Here’s automation and steps to minimize manual toil and mistakes but build-in secure practices and mechanisms to build global enterprises need. Not just for AZ-104, AZ-500
Overview
- Enterprise Adoption Sequence
- Sales pitches
- PHASE 01. Starter Account
- Ways to get into Azure
- Summary of Automation
- Portal Settings
- PHASE 03. People Information
- PHASE 02. Administrators
- Tenants
- Global Administrators
- PHASE 02. Admins
- Security Jobs To Be Done
- Naming Abbreviations
- Mindsets and Assumptions (Awareness)
- What Does Security Want?
- Out-sourcing
- Security Baselines
- Azure Security Benchmarks (ASB)
- The “Kill Chain”
- MS Defender offerings
- Regulatory Compliance
- Secure Score Posture Action Categories
- In Dev vs Prod
- Azure Government environments
- URLs for Microsoft and Azure
- URL Shortener
- Subscriptions
- Phase 05. Populate Groups Roles Users
- Phase 15. Devices - MS Authenticator app
- Learning Hubs
- Phase 06. IaC (Infrastructure as Code)
- My Azure-quickly repo on GitHub
- IaC Stacks
- IAM
- Licenses
- Built-in User Roles for RBAC
- PHASE 21. Scopes
- Resources
- Phase 10. Resource Groups
- Create Resources: Automation options
- Your own cloud shell
- Encrypted Passwords
- Terraform on Azure
- Create Resource Groups
- PHASE 11. Tags
- More Policies
- Policy creation
- Region = Location
- Access Control (IAM) Roles
- Management Certificates
- Management Group for RBAC
- Limits = Quotas
- Pricing Calculator
- Cloud Shell
- AZ API
- Subscriptions
- Entra ID B2B (Business-to-Business)
- Entra ID B2C (Business to Consumer)
- ARM Templates
- Concise, yet comprehensive
- Bicep PSRule
- CODEOWNERS
- markdownlint
- PSRule samples
- .devcontainer
- ps-rule.yaml
- .github/workflows/azure-analyze.yaml
- .github/workflows/ms-analyze.yaml
- Bicep Docs and Videos
- Better developer experience (DX)
- CLI to create storage account
- Bicep File to create storage account
- main.bicep
- PSRule Policy as Code
- At the Resource Group level
- Microsoft Learn Sandbox
- Playground
- Decompile
- Terraform for Azure
- AAD/Entra Connect
- Azure Policy
- Futures Roadmap
- Azure Import/Export Service
- Delete Subscription, Directory, Tenant
- Resources
- More about Azure
WARNING: There is a massive amount of information about Azure. YouTube videos about certifications only scratch the surface of all that is needed to get an enterprise up and running. Many demonstrate unsafe or inefficient practices with toy examples not suitable for production.
This article is what I’ve learned so far about how an initial administrator gets started in Azure with a starter account to create a global enterprise. Updates on this are sure to follow as I learn more and as Azure evolves.
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
PROTIP: Here, all in one page, are the hands-on, automation and OCM (Organizational Change Management) steps needed to build Azure for a whole global enterprise to minimize manual toil and add secure practices and mechanisms within workflows.
