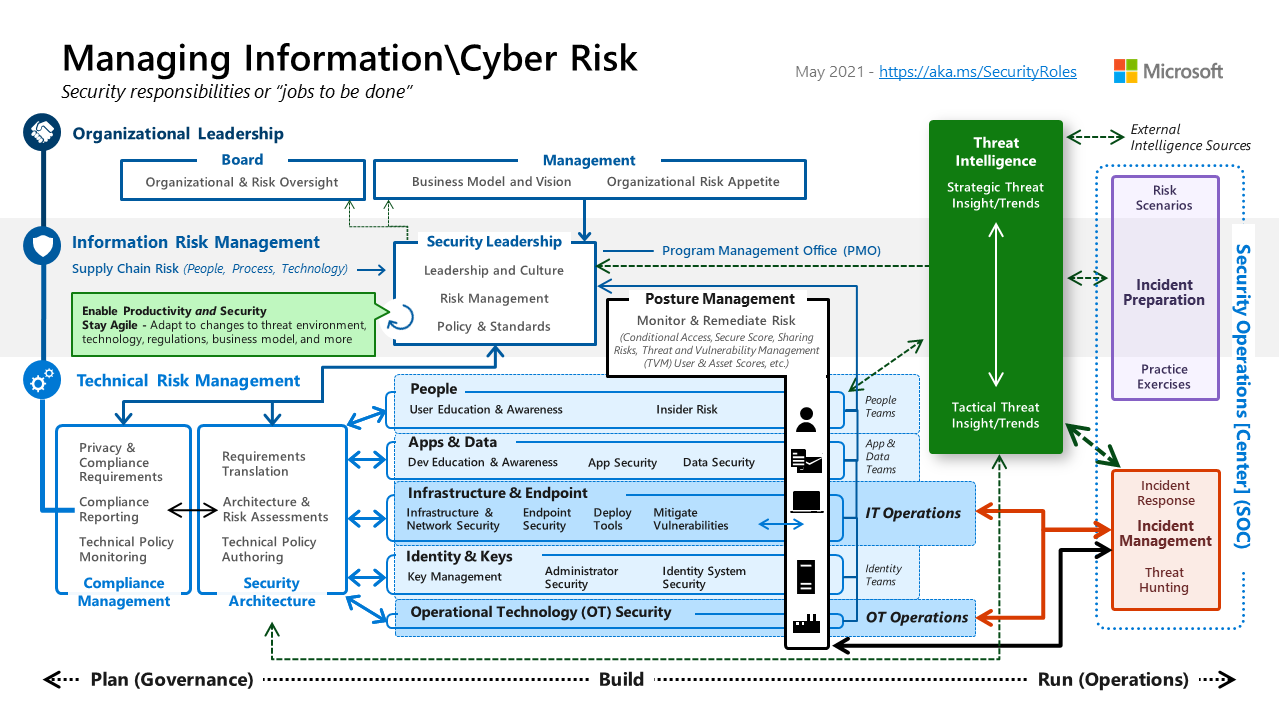
Microsoft’s Cybersecurity Reference Architecture (MCRA) is a technology agnostic framework that provides a blueprint for implementing a comprehensive, end-to-end cybersecurity solution. It is a companion to the Microsoft Cloud Adoption Framework for Azure and the Microsoft Azure Well-Architected Framework.
Microsoft’s cybersecurity capabilities and technologies are described in
Microsoft Security Documentation site and
Microsoft’s Security Adoption Framework (SAF)
(mcra-december-2023.pptx)
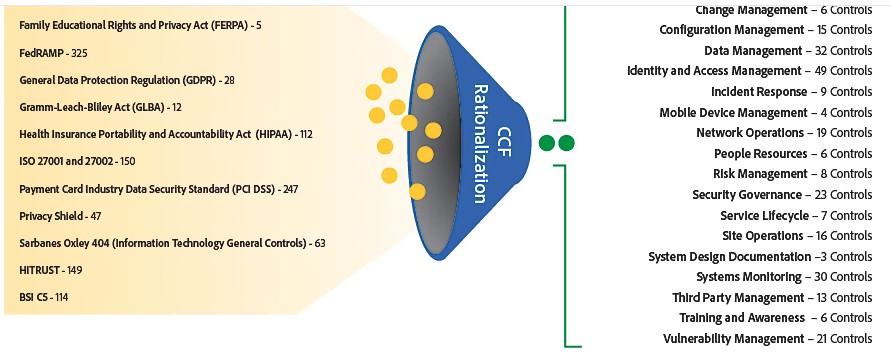
Adobe Common Control Framework
Adobe open-sourced its own comprehensive Common Control Framework.
Like the CAIQ, it aggregates questions and answers for several audit requirements: ISO 27001/27002, SOC, FedRAMP, PCI DSS, GLBA, FERPA, etc. Download the pdf.
- Asset management
- Business Continuity
- Backup Management
- Configuration Management
- Change Management
- Data Management
- Identity and Acccess Management
- Incident Response
- Mobile Device Management
- Network Operations
- People Resources
- Risk Management
- System Design Documentation
- Security Governance
- Service Lifecycle
- Systems Monitoring
- Site Operations
- Training and Awareness
- Third Party Management
- Vulnerability Management
CRR (Cyber Resilience Review)
The CRR is a lightweight assessment method created by the U.S. Department of Homeland Security (DHS) for evaluating the cybersecurity and service continuity practices of critical infrastructure owners and operators in cybersecurity, operations, physical security, and business continuity. It’s also used by the governments of Japan, Israel, and Italy, among others.
The CRR assessment consists of 299 questions over 10 domains, typically delivered in a 12 - 16 hour workshop led by a qualified facilitator over two consecutive days. This workshop yields a 176-page analysis and report.
CSF v2.0 intro for release Winter 2024.
HITRUST Common Security Framework
HITRUST Common Security Framework includes, harmonizes, and cross-references existing, globally recognized standards, regulations, and business requirements, including ISO, EU GDPR, NIST, and PCI.
It’s a part of the 2009 ARRA (American Recovery and Reinvestment Act).
Through a validated assessment performed by the Health Information Trust Alliance (HITRUST), a leading security and privacy standards development and accreditation organization, Office 365 is certified to the objectives specified in the NIST CSF.
ISO 22301
Business Continuity
ISO 27002
https://iso27001security.com
ISO Code of practice for information security controls defines 114 controls grouped into 14 categories.
REMEMBER:
-
ISO/IEC 27002 Controls (Counter-measures) of ISMS (Information Security Management System) lists:
- ISO/IEC 27005 addresses risk management
- ISO/IEC 27007 addresses auditing [as in James Bond]
- ISO/IEC 27012 addresses controls (counter-measures)
- ISO/IEC 27033 addresses network security
- ISO/IEC 27034 addresses application security
-
ISO/IEC 27037 addresses digital evidence guidelines
- ISO/IEC 27011 addresses telecommunications organization guidelines
- ISO/IEC 27015 addresses financial organization guidelines
- ISO/IEC 27799 addresses health organization guidelines
The ISO/IEC 27002:2013 standard is a 92-page document available for purchase from the ISO website. It is a code of practice for information security controls. It provides guidelines for organizational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organization’s information security risk environment(s).
| Ref. | Deliverable |
|---|---|
| - | Project Plan (Excel sheet) |
| 4.1 | External issues (4.1) |
| 4.1 | Internal Issues (4.1) |
| 4.2 b) | Requirements of interested parties (4.2 b)) |
| 4.3 | Scope of the ISMS (4.3) |
| 6.2 | Information security objectives (6.2) |
| 5.2 | Information security policy (5.2) |
| A.5.12 | Information classification policy (A.5.12) |
| A.5.9 | Inventory of assets (A.5.9) |
| 6.1.2 a) | Risk assessment criteria (6.1.2 a)) |
| 6.1.2 a) | Risk acceptance criteria (6.1.2 a)) |
| 6.1.2 | Risk assessment process (6.1.2) |
| 6.1.3 | Risk treatment process (6.1.3) |
| 7.2.a | Job Descriptions (Evidence of competence (7.2.a) |
| 7.2.b | Evidence of competence (7.2.b) |
| 7.2.c | Training records (7.2.c) |
| 7.2.d | Performance records (7.2.d) |
| 8.2 | Threats (8.2) |
| 8.2 | Existing controls (8.2) |
| 8.2 | Vulnerabilities in relation to assets, controls, and threats (8.2) |
| 8.2 | Incident scenarios (8.2) |
| 8.2 | Risks with risk levels assigned (8.2) |
| 8.2 | Prioritized risks (8.2) |
| 8.3? | Statement of Applicability (SoA) (6.1.3) |
| 8.3 | Risk treatment plan (8.3) |
| 9.1 | Information security metrics (9.1) |
| 9.2 | Internal Audit programme (9.2) |
| 9.2 | Internal Audit results (9.2) |
| 9.3 | Results of management reviews (9.3) |
| 10.2 f) | Nature of the nonconformities and any subsequent actions taken (10.2 f)) |
| 10.2 g) | Results of any corrective action (10.2 g)) |
Policies:
- Supplier Security Policy
- Password Policy
- Backup Policy
- Access Control Policy
- Clear Desk and Clear Screen Policy
- Remote Work Policy
- Information Transfer Policy
- Acceptable Use Policy
- Information Classification Policy
- Information Security Policy
- Cryptography Policy
- Mobile Device Policy
- Secure Development Policy
Standards:
- Change Management Standard
- Installation of Software Standard
- Working in Secure Areas - Physical Security Standard
- Operating Procedures
- Intellectual Property Rights Protection
- Information Security Response
- Information Handling
- Control of Documented Information
- Labeling of Information
- Cryptographic Key Management
-
Secure Disposal
- Patch Management Standard
-
Vulnerability Management Standard
- Network Security Standard
- Server Security Standard
Processes:
- Security Testing Process
- Disciplinary Process
- Information Security Incident Management Process
- Risk Treatment Process
- Risk Assessment Process
Key information assets:
- Employee Data: Personal information of employees, such as contact details, performance evaluations, compensation data, and training records.
-
Financial Data: Financial records and reports, including revenue, expenses, budgeting, forecasts, and financial analysis.
- Research and Development Data: Information related to ongoing R&D projects, including experimental results, analysis, and progress reports.
- Intellectual Property: Patents, trademarks, copyrights, and trade secrets related to the design, manufacturing, and improvement of their heavy machinery and equipment.
-
Technical Designs and Specifications: Detailed drawings, schematics, and specifications for the company’s products, including mechanical, electrical, and software components.
- Supplier Data: Information about suppliers, including contact details, agreements, pricing, and delivery schedules.
-
Production Data: Information about manufacturing processes, production schedules, quality control data, and equipment maintenance records.
- Sales and Marketing Data: Market research, competitor analysis, sales forecasts, and marketing campaign data. Legal and Compliance Data: Documents and records related to regulatory compliance, contracts, and legal disputes.
- Customer Data: Personal and business information about customers, including contact details, purchase history, preferences, and customer feedback.
https://hightable.io/top-10-iso-27001-companies-and-iso-27001-certification-bodies/
Stuart A. Barker (iso27001ninja)
To be certified a Lead Auditor of ISO 27001, ….
To be certified a Lead Implementor of ISO 27001, one must be a member of CIS and pass four exams online, each $100 to pass 75% of 65 questions over 70 minutes.
CIS CICRA, 27001 Lead Implementer, CICA, ISO 27001 Lead Auditor, CBCS, CBCA, and CBCM certifications.
-
RM101 as covered in “Policy Workshop: ISO 3100 Enterprise Risk Management” course.
-
ISMS101 as covered in “Policy Workshop: ISO 27001 Information Security Mgmt” course.
-
ISMS102 as covered in “Policy Workshop: ISO 27001 Information Security Mgmt” course.
-
ISMS103 as covered in “ISO 27001 Lead Auditor” course.
Valid for 3 years.
https://www.strongdm.com/blog/iso-27001-vs-soc-2
ISO/IEC 15288:2015
Four categories of processes:
- Agreement processes, including acquisition and supply
- Organizational project-enabling processes, including infrastructure management, quality management, and knowledge management
- Technical management processes, including project planning, risk management, configuration management, and quality assurance
- Technical processes, including system requirements definition, system analysis, implementation, integration, operation, maintenance, and disposal
Center for Internet Security (CIS)
“The Center for Internet Security (CIS) is a community of users, vendors and subject matter experts working together through consensus collaboration to deliver a framework that provides a starting point for organizations interested in implementing …
-
CIS creates hardened versions of images running on various clouds:
https://www.cisecurity.org/benchmark/amazon_web_services/
https://www.cisecurity.org/blog/cis-hardened-images-now-in-microsoft-azure-marketplace/
-
Download the CIS Controls poster (CIS-Controls-V7-Poster.pdf) from:
https://www.cisecurity.org/white-papers/cis-controls-v7-poster
-
Download CIS Benchmark pdf files for each product (Amazon Linux, MongoDB, etc.) from:
https://www.cisecurity.org/cis-benchmarks
PROTIP: View the “Distribution Independent Linux Benchmark” first because Benchmarks specific to a Linux distribution repeat much of its contents.
-
Download and review “Measures and Metrics” pdf and excel:
https://www.cisecurity.org/white-papers/cis-controls-v7-measures-metrics/
CIS Security Benchmarks for Linux
These are common asset items to be protected, as addressed by CIS Benchmarks across several Linux distributions:
-
Initial setup 1.1. Filesystem Configuration 1.2. Configure Software Updates 1.3. Filesystem Integrity Checking 1.4. Secure Boot Settings 1.5. Additional Processing Hardening 1.6. Mandatory Access Control 1.7. Warning Banners
-
Services 2.1. inetd Services 2.2. Special Purpose Services 2.3. Service Clients
-
Network Configuration 3.1. Network Parameters (Host Only) 3.2. Network Parametres (Host and Router) 3.3. IPv6 3.4. TCP Wrappers 3.5. Uncommon Network Protocols 3.6. Firewall Configuration
-
Logging and Auditing [MINDMAP] 4.1. Configure System Accounting (auditd) 4.2. Configure Logging
-
Access, Authentication, and Authorization 5.1. Configure cron 5.2. SSH Server Configuration 5.3. Configure PAM 5.4. User Accounts and Environment
-
System Maintenance 6.1. System File Permissions 6.2. User and Group Settings
Under each sub-item above are specific recommendations with Bash script commands to implement them out and commands to audit whether they have been implemented. That code is incorporated in the “CIS-CAT Lite (CIS Configuration Assessment Tool)” below.
Items in the Benchmark described as (Scored) indicates when compliance with the given recommendation impacts the assessed target’s benchmark score. Failure to comply with “Scored” recommendations will decrease the final benchmark score. Compliance with “Scored” recommendations will increase the final benchmark score. Compliance on “(Unscored)” items make no difference to the total score.
Compliance scores go to 100.
“CIS Controls Measures and Metrics for Version 7” Excel spreadsheet (file CIS-Controls-Version-7-cc.xlsx) contains 170 sub-controls applicable to these 20 controls (“best practices”) described by the CIS Controls Companion Guide:
file CIS-Controls-Version-7-cc.pdf from https://learn.cisecurity.org/20-controls-download
Linux permissions
https://h4cker.org/chmod Discretionary Access Control
In each set: Owner - Group - Other
-rw–r–r–
Read - Write - eXecute:
- 000 = 0
- 001 = 1
- 010 = 2
-
100 = 4
- 101 = 5
- 110 = 6
- 111 = 7
LSM = Linux Security Module
Basic:
- Inventory and Control of Hardware Assets
- Inventory and Control of Software Assets
- Continuous Vulnerability Management
- Controlled Use of Administrative Privileges
- Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations and Servers
-
Maintenance, Monitoring and Analysis of Audit Logs
Foundational:
- Email and Web Browser Protections
- Malware Defenses
- Limitation and Control of Network Ports, Protocols and Services
- Data Recovery Capabilities
- Secure Configuration for Network Devices, such as Firewalls, Routers and Switches
- Boundary Defense
- Data Protection
- Controlled Access Based on the Need to Know
- Wireless Access Control
-
Account Monitoring and Control
Organizational:
- Implement a Security Awareness and Training Program
- Application Software Security
- Incident Response and Management
- Penetration Tests and Red Team Exercises
The AWS (Amazon Web Services) Well Architected Framework books cover many of the above, but at a rather high-level.
Below is an approach that can be used for Gap Analysis of what needs to be done to protect hardware, software, and data assets.
CIS Sub-Controls alphabetically by Sensor
A. Active Device Discovery System
- 1.1 Utilize an Active Discovery Tool
B. Anti-Spam Gateway
- 7.8 Implement DMARC and Enable Receiver-Side Verification
- 7.9 Block Unnecessary File Types
- 7.10 Sandbox All Email Attachments
C. Application Aware Firewall
- 9.5 Implement Application Firewalls
D. Asset Inventory System
- 1.4 Maintain Detailed Asset Inventory
- 1.5 Maintain Asset Inventory Information
- 1.6 Address Unauthorized Assets
E. Backup / Recovery System
- 10.1 Ensure Regular Automated Back Ups
- 10.2 Perform Complete System Backups
- 10.3 Test Data on Backup Media
- 10.4 Ensure Protection of Backups
- 10.5 Ensure Backups Have At least One Non-Continuously Addressable Destination
F. Data Inventory / Classification System
- 13.1 Maintain an Inventory Sensitive Information
- 13.2 Remove Sensitive Data or Systems Not Regularly Accessed by Organization
- 14.5 Utilize an Active Discovery Tool to Identify Sensitive Data
G. Dedicated Administration Systems
- 4.6 Use of Dedicated Machines For All Administrative Tasks
- 11.6 Use Dedicated Machines For All Network Administrative Tasks
- 11.7 Manage Network Infrastructure Through a Dedicated Network
H. DNS Domain Filtering System
- 7.6 Log all URL requests
- 7.7 Use of DNS Filtering Services
- 8.7 Enable DNS Query Logging
I. Endpoint Protection System
- 8.1 Utilize Centrally Managed Anti-malware Software
- 8.2 Ensure Anti-Malware Software and Signatures are Updated
- 8.4 Configure Anti-Malware Scanning of Removable Devices
- 8.6 Centralize Anti-malware Logging
- 13.7 Manage USB Devices
- 13.8 Manage System’s External Removable Media’s Read/write Configurations
- 13.9 Encrypt Data on USB Storage Devices
J. Host Based Data Loss Prevention (DLP) System
- 14.7 Enforce Access Control to Data through Automated Tools
- 14.8 Encrypt Sensitive Information at Rest
Egress monitoring occurs when an organization monitors the outbound flow of information from one network to another. The most popular form of egress monitoring is carried out using firewalls that monitor and control outbound traffic. Continuous monitoring and Continuous Monitoring as a Service (CMaaS) are not specific enough to answer this question. Any logging and monitoring activities should be part of an organizational continuous monitoring program. The continuous monitoring program must be designed to meet the needs of the organization and implemented correctly to ensure that the organization’s critical infrastructure is guarded. Organizations may want to look into CMaaS solutions deployed by cloud service providers.