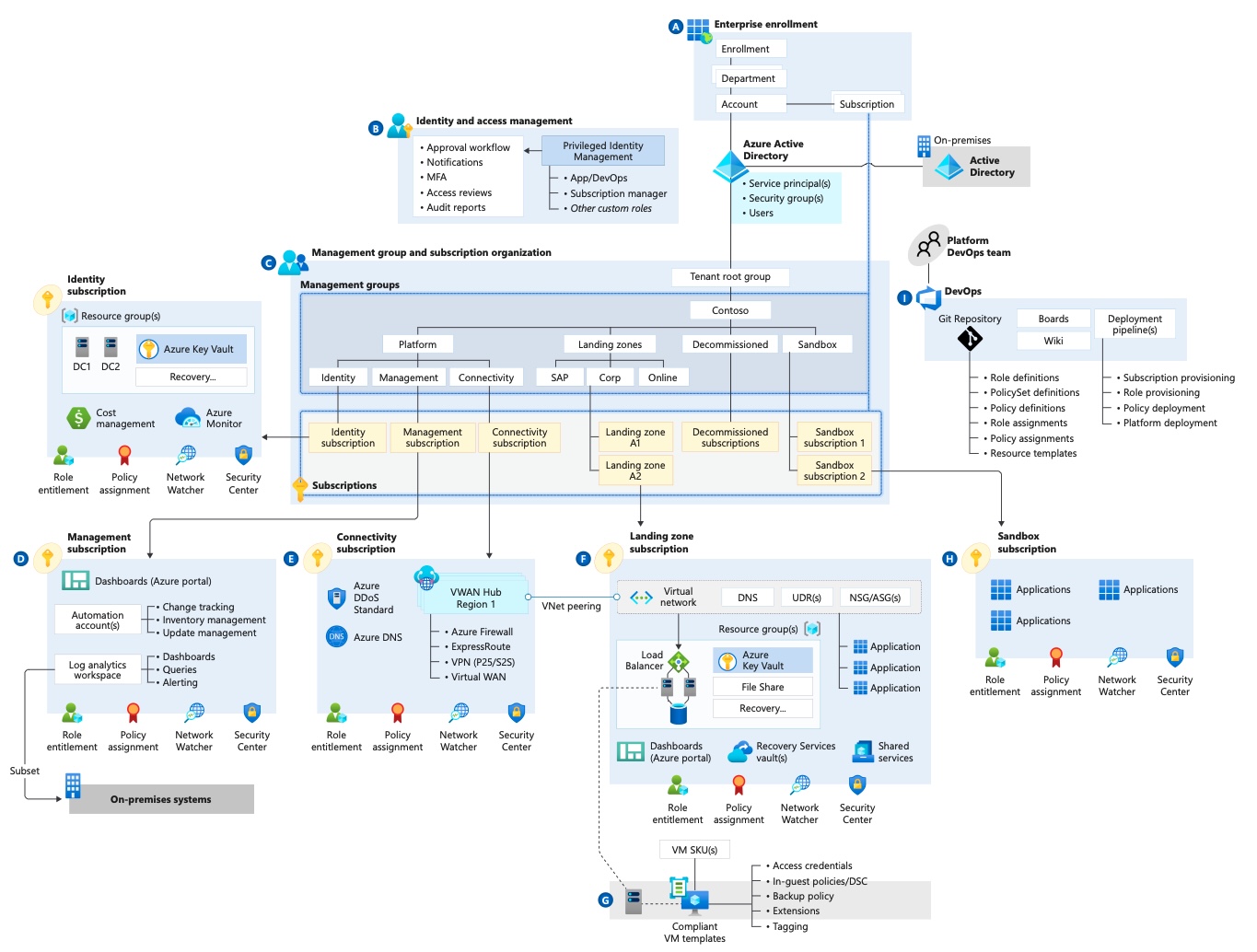
Enterprise Adoption Sequence
 Click here for a step-by-step 1-minute YouTube video (with no sound) about the sequence of work to setup a whole enterprise with Azure technologies in the cloud:
Click here for a step-by-step 1-minute YouTube video (with no sound) about the sequence of work to setup a whole enterprise with Azure technologies in the cloud:
 Click image here for full-screen image generated from animations in my animated PowerPoint file available on GumRoad.
Click image here for full-screen image generated from animations in my animated PowerPoint file available on GumRoad.
PHASES:
-
 First, we describe how the first person working on behalf of an enterprise – the initial Global Administrator – supplies an email to the Azure Portal GUI to get a Starter Azure with an initial Subscription. The default “User Access Admin” role can make any change, so a working set of roles need to be created, using the portal GUI. Skill at this are tested by Microsoft’s AZ-104 certification exam.
First, we describe how the first person working on behalf of an enterprise – the initial Global Administrator – supplies an email to the Azure Portal GUI to get a Starter Azure with an initial Subscription. The default “User Access Admin” role can make any change, so a working set of roles need to be created, using the portal GUI. Skill at this are tested by Microsoft’s AZ-104 certification exam. -
 Global Admins prepare versioned automation, aligned with training assets, to securely setup workstations (laptops) for other admins.
Global Admins prepare versioned automation, aligned with training assets, to securely setup workstations (laptops) for other admins.Automation can make it more necessary to follow naming conventions by constructing Resource names from various elements.
-
 Working within an enterprise requires an understanding of all the people involved: who reports to whom in the people organization, their job titles, and responsibilities, with metadata about each person (such as their geographic location, emails, phone number, carrier for SMS, GitHub account, etc.). This background metadata determines what IAM (Identity and Access Management) and Privileged Access Management structures need to be set up.
Working within an enterprise requires an understanding of all the people involved: who reports to whom in the people organization, their job titles, and responsibilities, with metadata about each person (such as their geographic location, emails, phone number, carrier for SMS, GitHub account, etc.). This background metadata determines what IAM (Identity and Access Management) and Privileged Access Management structures need to be set up.In 2023 Microsoft renamed from “Azure AD” (for Azure Active Directory) with Microsoft Entra ID to reference its “Identity as a Service (IDaaS)” solution (like Okta) for apps across cloud and on-premises.
NOTE: An Azure Resource exists in only one Resource Group (to store metadata). A Resource Group can have resources from different Regions and Subscriptions. Moving resources between Resource Groups is possible, but not between Subscriptions.
-
 Admins would work with Finance to work through financial workflows and oversight of the Payments for billings associated with each Subscription and licenses. Bills are paid for by credit cards or invoices set through a Microsoft salesperson or Cloud Service Provider.
Admins would work with Finance to work through financial workflows and oversight of the Payments for billings associated with each Subscription and licenses. Bills are paid for by credit cards or invoices set through a Microsoft salesperson or Cloud Service Provider. -
 PROTIP: A firm decision on what Licenses the enterprise will pay for can (contiunually) minimizes rework in automation efforts and workflow documentation. A P2 license for each user is needed for enterprises to use Azure securely. Among P2 features are MFA (Multi-Factor) verification, a crucial security feature.
PROTIP: A firm decision on what Licenses the enterprise will pay for can (contiunually) minimizes rework in automation efforts and workflow documentation. A P2 license for each user is needed for enterprises to use Azure securely. Among P2 features are MFA (Multi-Factor) verification, a crucial security feature. -
 Use of automation enables iterations to be quicker because of the written confirmation produced. There are several options for automating Bicep scripts to create resources. This is now favored over
Use of automation enables iterations to be quicker because of the written confirmation produced. There are several options for automating Bicep scripts to create resources. This is now favored over Terraform. Use of Bicep involves transpiling its YAML-formatted contents into the JSON format of ARM templates. Also, Microsoft has stopped development of its “Blueprints”) in favor of Template Specs). -
 IaC Policies aim to identify vulnerabilities and logic errors before resources are deployed and thus possibly exposed.
IaC Policies aim to identify vulnerabilities and logic errors before resources are deployed and thus possibly exposed. -
 Because it takes some effort to configure each resource according to documentation for each service, an important part of automation is to audit scripts.
Because it takes some effort to configure each resource according to documentation for each service, an important part of automation is to audit scripts. -
 other System Administrators from within the people organization are selected, assigned, and trained to be setup and trained by Global Admins to use automation.
other System Administrators from within the people organization are selected, assigned, and trained to be setup and trained by Global Admins to use automation.Administrators are the “gate-keepers” who define IaC (Infrastructure as Code) to setup technical “guardrails” that limit Actions operating on Resource.
-
 System Administrators implement for the portion assigned to them Roles needed to perform Actions on Resources within Scopes defined.
System Administrators implement for the portion assigned to them Roles needed to perform Actions on Resources within Scopes defined.Automatic resource deletion locks are set to prevent one group deleting resources needed by another, such as an ExpressRoute circuit with connectivity back on the on-premises network.
-
 End Users on Entra are usually provisioned by responding to requests from external HR systems such as Workday, SuccessFactors, Oracle Peoplesoft.
End Users on Entra are usually provisioned by responding to requests from external HR systems such as Workday, SuccessFactors, Oracle Peoplesoft. -
 When MFA (Multi-Factor Authentication) is available for each user, users can register their mobile Devices for identity verification.
When MFA (Multi-Factor Authentication) is available for each user, users can register their mobile Devices for identity verification. -
 Using groups enables Administrators to assign a set of access permissions to all members of the group.