K. Host Based Firewall
- 9.4 Apply Host-based Firewalls or Port Filtering
L. Identity & Access Management System
- 16.1 Maintain an Inventory of Authentication Systems
- 16.2 Configure Centralized Point of Authentication
- 16.4 Encrypt or Hash all Authentication Credentials
- 16.5 Encrypt Transmittal of Username and Authentication Credentials
- 16.6 Maintain an Inventory of Accounts
- 16.7 Establish Process for Revoking Access
- 16.8 Disable Any Unassociated Accounts
- 16.9 Disable Dormant Accounts
- 16.10 Ensure All Accounts Have An Expiration Date
- 16.11 Lock Workstation Sessions After Inactivity
M. Incident Management Plans
- 19.1 Document Incident Response Procedures
- 19.2 Assign Job Titles and Duties for Incident Response
- 19.3 Designate Management Personnel to Support Incident Handling
- 19.4 Devise Organization-wide Standards for Reporting Incidents
- 19.5 Maintain Contact Information For Reporting Security Incidents
- 19.6 Publish Information Regarding Reporting Computer Anomalies and Incidents
- 19.7 Conduct Periodic Incident Scenario Sessions for Personnel
- 19.8 Create Incident Scoring and Prioritization Schema
N. Log Management System / SIEM
- 1.3 Use DHCP Logging to Update Asset Inventory
- 4.8 Log and Alert on Changes to Administrative Group Membership
- 4.9 Log and Alert on Unsuccessful Administrative Account Login
- 6.2 Activate audit logging
- 6.3 Enable Detailed Logging
- 6.4 Ensure adequate storage for logs
- 6.5 Central Log Management
- 6.6 Deploy SIEM or Log Analytic tool
- 6.7 Regularly Review Logs
- 6.8 Regularly Tune SIEM
- 8.8 Enable Command-line Audit Logging
- 14.9 Enforce Detail Logging for Access or Changes to Sensitive Data
- 16.12 Monitor Attempts to Access Deactivated Accounts
- 16.13 Alert on Account Login Behavior Deviation
O. Multi-Factor Authentication System
- 4.5 Use Multifactor Authentication For All Administrative Access
- 11.5 Manage Network Devices Using Multi-Factor Authentication and Encrypted Sessions
- 12.11 Require All Remote Login to Use Multi-factor Authentication
- 16.3 Require Multi-factor Authentication
P. Network Based Data Loss Prevention (DLP) System
- 13.3 Monitor and Block Unauthorized Network Traffic
- 13.5 Monitor and Detect Any Unauthorized Use of Encryption
Q. Network Based Intrusion Detection System (NIDS)
- 12.6 Deploy Network-based IDS Sensor
R. Network Based Intrusion Prevention System (IPS)
- 12.7 Deploy Network-Based Intrusion Prevention Systems
S. Network Device Management System
- 11.1 Maintain Standard Security Configurations for Network Devices
- 11.2 Document Traffic Configuration Rules
- 11.3 Use Automated Tools to Verify Standard Device Configurations and Detect Changes
- 11.4 Install the Latest Stable Version of Any Security-related Updates on All Network Devices
- 12.8 Deploy NetFlow Collection on Networking Boundary Devices
- 15.1 Maintain an Inventory of Authorized Wireless Access Points
- 15.7 Leverage the Advanced Encryption Standard (AES) to Encrypt Wireless Data
- 15.8 Use Wireless Authentication Protocols that Require Mutual, Multi-Factor Authentication
- 15.10 Create Separate Wireless Network for Personal and Untrusted Devices
T. Network Firewall / Access Control System
- 2.10 Physically or Logically Segregate High Risk Applications
- 12.1 Maintain an Inventory of Network Boundaries
- 12.3 Deny Communications with Known Malicious IP Addresses
- 12.4 Deny Communication over Unauthorized Ports
- 12.9 Deploy Application Layer Filtering Proxy Server
- 12.10 Decrypt Network Traffic at Proxy
- 13.4 Only Allow Access to Authorized Cloud Storage or Email Providers
- 14.1 Segment the Network Based on Sensitivity
- 14.2 Enable Firewall Filtering Between VLANs
- 14.3 Disable Workstation to Workstation Communication
U. Network Level Authentication (NLA)
- 1.7 Deploy Port Level Access Control
V. Network Packet Capture System
- 12.5 Configure Monitoring Systems to Record Network Packets
W. Network Time Protocol (NTP) Systems
- 6.1 Utilize Three Synchronized Time Sources
X. Network URL Filtering System
- 7.4 Maintain and Enforce Network-Based URL Filters
- 7.5 Subscribe to URL-Categorization service
Y. Passive Device Discovery System
- 1.2 Use a Passive Asset Discovery Tool
Z. Patch Management System
- 3.4 Deploy Automated Operating System Patch Management Tools
- 3.5 Deploy Automated Software Patch Management Tools
AA. Penetration Testing Plans
- 20.1 Establish a Penetration Testing Program
- 20.2 Conduct Regular External and Internal Penetration Tests
- 20.3 Perform Periodic Red Team Exercises
- 20.4 Include Tests for Presence of Unprotected System Information and Artifacts
- 20.5 Create Test Bed for Elements Not Typically Tested in Production
- 20.6 Use Vulnerability Scanning and Penetration Testing Tools in Concert
- 20.7 Ensure Results from Penetration Test are Documented Using Open, Machine-readable Standards
- 20.8 Control and Monitor Accounts Associated with Penetration Testing
AB. Privileged Account Management System
- 4.1 Maintain Inventory of Administrative Accounts
- 4.2 Change Default Passwords
- 4.3 Ensure the Use of Dedicated Administrative Accounts
- 4.4 Use Unique Passwords
AC. Public Key Infrastructure (PKI)
- 1.8 Utilize Client Certificates to Authenticate Hardware Assets
AD. SCAP Based Vulnerability Management System
- 3.1 Run Automated Vulnerability Scanning Tools
- 3.2 Perform Authenticated Vulnerability Scanning
- 3.3 Protect Dedicated Assessment Accounts
- 3.6 Compare Back-to-back Vulnerability Scans
- 3.7 Utilize a Risk-rating Process
- 5.5 Implement Automated Configuration Monitoring Systems
- 9.1 Associate Active Ports, Services and Protocols to Asset Inventory
- 9.2 Ensure Only Approved Ports, Protocols and Services Are Running
- 9.3 Perform Regular Automated Port Scans
AE. Secure Coding Standards
- 18.1 Establish Secure Coding Practices
- 18.2 Ensure Explicit Error Checking is Performed for All In-house Developed Software
- 18.3 Verify That Acquired Software is Still Supported
- 18.4 Only Use Up-to-date And Trusted Third-Party Components
- 18.5 Use Only Standardized and Extensively Reviewed Encryption Algorithms
- 18.9 Separate Production and Non-Production Systems
Secure Coding Practices Specialization” consists of 4 courses on Coursera:
by Matthew Bishop, PhD at UCDavis
AF. Software Application Inventory
- 2.1 Maintain Inventory of Authorized Software
- 2.2 Ensure Software is Supported by Vendor
- 2.3 Utilize Software Inventory Tools
- 2.4 Track Software Inventory Information
- 2.5 Integrate Software and Hardware Asset Inventories
- 2.6 Address unapproved software
AG. Software Vulnerability Scanning Tool
- 18.7 Apply Static and Dynamic Code Analysis Tools: SonarQube, Fortify, .NET, SpotBugs, IBM AppScan, Breakman
- 18.8 Establish a Process to Accept and Address Reports of Software Vulnerabilities
AH. Software Whitelisting System
- 2.7 Utilize Application Whitelisting
- 2.8 Implement Application Whitelisting of Libraries
- 2.9 Implement Application Whitelisting of Scripts
- 4.7 Limit Access to Script Tools
- 7.1 Ensure Use of Only Fully Supported Browsers and Email Clients
- 7.2 Disable Unnecessary or Unauthorized Browser or Email Client Plugins
AI. System Configuration Baselines & Images
- Baselines are used assess the security state
- Procedures provide all the detailed actions that personnel are required to follow.
- Standards provide the steps necessary to achieve security.
- Guidelines provide recommended actions to carry out under certain conditions.
-
Initiation is not a component of configuration management!
- 5.1 Establish Secure Configurations
- 5.2 Maintain Secure Images
- 5.3 Securely Store Master Images
AJ. System Configuration Enforcement System
- 5.4 Deploy System Configuration Management Tools
- 7.3 Limit Use of Scripting Languages in Web Browsers and Email Clients
- 8.3 Enable Operating System Anti-Exploitation Features/ Deploy Anti-Exploit Technologies
- 8.5 Configure Devices Not To Auto-run Content
- 12.2 Scan for Unauthorized Connections across Trusted Network Boundaries
- 12.12 Manage All Devices Remotely Logging into Internal Network
- 14.4 Encrypt All Sensitive Information in Transit
- 14.6 Protect Information through Access Control Lists
- 15.2 Detect Wireless Access Points Connected to the Wired Network
- 15.4 Disable Wireless Access on Devices if Not Required
- 15.5 Limit Wireless Access on Client Devices
- 15.6 Disable Peer-to-peer Wireless Network Capabilities on Wireless Clients
- 15.9 Disable Wireless Peripheral Access of Devices
- 18.11 Use Standard Hardening Configuration Templates for Databases
AK. Training / Awareness Education Plans
- 17.1 Perform a Skills Gap Analysis
- 17.2 Deliver Training to Fill the Skills Gap
- 17.3 Implement a Security Awareness Program
- 17.4 Update Awareness Content Frequently
- 17.5 Train Workforce on Secure Authentication
- 17.6 Train Workforce on Identifying social engineering Attacks
- 17.7 Train Workforce on Sensitive Data Handling
- 17.8 Train Workforce on Causes of Unintentional Data Exposure
- 17.9 Train Workforce Members on Identifying and Reporting Incidents
- 18.6 Ensure Software Development Personnel are Trained in Secure Coding
AL. Web Application Firewall (WAF)
- 18.10 Deploy Web Application Firewalls (WAFs)
AM. Whole Disk Encryption System
- 13.6 Encrypt the Hard Drive of All Mobile Devices.
AN. Wireless Intrusion Detection System (WIDS)
- 15.3 Use a Wireless Intrusion Detection System
CIS states the status of the above Control Measures as the percentage among all the organization’s assets. But CIS doesn’t weight some parts of the organization more over others.
CIS borrows from Statistics for the area under the curve at integer levels of Standard Deviation (called a Sigma). CIS scores are named “Sigma Level One” to “Sigma Level Six”, with One at 69% or Less 31% or Less 6.7% or Less 0.62% or Less 0.023% or Less 0.00034% or Less
PROTIP: Also identify and count the base of consideration whether controls are applicable. A control may not be applicable to every item or organizational role assessed. Such are a separate set of calculation not addressed by CIS but need to be considered nonetheless to measure progress toward assessment completion.
The above form the basis for Security Implementation Plans provided by services vendors such as GuidePoint. Such plans sequence work so that technical and organizational dependencies among tasks are achieved in the appropriate order.
CIS Lite
- Make a full backup of your machine before starting this procedure.
-
Request an email to download the free “CIS-CAT Lite (CIS Configuration Assessment Tool)” at https://learn.cisecurity.org/cis-cat-lite (file CIS-CAT Lite v3.0.56.zip).
“CIS-CAT Lite provides a fast, detailed assessment of your system’s conformance with CIS Benchmarks for Windows 10, Mac OS, Ubuntu, and Google Chrome. Simply run the tool,receive a compliance score (1 - 100) and quickly view remediation steps for non-compliant settings.”
-
Expand downloaded file “CIS-CAT Lite v3.0.56.zip” to folder cis-cat-lite.
- Read the CIS-CAT Users Guide.pdf (104 pages).
- Install a JVM because the CISCAT.jar is Java-based.
- Move the folder under “temp” or other folder of your choice. Change to that directory.
-
On a Mac, open a Terminal and run CIS-CAT.sh
chmod CIS-CAT.sh ./CIS-CAT.sh
Alternately, run CIS-CAT.BAT on Windows machines.
- Click “Accept” to the pop-up GUI.
-
Click “Benchmark” to select from the pull-down.
There is also the LiteCIS-CAT Pro (for paid members) which covers CLI as well and provides more Benchmark items to scan (for a price).
-
Select “CIS_Apple_OSX_10.12_Benchmark” even if you have a more recent version.
View the misc folder benchmarks.txt to see this list:
- /benchmarks/CIS_Apple_OSX_10.12_Benchmark_v1.0.0.xml
- /benchmarks/CIS_Google_Chrome_Benchmark_v1.3.0-xccdf.xml
- /benchmarks/CIS_Microsoft_Windows_10_Enterprise_Release_1803_Benchmark_v1.5.0-xccdf.xml
- /benchmarks/CIS_Ubuntu_Linux_18.04_LTS_Benchmark_v1.0.0-xccdf.xml
- Click “Next”.
- Selet Profile Level 1.
- Notice that the report goes to your user home folder, not your present Working Directory containing the program.
- Click “Next” then “Start Assessment”, and watch the progress scroll by.
- Click “View Reports”.
- Exit the program.
- Click on the Benchmark link associated with a number in the “Fail” column.
- Assess each Fail.
Some people prefer to hold off on automatic updates until hearing if early adopters experienced problems. The risk is fending off “zero day” security issues.
2.2.2 Ensure time set is within appropriate limits
-
The default NTP server is
time.apple.com.<pre>sudo ntpdate -sv time.apple.com</pre>
However, the ntpdate tool was removed in macOS Mojave 10.14 because the
ntpd daemonsince Mavericks (10.9) and Yosemite (10.10) is no longer responsible for adjusting the time. and instead a new program pacemaker has been introduced. -
To know whether time is good or need adjustment to keep sync’d with reality:
sudo sntp -sS pool.ntp.org
Sample response:
+317.919218 +/- 0.124161 pool.ntp.org 51.81.209.232
See https://apple.stackexchange.com/questions/117864/how-can-i-tell-if-my-mac-is-keeping-the-clock-updated-properly
2.4.3 Disable Screen Sharing
CIT Fails thinking that Screen Sharing is enabled. But in System Preferences, Sharing, only Printer sharing is selected.
3.1.1 Retain system.log for 90 or more days
Edit /etc/asl.conf to change from
> system.log mode=0640 format=bsd rotate=seq compress file_max=5M all_max=50M
to
> system.log mode=0640 format=bsd rotate=utc compress file_max=5M ttl=90
Add for 3.1.2 Retain appfirewall.log for 90 or more days
> appfirewall.log mode=0640 format=bsd rotate=utc compress file_max=5M ttl=90
3.1.3 Retain authd.log for 90 or more days
sudo vim /etc/asl/com.apple.authd
Replace or edit the current setting
* file /var/log/authd.log mode=0640 compress format=bsd rotate=seq file_max=5M all_max=20M
with a compliant setting:
* file /var/log/authd.log mode=0640 format=bsd rotate=utc compress file_max=5M ttl=90
3.2 Enable security auditing
Run:
sudo launchctl load -w /System/Library/LaunchDaemons/com.apple.auditd.plist
RESPONSE: /System/Library/LaunchDaemons/com.apple.auditd.plist: service already loaded
3.5 Retain install.log for 365 or more days
subl /etc/asl/com.apple.install
Replace:
* file /var/log/install.log format='$((Time)(JZ)) $Host $(Sender)[$(PID)]: $Message'
with
* file /var/log/install.log mode=0640 format=bsd rotate=utc compress file_max=5M ttl=365
5.1.1 Secure Home Folders
Run one of the following commands in Terminal, substituting user name:
sudo chmod -R og-rwx /Users/username sudo chmod -R og-rw /Users/username
RESPONSE: chmod: Unable to change file mode on /Users/wilsonmar/projects/WM/bin/jad.readme.txt: Operation not permitted
Security Information and Event Management (SIEM) tools help analysts better understand security threats, risks, and vulnerabilities. When security analysts need to review vulnerabilities, they conduct a periodic security audit, which reviews an organization’s records, activities, and related documents.
Change management
VIDEO: REMEMBER memonic: Ricard Rarely Approves The Scheduled Deployment
- Request the change
- Review the change
- Approve/reject the change
- Test the change
- Schedule and implement the change
- Document the change
Docker CIS
https://github.com/dev-sec/cis-docker-benchmark
There is also a Docker CAT: https://www.cisecurity.org/benchmark/docker/
https://github.com/docker/docker-bench-security The Docker Bench for Security is a script that checks for dozens of common best-practices around deploying Docker containers in production.
https://blog.theodo.fr/2017/12/security-best-practices-tool-vms-including-dockers-host/
https://nvd.nist.gov/ncp/checklist/740
https://nvd.nist.gov/vuln/search for known issues
NIST NVD CVE
http://csrc.nist.gov (Computer Security Resource Center) maintains the NIST 800-53 “National Vulnerability Database” by MITRE’s CVE (Computer Vulnerabilities and Exposures) system using OSCAL (Open Security Controls Assessment Language), currently available in JSON, XML, and YAML. OVAL : (Open Vulnerability and Assessment Language) for use world-wide.
[MINDMAP] PROTIP: Many Software Component Vulnerabity scan programs (Rapid7, JFrog Xray, etc.) refer to the NVD online as the basis for scanning.
PDF: SP 800-53 Rev 5 “Security and Privacy Controls for Information Systems and Organizations”

NIST also publishes SP1800 (Cybersecurity practice guides) and the broader SP 500 (Information Technology).
FedRAMP/FISMA compliance
In 2011 a “cloud first” policy was defined in the Federal Risk and Authorization Program (FedRAMP) [pdf] where federal agencies make use of cloud service providers (CSPs) given authority to operate (ATO) after receiving system authorization from a security assessment conducted by an independent 3PAO (Third-Party Assessor Organization).
A System Security Plan (SSP) – submitted in both Word and PDF formats – is required by the OMB Security Authorization of Information Systems in Cloud Computing [pdf].
Each SSP authorization package can be in a machine-readable (JSON or XML format) https://github.com/usnistgov/OSCAL Open Security Controls Assessment Language - based on templates created based on this Excel xlsx file which defines fields (extensions), identifiers, and values in the FedRAMP Registry at https://github.com/GSA/fedramp-automation. The template is from FedRAMP PMO and NIST.
VIDEOS from info.fedramp.gov
Every federal agency is covered by the FISMA (Federal Information Security Management Act) of 2002 law. It’s implemented according to NIST (National Institute of Standards and Technology) Special Publication (SP) 800-53 [pdf]. The security controls development framework contains of 157 controls within 19 control families. Each control is designated as low, moderate, or high impact.