Using groups enables Administrators to assign a set of access permissions to all members of the group.P2 licenses enable users to automatically be joined to Security Groups dynamically, which saves manual time and effort in assigning Roles and Policies to each User.
Users can individually request to join groups to gain access. This would require individual approvals as well.
-
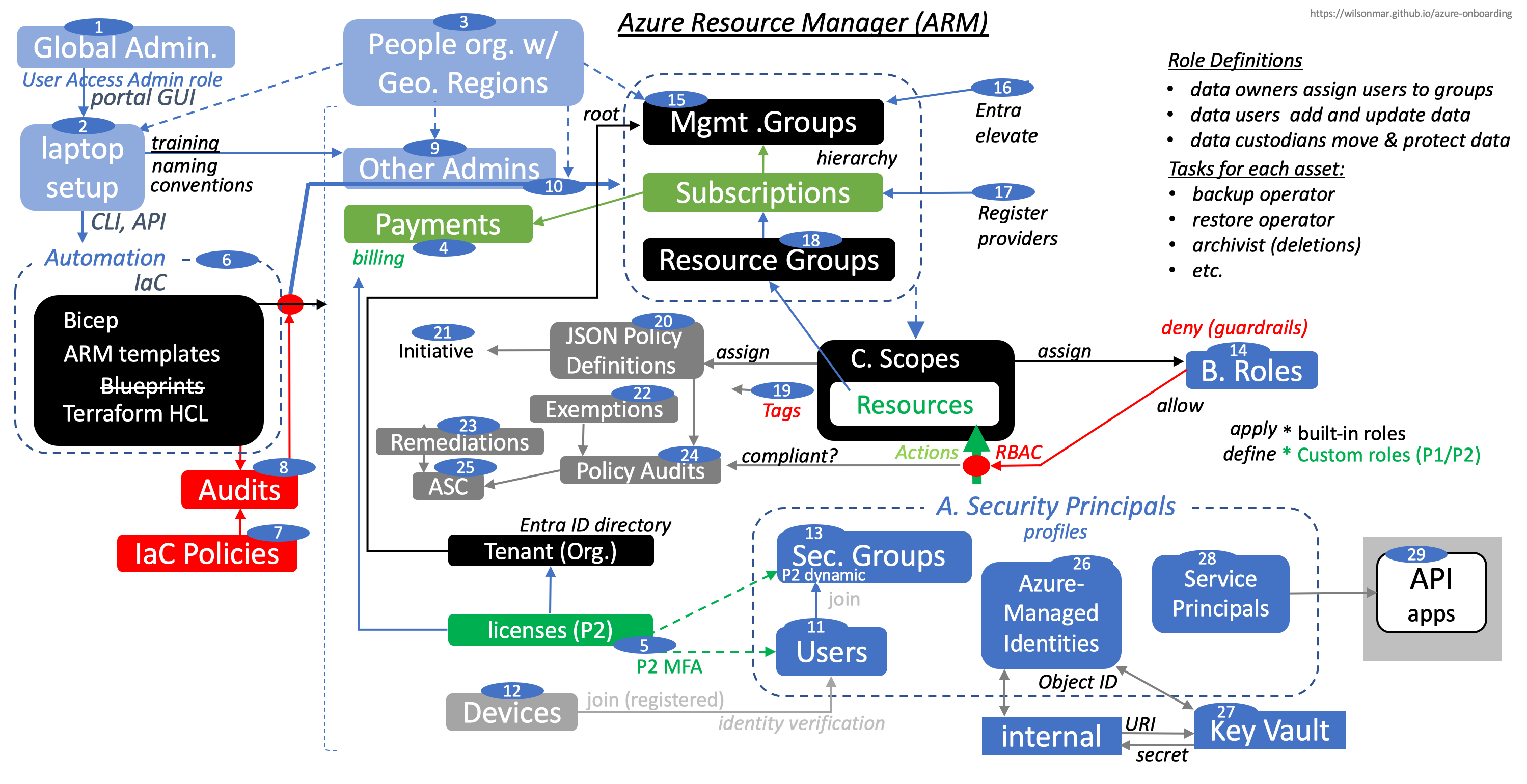
 Azure provides a RBAC (Role-based Access Control) mechanism defined by: the profile defined for each A. Security Principals limited by B. Role Definitions assigned to C. Scopes around resources.
Azure provides a RBAC (Role-based Access Control) mechanism defined by: the profile defined for each A. Security Principals limited by B. Role Definitions assigned to C. Scopes around resources.As for Role Definitions: A P2 license enables custom roles to be defined in addition to built-in roles that apply to Security Principals.
REMEMBER: Roles are about what users do: data owners assign users to groups. data users add and update data. data custodians move and protect data.
Roles relate to the task relevant to assets:
_JobTitle _AssetRole Payroll Supervisor Payroll metrics Payroll Clerk Process Payroll HR Operations Create Payroll Backups Operations Clerk Restore Payroll Backups Archive Manager Delete Payroll Backups Scopes assigned to specific Roles are about the attributes of resources.
Each Scope is defined as a leaf of a hierarchy that consists of a Subscription under a Management Group so each Administrator has their own group to manage.
A set of files are in an Azure Stack folder. Each Stack creates a set of coordinated resources for a particular Scope.
The hierarchy defines the path of escalation if alerts are not addressed on a timely manner.
The hierarchy also defines which supervisor takes over if an Administrator is not available.
To ensure that it’s intentional, the more secure enterprises restrict deletion actions to be performed only by the administrator above the administrator of a cell in the diagram.
The work of the “MyCo” Administrator at the top is largely financial - aggregating bills for enterprise volume discount reconciliation with the cloud vendor. This team would have the statistics to partner with technical people on cost minimization efforts.
Inadvertant Deletion of data can be disastrous. So it helps to have a specialist centrally setup and manage mechanisms for that. For example, individual users who do not have delete permissions can reassign obsolete resources to “Decommissioned”. This is to avoid accidental deletion of resources and enable central review before deletion.
Most enterprises today have a central SOC (Security Operations Center) to monitor and quickly respond to incidents in Production environments (“PRD”).
The Operations (“Ops”) team builds complete Staging (“STG”) environment to conduct systems capacity testing and chaos engineering once the QA team has tested individual components. Each of these teams can be from under different Vice Presidents, to serve as liaisons to those other organizations.
For example, virtual machines (VMs) in a particular Management Group can be limited to being created in specific regions (soverignties). Policies for each management group apply to all nested management groups, subscriptions, and resources.
Paired region backup
Boxes within dotted lines represents the paired region where Azure automatically sends back up data so they can restore everything in case of disaster in any given region. This is a major differentiator for Azure versus AWS which makes each customer do their own backup and recovery.
-
 Management Groups usually map to the people Organization.
Management Groups usually map to the people Organization.PROTIP: Our automation includes using a spreadsheet to define the hierarchy, and loading that into Azure, for both samples in test and to prepare for productive use.
The design begins from the top of the chart at the root of the Tenant Entra ID directory because that’s where Scopes are stored.
-
Entra elevate
 PROTIP: Azure makes it such that a Global Admin make changes to Management Groups after signing into Entra to give themselves the “User Access Admin” role.
PROTIP: Azure makes it such that a Global Admin make changes to Management Groups after signing into Entra to give themselves the “User Access Admin” role.To minimize mistakes and abuse at enterprise scale, repeatability is needed to efficiently set up a whole enterprise full of users and resources. That’s why IaC (Infrastructure as Code) automation is needed.
-
 The Provider to each service used needs to be Registered. For example, use of Entra ID B2C needs to be registered to an Entra ID Tenant.
The Provider to each service used needs to be Registered. For example, use of Entra ID B2C needs to be registered to an Entra ID Tenant. -
 Commands to create each Resource require Resource Group to be specified. Since Resource Groups being created must specify a Subscription, Azure knows how to bill for each Resource.
Commands to create each Resource require Resource Group to be specified. Since Resource Groups being created must specify a Subscription, Azure knows how to bill for each Resource. -
 The most common policy check in IaC is to ensure that Tags are included with every resource so that billing, disposal, and other aspects of every resource are defined.
The most common policy check in IaC is to ensure that Tags are included with every resource so that billing, disposal, and other aspects of every resource are defined.PROTIP: IaC Policies and Policy Definitions should ensure that each Resource in the DEV environment contain at least one Tag for billing. In Production, each Resource should be defined with several Tags.