Coalfire
came up with this count of controls:
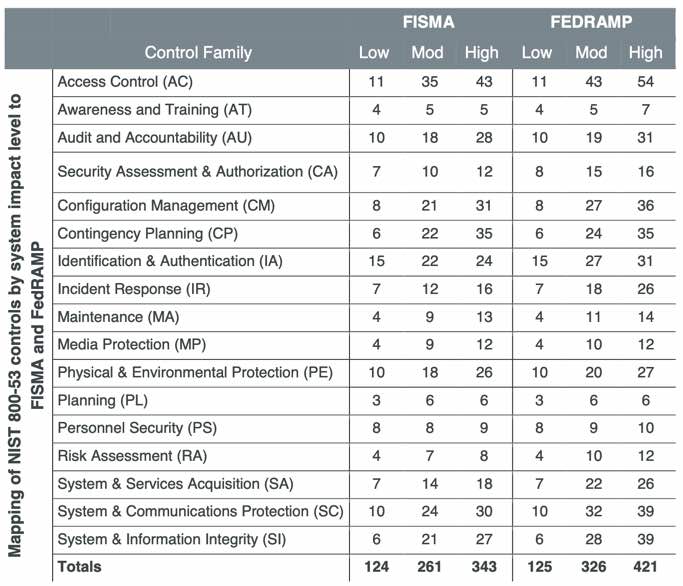
FedRAMP added 144 control to 728 in FISMA, for a total of 872 controls. Control Families:
- AC - Access Control [CMMC]
- AU - Audit and Accountability [CMMC]
- AT - Awareness and Training [CMMC]
- CM - Configuration Management [CMMC]
- CP - Contingency Planning
- IA - Identification and Authentication [CMMC]
- IR - Incident Response [CMMC]
- MA - Maintenance [CMMC]
- MP - Media Protection [CMMC]
- PS - Personnel Security [CMMC]
- PE - Physical and Environmental Protection [CMMC]
- PL - Planning
- PM - Program Management
- RA - Risk Assessment [CMMC]
- CA - Security Assessment and Authorization [CMMC]
- SC - System and Communications Protection
- SI - System and Information Integrity [CMMC]
- SA - System and Services Acquisition
CMMC
The Cybersecurity Maturity Model Certification (CMMC) framework consists of 14 domains that align with the families specified in NIST SP 800-171.
I was first published March 18, 2020 at https://www.acq.osd.mil/cmmc by US DoD aims to address supply chain risks.
CMMC has 3 layers.
The OSI (Open System Interconnect) networking model 7-layers:
- App Layer 7 protocols SNMP, TFTP
- Layer 6
- Layer 5
- Layer 4
- IP Layer 3 routers
- MAC Layer 2 switches (outputs to a specific port)
- Layer 1 hub (multi-port repeater outputs to all ports)
The sending computer encapsulates data and the receiving computer de-encapsulates the data. Encapsulation means that as data flows from one layer to the next, headers and footers are added to tell the receiving system how to process the data at each layer.
FTP & TELNET protocols do not encrypt data in transit.
The DoD (Department of Defense) Networking Model has a 4-layer stack:
- Process/Application layer accepts and processes user-level functions, such as mail delivery, file transfer and remote administration.
- Host-to-Host layer manages connections, flow control, retransmissions, error correction, etc.
- Internet layer manages data delivery across networks (routing) and related functions.
- Network Access layer takes data to the wire (or wireless) and back up through the “stack”.
192 in binary = 110000000
NIST documents
NIST SP 800-30
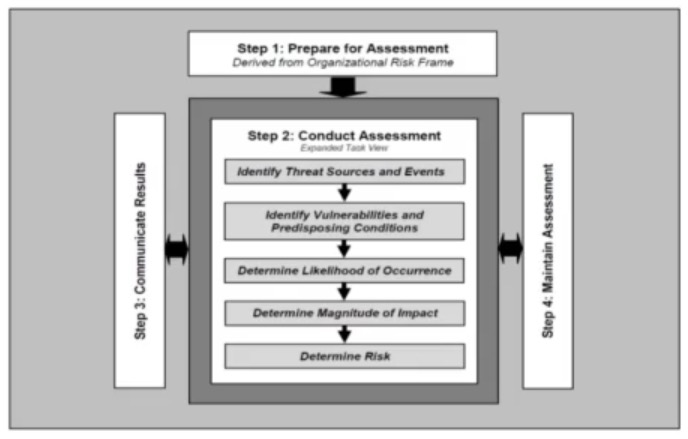
📓 NIST 800-30 Rev. 1 September 2012 “Guide for Conducting Risk Assessments” offers a structured approach for identifying, evaluating, and prioritizing information security risks through risk assessments. The government of Canada has a harmonized TRA Methodology. Mozilla offers RRA (Rapid Risk Assessment) guidance.
SP 800-30 steps for a risk assessment:
- Identify the assets and their value.
- Identify threats.
- Identify vulnerabilities.
- Determine likelihood.
- Identify impact.
- Determine risk as a combination of likelihood and impact.
SP 800-34 defines “vulnerability” as “an inherent weakness in an information system, security procedures, internal controls, or implementation that could be exploited by a threat source.”
NIST SP 800-34
-
A CIP (critical infrastructure protection) plan is a set of policies and procedures that serve to protect and recover assets and mitigate risks and vulnerabilities.
-
An OEP (occupant emergency plan) outlines first-response procedures for occupants of a facility in the event of a threat or incident to the health and safety of personnel, the environment, or property.
-
An ISCP (information system contingency plan) provides established procedures for the assessment and recovery of a system following a system disruption.
-
A COOP (Continuity Of Operations Plan) focuses on restoring an organization’s mission-essential functions (MEFs) at an alternate site and performing those functions for up to 30 days before returning to normal operations.
NIST SP 800-37
800-37 RMF (Risk Management Framework) - to obtain cATO (continuous Authority To Operate):
- Categorize information system based on impact FIPS 199 doc
- Select a baseline set of security controls using FIPS 200, SP 800-30, SP 800-53
- Implement security controls SP 800-18, 800-34, 800-70
- Assess the effectivenss of security controls SP 800-53A
- Authorize the information system to operate SP-800-37
- Monitor security controls for the protection they provide SP-800-37, SP-800-53A
PROTIP: Notice that Categorize and Authorize refer to information systems. The rest refer to security controls.
PROTIP: A memonic story I made up:
- Categorize clothing choices to select one to implement on the Oscars red carpet for magazines who assess mine as the best so I can authorize it for sales to fans who monitor who's wearing it too.
📓 NIST SP 800-171 Rev 2
Audit Prep, Logistics (Who, Require SOP/Policies), Audit (show me evidence), Post-Audit Reconciliation, Analysis, Reporting, Remediation, and Continuous Monitoring
SP 800-171 Rev 2 replaces
📓 NIST SP 800-161 “Cybersecurity Supply Chain Risk Management Practices for Systems and Organizations”
which was withdrawn on May 05, 2022. 161 provides guidance for organizations to identify, assess, and mitigate cybersecurity risks associated with products and services throughout the supply chain, integrating cybersecurity supply chain risk management (C-SCRM) into risk management activities at all levels, and offering guidance on C-SCRM strategy implementation plans, policies, plans, and risk assessments.
📓 NIST SP 800-39 (March 2011) “Managing Information Security Risk: Organization, Mission, and Information System View” offers structured and flexible guidance for managing information security risk across an organization’s operations, assets, individuals, and other organizations, providing an integrated and complementary approach to other risk-related activities, processes, or approaches that organizations have implemented or intend to implement.
NIST SP 800-40
NIST SP 800-40
Guide to Enterpise Patch Management Technologies
NIST SP 800-53
https://www.cybersaint.io/blog/nist-800-53-control-families
📓 NIST SP 800-53 Rev 5 September 2020 “Security and Privacy Controls for Information Systems and Organizations” outlines a set of security and privacy controls that organizations can implement to protect against potential threats and vulnerabilities. The controls are organized into families, and each control includes a description, implementation guidance, and assessment procedures.
Its 121 requirements are supported among the 36 AWS Services by AWS Security Hub.
NIST SP 800-53 is within section 4 SECURITY CONTROL SELECTION of https://csrc.nist.gov/publications/fips NISP FIPS-200 and 201-3 catagorizes by impact.
📓NIST SP 800-53A
provides a methodology for assessing the security controls of federal information systems.
📓NIST SP 800-53B
is based on the security and privacy controls outlined in NIST SP 800-53 and provides a set of control baselines that organizations can use to tailor their security controls to meet their specific needs.
DISA SIST & SRG
Security Technical Implementation Guides (STIGs) [Wiki] defines (over 425) “lock down” configuration settings to minimize vulnerabilities to malicious attack of DOD IA (Information Assurance) and IA-enabled devices/systems, both Windows and Apache Unix. Cloud Computing Security Requirements Guide (CC SRG) are also defined by DISA (Defense Information Systems Agency) which provides a Viewer to scan for them.
SCAP (Security Content Automation Protocol) [Wikipedia] checklists enable automated vulnerability management, measurement, and policy compliance evaluation of systems deployed in an organization. See the 2015 viewer video.
See https://www.open-scap.org for tools.
- ITAR (International Traffic in Arms Regulations)
- ECCN (Export Control Classification Number)
Source of Vulnerabilities
Top 50 Products By Total Number Of “Distinct” Vulnerabilities - for all time include product versions now obsolete.
(At the top of the list is Debian.)
Social Engineering
- Tailgating / piggybacking
Credential harvesting:
- Eliciting information
-
Impersonation
- Phishing, Spear-phishing, whaling
- Vishing (via a voicemail by phone )
- Smishing, aka SMS phishing, uses phishing methods through text messaging
- Watering Hole Attack attacks a site that the target frequently visits.
-
Pharming redirects victims to a bogus website
- Invoice scam
- Pretexting
-
Credential harvesting
-
Prepending - adding something to the front of something else, such as adding an asterisk to the front of code or prepending text to the subject line or body of an email.
- “Hybrid warfare”: Influencing campaign, propaganda, disinformation, hoaxes
- Manufacturing consent
Lures:
- Authority (posing as government, customer)
- Scarcity
- Familiarity/liking
- Urgency
Hoax
Influence campaign
Watering hole attack
Typo squatting
International
International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) 27018:2019 Code of practice for protection of Personally Identifiable Information (PII) in public clouds acting as PII processors covers the processing of personal information by cloud service providers. 27018 interprets rather than duplicates ISO/IEC 27002:2013. For example, advising cloud service providers to advise their customers if they use sub-contractors.
PII includes Social Security numbers, Drivers license, Passport or Alien Registration numbers, Financial account numbers, biometric identifiers.
PDF: SPII (Sensitive Personally Identifiable Information) includes what, if lost, compromised, or disclosed without authorization, could result in substantial harm, embarrassment, inconvenience, or unfairness to an individual.
Not considered private are last names, email addresses.
MTCS (Multi-Tier Cloud Security) Singapore 584:2013 Certification covers
- Infrastructure as a Service (IaaS),
- Platform as a Service (PaaS), and
- Software as a Service (SaaS).
PLA (Privacy Level Agreement)
GDPR (General Data Protection Regulation) states that the data gathered for private individuals should be used only for the purpose for which it is collected. The European Union (EU) Principles on Privacy state that data gathered for private individuals should be used only for the purpose for which it is collected. As of May 25, 2018, European privacy law GDPR (General Data Protection Regulation) imposes new rules on companies, government agencies, non-profits, and other organizations that offer goods and services to people in the European Union (EU), or that collect and analyze data tied to EU residents. But the GDPR applies no matter where they are located.
EU Cookie Law http://ec.europa.eu/ipg/basics/legal/cookies/index_en.htm
OECD.org Privacy Principles for Canada, Mexico, EU GDPR
eDiscovery EDRM (electronic Discovery Reference Model) A framework that provides guidance for gathering and assimilating electronic data during the legal process:
- Preserving
- Collection
- Processing
- Review
- Analysis production
Rules of evidence:
- Be authentic.
- Be accurate.
- Be complete.
- Be convincing.
- Be admissible.
ISO/IEC 27050
CSA (Cloud Security Alliance) guidelines
US Laws
- Jurisdiction is the power or right of a legal or political agency to exercise its authority over a person, subject matter, or territory. Jurisdiction can be affected when the organization that owns the data is in one country while the data itself is stored in a facility in another country
- Standing
- Jurisprudence
- Authority
QUESTION: How does CIS relate to ITIL?
Criminal Justice Information Services (CJIS) Security Policy compliance for any US state or local agency that wants to access the FBI’s CJIS database.
UK Government G-Cloud is a cloud computing certification for services used by government entities in the United Kingdom.
HIPAA (Health Insurance Portability and Accountability Act) is a US federal law that regulates patient Protected Health Information (PHI). HIPAA security rules prevent medical organizations (including health insurance companies, hospitals, and doctors’ offices) from sharing patient healthcare information without consent.
The HIPAA Omibus Final Rule in 2013 combined HIPPA with HITECH (Health Information Technology for Economic and Clinical Health Act), which defined mandatory penalties of up to $1.5 million for HIPAA-covered entitites. A Business Associate Agreement (BAA) stipulates adherence to security and privacy provisions in HIPAA and HITECH. The HIPPA Breach Notification Rule requires entities to issue notifications within 60 days of discovery. In 2011 a HITECH-required Rule allows patients to request access reports.
Service Organization Controls (SOC) 1, 2, and 3 report is a framework by independent third-party auditors covering controls for data security, availability, processing integrity, and confidentiality as applicable to in-scope trust principles for each service. SOC reports are internal control reports on the services provided by a service organization.
- SOC 3 is the only SOC report that should be shared with the general public.
- SOC 2 Type II, along with ISO 27001
AICPA (American Institue of Certified Public Accountants) Trust Service Principles, including Security, Availability and Confidentiality. PDF: SSAE #18 (Statement on Standards for Attestation Agreement #18). GAPP (Generally Accepted Privacy Principles) component of SOC2:
- Management. The entity defines, documents, communicates, and assigns accountability for its privacy policies and procedures.
- Notice. The entity provides notice about its privacy policies and procedures and identifies the purposes for which personal information is collected, used, retained, and disclosed.
- Choice and consent. The entity describes the choices available to the individual and obtains implicit or explicit consent with respect to the collection, use, and disclosure of personal information.
- Collection. The entity collects personal information only for the purposes identified in the notice.
- Use, retention, and disposal. The entity limits the use of personal information to the purposes identified in the notice and for which the individual has provided implicit or explicit consent. The entity retains personal information for only as long as necessary to fulfill the stated purposes or as required by law or regulations and thereafter appropriately disposes of such information.
- Access. The entity provides individuals with access to their personal information for review and update.
- Disclosure to third parties. The entity discloses personal information to third parties only for the purposes identified in the notice and with the implicit or explicit consent of the individual.
- Security for privacy. The entity protects personal information against unauthorized access (both physical and logical).
- Quality. The entity maintains accurate, complete, and relevant personal information for the purposes identified in the notice.
Policies, procedures, governance structures in place to protect privacy. Clearly define roles of data owner, steward, custodian.
Others:
-
The Federal Privacy Act of 1974 ensures that only authorized persons should have access to personal information and that personal records should be up to date and accurate. The act affects any computer that contains records used by a federal agency.
-
The Federal Intelligence Surveillance Act (FISA) of 1978 affects law enforcement and intelligence agencies and gives procedures for the physical and electronic surveillance and collection of “foreign intelligence information” between “foreign powers” and “agents of foreign powers.”
-
1986 Computer Fraud and Abuse Act (CFAA) was the first law that required a formal computer security plan. It also requires appropriate training of system users or owners where the systems house sensitive information. Although “protected computers” was initially applicable to feds and financial institutions, court cases have expanded coverage to any computer in “interstate commerce”.
-
1986 Electronic Communications Privacy Act (ECPA) extended government restrictions on wiretaps from telephone calls to include transmissions of electronic data by computer.
-
1987 Public Law 100-235 Title 101, Statute 1724 applies to federal systems
-
1991 United States Federal Sentencing Guidelines of affects individuals and organizations convicted of felonies and serious (Class A) misdemeanors. It provides guidelines to prevent sentencing disparities that existed across the United States.
-
1996 US Economic Espionage Act provides a framework to deal with espionage attacks on corporations. According to the Act, all the assets of the organization, whether substantial or not, require protection. The Economic Espionage Act of 1996 affects companies that have trade secrets and any individuals who plan to use encryption technology for criminal activities.
-
1994 Communications Assistance for Law Enforcement Act (CALEA) requires telecommunications carriers and manufacturers of telecommunications equipment to modify and design their equipment, facilities, and services to ensure that they have built-in surveillance capabilities.
-
1996 Clinger-Cohen Act requires a CIO for each agency to oversee adoption of the Department of Defense Architecture Framework (DODAF) Federal Enterprise Architecture (FEA)
-
1999 GLBA (Gramm-Leach-Bliley Act) requires all financial institutions, including banks, loan companies, insurance companies, investment companies, and credit card providers to explain practices to consumers.
-
The Personal Information Protection and Electronic Documents Act (PIPEDA) affects private sector organizations that collect, use, and disclose personal information in the course of commercial business in Canada.
-
2002 & 2014 Federal Information Security Management Act (FISMA) affects every federal agency. It requires federal agencies to develop, document, and implement an agency-wide information security program. It requires federal agencies to develop, document, and implement an agency-wide information security program.
-
Basel II affects financial institutions and addresses minimum capital requirements, supervisory review, and market discipline.
-
The Sarbanes-Oxley (SOX) Act provides guidelines on accurately reporting corporate financial data to shareholders and retention of record storage. (to prevent another Enron)
- The Payment Card Industry Data Security Standard (PCI DSS) affects any organizations that handle cardholder information for a major credit card company (VISA, MasterCard, Amex, etc.). Each year each merchant submits a SAQ (Self-Assessment Questionaire) to its transaction bank. A QSA (Qualified Security Assessor) certified by the PCI Security Standards Council issues a ROC (Report on Compliance) form. PCI DSS compliance:
- Build and maintain a secure network and systems
- Protect cardholder data
- Maintain a vulnerability management program
- Implement strong access control measures
- Regularly monitor and test networks
- Maintain an information security policy
Objectives:- Minimize the Attack Surface
- Software Protection Mechanisms
- Secure Software Operations
- Secure Software Lifecycle Management
-
COPPA (???) - online collection and use of data for minors under 13
- FERPA (Family Educational Rights and Privacy Act) requires educational institutions to protect the privacy of student records.
Be careful of the “color of law” who may not be the right people at the appropriate time so they don’t become a hinderance.
Reporting
https://threatmap.checkpoint.com/ThreatPortal/livemap
Interpol: https://www.interpol.int/Crime-areas/Cybercrime/Cybercrime
FBI https://fbi.gov/investigate/cyber
DHS (Department of Homeland Security): https://www.dhs.gov/topic/cybersecurity
Property Law: https://www.bsa.org
US State laws
- 2003 Calif. SB 1386 Security Breach Information Act is the first state to require notification
-
2010 201 CMR 17 Massachusetts Standards for the Protection of Personal Information of Residents
- ncsl.org (National Conference of State Legislators) has research on data-security-laws (Private Sector), data-disposal-lawsx, security-breach-notification-laws.
FIPS
FIPS 199 says federal organizations
- determine the security category of their information system in accordance with FIPS (Federal Information Processing Standard) Publication 199, Standards for Security Categorization of Federal Information and Information Systems
- derive the information system impact level from the security category in accordance with FIPS Publication 200
- apply the appropriately tailored set of baseline security controls in NIST Special Publication 800-53 Rev. 4.