-
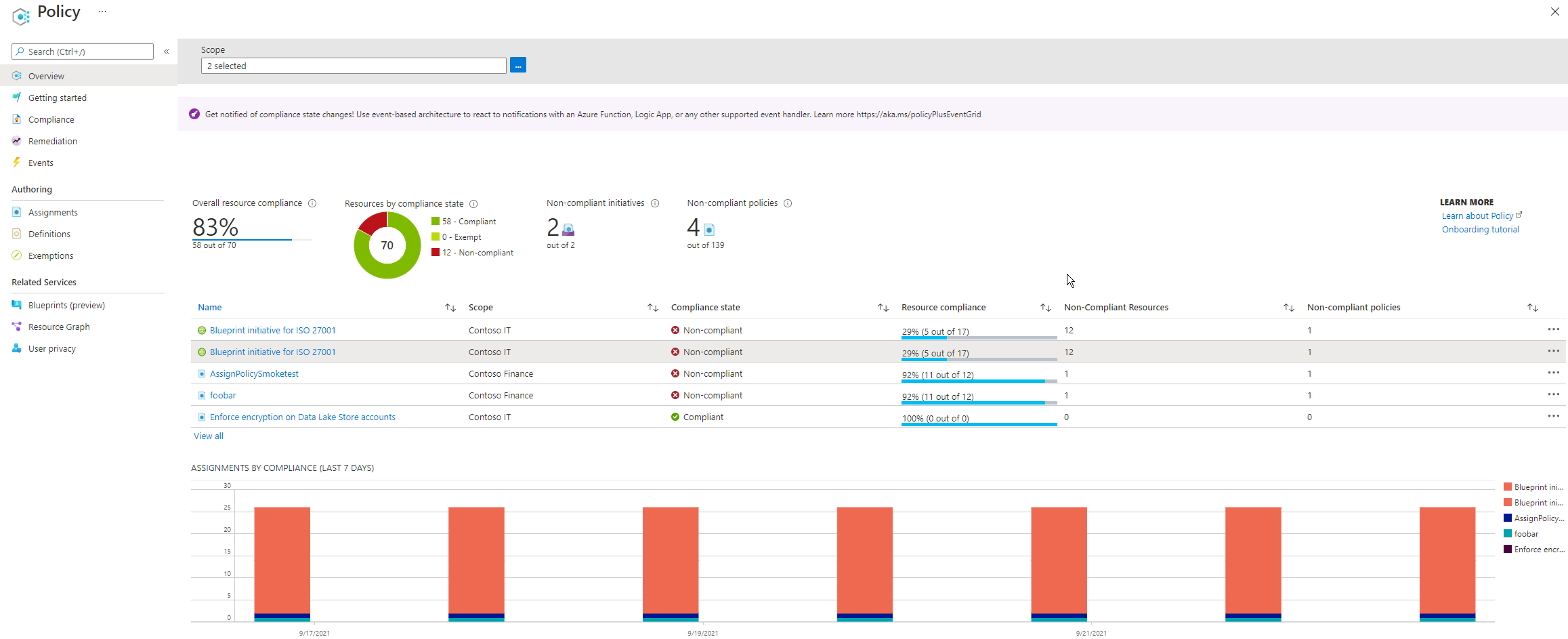
 Policy Definitions are defined in JSON files that define rules assigned by resource Scope.
Policy Definitions are defined in JSON files that define rules assigned by resource Scope. -
 Individual policies are grouped under an Initiative - such as a corporate policy/mandate.
Individual policies are grouped under an Initiative - such as a corporate policy/mandate. -
 ASC (Azure Security Center), or “Security” for short:
ASC (Azure Security Center), or “Security” for short:https://portal.azure.com/#view/Microsoft_AAD_IAM/SecurityMenuBlade/~/GettingStarted
-
 Azure-Managed Identities eliminates the need for developers to leave secret credentials in their code to access internal Azure resources. Instead of static user account keys and connection strings, VIDEO: the unique reference to blobs and such are associated with the caller’s Managed Identity. When its ObjectID is given to the
Azure-Managed Identities eliminates the need for developers to leave secret credentials in their code to access internal Azure resources. Instead of static user account keys and connection strings, VIDEO: the unique reference to blobs and such are associated with the caller’s Managed Identity. When its ObjectID is given to the -
 Key Vault service, it generates its managed identity (based on a Role) that’s then encrypted into a URI used to retrieve secrets. Brilliant! [VIDEO of scripts]
Key Vault service, it generates its managed identity (based on a Role) that’s then encrypted into a URI used to retrieve secrets. Brilliant! [VIDEO of scripts] -
 API-calling applications to access resources such as Storage or web apps.