Data Classification
| Impact (damaged) from release | Military Government | Commercial | Classification |
|---|---|---|---|
| Exceptionally Grave | Top-secret | Confidential Proprietary | Class 3 |
| Serious | Secret | Private | Class 2 |
| Damage | Confidential / Controlled Unclassified (CUI) | Sensitive | Class 1 |
| No damage | Unclassified | Public | Class 0 |
Commercial data classification levels:
\0. Public = freely available Information that is accessible to the public without any restrictions or adverse consequences, such as marketing material, corporate contact information, customer service contracts, and website data.
\1. Internal = Non-sensitive data with low security requirements, but not meant for public disclosure, such as client communications, sales playbooks, and organizational charts. Unauthorized disclosure of such information can lead to short-term embarrassment and loss of competitive advantage.
\2. Confidential = Sensitive data that, if compromised, could negatively impact operations, including harming the company, its customers, partners, or employees. Examples include trade secrets, vendor contracts, employee reviews and salaries, and customer information.
\3. Restricted = Highly sensitive information that, if compromised, could put the organization at financial, legal, regulatory, and reputational risk. Examples include customers’ PII, PHI, employee ID number, and credit card information.
Private = Medical information
CUI (Controlled Unclassified) previously marked:
- For Official Use Only (FOUO)
- Sensitive But Unclassified (SBU)
- Dozens of other “sensitive” labels used by different U.S. agencies
- Sensitive Security Information (SSI)
Data classification program:
- Define the classification levels.
-
Specify the data classification criteria.
- Identify the data owners who determine the classification level of the information he owns and protects the data for which he is responsible.
-
Identify the data custodian who implements (records) the information classification and controls determined by the data owner.
- Indicate the controls required for each classification level. The System owner ensures that the appropriate controls are in place.
-
Document any known exceptions to the controls.
- Document information custody transfer guidelines.
- Create data classification review procedures.
-
Document data declassification procedures.
- Develop the data classification security awareness program.
- Security administrator maintains security devices and software, including firewalls, antivirus software, etc.
- Security administrator maintains security devices and software, including firewalls, antivirus software, etc.
NIST CSF
SUBSCRIBE: NIST Information Technology Laboratory emails out bulletins about vulnerabilities NIST CSRC (Computer Security Resource Center)
Executive Order 13636: “Improving Critical Infrastructure Cybersecurity” issued by the Obama White House on Feb 2013 charged the US National Institute of Standards and Technology (NIST) to develop their Cybersecurity Framework (CSF) as a prescriptive standard mandatory for federal agencies but a voluntary framework for commercial organizations. CSF does not tell organizations how much risk is tolerable.
Executive Order 13800: “Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure” PDF from the Trump White House on May 11, 2017 aims to improve the nation’s cyber posture and capabilities in the face of intensifying cybersecurity threats. Sections: 1) Federal Networks, 2) Critical Infrastructure, 3) the nation.
- Homeland Security Directive 7 (HSPD-7) “Critical Infrastructure Identification, Prioritization, and Protection”.
- https://www.cisa.gov/topics/cybersecurity-best-practices/executive-order-strengthening-cybersecurity-federal-networks-and-critical-infrastructure
- https://trumpwhitehouse.archives.gov/articles/strengthening-the-cybersecurity-of-federal-networks-and-critical-infrastructure/
- https://www.federalregister.gov/documents/2017/05/16/2017-10004/strengthening-the-cybersecurity-of-federal-networks-and-critical-infrastructure
The current CSF version 1.1, was released April 2018.
The CSF provides a common Language and systematic methodology for managing cyber risk management with “best practices”.
The CSF consists of standards, guidelines, and best practices to manage cybersecurity-related risks.
NIACAP (National Information Assurance Certification and Accreditation Process) evaluates an application or system that is distributed to a number of different locations. System accreditation evaluates an application or support system. Site accreditation evaluates the application or system at a specific self-contained location.
CSF Functions and Categories maps NIST 800-53 to CIS Controls:
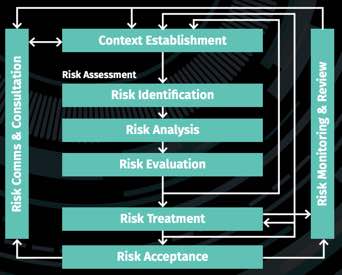
NIST SP 800-39 provides guidance for an integrated, organization-wide program for managing information security risk to organizational operations (i.e., mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the nation resulting from the operation and use of federal information systems.
Among The many NIST SP 800 documents:
- NIST SP 800-60 provides guidelines for mapping types of information and information systems to security categories.
- SP 800-183 describes the Internet of Things (IoT).
NIST SP 800-57 Key management lifecycle:
- Pre-operational phase
- Operational phase
- Post-operational phase
- Destroyed phase
NIST SP 800-92 log management infrastructure functions:
- General functions (log parsing, event filtering, and event aggregation)
- Storage (log rotation, log archival, log reduction, log conversion, log normalization, log file integrity checking)
- Log analysis (event correlation, log viewing, log reporting)
- Log disposal (log clearing)
NIST SP 800-137 ISCM (information security continuous monitoring) plan:
- Define an ISCM strategy.
- Establish an ISCM program.
- Implement an ISCM program.
- Analyze the data collected, and report findings.
- Respond to findings.
- Review and update the monitoring program.
Tiers in an organization defined by SP 800-139
- Organization view, which addresses risk from an organizational perspective by establishing and implementing governance structures that are consistent with the strategic goals and objectives of organizations and the requirements defined by federal laws, directives, policies, regulations, standards, and missions/business functions.
- Tier 2 is the mission/business process view, which designs, develops, and implements mission/business processes that support the missions/business functions defined at Tier 1.
- Tier 3 is the information systems view, which includes operational systems, systems under development, systems undergoing modification, and systems in some phase of the system development life cycle.
CSF process:
- Prioritize and scope. Varying risk tolerances may be defined for each implementation tier. Inputs, Activities, Outputs
- Orient
- Create a Current Profile
- Conduct Risk Assessment
- Create Target Profile
- Determine, Analyze, Prioritize gaps
- Implementation Action Pln
SP 800-139 Functions to implement the appropriate safeguards to ensure delivery of critical infrastructure services
IDENTIFY, PROTECT, DETECT, RESPOND, RECOVER
- Identify (ID): Develop the organizational understanding to manage cybersecurity risk to systems, assets, data, and capabilities.
-
Protect (PR): Develop and implement the appropriate safeguards to ensure the delivery of critical infrastructure services.
-
Detect (DE): Develop and implement the appropriate activities to identify the occurrence of a cybersecurity event.
- Respond (RS): Develop and implement the appropriate activities to take action regarding a detected cybersecurity event.
- Recover (RC): Develop and implement the appropriate activities to maintain plans for resilience and to restore any capabilities or services that were impaired due to a cybersecurity event.
| Core Function | ID | 23 Category | CIS |
|---|---|---|---|
| IDENTIFY (What processes & assets need protection?) | ID.AM | Asset Management #1, #2 | |
| ID.AM | Asset Management - | ||
| ID.BE | Business Environment - | ||
| ID.GV | Governance - | ||
| ID.RA | Risk Assessment #3 | ||
| ID.RM | Risk Management Strategy - | ||
| ID.SC | Supply Chain Risk Management - | ||
| PROTECT | PR.AC | Identity Management & Access Control #4, 9, 11, 12, 13, 14, 16 | |
| PR.AM | Asset Management - | ||
| PR.AT | Awareness and Training #4, 17 | ||
| PR.DS | Data Security #1, 2, 13, 14, 18 | ||
| PR.IP | Information Protection Processes & Procedures #3, 5, 7, 10, 11 | ||
| PR.MA | Maintenance #4, 12 | ||
| PR.PT | Protective Technology #4, 6, 8, 11, 13, 14, 16 | ||
| DETECT | DE.AE | Anomalies and Events #6, 9, 12, 19 | |
| DE.CM | Security Continuous Monitoring #3, 8, 19 | ||
| DE.DP | Detection Processes #6 | ||
| RESPOND | RS.RP | Response Planning #19 | |
| RS.CO | Communications #19 | ||
| RS.AN | Analysis #3, 19 | ||
| RS.MI | Mitigation #3, 19 | ||
| RS.IM | Improvements #19 | ||
| RECOVER | RC.RP | Response Planning #19 | |
| RC.IM | Improvements #19 | ||
| RC.CO | Communications #19 |
“Communications” occur early in RESPOND but later in RECOVER.
Notice that “Improvements” is in both RESPOND and RECOVER.
There are also 108 (previously 97) subcategories.
The Category IDs are different from the 18 family identifiers used by RMF SP 800-53.
| Class | ID | RMF Family |
|---|---|---|
| Management | CA | Security Assessment and Authorization |
| PL | Planning | |
| RA | Risk Assessment | |
| SA | System and Services Acquisition | |
| PM | Program Management | |
| Operational | AT | Awareness and Training |
| CM | Configuration Management | |
| CP | Contingency Planning | |
| IR | Incident Response | |
| MA | Maintenance | |
| MP | Media Protection | |
| PE | Physical and Environmental Protection | |
| PS | Personnel Security | |
| SI | System and Infomration Integrity | |
| Technical | AC | Access Control |
| AU | Audit and Accountability | |
| IA | Identification and Authentication | |
| SC | System and Communications Protection |
- Prepare (added by SP 800-37 Rev 2)
- Categorize SPSCRs
- Select 800-53 Rev 5
- Implement
- Assess
- Authorize
- Monitor
In the NIST CSF, “Informative References” citations relate to more technical activities from other standards or guidelines, to provide additional information on how to achieve outcomes described in Subcategories.
SP 800-139 framework implementation (maturity) tiers:
- Tier 1: Partial - risk management practices are not formalized, and risk is managed in an ad hoc and sometimes reactive manner.
- Tier 2: Risk Informed - risk management practices are approved by management but may not be established as organizational-wide policy.
- Tier 3: Repeatable - the organization’s risk management practices are formally approved and expressed as policy.
- Tier 4: Adaptive - the organization adapts its cybersecurity practices based on lessons learned and predictive indicators derived from previous and current cybersecurity activities through a process of continuous improvement.
NIST SP 800-154 is a draft publication for data-centric system threat modeling. Its steps:
- Identify and characterize the system and data of interest.
- Identify and select the attack vectors to be included in the model.
- Characterize the security controls for mitigating the attack vectors.
- Analyze the threat model.
NIST SP 800-160 defines the systems security engineering framework. It defines, bounds, and focuses the systems security engineering activities, both technical and nontechnical, toward the achievement of stakeholder security objectives and presents a coherent, well-formed, evidence-based case that those objectives have been achieved. Contexts within which security activities are conducted:
- Problem context
- Solution context
- Trustworthiness context
NIST SP 800-66 provides guidelines for implementing the HIPAA Security Rule, which requires securing protected health information (PHI) - any individually identifiable health information, also referred to as EPHI or ePHI (electronic protected health information).
NIST SP 800-122 gives guidelines on protecting the confidentiality of PII (Personally identifiable information) considered information that should be classified and protected. PII are assigned confidentiality impact levels based on FIPS 199 designations:
- LOW if the loss of confidentiality, integrity, or availability could be expected to have a limited adverse effect on organizational operations, organizational assets, or individuals.
- MODERATE if the loss of CIA could be expected to have a serious adverse effect on organizational operations, organizational assets, or individuals.
- HIGH if the loss of CIA could be expected to have a severe or catastrophic adverse effect on organizational operations, organizational assets, or individuals.
U.S. federal agencies use the SBU (Sensitive But Unclassified) designation for information not secret but still needs to be protected and requires strict controls over its distribution.
http://ethics-wg.org/framework.htm says: “Do not appropriate other people’s intellectual output” is one of the Computer Ethics Institute (CEI) Ten Commandments of Computer Ethics, but is not part of the (ISC)2 code of ethics preamble.
Components of configuration management:
- configuration control
- configuration status accounting
- configuration auditing
- Planning - prework to prepare
- Overview - assign roles, provide overview of software
- Preparation - independent review of code for potential defects
- Meeting - formally identify issues as a team
- Rework - fix. May return to the planning phase.
- Follow-up to confirm defects corrected
Defense in Depth
- Physical security
- Identity
- Perimeter
- Network
- Compute
- Application
- Data
Security Testing
OSSTMM (Open Source Security Testing Methodology Manual) published by Pete Herzog of ISECOM (Institute for Security and Open Methodologies) covers the different kinds of security tests of physical, human (processes), and communication systems. It does not cover any specific tools that can be used to perform these tests. It defines five risk categorizations:
- vulnerability,
- weakness,
- concern,
- exposure, and
- anomaly.
Once a risk is detected and verified, it is assigned a risk assessment value.
COSCO (Committee of Sponsoring Organizations) broadly defines ERM (Enterprise Risk Management) as “the culture, capabilities and practices integrated with strategy-setting and its execution, that organizations rely on to manage risk in creating, preserving and realizing value.” The ERM framework is presented in the form of a three-dimensional matrix. The matrix includes eight components of enterprise risk management and four categories of objectives across the top: strategic, operations, reporting, and compliance.
The organization, its divisions, and business units are depicted as the third dimension of the matrix for applying the framework.
Levels of testing:
- Small Unit Tests at functional level by input and output
- Medium Integration Tests for functional dependencies
- Large System Tests of critical components only - Tackle the APIs, leave the UI untested
- Manual validation of every commit, exploratory testing
RFCs
RFC’s https://tools.ietf.org/html/rfc1087
- RFC 1087 outlines concepts pertaining to what the IAB considers unethical and unacceptable. It considers destroying the integrity of computer-based information unethical.
- RFC 2010 Operational Criteria for Root Name Servers
- RFC 1589 A Kernel Model for Precision Timekeeping
- RFC 1150 F.Y.I. on F.Y.I.
Credential Rotation Lifecycle
Different periods for rotating different key types. Here is the “regular basis” recommended:
| Key Type | Rotation Period |
|---|---|
| Tokens | ADFS – 24 hours |
| Domain Passwords | 70 days |
| Connection strings | 70 days |
| Shared Access Signatures | 60 days |
| Self-Signed Certificate | 2 Years |
| Symmetric Keys | 2 Years |
| Asymmetric Keys | 2 years |
| Storage Account Keys | 2 years |
Book copyright in the US & UK is 70 years after death of author.
Security Engineer
Here are “Essential Job Functions” from various job descriptions:
- Apply established and ad hoc processes and techniques to identify, validate, prioritize, and track security risks.
- Identify uncontrolled risks and recommend control improvements.
- Proactively identify security requirement deficiencies.
- Engage business and technology personnel to elicit security requirements.
- Architect and design security control systems to address requirements.
- Operate and monitor established security controls.
- Identify control deficiencies and make appropriate recommendations.
- Ensure that controls are operating effectively; resolve operating discrepancies.
- Review, triage, and prioritize control output.
- Take appropriate action to resolve security discrepancies.
- Identify, evaluate, and recommend new security technologies, techniques, and tools.
-
Define, review, and promote information security policies, standards, guidelines, and procedures.
- As compliance subject matter expert, enforce and monitor compliance with internal and external regulations, policies, and standards.
- Establish and promote strategies to ensure that compliance is effectively monitored and enforced.
-
Lead/Co-lead internal process improvement initiatives. Provide feedback on processes by offering suggestions.
- Mentor and supervise junior staff in project-level tasks.
- Assist with adherence to technology policies and comply with all security controls.
Education/Experience Requirements:
- Experience must include direct experience in several of the key areas listed: securing networks and systems architecture, design and implementation, secure software assurance, intrusion detection, defense and incident response, security configuration management, access controls design and implementation and security policy and standards development.
- In-depth knowledge of one or more communications protocols.
-
Experience with more than one Cyber Security tools, including: Configuration Assessment, Log Aggregation, Integrity Verification, Web Application Security Testing, Network Access Control System, Network Intrusion prevention systems, and Endpoint Security Solutions.
- Strong written and verbal technical communication skills.
- Demonstrated ability to develop effective working relationships that improved the quality of work products.
- Should be well organized, thorough, and able to handle competing priorities.
- Ability to maintain focus and develop proficiency in new skills rapidly.
- Ability to work in a fast paced environment.
- In-depth knowledge of more than one Information Security principle and discipline.
Threats
CRAMM is an abbreviation of “C” for the UK government’s Central Computer and Telecommunications Agency (CCTA) Risk Analysis and Management Method. CRAMM reviews includes three steps:
- Identify and value assets.
- Identify threats and vulnerabilities and calculate risks.
- Identify and prioritize countermeasures.
A threat modeling program continually reassess the threat environment, including new adversaries, and proactively adapt their information security program. Threat modeling process:
- Decompose the application or infrastructure
- Determine the threats
- Determine countermeasures and mitigations
- Rank the threats
Costs include annual maintenance.
Microsoft’s STRIDE
Microsoft Threat Model Tool uses “STRIDE” as a mnemonic for classification of threats in an application:
- Spoofing of user identity
- Tampering of data, source code, or program binary code
- Repudiation
- Information disclosure (privacy breach or data leak)
- Denial of service (DoS)
- Elevation of privilege
Threat Hunting - MITRE ATT&CK & Dragos
Since 2013, MITRE’s ATT&CK process looks at Tactics, Techniques, and Procedures (TTPs) for Enterprise IT. PROTIP: Click on the icon to the right of each item for additional info.
Dragos PDF: ATT&CK for IoC (Industrial Control Systems)
Cyber Kill Chain: MITRE ATT&CK
| MITRE | Dragos ICS |
|---|---|
| 1. Reconnaissance | - |
| 2. Resource Development (new) | - |
| 3. Initial Access [Intrusion] | 1. Initial access |
| 4. Execution [Exploitation] | 2. Execution |
| 5. Persistence [new] | 3. Persistence |
| 6. Privilege Escalation | - |
| 7. Defense Evasion (Obfuscation Anti-forensics) | 4. Evasion |
| 8. Credential Access | - |
| 9. Discovery [new] | 5. Discovery |
| 10. Lateral Movement | 6. Lateral Movement |
| 11. Collection [new] | 7. Collection |
| 12. Command and Control [Denial of service] | 8. Command and Control |
| 13. Exfiltration | - |
| 14. Impact [new] | 9. Inhibit response function [+] 10. Impair process control [+] 11. Impact process |
Attackers
Mandiant’s list of known APT (Advanced Persistent Threat) actors. AVT (Advanced Volatile Threat)
Attacks
Attacks: attempts to violate an organization’s security or privacy: REMEMBER:
Attacks are classified by the method and vector:
- Method is how an attack is executed, or “the mechanism that was used”. Example: ransomware
- Vector is how an attack is carried out, or “the course that was taken”. Example: email
Cryptoanalytic attacks try to deduce the key via brute force
- a dictionary of common passwords
- a Rainbow Table - a very large set of precomputed hash values for every possible combination of characters that is able to reverse cryptographic hash functions
Cryptographic attacks: man-in-the-middle, replay, timing, radiation
- A smurf attack uses a type of ping packet called an ICMP ECHO REQUEST.
- In a side-channel attack, the attacker gains information about the encryption algorithms from the cryptosystem that is implemented in the network.
- Evesdropping (traffic analysis). Countermeasures are sending noise, padding messages, mix non-info in data.
- In a known plaintext attack, an attacker uses the plaintext and ciphertext versions of a message to discover the key used.
- In an analytic attack, an attacker uses known structural weaknesses or flaws to determine the algorithm used.
- In a replay attack, an attacker monitors the traffic stream in a network and maliciously repeats or delays the transmission of valid data over the network.
- A race condition causes processes to execute in a different order to affect the result.
- A Time-Of-Check/Time-Of-Use (TOC/TOU) attack, also called asynchronous attack, interrupts a task and changes something to affect the result while the tasks occur in the correct order. A countermeasure is making critical sets of instructions atomic.
- Emanations capturing is eavesdropping on wave frequencies to capture traffic.
- A maintenance hook is a backdoor in an application that is designed by the application developers to perform maintenance tasks, which can enable code to be executed without the usual security checks. A countermeasure for maintenance hooks is code reviews.
- A buffer overflow transmits too much data to an application or operating system. A countermeasure for buffer overflows is input validation.
- A covert storage channel attack is when one process writes data to a hard drive and another process reads it. In this attack a higher-level subject writes data to a storage area and a lower-level subject reads it.
- A land attack sends a spoofed TCP SYN packet with the target host’s IP address and an open port as both the source and the destination to the target host on an open port.
- Network address hijacking reroutes data traffic from a network device to the attacker.
- A ping of death attack floods target computers with oversized packets, causing the target computer to either freeze or crash.
- In SMTP relay attacks outbound mail folders fill up with spam relayed through an email server.
- A salami attack is when small changes to data are made over time.
- Data diddling is when changes to data are made before and after an attack.
“Live off the land” malware have Low Observable Characteristics (LOC). They are called “fileless”. So they can evade traditional anti-virus signature detection. They can also continually evolve.
Bluejacking is when a user’s device gets paired with an attacker’s device, and the user’s device makes its data available for unauthorized access, modification, or deletion. Bluejacking enables the receipt of unsolicited photos or messages from a nearby device to another Bluetooth-enabled device, such as a smartphone.
Bluesnarfing is also a Bluetooth attack, but it involves unauthorized pairing and access to the device.
Jamming is an attack on a wireless network that is performed by setting up a nearby access point and using a dedicated wireless jamming device to block Wi-Fi signals.
An initialization vector (IV) is a fixed-size input of a random or pseudo-random value used with block cipher modes. Some Wi-Fi technologies are susceptible to IV attack, which uses passive statistical analysis. An IV is an input to a cryptographic algorithm, which is essentially a random number. Ideally, an IV should be unique and unpredictable. “It should be short” is incorrect because an IV attack can occur when the IV is too short. The attack is possible when the IV is not long enough, which means it has a high probability of repeating itself after only a small number of packets.
An evil twin is a wireless access point fraudulently installed to perform a man-in-the-middle attack and often used for eavesdropping.
Maneuvering enables a security team to completely disrupt an attacker or quickly mitigate an attacker’s ability to move across the attack chain.
Intelligence fusion brings together internal and external threat feeds.
A zero-day attack or threat is a computer threat that tries to exploit computer application vulnerabilities that are unknown to others and possibly even the software developer.
Attacks to data and databases VIDEO [MINDMAP]
- An inference attack is the development of a detailed version of an object from another object using different values in the new object, such as the difference between totals versus details allowed. A countermeasure is Polyinstantiation which prevents low-level database users from inferring the existence of higher-level data. It enables a relation to contain multiple tuples (rows) with the same primary keys, with each instance distinguished by a security level. [WIKIPEDIA]
- A data contamination attack. Proper implementation of security levels is a countermeasure for data contamination.
A breach is an attack that has been successful in reaching its goal.
- Means is how a criminal committed a crime.
- Motive is why a crime is committed.
- Opportunity is when and where a crime occurred.
- Exigent circumstances are when evidence might be destroyed.
Events: System-level, application-level, or user-level? REMEMBER
- User-level events include Authentication attempts, command run, security violations.
- System-level events include logon attempts, logon IDs, logon attempts, Administration tools usage, user and client computer lockout, system performance, time/date, administration tools usage, and device usage.
- Application-level events include files opened and closed, error messages, security violations, and file modifications.
Malware (malicious software - malware):
See https://www.caida.org/research/security/code-red/
- Password spraying is a horizontal brute-force online attack, where the attacker tries common passwords in conjunction with multiple usernames.
-
An offline attack occurs when the attacker does not interact with the authentication system because he/she has obtained a database of password hashes, such as %SystemRoot%\System32\config\SAM, %SystemRoot%\NTDS\NTDS.DIT (the Active Directory credential store), or /etc/shadow.
- A worm is memory-resident malware that can run without user intervention and replicate over network resources.
- Fileless malware uses memory resident techniques to run in its own process rather than writing its code to disk.
- A companion is a new file created with a similar name so users activate it.
- A virus relies upon other application programs to execute itself and infect a system.
-
An armored virus includes protective code that prevents examination of critical elements, such as scans by antivirus software.
- Spyware uses tracking cookies to collect and report on a user’s activities to the spyware programmer.
- A Trojan is malware disguised as a useful utility but embeds malicious code in itself. A symptom of a Trojan horse is that unknown software is using covert channels to perform malicious activities, such as deleting system files and planting a backdoor into a system. The term is based on the “Trojan horse” story where soldiers hid in a large wooden horse which the opposition pulled inside their gates.
- A RAT is a Remote Access Trojan backdoor malware that mimics the functionality of legitimate remote control programs, but operate covertly. It allows the threat actor to access the host, upload files, and install software or use “live off the land” techniques to effect further compromises.
- A host that is under malicious control is sometimes described as a “zombie”.
- A Macro is written into like VB in Excel.
-
Logic bombs are triggered by events such as a specific date.
- PUPs/PUAs (Potentially Unwanted Programs/Applications) are installed alongside (bundled with) a package selected by the user, such as part of a new install of operating system (Ubuntu, printer, etc.)without active consent or consent from a purposefully confusing license agreement. Unlike a Trojan, the presence of a PUP is not automatically regarded as malicious, so it’s sometimes described as grayware.
-
Adware is a software application that displays advertisements (which generates revenue) while the application is executing.
- Multipartite spreads in different ways
- Polymorphic can change to avoid detection.
DREAD Risk ratings
REMEMBER: DREAD is a mnemonic for categories used to rate security threats for a given issue:
- Damage
- Reproducibility
- Exploitability, such as allowing RCE (Remote Control Execution)
- Affected users
- Discoverability
Each category is given a rating from 1 to 10. The sum of all ratings is used to prioritize among different issues.
CVSS
- Attack vector
- Attack complexity
- Privileges required
- User interaction
- Scope
CIS (Center for Internet Security)
CIS Controls (at v8 at time of writing) presents 18 must-have controls for cybersecurity.
https://www.networkworld.com/article/2992503/sans-20-critical-security-controls-you-need-to-add.html
Control 1: Inventory and control of enterprise assets
Actively manage inventories, track, and correct all end-user devices, including portable and mobile; network devices; non-computing/Internet of Things (IoT) devices; and servers that connect to the infrastructure physically, virtually, remotely, and those within cloud environments. The inventory helps identify devices to remove or remediate.
Control 2: Inventory and control of software assets
Actively inventory, track, and correct all operating systems and applications on the network to spot and block unauthorized and unmanaged software so that only authorized software is installed and can execute.
Control 3: Data protection
Identify, classify, securely handle, retain, and dispose of data.
The ideal for this is to put data of the same sensitivity level on the same network and isolated from data with other sensitivity levels. Firewalls would control access to each segment, and access would be granted only to users with a business need to access them.
Control 4: Secure configuration of assets and software
Secure configuration of end-user devices, including portable and mobile; network devices; non-computing/IoT devices; servers; operating systems and applications should be established, stored, and maintained. Installing VPNs in front of servers and using DNS servers that are controlled by the enterprise are recommended.
Contol 5: Account management
This recommends using processes and tools to manage authorization to enterprise assets and software. These include administrator and service accounts. One recommendation calls for restricting administrator privileges to dedicated administrator accounts and granting those privileges only to those who actually administer network assets. These admins should also have separate accounts that they use for accessing email, web browsing and productivity apps.
Control 6: Access-control management
Enterprises should use processes and tools to create, assign, manage, and revoke access credentials and privileges for user, administrator, and service accounts for enterprise assets and software. Role-based access should be assigned to each account based on need-to-know, least privilege, privacy requirements, and separation of duties.
Control 7: Continuous vulnerability management
Vulnerabilities should be continuously assessed and tracked on enterprise infrastructure so they can be remediated in a timely fashion that minimizes the window of opportunity for attackers to exploit them. Public and private industry sources of new threat and vulnerability information should be used to help this process.
Control 8: Audit log management
Audit logs should be collected, reviewed and retained to document events and help detect, understand, and recover from attacks. Logs can show when and how attacks occur, what information was accessed, and if data was exfiltrated. Retention of logs is critical for follow-up investigations or to understand attacks that remain undetected for a long period of time.
Control 9: Email and web browser protections
Improve protections and detections of email and web threats that can manipulate human behavior through direct engagement; these are prime targets for both malicious code and social engineering. Safeguards include the use of DNS-filtering services to reduce exposure and enforcement of network-based URL filters.
Control 10: Malware defenses
Prevent or control the installation, spread, and execution of software on enterprise assets, using methods that include anti-malware software on all enterprise assets, scanning for malware on removable media such as thumb drives, and enabling anti-exploitation features “such as Microsoft® Data Execution Prevention (DEP), Windows® Defender Exploit Guard (WDEG), or Apple® System Integrity Protection (SIP) and Gatekeeper™.”
Control 11: Data recovery
Data-recovery practices sufficient to restore in-scope enterprise assets to a pre-incident and trusted state. Because configuration changes can create vulnerabilities for attackers to exploit, it is important to have recent backups to recover enterprise assets and data back to a known trusted state.
Control 12: Network infrastructure management
Track, report, and correct network devices, to prevent attackers from exploiting network services and points of access. The infrastructure includes physical and virtual gateways, firewalls, wireless access points, routers, and switches. These measures should address vulnerabilities that can be introduced by using default settings, monitoring for changes, and reassessing current configurations. One example is running the latest stable release of software or using currently supported network-as-a-service (NaaS) offerings.
Further, enterprises should maintain network diagrams and other system documentation, and review and update them annually. Computing resources used for administrative tasks should be physically or logically separated from the primary enterprise network and isolated from internet access.
Control 13: Network monitoring and defense
Comprehensive network monitoring and defenses against threats should be established, including intrusion detection, traffic filtering between network segments, and deploying port-level controls such as those supported by 802.1x authentication.
Network segmentation and isolation are different. Network segmentation primarily uses VLANs to segment network traffic and does not place restrictions based on applications, ports, or data. Segmentation decisions are made a Layer 2 (Data Link) of the OSI Model.
Network isolation is much more secure and is a requirement to restrict lateral movement within the network. When configured properly, it only permits network traffic that is explicitly required and authorized for organizational operations. Network isolation can be implemented to work at all layers of the OSI model, but can me more difficult to manage because the organization will need an intimate understanding of the network, the systems on the network, and the applications on the systems on the network. Thus, Network isolation requires data flow diagrams and is part of a Zero Trust Architecture (or ZTA).
Control 14: Security-awareness and skills training
A security awareness program should be established create security consciousness among the workforce and provide them the skills to reduce cybersecurity risks.
Control 15: Service provider management
A process to evaluate service providers who hold sensitive data or are responsible critical enterprise-IT platforms or processes should be set up to ensure they are providing appropriate protection. Enterprises should set requirements for service providers, which might include minimum security programs, security incident and data-breach notification and response, data-encryption requirements, and data-disposal commitments. Enterprises should review service provider contracts annually to ensure they include the requirements.
Control 16: Application software security
Manage the security life cycle of in-house developed, hosted, or acquired software to prevent, detect, and remediate security weaknesses before they affect the enterprise. Organizations should also use standard, industry-recommended configuration templates to harden underlying servers, databases, and web servers. This also applies to cloud containers, platform-as-a-service components, and SaaS components.
Control 17: Incident-response management
Key roles and responsibilities should be assigned for incident response, including staff from legal, IT, information security, facilities, public relations, human resources, incident responders, and analysts, as applicable. The plan should be review annually or when significant enterprise changes occur that could affect incident response.
RMF Incident Response severity/priorities:
- CAT 0 - Exercise/network defense testing
- CAT 1 - *Unauthorized access
- CAT 2 - *Denial of Service (DoS)
- CAT 3 - *Malicious code
- CAT 4 - *Inappropriate usage
- CAT 5 - Scans/probes/attempted access
- CAT 6 - Investigation
Control 18: Penetration testing
A penetration testing program should simulate the actions of an attacker to identify and exploit weaknesses among people, processes, and technology. The program should be appropriate to the size, complexity, and maturity of the enterprise. Vulnerabilities should be remediated based on the enterprise’s policy for remediation scope and prioritization.
Models & Lifecycles
Focus of security awareness training:
- Senior management: risk to the organization and the laws and regulations that affect the organization.
- Middle management: policies, standards, baselines, guidelines, and procedures that affect security.
- Technical staff: configuring and maintaining security controls, including how to recognize an attack when it occurs.
- Regular staff: responsibilities regarding security for performing day-to-day tasks in a secure manner.
FERMA (Federation of European Risk Management Associations) provides guidelines for managing risk in an organization.
The “PASTA” methodology provides a seven-step process for analyzing applications to align business objectives and technical requirements. This method provides a threat identification, enumeration, and scoring process. It is intended to provide an attacker-centric view of the application and infrastructure from which defenders can develop an asset-centric mitigation strategy.
SABSA, COBIT and TOGAF together make up the Enterprise Security Architecture:
The Open Group Architecture Framework (TOGAF) is an enterprise architecture framework that is based on four interrelated domains: technology, applications, data, and business. They have a certification on that.
Sherwood Applied Business Security Architecture (SABSA) is a framework in addition to a methodology in that it prescribes the processes to follow to build and maintain the architecture. It uses the six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers (operational, component, physical, logical, conceptual, and contextual). The SABSA (Sherwood Applied Business Security Architecture) is a “customizable” framework and methodology for enterprises, based on business requirements (like NIST for private businesses). The framework uses six communication questions (What, Where, When, Why, Who, and How) that intersect with six layers of Enterprise Security Architecture (ESA) (operational, component, physical, logical, conceptual, and contextual):
COBIT: Auditors’ Control Objectives for Information and Related Technology (COBIT) is a set of control objectives used as a framework for IT governance.
- Provide stakeholder value
- Holistic approach [end-to-end]
- Dynamic governance system
- Governance distinct from management
- Tailored to enterprise needs
- End-to-end governance system
The Zachman Framework is a two-dimensional model that intersects communication interrogatives (What, Why, Where, and so on) with various viewpoints (Planner, Owner, Designer, and so on).
The ISO/IEC 27000 Series establishes information security management systems (ISMS) family of standards published jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC). “ISO/IEC 27000:2018” is an Overview and vocabulary standard that references 4 “normative requirements” that are the basis of audits:
- ISO/IEC 27001:2013 - Information security management systems — Requirements
- ISO/IEC 27006:2015 - Requirements for bodies providing audit and certification of information security management systems
- ISO/IEC 27009:2016 - Sector-specific application of ISO/IEC 27001 — Requirements
- ISO/IEC 27701:2019 - Security techniques — Extension to ISO/IEC 27001 and ISO/IEC 27002 for privacy information management — Requirements and guidelines
Each doc is purchased for $124 USD. There are also 11 code of practice, and 41 guidelines.
The Trike methodology is an implementation model created and then analyzed to produce a threat model. Risk values are assigned to the identified threats. Mitigating controls are assigned to the vulnerabilities that lead to the identified threats.
Security program life cycle:
- Plan and Organize
- Implement
- Operate and Maintain
- Monitor and Evaluate
- Stakeholder refers to any individuals, teams, and departments, including groups outside the organization, with interests or concerns that should be considered.
- View refers to the representation of the system from the perspective of a stakeholder or a set of stakeholders.
- Viewpoint is a template used to develop individual views that establish the audience, techniques, and assumptions made.
- Architecture describes the organization of the system, including its components and their interrelationships along with the principles that guided its design and evolution.
- Architectural description (AD) refers to the set of documents that convey the architecture in a formal manner.
Software Capability Maturity Model (SCCM) - REMEMBER: Memonic: I Read Data Maps Online:
- Initial (chaotic, ad hoc, individual heroics) - the starting point for use of a new or undocumented repeat process.
- Repeatable - process is at least documented sufficiently such that repeating the same steps may be attempted.
- Defined - the process is defined/confirmed as a standard business process.
- Managed/Capable - the process is quantitatively managed in accordance with agreed-upon metrics.
- Optimized - process management includes deliberate process optimization/improvement.
Like the Capability Maturity Model Integration (CMMI) addresses development, services, and acquisitions.
Process improvement approaches:
-
Six Sigma includes methodologies DMAIC (Define, Measure, Analyze, Improve existing, Control process) or DMADV (Define, Measure, Analyze, Design, Verify new customer)
-
Control Objectives for Information and Related Technology (COBIT) is a security controls development framework that uses a process model to subdivide IT into four domains: 1) Plan and Organize (PO), 2) Acquire and Implement (AI), 3) Deliver and Support (DS), and 4) Monitor and Evaluate (ME).
-
Department of Defense Architecture Framework (DoDAF) is an architecture framework that organizes a set of products under eight viewpoints: Capability Viewpoint (CV), Data and Information Viewpoint (DIV), Operation viewpoint (OV), Project Viewpoint (PV), SerViCes Viewpoint (SvcV), STanDards Viewpoint (STDV), and Systems viewpoint (SV), All Viewpoint (required) (AV).
-
British Ministry of Defense Architecture Framework (MODAF) is an architecture framework that divides information into seven viewpoints: Strategic Viewpoint (StV), Operational Viewpoint (OV), Service-Oriented Viewpoint (SOV), Acquisition Viewpoint (AcV), Technical viewpoint (TV), Systems Viewpoint (SV), All viewpoint (AV).
-
DHS (Department of Homeland Security) is involved in promoting software security best practices. Its Build Security In (BSI) initiative promotes a process-agnostic approach that makes security recommendations with regard to architectures, testing methods, code reviews, and management processes.

System Development Life Cycle:
- Initiate
- Acquire/Develop
- Implement
- Operate/Maintain
- Dispose
Security program lifecycle:
- Plan and organize
- Implement
- Monitor and evaluate (review audit logs)
- Operate and Maintain (perform audits)
IDEAL model: REMEMBER MEMONIC: I Do Every exAm Live
- Initiating - provide business reasons behind change
- Diagnosing - need for changes by analysing current state
- Establishing - plan of action from recommendations
- Acting - develop, test, refine, implement solutions
- Learning - analyzing results and proposing new actions
Information life cycle:
- Create/receive
- Distribute
- Use
- Maintain
- Dispose/store
The process of acquiring software:
- Planning: During this phase, the organization performs a needs assessment, develops the software requirements, creates the acquisition strategy, and develops evaluation criteria and a plan.
- Contracting: Once planning is complete, the organization creates a request for proposal (RFP) or other supplier solicitation forms, evaluates the supplier proposals, and negotiates the final contract with the selected seller.