API-calling applications to access resources such as Storage or web apps.Permanent active access permissions are dangerous to grant because they can be stolen. So Just-in-time temporary access is provided for ad hoc and limited periods of time after approval by a Privileged Role Administrator. The Administrator uses the PIM (Privileged Identity Management) GUI and CLI.
Additional “activation”, such as a multi-factor authentication (MFA) check, is requested if usage is needed outside the usual time of day, use from a specific IP address, and other criteria.
The objective is to minimize the number of users having Instead, Just-in-time access is provided for ad hoc and limited periods of time after approval by a Privileged Role Administrator. The Administrator uses the PIM (Privileged Identity Management) GUI and CLI.
(with Entra ID Governance licensing) provide users Just-in-time access for ad hoc and limited periods of time after approval by a Privileged Role Administrator. The Administrator uses the PIM (Privileged Identity Management) GUI and CLI.
Recap:
 Click image here for full-screen image generated from animations in my animated PowerPoint file available on GumRoad.
Click image here for full-screen image generated from animations in my animated PowerPoint file available on GumRoad.
Sales pitches
For a high-level technical overview from a Sales Engineer, with demos:
SIGN-UP: Microsoft’s LIVE 2-hour Virtual Training Days:
- Azure : Modernize Enterprise Applications [LINKS] makes use of Artilery to generate artificial load on web apps.
- 365
- Security
- Dynamics 365
- Power Platform
mybuild.microsoft.com “Build” conference every year.
PHASE 01. Starter Account
This chapter explains Best Practices and efficiency Tips for all Users.
- Setup & Use Browser Profiles
- Free Subscriptions
- Entra (Azure Active Directory/Azure AD/AAD)
- P1 vs P2 features
- Phone for MFA
- portal.azure.com GUI
- Enterprise discounts
- All URLs for Azure I’ve found
- Acronyms (three letters and otherwise)
Ways to get into Azure
The set of services to create and manage resources (such as network, storage, compute, etc.) in the Azure cloud is called the Azure Resource Manager (ARM for short).
- GUI Portal
- GUI CloudShell
- CLI Bash scripts
- CLI PowerShell scripts
Summary of Automation
-
mac-setup.sh for laptop setup – installing everything needed on your mac with a single command. Then it makes runs simple to repeat and optionally cleans up after runs.
-
org-gen.py generates csv files containing sample values for an organization with a size of your choosing. (100, 1000, 10000, etc.). The data describes a hierarchy of departments, jobs, roles, groups, people, projects, etc. used as the basis for assigning Least-Privilege permissions to resources.
-
org-chart.py generates an organization chart graphic from a csv spreadsheet file.
-
az-info.sh displays the status of various resources in Azure
-
azure-quickly.sh automates the creation of Azure Scopes, Policies, Groups, Users, Resources, etc.
Setup & Use Browser Profiles
Websites (including Azure) store your browser history, what account you logged in, etc. locally in “cookies” associated with your browser account.
That’s how you get returned to the last account used when you go back to a website.
PROTIP: Setup different browser profiles on the same browser, associated with different profile avatars and colors: one for each account (email).
-
Click your browser’s avatar picture at the upper-right corner:
- The Learn account using your personal email (such as at gmail.com).
- The account associated with your Visual Studio benefit (using your work email)
- Each of your work accounts (to do your job as an Administrator).
-
Do the above for each browser (Google Chrome, Microsoft Edge, Firefox, etc.).
Free Subscriptions
DEFINITION: A “Subscription” in Azure is the account for billing to payment options such as a credit card or invoice account setup with a Microsoft salesperson.
-
Some “Exercises” in Microsoft Learn provide FREE “MICROSOFT LEARN SANDBOX” temporary “Concierge” subscription access one or two hours at a time.