- Monitoring and accepting: When a contract is in place, the organization establishes the contract work schedule, implements change control procedures, and reviews and accepts the software deliverables.
- Follow-up: When the software is in place, the organization must sustain the software, including managing risks and changes. At some point, it may be necessary for the organization to decommission the software.
Change control process of each change:
- requested.
- approved.
- documented in the change log.
- tested and presented.
- implemented.
- reported to management (CCB)
VIDEO: REMEMBER picmonic: Incident response process: DRMRRRL (drumroll)
- Detect (identify) using monitoring tools, IPs, firewalls, users, notifications
- Respond (triage) in decision to declare a real incident
- Mitigate (correction & containment) with malware - disconnect device
- Report the incident to relevant stakeholders (legal, customers, regulatory)
- Recover (return to normal) from the incident.
- Remediate (root cause) so all components affected by the incident to ensure that all traces of the incident have been removed.
- Lessons Learned review of the incident and document all findings (to prevent reccurence)
Types of Network intrusion systems:
- Network-based Intrusion Detection System (NIDS) - Monitors the network and alerts to potential malicious traffic.
-
Network-based Intrusion Prevention (NIPS) - Monitors the network and blocks potentially malicious traffic.
- Host-based Intrusion Detection (HIDS) - Monitors the host and alerts to potential malicious activity.
- Host-based Intrusion Prevention (HIPS) - Monitors the host and blocks potentially malicious activity.
Incident response:
- Triage: The incident response team examines the incident to see what was affected and sets priorities.
- Investigation: Involves the collection of relevant data.
- Analysis: Where the root cause of the incident is discovered.
- Tracking: Where the source (user or device) of the incident is determined.
- Post-mortem review: Record lessons learned.
- Recovery: Necessary adjustments or enhancements are made to policies and procedures.
NIST 800-61r2 Incident Handling PDF
- Preparation – the preparatory activities related to incident response, such as policy and procedures, and hiring an adequately skilled IR team.
- Detection – intake and incident discovery.
- Analysis – looking at the evidence of a reported potential incident.
- Response = Mitigation
- Containment of damage
- Eradication
- Recovery – returning to normal operations
- Reporting – notifying management and authorities
- Remediation - taking care of other areas that may be vulnerable.
- Post-incident activity - Review and improvement – identifying lessons learned and steps to implement improvements
FIRST (Forum of Incident Response Security Teams) at first.org
Forensic investigation process: REMEMBER:
- Identification - start action log, reviewing audit logs, monitoring systems, analyzing user complaints, analyzing detection mechanisms, signature resolution.
- Preservation - chain of custody standards, imaging technologies, and time synchronization. All while folling chain of custody standards.
- Collection - making system images, implementing chain of custody, documenting the evidence, and recording timestamps. Data reduction.
- Examination determining and documenting characteristics, such as timestamps and identification properties. Examination includes traceability, validation techniques, filtering techniques, pattern matching, hidden data discovery, and hidden data extraction. After the evidence has been fully analyzed using scientific methods, the full incident should be reconstructed and documented.
- Analysis
- Presentation
- Decision
Order evidence should be saved: REMEMBER: ephemeral first
- Memory contents
- Swap files
- Network processes
- System processes
- File system information
- Raw disk blocks
Cohesion is opposite of Coupling
- Low cohesion describes a module that carries out many tasks, making it harder to maintain and reuse.
-
High cohesion describes a software module that does NOT affect many other modules, so is easier to update.
- High coupling describes a module that must interact with many other modules.
- Low coupling describes a module that performs its job without using other modules.
ACID properties: REMEMBER: MEMONIC: Analysts Can Interpret Data
- Atomicity - either all operations are complete or changes are rolled back.
- Consistency - transaction follows an integrity process that ensures that data is consistent in all places where it exists.
- Isolation - transaction separately from each other, does not interact with other transactions until completion.
- Durability is present when, once verified, the transaction is committed and cannot be rolled back.
Polyinstantiation is a process used to prevent data inference violations.
Relationship cardinality means whether a relationship is one-to-one, many-to-one, or many-to-many. High cardinality means a high number of distinct (unique) values in a table column, relative to the number of rows in the table.
Aggregation is a database security concern that arises when a user does not have complete access to sensitive data but can access portions of it.
The domain of a relation is the set of allowable values that an attribute can take, composed of values that can be entered in a column (attribute) of a table (relation).
WASC (Web Application Security Consortium) is an organization that provides best practices for web-based applications along with a variety of resources, tools, and information that organizations can make use of in developing web applications.
To establish a relationship with a third party which accesses organizational assets both remotely and locally:
- Perform a risk assessment on the third party’s network, to determine its compliance with organizational security policies and standards.
- Establish a written security policy with the third party.
- Provide access to internal resources for the third-party personnel.
- Audit the third party’s access to internal resources.
Types of control function:
- Preventive - Reduces the probability or impact of a threat, like firewalls.
- Detective - dentifies attacks as they happen, like surveillance.
- Corrective - Controls how the system responds to an ongoing attack, like system patches.
- Deterrent - Keeps attackers away from the system, like least privilege.
- Recovery - Recovers system from an attack, like backups.
Examples:
- A DBMS is a technical control.
- Operational controls: backup control, software testing, anti-virus,
- Data backups are recovery logical controls.
- Recovery administrative controls do NOT include data backups.
- Server images are both corrective and technical controls.
- Disaster recovery plans are recovery administrative controls.
- Job rotation and background checks are detective administrative controls.
REMEMBER: Risk Resolution:
- Accept - Ignored without resolution. Based on threat severity.
- Avoid - The part of the system containing the issue will be cut.
- Reduce - Issue will be addressed with bug fixes or redesign to reduce or eliminate threat impact and severity.
- Transfer - Issue will be handled by another system or team.
Resilience is the ability of a system, device, or data center to recover quickly and continue operating after an equipment failure, power outage, or other disruption. It involves the use of redundant components or facilities.
DRP (Disaster Recovery Plan) defines “how” - implemented when the emergency occurs and includes the steps to restore functions and systems. Includes identification of specific hardware. DRP lifecycle phases:
- BIA (Business Impact Analysis) is a functional analysis of critical and necessary business functions, their resource dependencies, and their level of criticality to the overall organization. Risks. Minimum Operating Requirements (MOR)
- Define strategies
- Define Plans and Procedures
- Train users
- Exercise the plan
- Review and update the plan
- OEP (Occupant Emergency Plan) - a facility-based plan focused on safety and evacuation
- The BCP (business continuity plan) defines “what” – considers all aspects that are affected by a disaster, including functions, systems, personnel, and facilities, and lists and prioritizes the services that are needed.
- A contingency plan provides instruction on what personnel should do until the functions and systems are restored to full functionality.
- A CCP (Crisis Communication Plan)
Strategies:
- Backup & restore - cheapest and slowest
- Pilot Light - cheap but faster
- Warm Standby - costly but quicker to recover
- Active/Active - expensive but quickest recovery time
DRP activation:
- Mitigation
- Preparation (for preparedness)
- Response (activation, execution)
- Recovery toward normalcy
Metrics defined by BIA (Business Impact Assessment): REMEMBER: MTD <= RTO + WRT

- Identify Essential Services & Dependencies
- Determine MTD (Maximum Tolerable Downtime) = Max. total time process can be disrupted
- Determine RPO (Recovery Point Objective) = Maximum tolerable data loss period
- Identify infrastructure and Dependencies
- Determine current RPO & RTO (Recovery Time Objective) = Recovery time to a defined service level, including WRT (Work Recovery Time) = Max. time to verify integrity of systems & data
- Gap Analysis
- Report to management
- Mean time to repair (MTTR) is the average amount of time it takes to get a device fixed and back online.
- Mean time between failure (MTBF) describes how often a component fails on average.
Roles:
- System owners are responsible for the systems on which data resides.
- Data owners own the data
- Data custodian configures the appropriate permissions for user access to the data,
- The system owner determines the parameters that govern the system, such as what types of data and applications can be stored on the system, who owns the data and applications, and who determined the users that can access the data and applications.
Dedicated security mode employs a single classification level.
“System integrity” implies that a system will work as intended.
REMEMBER: Aspects of identity management whereby users are identified, authenticated, and authorized: entities, attributes, credentials, and entitlements.
[MINDMAP] Trusted Computer System Evaluation Criteria (TCSEC) functionality at least once. Enhanced by EU in ITSEC to assurance every time:
- F6 + E6 = A1 = Mathamatically Verified protection
- F5 + E5 = B3 = Mandatory Protection (military) resistant to penetration attempts.
- F4 + E4 = B2 = Structured Protection (military)
- F3 + E3 = B1 = Mandatory Protection (military)
- F2 + E2 = C2 = Controlled access protection
- F1 + E1 = C1 = Discretionary Protection (commercial)
- E0 = D = Minimal Protection
Covert channel analysis is introduced at B2 and above.
Security controls from requirements:
Common Criteria
ISO 15408 2005 = Common Criteria on TOE (Target of Evaluation) for Security Target report satisfies independently verified by the NIAP (National Information Assurance Partnership).
Previous EAL (Evaluation Assurance Levels) 1 - 7 highest: REMEMBER:
- EAL1 = Functionally tested
- EAL2 = Structurally tested
- EAL3 = Methodically tested and checked
- EAL4 = Methodically designed, tested, and reviewed
- EAL5 = Semi-formally designed and tested
- EAL6 = Semi-formally verified, designed, and tested
- EAL7 = Formally verified, designed, and tested
Now “compliant” levels instead:
- Users want the system to operate but ignores security threats.
- Developers use good design practices but security is not a high priority.
- Security configuration is based on good commercial development. This level is the common benchmark for commercial systems, including operating systems and products.
- Security is implemented starting in early design. Provides high levels of security assurance.
- Specialized security engineering provides high levels of assurance. Highly secure from penetration attackers.
- Extremely high levels of security are provided. This level requires extensive testing, measurement, and independent testing.
Security Models
-
The Bell-LaPadula (BLP) model focuses on data confidentiality and controlled access to classified information. It uses a state machine with transition functions to control information flow, characterized by the phrase “write up, read down” (WURD). MEMONIC: Bell. It uses security labels (Top Secret to Public). It was the first mathematical model of a multilevel system for enforcing access control. Not dynamic. It’s a multilevel security model because it allows simultaneous processing of classified information across the security levels.
-
The Brewer-Nash (Chinese Wall) model introduced the concept of allowing dynamic access controls based on a user’s previous actions (conflicts of interest). Based on RBAC.
-
The Clark-Wilson integrity model concerns itself with data integrity by allowing data to be altered only through programs and not directly by users.
-
The Lipner model shares characteristics with the Clark-Wilson model in that it separates objects into data and programs.
-
The Biba Integrity Model describes rules for the protection of data integrity.
-
Graham-Denning model
-
HRU (Harrison-Ruzzo-Ullman) uses ACL matrix of subject roles with columns of objects.
-
The Take-Grant model is represented as a directed graph, called a protection graph. The subjects and objects of the computer system are the vertices and the access rights of subjects to objects are represented by arcs.
-
The Goguen-Meseguer model is the foundation of the noninterference model. With this model, the list of objects that a subject can access is predetermined.
-
The Sutherland model defines a set of system states, initial states, and state transitions. Using these predetermined secure states, the Sutherland model maintains integrity and prohibits interference.
TCB RMC
The TCB (Trusted Computer Base) [MINDMAP] comprises the components (hardware, firmware, and/or software) that are trusted to enforce the security policy of the system that, if compromised, jeopardize the security properties of the entire system.
The RMC Reference monitor Concept has active Subject and passive Object, with Rules component enforces access controls on an object.
- A PLD (programmable logic device) is an integrated circuit with connections or internal logic gates that can be changed through a programming process.
- A FPGA (field-programmable gate array) is a type of PLD that is programmed by blowing fuse connections on the chip or using an antifuse that makes a connection when a high voltage is applied to the junction.
- Flash memory is a type of electrically programmable ROM.
- Firmware is a type of ROM where a program or low-level instructions are installed.
Multithreading allows multiple tasks to be performed within a single process. A thread is a self-contained sequence of instruction that can execute in parallel with other threads that are part of the same process. Multithreading is often used in applications to reduce overhead and increase efficiency.
Multitasking …
A protection domain is memory space isolated from other running processes in a multiprocessing system.
State machine models:
- A state machine model examines every possible state the system could be in and ensures that the system maintains the proper security relationship between objects and subjects in each state.
- The multilevel lattice and information flow model types focus mainly on information flow. The multilevel lattice model was developed mainly to deal with confidentiality issues, and the information flow model focuses on controlling information flows that relate two versions of the same object.
- A non-interference model is less concerned with the flow of information and more concerned with a subject’s knowledge of the state of the system at a point in time; it concentrates on preventing the actions that take place at one level from altering the state presented to another level.
- A matrix-based model organizes tables of subjects and objects indicating what actions individual subjects can take upon individual objects.
Cryptography
[MINDMAP]
Cryptographic key life cycle:
- Creation
- Initialization
- Distribution
-
Activation
- Inactivation
- Termination
PROTIP: Creation before Initialization; Activation after Distribution.
Cipher strategies:
-
Substitution exchanges one byte in a message for another. The key is the shift pattern, as in the “Caesar cipher”.
-
A running key cipher uses a physical component, usually a book, to provide the polyalphabetic characters. All the other options are substitution ciphers.
-
Confusion substitutes values during each round of encryption, on the entire key. As in RC4 stream ciphers.
- Transposition shuffles or reorders plaintext to another place in the block. The key is the transposition code.
-
Diffusion changes the order/location of plaintext within the ciphertext through multiple rounds, for block ciphers. Dissipates redunancy such as “u” after “q”.
- Key stretching to output an enhanced (stronger) key
A salt is a non-secret, random value that’s used to ensure that the same plaintext will not consistently hash to the same output value; A salt is used to prevent pre-computation attacks such as Rainbow Tables (hash of passwords).
A nuonce (“number used once”) is typically used to prevent replay attacks. A nounce is typically a randomly generated value associated with a message in a cryptographic scheme, and must be unique within some specified scope (such as a given time interval, or a session).
Steganography:
- Distortion techniques are when the knowledge of original cover in the decoding process is essential at the receiver side.
- Least significant bit steganography is when some or all the bits or bytes inside an image are replaced with bits of the secret message. quality of the image is degraded.
- Transform domain techniques are when secret information is embedded in the frequency domain of the signal.
- Statistical methods encode information by changing several statistical properties of a cover.
- Linguistic steganography hides a message in a nonobvious way like within another file.
- Visual and text semagrams hide a message using signs or symbols that look innocuous.
- Open codes, which include jargon code and covered ciphers, hide a message in a legitimate looking carrier, sometimes called overt communication.
- The payload is the message that is hidden.
- The cover medium is the file or object before the message is hidden within it.
- stego medium is the file or object after the message has been hidden.
-
The carrier is the method of transmitting the stego medium (Email, Instagram, Facebook).
- Due care means an organization has taken the necessary steps to protect the organization, its resources, and personnel.
- Due diligence means an organization has evaluated information to identify vulnerabilities, threats, and issues related to risk.
Model:
- A state machine model examines every possible state the system could be in and ensures that the system maintains the proper security relationship between objects and subjects in each state.
- The non-interference model is less concerned with the flow of information and more concerned with a subject’s knowledge of the state of the system at a point in time; it concentrates on preventing the actions that take place at one level from altering the state presented to another level.
- The matrix-based model organizes tables of subjects and objects indicating what actions individual subjects can take upon individual objects.
- The multilevel lattice model was developed mainly to deal with confidentiality issues and focuses mainly on information flow.
- The information flow model focuses on controlling information flows that relate two versions of the same object.
Ciphers:
- A concealment cipher occurs when plaintext is interspersed somewhere within other written material. Also called “Null” cipher.
-
Vigenere cipher VIDEO was used by US Confederates using a brass cipher disk. It aims to defeat simple frequency analysis.
- A running key cipher uses a physical component, usually a book, to provide the polyalphabetic characters.
- Enigma
- “Lucifer” was created by IBM and used a Feistel cipher a framework to build ciphers. based on DES. Used by TwoFish. Its innovation is decryption.
Kerckhoff’s Principle - the only safe part is the key.
- discrete logarithms ?? https://crypto.stanford.edu/pbc/notes/crypto/factoring.html
REMEMBER Algorithms: https://competitions.cry.yp.to/aes.html
http://thedigitalstandard.blogspot.com/2009/11/why-fuzzy-hashing-is-really-cool.html
https://www.thesslstore.com/blog/how-do-digital-signatures-work-a-look-at-how-a-pki-signature-works/
Hashing digital signatures:
- MD5 (128-bit)
- RIPEMD-160 (originally based on MD4, obsoleted)
- SHA-1 by NSA (160 bit), SHA-256, 384, 512 VIDEO QUIZ
- Whirlpool 512 hash
Cryptographically strong hash algorithm:
- Argon2id
- scrypt
- bcrypt
- PBKDF2
Symmetric encryption algorithms (same key for encrypt/decrypt, so one time), use a private or secret key that must remain secret between the two parties. It provides confidentiality but NOT authentication or nonrepudiation.
- DES uses a 64-bit block size. 56 bits.
- 3DES,
- AES (Rijndael),
- RC5/RC6,
- Skipjack cipher by NSA Clipper chip in phones. Uses 80-bit key on 64-key blocks.
- Blowfish 32 - 448 bits on 64-bit block size. Uses hex digits of Pi.
- Twofish (written by Bruce Sheiner) have key size 128-, 192-, 256 bits and block size of 128 bits.
- SAFER, CAST-128,
- Serpent
- El Gamal (slowest)
- TEA (Tiny Encryption Algorithm) has 128 bit keys. Presented in Cambridge 1994.
DES was first cracked as part of the DES Challenge (“DESCHALL”) in 1997. The winner of DESCHALL announced they were able to crack a DES encrypted message in 96 days. Then in 2017 a chosen-plaintext attack utilizing a rainbow table was able recover the DES key for a single specific chosen plaintext 1122334455667788 in 25 seconds.
Asymmetic encryption algorithms meaning it uses a public key and a private key (i.e two different, mathematically linked keys). They include both stream-based and block ciphers:
- Diffie-Hellman key exchange published 1976 – one of the first public-key protocols in wide use. Used to exchange crypto keys for symmetric encryption algorithms like AES used by HTTPS.
- RSA is defacto commercial asymmetic algorithm
- ECC (Elliptic Curve Cryptosystem) is US govt. standard asymmetric (efficient) support digital signatures and encryption.
- DSA (???)
-
Knapsack
- IDEA provides a key size up to 128 bits.
- 3DES provides a key size up to 168 bits. 3 costly rounds. Not widely used.
- AES supports a 128-, 192-, or 256-bit (16 byte) block size, weaved through data blocks. Subset of Rijndael, winner of NIST contest for faster in 1998.
-
RC6 (written by Ron Rivest) provides the largest key size up to 2,048 bits. From NSA. RC6 supports a 32-, 64-, or 128-bit block size.
- Quantum crypto replaces the 1 and 0 of binary computing with multidimentional qubits for faster mathematical solutions.
Rounds of computations: REMEMBER:
- HAVAL performs 3, 4, or 5
- MD5 performs 4
- IDEA performs 8
- AES (Rijndael) performs 14
- Twofish performs 16
- Tiger performs 24
- Skipjack performs 32
- SHA-256 performs 64
Block symmetric cipher modes use of IVs to ensure that patterns are not produced during encryption. But IVs are not modes.
- Block ciphers are generally less susceptible to security issues.
-
Block ciphers are generally used more in software implementations.
- ECB (Electronic Code Book) blocks have no relationship with other blocks. Least secure but fastest because it doesn’t use initialization vector. Used for small random code.
- CTR (DES CounTeR Mode) turns into a string cipher used in IEEE 802.11i which details security mechanisms. Has best balance of speed and security.
- CBC (Cipher Block Chaining) can have pipeline stalls
- CFB (Cipher FeedBack)
- GCM (Galois field/Counter Mode) parallel 128 bits https://www.wikiwand.com/en/Galois/Counter_Mode
Stream ciphers are generally cheaper to implement than block ciphers.
- RC4 is a symmetric stream cipher, so does not have a block size.
VIDEO: Hybrid cryptography combines the convenience of a public-key cryptosystem with the efficiency of a symmetric-key cryptosystem. Public-key cryptosystems are convenient in that they do not require the sender and receiver to share a common secret in order to communicate securely:
- The symmetric algorithm provides keys used for encryption.
- The symmetric keys are passed to the asymmetric algorithm, which encrypts the symmetric keys and automatically distributes them.
- The message is encrypted with the symmetric key.
- Both the message and the public key are sent to the receiver.
- The receiver decrypts the symmetric key and uses the symmetric key to decrypt the message.
Implementation of Confusion is the process of changing a key value during each round of encryption.
- 3DES-EEE3 encrypts each block of data three times, each time with a different key.
- 3DES-EDE3 encrypts each block of data with the first key, decrypts each block with the second key, and encrypts each block with the third key.
- 3DES-EDE2 encrypts each block of data with the first key, decrypts each block with the second key, and then encrypts each block with the first key.
- 3DES-EEE2 encrypts each block of data with the first key, encrypts each block with the second key, and then encrypts each block with the third key.
PKI (Public Key Infrastructure):
- A subject is an entity that seeks to have a certificate validated.
- A target is a path to a public key.
- A verifier is an entity that verifies a public key chain.
- A trust anchor is a public key that verifies the certificate used in a digital signature.
For data in use within memory flushing: Homomorphic encryption allows computations to be performed on encrypted data without first having to decrypt it. It can be used for privacy-preserving outsourced storage and computation. This allows data to be encrypted and out-sourced to commercial cloud environments for processing, all while encrypted. Even if a service provider’s system is compromised, the data would remain secure.
HSM
Hierarchical storage management (HSM) is type of backup management system that provides a continuous online backup by using optical or tape “jukeboxes.”
RAID
RAID (Redundant Array of Independent Disks): parity information is used to regenerate the data in the case of a single drive failure.
- RAID-0 Striping of data parts over 2 drives
- RAID-1 Mirroring of 2 drives
- RAID-10 Mirroring+Striping
- RAID-2 stripes the data across all drives at the bit level rather than the byte level.
- RAID-3 parity information is written to a single dedicated drive. Data is written across all drives like striping.
- RAID-5 Parity information is written across all drives like striping as well. Min. 3 drives?
- RAID-6 Parity of 2
- RAID-7 enables the drive array to continue to operate if any disk or any path to any disk fails. The multiple disks in the array operate as a single virtual disk.
Network Protocols
CHAP (Challenge Auth Protocol) from Microsoft negotiates a 3-way handshake asymmetric algorithm to support mutual auth. can randomly require re-auth. Based on the username and password, so is vulnerable.
FHRP (First Hop Redundancy Protocol) for shared IP routing redundancy VRRP group
RARP (Reverse Address Resolution Protocol) when communicating for the first time to find the IP address matching the MAC.
OCSP (Online Certificate Status Protocol) is the Internet protocol that obtains the revocation status of an X.509 digital certificate. A certificate revocation list (CRL) contains a list of all the certificates that have been revoked. In reality, many browsers have stopped accessing it. Pinned.
Key clustering occurs when different encryption keys generate the same ciphertext from the same plaintext message. Cryptanalysis is the science of decrypting ciphertext without prior knowledge of the key or cryptosystem used. A keyspace is all the possible key values when using a particular algorithm or other security measure.
A TPM (Trusted Platform Module) protects the contents of an encrypted hard drive by storing the decryption key in the host computer. If the hard drive is removed, the data cannot be decrypted.
Secure Electronic Transaction (SET) was used to verify credit card transactions in 1966.
SAML (Security Assertion Markup Language) is an XML-based open standard data format for exchanging authentication and authorization data between parties, in particular, between an identity provider and a service provider.
OVAL (Open Vulnerability and Assessment Language) is a standard written in XML that provides open and publicly available security content. Its purpose is to standardize information between different security tools.
Memory:
- Associative memory searches for a specific data value in memory rather than using a specific memory address.
- Indirect addressing is the type of memory addressing where the address location that is specified in the program instruction contains the address of the final desired location.
- Absolute addressing addresses the entire primary memory space. Implied addressing refers to registers usually contained inside the CPU.
- A memory leak occurs when a computer program incorrectly manages memory allocations, which can exhaust available system memory as an application runs.
Processes:
A process is a series of actions or steps taken in order to achieve a particular end. Organizations will define individual processes and their relationship to one another.
Confinement describes processes confined to only read from and write to certain memory locations and resources. Confinement is usually carried out using the operating system, through a confinement service, or using a hypervisor.
The bounds of a process set limits on the memory addresses and resources the process can access. The bounds logically segment memory areas for each process to use.
For list of ports, see my https://wilsonmar.github.io/ports-open
MPLS is a protocol-independent transport mechanism. Uses labels, but not for IP routing.
Convergence to use IP protocol for a variety of formats (data, voice, etc.)
PROTIP: TOOL: When using a USB power source only for power, block its ability to transfer data by using a “USB condom”. PortaPaw has 4th gen USB-A and as a USB-A to USB-C converter.
IDS (Intrusion Detection System)
- Blocks autorun when USB are attached, a prolific infection vector
- HIDS (Host-based IDS) on servers
- A heuristic-based (or rule-based) IDS is an expert system that uses a knowledge base, inference engine, and rule-based programming.
- A signature-based IDS analyzes traffic and compares it to attack or state patterns, called signatures, that reside within the IDS database.
- A traffic anomaly-based IDS tracks traffic pattern changes. All future traffic patterns are compared to the sample.
- An anomaly-based IDS analyzes traffic and compares it to normal traffic to determine if said traffic is a threat.
- An application-based IDS is a specialized IDS that analyzes transaction log files for a single application.
Better to use a sandboxed lab system (sometimes referred to as a “sheep dip”).
Backups:
- GRS (grandfather-father-son) backup rotation scheme Three sets of backup media
- ASR (Automated System Recovery) from disk image to restore
- Remote journaling
- Electronic vaulting - files copies auto transmitted to backup location
- Disk shadowing - written to independent disks, transparent to the user
RAM
- DRAM (Dynamic Random Access Memory) capacitors
- SRAM keeps data stored as long as it has power
- SDRAM (Synchronous Dynamic Access Memory) access commands simultaneously,
- DDR (DD2, DD3, DDR4)
Physical Security (DOMAIN 3)
[MINDMAP]
Strategies: Deter, Delay, Detect, Assess, Respond. Acronym?
CPTED (Crime Prevention Through Environmental Design):
- natural access control
- natural territorials reinforcement
-
natural surveillance
- People protect territory they feel is their own
- People have a certain respect for the territory of others
- Intruders do not want to be seen
- Limiting access discourages intruders and/or marks them as intruders
Perimeter of two lines: sterile zone
- Fail-Safe protects human life over systems (opening doors after a power failure)
-
Fail-Secure locks the system for default secure when a failure occurs (doors lock after power failure) – prioritizes systems over human life
- Fail-Open ensures Availability to continue to operate when a failure occurs
- Fail-Close closes (terminates/shuts all non-critical) processes when a failure occurs
Avoid Single point of failure. The weakest link jeopardizes the whole.
Gates:
- Class 1 gates are suitable for residential use.
- Class 2 gates are suitable for commercial usage.
- Class 3 gates are suitable for industrial usage.
- Class 4 gates are suitable for restricted areas.
Alternative sites:
- A redundant site provides a site that is recoverable in the least amount of time and will allow the organization to have the most control of the resources.
- A hot site contains telecommunications and computers and is the most expensive alternative site. It takes the shortest amount of time to recover. Has Backups??
- A cold site does not contain any computers or telecommunications equipment. It does contain wiring, heating and air, and raised flooring. It is much cheaper than a hot site. However, it takes much longer to recover.
- A warm site contains telecommunications equipment but no computers and is cheaper than a hot site but more expensive than a cold site. It takes longer to recover than a hot site but shorter to recover than a cold site.
- A tertiary site provides an alternate in case both the primary and hot site, warm site, or cold site is unavailable.
Fail-over testing:
- A full-interruption test involves a hard switchover from the primary facility to the alternative facility.
- A structured walk-through test is a representative of each department or functional area thoroughly reviews the business continuity plan’s accuracy.
- A functional drill tests a single department to see whether the department’s disaster recovery plan (DRP) is complete.
- An evacuation drill has personnel follow the exiting or shelter-in-place guidelines for a particular disaster type.
Fire extinguisher classes and suppression:
- Class A - ordinary combustibles (paper, wood) - Water, soda acid powders
- Class B - flammable liquids and flammable gases - CO2, Halon, soda acid
- Class C - electrical equipment - CO2, Halon
- Class D - combustible metals - Dry powder
- Class K - cooking oil or fat (grease, oil) - Alkaline mixture
Incipient smoke detection detects chemicals released during early stage of fire.
A dry pipe system (filled with pressurized air. Preaction extinguisher pipe sprinkler heads holds a thermal-fusible link that melts before the water is released. This is currently the recommended system for computer rooms.
Locks:
- A warded lock has a spring-loaded bolt with a notch in it. The lock has wards or metal projections inside the lock with which the key will match and enable opening the lock.
- A tumbler lock has more moving parts than the warded lock, with the key raising the lock metal piece to the correct height.
- A combination lock requires rotating the lock in a pattern, which if correct lines up the tumblers and opens the lock.
- A cable lock has vinyl-coated steel cables that connect to the laptop and then lock around an object.
IAM
Identity provisioning life cycle: The identity must be created first. It is then configured, modified, and monitored. The account is is revoked when no longer needed.
IDaaS (Identity as a Service) Provides a set of identity and access management functions to target systems on customers’ premises and/or in the cloud.
SSO
[MINDMAP]
Shibboleth is a SAML standards-based open source software for web single sign-on and attribute exchange framework.
OAuth2 is an auth framework that enables apps to obtain limited access to user account on an HTTP service.
On top of OAuth 2.0 OIDC (OpenID Connect) version 1.0 from the non-profit OpenID foundation adds an authentication identity layer. It allows users to be authenticated by co-operating sites known as Relying Parties (RP) providing SSO. It’s decentralized in that a traditional central authority is NOT required for authentication. User Passwords are given only to an identify provider (IdP) to confirm, who then vouches for you to various web-based mobile JavScript clients. The spec. is extensible to add discovery of OpenID providers, encryption of identity data, session management, etc. Resource Server OIDC version 2 ??? XACML can be used to define authorization policies (such as managers can view certain docs in their regions).
Access Control IAAA
Entities include a human user, program, service, or computer.
An object is an entity that provides information to a subject.
A subject is an entity that accesses an object to retrieve information about the object.
- Identification is the act of a subject professing an identity to an access control system.
- Authentication (AuthN) is the act of validating a user with a unique identifier by providing the appropriate credentials.
-
Authorization (AuthZ) determines what access you have.
-
Accountability is not a step in access control.
Accountability is the capability of an organization to hold users responsible for their actions. - Remote Authentication Dial-In User Service (RADIUS) is a standard published in RFC 2138.
- Terminal Access Controller Access-Control System Plus (TACACS+) is a Cisco-proprietary method.
MFA (Multi-Factor Authentication) types:
-
Type 1 – Something You Know (remember)– includes passwords, PINs, combinations, code words, or secret handshakes. Anything that you can type, say, do, perform, or otherwise recall when needed falls into this category.
-
Type 2 – Something You Have (possssion) – includes all items that are physical objects, such as keys, smart phones, smart cards, USB drives, and TOTP token devices. (A token device produces a time-based PIN or can compute a response from a challenge number issued by the server.).
-
Type 3 – Something You Are (characteristic) – includes any part of the human body that can be offered for verification using biometrics such as fingerprints, palm scanning, facial recognition, retina scans (used by CLEAR), iris scans, and voice verification.
Other Authentication Factors:
- Somewhere you are - location determined by IP address from wi-fi, GPS.
CAUTION: Knowledge-based authentication (such as previous address, mother’s maiden name) can be cracked by information on social media, data brokers, or vendors on dark web offering information stolen from websites, or by social engineering. PROTIP: Give a different fake mother’s maiden name to each organization who asks, and record that on your 1Password.
“Cognitive” passwords are something information you know, such as your favorite sport, food, etc.
REMEMBER: A password and pin combo includes only a single knowledge authentication factor type, so is not 2FA.
In a MAC (Mandatory access control) environment: VIDEO
- a label is required for each subject and object. Each file is an object. Users are subjects. Clearance is a privilege.
- Rule-based access control is most often used by routers and firewalls to control access to networks.
- The dedicated mandatory access control (MAC) security mode employs a single classification level.
- In the system high mandatory access control (MAC) security mode, all users of the system have the same security clearance but do not all possess a need-to-know clearance for all the information in the system.
- In dedicated security mode, all users can access all data, but they must sign a nondisclosure agreement (NDA) and be formally approved for access on a need-to-know basis.
- In multilevel security mode allows two or more classification levels of information to be processed at the same time.
- In the compartmented security mode, all users must possess the highest security clearance (as in both dedicated and system high security), but they must also have a valid need-to-know clearance, a signed NDA, and formal approval for all information to which they have access.
CAUTION: TOOL: Type a password you type into password.kaspersky.com to see whether it has been found in a dark database of passwords found in the wild and how long it would take to crack that password. However, whatever you type is also logged and stored in their database, which may be accessed by the Russia government.
A capability table lists the access rights that a particular subject has to objects.
PIV (Personal Identity Verification) card, call “CAC” card by the US military. https://piv.idmanagement.gov/ Derived PIV credentials stored securely on mobile device in a TPM.
Type 2 Have Smart Cards
The user private key encrypts a challenge regnerated by the computer.
Type 3 Are Biometrics
Biometrics are PHI (Protected Health Information):
Facial recognition:
- In an eigenfaces facial scan, measurements of facial components are gathered and compared to a set of standard eigenfaces.
-
In an eigenfeatures facial scan, the distances between the facial features are measured and recorded.
- In an iris scan, the colored portion of the eye, including all rifts, coronas, and furrows, are analyzed.
- In a retina scan, blood vessel patterns are analyzed.
-
Vascular scan
- Keystroke dynamics
- Signature dynamics
A characteristics factor for authentication?
Biometric Errors:
- A Type I error – False Rejection Rate (FRR) – increases with sensitivity
- A Type II error – False Acceptance Rate (FAR) – reduces with sensitivity
- Crossover Error Rate (CER) is the point at which FRR equals FAR.
- Throughput rate is the rate at which users are authenticated.
Desktop sessions can be managed through screensavers, timeouts, logon, and schedule limitations. Federal Information Processing Standards (FIPS) Publication 201.2 and NIST Special Publication 800-79-2 are documents that provide guidance on proof of identity.
In Kerberos, the Key Distribution Center (KDC) issues a ticket-granting ticket (TGT) to the principal. The principal sends the TGT to the ticket-granting service (TGS) when the principal needs to connect to another entity.
In a MAC environment, each subject and object is given a label.
- A file in a mandatory access control (MAC) environment is an object.
- A user in an MAC environment is a subject.
- A clearance in a MAC environment is a privilege.
DAC controls are determined by the data owner.
RBAC uses roles to provide access to the data.
Networking: OSI (Open System Interconnect)
[MINDMAP]
Memomnic: Please Do Not Throw Sausage Pizza Away or All People Seem To Need Data Processing
PDUs (Process Data Units)
- Physical bits - Signal through cable hubs, Repeaters, Amplifiers, patch panels
- Data Link frames - MAC address, Logical Link control switching through Ethernet Bridges
- Network packets - Fragment logical addressing routers in IP headers IPv4, IPv6, BGP, OSPF
- Transport segments - Adds protocol for end-to-end TCP, UDP, SSL, TLS ports sockets (no hardware)
- Session data - RPC, tunneling makes a communication session between a service or application on the source device possible with the same service or application on the destination device.
- Presentation data - file format operating system, encryption
- Application data - encapsulation of content HTTP, FTP, SSH, SMTP, API Gateways, Proxy servers doing conversions. It receives the raw data from the application in use and provides services, such as file transfer and message exchange to the application
Access control lists (ACLs) are typically used on routers, which map to layer 3 of the OSI model. The Link layer of the TCP/IP model corresponds to the Data Link and Physical layers of the OSI model. The Transport layer of the TCP/IP model corresponds to the Transport layer of the OSI model.
OSI Resources:
- https://www.youtube.com/watch?v=G7aVKgGUe9c by Professor Messer has graphic illustrations, using WireShark to display details
- https://www.youtube.com/watch?v=HEEnLZV2wGI by Kelly Handerhan uses an analogy of a letter being sent among two buildings where each floor is a layer of the OSI stack.
- https://www.youtube.com/watch?v=H6Jy-P_iFmo by Skillset
- https://www.youtube.com/watch?v=HEEnLZV2wGI by Eli the computer guy on a whiteboard is a bit repetitive
- https://www.youtube.com/watch?v=LANW3m7UgWs by CertBros Real World Example https://www.youtube.com/watch?v=LANW3m7UgWs&list=PLF1hDMPPRqGxpYdo0ctaa7MxfOi9vjs1u&index=3
- https://www.youtube.com/watch?v=Ilk7UXzV_Qc by RealPars
Point-to-Point Tunneling Protocol (PPTP) encapsulates the original LAN packet with another header and trailer, while encrypting the original packet.
Address Resolution Protocol (ARP) resolves IP addresses to MAC addresses. Between layer 2 and 3. RAP (Reverse Address Protocol) resolve MAC address to IP addresses.
Network File System (NFS) is a client/server file-sharing protocol used in UNIX/Linux.
Fibre Channel over Ethernet (FCoE) encapsulates Fibre Channel frames over Ethernet networks.
CSMA/CD (Carrier-sense multiple access with collision detection) Ethernet
Network Address Translation (NAT) was originally designed for IPv4 address conservation, so private IP networks can use unregistered IP addresses to connect to the Internet. The NAT service can operate on a router or by a server to connect two networks together, and translates the private (not globally unique) addresses in the internal network into legal addresses, before packets are forwarded to another network. For additional security, NAT in remote-access environments can be configured to advertise only one address for the entire network to the outside world. (??? Static Address, Dedicated Address, Port Address)
DNP3 is a multilayer protocol used between components in process automation systems in electric and water companies.
IPv4 uses 32 bits.
IPv6 uses 128 bits, has built-in IPSec. Sends Solicited Node (ICMP) Multicast Address unicast to a single node to resolve MAC addr.
concatenated with 104-bit addr. SLAAC (StateLess Address Auto Configuration) to auto configure based on network prefix.
Private addresses: REMEMBER: VIDEO QUZ
- Class A 10.x.x.x/16 (to 10.255.255.255)
- Class B 172.16.x.x/20 (to 172.31.255.255)
- Class C 192.168.x.x/ (to 192.168.255.255) in range of addresses is from 192.0.0.0 to 223.255.255.255.
An IPv4 address is comprised of a network address and a host address. A subnet mask is used to determine what part of the IP address belongs to which. This is important because it determines whether the host will communicate directly with another host or send communication through a router.
802.11ac includes multi-user multiple-input, multiple-output (MU MIMO).
High-Data-Rate Digital Subscriber Line (HDSL) can achieve 1.544 Mbps each way over two copper twisted pairs.
Secure HTTP (S-HTTP) encrypts only a single message. Hypertext Transfer Protocol Secure (HTTPS) establishes a session using a digital certificate and encrypts an entire session. Secure Electronic Transaction (SET) secures credit card transaction information over the Internet.
Internet Protocol Security (IPsec) protects data transmitted over a VPN. HMAC (Hashed Message Authentication Code), used by TLS, includes a symmetric key to provide data integrity and data origin auth.
-
In Transport Mode, the original IP header is retained. The payload data transmitted within the original IP packet is protected, but not the IP header. Encrypted traffic is sent directly between two hosts that previously established a secure IPsec tunnel.
-
In Tunnel Mode, the entire original IP packet is encapsulated to become the payload of a new IP packet. Additionally, a new IP header is added on top of the original IP packet. Since a new packet is created using the original information, tunnel mode is useful for protecting traffic between different networks. This establishs a “tunnel” between two secure IPsec gateways.
TLS 1.3 server cert. is encrypted when sent to client, which hides the name of the server.
In 2016, DROWN vulnerability (Decrypting RSA with Obsolete and Weakened eNcryption) by taking advantage of backward compatibility to force insecure SSLv2 connection downgrade from TLS. So disable obsolete protocol downgrading.
Implementing an IPS is more expensive than implementing an IDS.
- IPS (intrusion prevention system) is a network device that detects a network intrusion and prevents the network intrusion.
- IDS (An intrusion detection system) is a network device that detects network intrusion attempts and either logs the intrusion or contacts the appropriate personnel.
Network access control (NAC) ensures that the computers on the network meet an organization’s security policies. A virtual private network (VPN) is a private network that users can connect to over a public network. Internet Protocol Security (IPsec) is a protocol that secures IP communication over a private or public network. A demilitarized zone (DMZ) is a section of a network that is isolated from the rest of the network with firewalls.
Frame Relay and X.25 are packet-switched technologies.
DSL:
- Symmetric DSL (SDSL), data travels in both directions at the same rate.
- Asymmetric DSL (ADSL) provides faster download speed than upload speed.
- High Bit-Rate DSL (HDSL) offers speeds up to 1.544 Mbps over regular UTP cable.
- Very High Bit-Rate DSL (VDSL) is capable of supporting high-definition TV (HDTV) and VoIP.
DSA (Digital Signature Algorithm) - US standard
Network Penetration test
[MINDMAP]
Penetration test methodology - To simulate an attack on a system or network to evaluate the risk profile of an environment
- Reconnaissance
- Enumeration
- Vulnerability Analysis
- Execution/Exploitation
- Document Findings
Firewalls
A three-legged firewall uses three interfaces, one connected to the untrusted network, one to the internal network, and another to a DMZ.
A kernel proxy firewall is an example of a fifth generation firewall. It inspects the packet at every layer of the OSI model but does not introduce the performance hit that an application layer firewall will because it does this at the kernel layer.
- A stateful firewall forwards packets on behalf of the client. It examines each packet and permits or denies it passage based on many factors, including the state table.
- A proxy firewall hides a packet’s true origin before sending it through another network.
- BA packet-filtering firewall forwards packets based on rules that define which traffic is permitted and denied on the network.
- A bastion host is a hardened machine that usually resides on a demilitarized zone (DMZ) open to the public.
Acceptable Use Policy (AUP)
An AUP (acceptable use policy) details appropriate use of information systems, handling standards, monitoring, and privacy expectations.
Open-source intelligence (OSINT)
Open-source intelligence feeds:
- Malware Information Sharing Project (MISP) [Wikipedia]
- AT&T Security (Alien Vault Open Threat Exchange)
- Spamhaus.org
- SANS ISC Suspicious Domains
- VirusTotal
- us-cert.gov/ncas = NCAS (National Cyber Awareness System) - alerts
Closed-source or proprietary intelligence sources:
- IBM X-Force Exchange
- Recorded Future
- FireEye
Incident Response (DFIR)
DFIR (Digital Forensics and Incident Response) is the process of collecting, preserving, analyzing, and reporting on digital evidence in a way that is legally admissible.
DFIR is useful to answer questions such as:
- Who attacked? (Attribution)
- What is the full scope and impact of the incident?
- How did the attacker get in?
- What steps were taken to escalate the operation?
- How do we ensure this type of attack won’t occur again?
- How do we fully remediate the existing issue to restore trust?
Forest Monsen and Kevin Glisson in Netflix’s Security Intelligence and Response Team (SIRT):
-
open-sourced their “Diffy” Differencing Engine for Digital Forensics in the Cloud tool, which include “osquery” to collect and retain a functional baseline against comparison with all running instances. See https://diffy.readthedocs.io/
-
open-sourced their “Dispatch” crisis management orchestration tool, which leverages existing familiarity with existing tools used throughout an organization (Slack, GSuite, Jira, etc.). Dispatch focuses on managing metadata (incident context) about responses and resources, assembling participants, sending out notifications, tracking tasks, assisting with post-incident reviews, etc. The system builds on past incidents to speed up the resolution of future incidents. It’s made using Python, VueJs, Postgres. Available as a Docker image. See https://hawkins.gitbook.io/dispatch/
UEBA (User and Entity Behavior Analytics), such as Splunk and Microsoft Advanced Threat Analysis provides automated id. of suspicious activity by user accounts and computer hosts, using AI/ML techniques.
tcpdump options:
- -e includes the ethernet header during packet capture
- -n flag shows the IP addresses in numeric form
- -nn shows IP addresses and ports in numeric format
- -X captures the packet’s payload in hex and ASCII formats
Podcasts
-
https://www.hubermanlab.com/podcast by Andrew Huberman
-
https://opensoc.io/ Network Defense Range (NDR) - a free, open-source, and community-driven project that provides a virtualized environment for security professionals to practice their skills in a safe and controlled environment. The NDR is a collection of virtual machines (VMs) that are pre-configured to simulate a real-world network. The NDR is designed to be used by security professionals to practice their skills in a safe and controlled environment.
- PODCAST: SANS.edu Internet Storm Center daily
- SANS Cyber Access
- SANS.edu diary
-
Purdue University’s CERIAS (Center for Eduation and Research in Information Assurance and Security) weekly, YOUTUBE channel
-
Naked Security by Sophos (@nakedsecurity) PODCAST weekly since April 2010 by Product Evangelist Tony Ross.
-
(Brian) Krebs on Security is an investigative report.
-
Schneier.com Blog (@schneierblog)
-
GrahamCluley.com (@gcluley)
SmashingSecurity podcast -
Information Security magazine (@InfosecurityMag)
-
Wired magazine Security articles had Christopher Krebs of Krebs-Stamos Group, was first Director of Cybersecurity at the Department of Homeland Security (fired by Trump), discusses the real threats to voting, from disinformation to intimidation to foreign interference.
-
Darknet Diaries podcast from 2017
-
Dark Reading news website
-
Threatpost news website
-
cybrary.it “The Leading Cybersecurity Professional Development Platform”
-
Metasploit Unleashed by Offensive Security training
-
RoadTripNation.com “Life Hackers” episode on Cyber Security.
-
Pass the Cybersecurity Exam in 3 courses from the Hasso Plattner Institut (HPI) free Open university in Germany.
-
https://thorteaches.com/the-memory-palace-prashant-mohan/ https://thorteaches.com/wp-content/uploads/2021/06/The-Memory-Palace-CISSP-by-Prashant-Mohan-4th-edition.pdf One large PDF of what to remember while taking the CISSP exam.
-
At Cisco, Ron Taylor https://github.com/The-Art-of-Hacking/h4cker (by Omar Santos used in Cisco’s Cyber Defense Clinic Lab catalog
- NetFlow uses less disk space than full packete capture.
Ron also created the https://cyberresiliencebootcamp.com/ uses Cisco’s Cyber Defense Clinic Lab at https://dcloud.cisco.com referencing https://github.com/The-Art-of-Hacking/h4cker
Microsoft’s Security Development Lifecycle
https://flaksec.com/not-all-metrics-are-created-equal-a-gitlab-security-case-study/
Sharing groups
-
Gerald Auger</a>’s Daily Cyber Threat Brief videos within his Simply Cyber YouTube channel.
- https://www.nationalisacs.org/ ISAC (Information Sharing and Analysis Center)
- https://www.nationalisacs.org/member-isacs-3 www.it-isac.org
- https://www.linkedin.com/company/isacindia/
- https://www.linkedin.com/company/it-isac/
- https://www.linkedin.com/company/health-isac/ contact@h-isac.org
- https://h-isac.org/health-industry-cybersecurity-practices/ = Video & PDF of practices
-
https://h-isac.org/wp-content/uploads/2019/09/405-vol1-508.pdf ISAC Certified Basics in Information Security (ICBIS) Course.
-
CISC (Cyber Intelligence Sharing Center)
-
https://www.cio.com/article/2600345/11-steps-attackers-took-to-crack-target.html
- https://podcasts.apple.com/us/podcast/hard-fork/id1528594034 by the New York Times reporters talking about TikTok’s Spying, ChatGPT
Discord channels
Blackhills Infosec https://discord.gg/BHIS VIDEO: John Strand, Ean Meyer, etc run a supportive and valuable server. The one knock is it’s SO big and busy that it can be tough to make connections.
Recon Infosec https://discord.gg/aCArEkb7 is focused on Blue Team and SOC Analyst life. They are a security company led by security people. “guaranteed good times”.
Simply Cyber https://discord.gg/SimplyCyber is Gerald’s server. He strives to make safe spaces for asking questions and getting answers without criticism.
DC Cybersec https://discord.gg/v8ZVhEDv Same as the YouTuber of the same name, DC Cybersec provides real talk on cybersecurity and promotes an inclusive good times community.
Cyber Job Hunting https://discord.gg/tjVaFdgu Led by UK cyber recruiters, this server is all about helping people get jobs in the field and make sure their resume is tight and their mind is right for the job hunting process.
https://medium.com/@KillSwitchX7/cyber-security-discord-servers-7d9c0b7cd7cb
https://www.simplycyber.io/post/5-vetted-discord-cyber-communities-you-should-join
https://github.com/INIT6Source/Hacker_Hiring_Discords
VIDEO: The SKF (Security Knowledge Framework) demo.SecurityKnowledgeFramework.org admin/secure-skf now redirects to https://securityby.design for security-by-design using the OWASP ASVS (Application Security Verification Standard). defensive coding design patterns and code examples for ASP, java, PHP, Flask, Django, Go, Ruby, Nodejs. It provides checklist.
Proxies:
- Browser “Developer Tools”
- https://www.charlesproxy.com
- https://www.telerik.com/fiddler
- https://httptoolkit.tech/
WAF (Web Application Firewall) applies rules to bi-directional HTTP traffic, to detect XSS, SQL injection, Cookie poisoning, Unvalidated input, DoS, web scraping. But not all security issues. It can have performance issues. AKA Application Security Manager. Can be configured as a reverse proxy that accepts traffic on a virtual IP address to proxy the traffic to a back-end server network behind the WAF.
Security Bootcamps Projects
https://upskilltocyber.com/ by https://www.youtube.com/watch?v=JzEeK8JcgpU”>Nicole
https://www.youtube.com/watch?v=7Tiq0mfXcH8 5 FREE Cybersecurity Projects (Home Labs) by MyDFIR
https://www.cyberseek.org/heatmap.html
Masters Degrees
-
Western Governors University Masters in Cybersecurity can be obtained online and for a lot less than others at $4,555 per 6-month term for as many courses as you can complete during that time. They say 70% graduate within 21 months (5 terms) for $18,220 plus MSCSIA eBook & Resource Fee $200.00. There is a one-time MSCSIA Program Fee $150.
Their curriculum is aligned to:
- NICE Workforce Framework of pathway job titles and tasks
- NSA Center of Academic Excellence guidelines
- CISSP Common Body of Knowledge (CBK)
The degree includes passing industry certifications:
- ISC2 Certified in Cybersecurity (CC)
- CompTIA Cybersecurity Analyst (CySA+)
- CompTIA PenTest+
- CompTIA Advanced Security Practioner (CASP+)
- ISACA Certified Information Security Manager (CISM)
Term CUs ID Course Name Type Certification 1 2 D481 Security Foundations ? ISC2 CC, Network+, Security+, CASP+, SSCP, CISSP, CISM, GSEC 1 3 D482 Secure Network Design ? - 1 4 D483 Security Operations ? CySA+, ECIH, GCIH 2 4 D485 Cloud Security ? - 2 4 D484 Penetration Testing ? PenTest+ 3 2 D486 Governance, Risk, and Compliance ? - 3 3 D487 C706Secure Software Design Exam - 3 4 D488 Cybersecurity Architecture & Engineering Essay CASP+ 4 4 D489 C727 C795Cybersecurity Mgmt. (Strategic & Tactical) Essay + Exam CISM 4 4 D490 C700Cybersecurity Graduate Capstone Essay - ? ? C702Forensics and Network Intrusion Exam - ? ? C701Ethical Hacking Exam (External) CEH ? 4 C725Info Sec & Assurance Exam - - https://www.reddit.com/r/WGUCyberSecurity/
- https://socialgrep.com/search?query=mscsia
- CourseHero.com
- VIDEO says he graduated in one term.
Those who graduated:
- https://www.linkedin.com/in/thuatuanlee
- https://www.linkedin.com/in/travis-w-duncan
- VIDEO: Nicole Enesse: “Accredited. Large alumni group getting larger. puts you higher in the invisible caste system. Get higher salary. Helped me get CISSP. Paid for $1,000 CEH.”
-
University of Wisconsin-Whitewater’s Master of Science in Cybersecurity is all online - $678 per credit hour, 30 credits, 10 courses, 2 years = $20,340.
-
SANS Technology Institute Master of Science in Information Security Engineering (MSISE)
-
Coursera online:University of London MSc in Cyber Security
-
Embry-Riddle Aeronautical University Master of Science in Cybersecurity Management & Policy
Harvard CS50
Professor Dr. David J. Malan created several “CS50” courses at Harvard on Edx, with videos on YouTube. Videos can be watched on from the CS50’s Introduction to Cybersecurity course website or on YouTube.
- 0. Securing Accounts
- 0:00:17 Passwords
- 0:35:08 Two-Factor Authentication
- 0:45:21 Credential Stuffing
- 0:47:31 Social Enginering
- 0:50:02 Phishing
- 0:55:21 Machine-in-the-Middle Attacks
- 0:58:38 Single Sign-On
- 1:01:50 Password Managers
- 1:11:56 Passkeys
- 1. Securing Data
- 0:00:17 Securing Data
- 0:02:21 Hashing
- 0:39:52 Secret-Key Cryptography
- 1:03:21 Public-Key Cryptography
- 1:16:14 Digital Signatures
- 1:27:57 Passkeys
- 1:34:47 Encryption in Transit
- 1:40:10 Deletion
- 1:46:28 Encryption at Rest
- 1:50:59 Ransomware
- 1:52:24 Quantum Computing
- 2. Securing Systems
- 0:00:17 Wi-Fi
- 0:02:50 HTTP
- 0:08:50 Packet Sniffing
- 0:13:45 Cookies
- 0:18:32 HTTPS
- 0:37:56 VPNs
- 0:41:11 SSH
- 0:43:48 Ports
- 0:51:33 IP Addresses
- 0:53:33 Deep Packet Inspection
- 0:54:50 Proxy
- 1:03:49 Malware
- 1:12:43 Antivirus
- 1:15:19 Zero-Day Attacks
- 3. Securing Software
- 0:00:17 Phishing
- 0:11:48 Code Injection
- 0:26:54 Stored Attacks
- 0:39:26 SQL Injection
- 0:54:49 Prepared Statements
- 0:59:57 Command Injection
- 1:07:51 Client-Side Validation
- 1:10:31 Server-Side Validation
- 1:12:44 Cross-Site Request Forgery
- 1:28:39 Open Worldwide Application Security Project
- 1:29:11 Arbitrary Code Execution
- 1:40:28 Reverse Engineering
- 1:42:03 Open-Source and Closed-Source Software
- 1:45:15 App Stores
- 4. Preserving Privacy
- 0:00:17 Preserving Privacy
- 0:01:15 Web Browsing History
- 0:03:54 Logs
- 0:06:36 HTTP headers
- 0:16:47 Fingerprinting
- 0:26:35 Session Cookies
- 0:31:00 Tracking Cookies
- 0:33:54 Tracking Parameters
- 0:39:22 Third-Party Cookies
- 0:49:10 Private Browsing
- 0:51:40 Supercookies
- 0:58:01 DNS
- 1:03:21 DNS over HTTPS
- 1:04:21 DNS over TLS
- 1:06:59 Virtual Private Network (VPN)
- 1:10:14 Tor
- 1:14:09 Permissions
- 1:15:43 Location-Based Services
Resources
https://www.microsoft.com/en-us/cybersecurity/content-hub/cybersecurity-policy-framework
https://twitter.com/npm_malware announces malicious packages in the npm registry.
https://github.com/ufrisk/MemProcFS for Digital Forensics. It provides a GUI to view physical memory as DumpLit or WinPMEM read-only files in a virtual file system, perhaps obtained from a PCILeech FPGA.
More on Security
This is one of a series on Security in DevSecOps:
- Security actions for teamwork and SLSA
- Code Signing on macOS
- Git Signing
- GitHub Data Security
- Azure Security-focus Cloud Onramp
- AWS Onboarding
- AWS Security (certification exam)
- AWS IAM (Identity and Access Management)
- SIEM (Security Information and Event Management)
- Intrusion Detection Systems (Goolge/Palo Alto)
- SOC2
- FedRAMP
-
CAIQ (Consensus Assessment Initiative Questionnaire) by cloud vendors
- AKeyless cloud vault
- Hashicorp Vault
- Hashicorp Terraform
- SonarQube
- WebGoat known insecure PHP app and vulnerability scanners
- Security certifications
- Quantum Supremecy can break encryption in minutes
- Pen Testing
- Threat Modeling
- WebGoat (deliberately insecure Java app)