-
azuredevopslabs.com/labs/devopsserver/handsonlabs with code at github.com/Microsoft/azuredevopslabs/tree/master/labs/devopsserver/handsonlabs, which provides a quick and easy way to evaluate and test (currently only DevOps and Visual Studio) through virtual environments that do not require any complex setup or installation. You can use virtual labs online immediately for free :)
-
Search for others in Microsoft’s LEARN website:
-
Microsoft offers free student accounts at:
https://azure.microsoft.com/en-us/free/students/
-
CloudAcademy.com licenses include Lab time in some of their monthly subscriptions.
Subscription Offers (deals)
-
Get a “Microsoft Learn” account for $200 of credits to spend in 30 days and also a year of free services. See docs.microsoft.com/en-us/learn/azure/
After that instead of “Pay-As-You-Go”,
-
PROTIP: Obtain Azure credits as a benefit of a monthly license of Visual Studio (even though they don’t intend on using the IDE). Azure Subscriptions (like Netflix, Disney+, etc.) are billed monthly.
- $50/month credits from a $39/mo Visual Studio Professional license
- $150/month credits from a $79/mo Visual Studio Enterprise license
PROTIP: Visual Studio Subscriptions are, as of this writing, NOT offered in the Brazil South and Central India regions, as noted in https://azure.microsoft.com/en-us/regions/offers/.
-
“BizSpark” is Microsoft’s effort to encourage start-ups.
-
CSP (consultants) may charge less than Microsoft due to incentives provided.
-
“Enterprise Agreement Support” are billed using invoices.
-
Consumer sign up for Azure:
https://signup.live.com/signup
SECURITY PROTIP: Use address with a zip code that’s not associated with your home address, and not used for banking.
PROTIP: Microsoft does not force consumers to pay for a subscription with a credit card until 5 or more users or initial free vouchers are used up.
PROTIP: Microsoft no longer accepts debit cards such as from Walmart Bluebird VISA card (by American Express).
PROTIP: Create a separate card sub-account for each cloud account.
Support
- See the list of support tickets here
PROTIP: Avoid using an email that you use for your own banking, shopping, social media, etc. For continuity with a real cloud, you’ll need an email address that you can share and transfer to other people. That’s so at a company, you will need to give someone else the password so that if you’re ever go on vacation (or get run over or thrown under a bus), your organization can continue.
In you’re in an enterprise company, get an email adddress from a corporate assets administrator. A different (service) account is often created for each department of responsibility.
PROTIP: In the name include the month and year in the account name (such as johndoe1901@hotmail.com) for 2019-01 (January). Many create several email accounts because each Azure subscription includes a $200 credit to spend on any service for the first 30 days, free access to Azure products for 12 months.
Entra (Azure Active Directory/Azure AD/AAD)
In 2023, Microsoft rebranded “Azure Active Directory (AAD)” or “Azure AD” to Microsoft Entra ID. [VIDEO]
The word “entra” means “entrance” (enter in) in Italian. It’s a nod to the fact that Microsoft Entra ID is the gateway to Microsoft 365 and Azure services.
When someone signs up for a Microsoft cloud service subscription (such as Microsoft Azure, Office 365, Microsoft Intune, etc.), a dedicated instance of Entra (Azure AD) is created automatically.
READ: Entra pricing.
https://www.microsoft.com/en-us/security/business/microsoft-entra-pricing
- Entra ID External Identities (B2B/B2C) are licensed separately -> Microsoft Entra External ID
Phone for MFA
DOTHIS: Recommend how each user can setup MFA. These options are available:
- Number of MFA denials to trigger account lockout (from 1 to 99)
- Minutes until account lockout counter is reset (from 1 to 1440)
- Minutes until account is automatically unlocked (from 1 to 9999)
P1 vs P2 features
Premium P1 (included in Microsoft 365 E3) features include Password Protection (custom banned password). Dynamic groups require a Premium P1 license.
- Conditional access
- Group assignment to applications
-
Advanced group management (dynamic groups, naming policies, expiration, default classification)
- Cloud app discovery (Microsoft Defender for Cloud Apps)
- Application proxy for on-premises, header-based, and integrated Windows authentication
-
Service level agreements (SLAs)
- Microsoft identity manager user client access license (CAL)
- Cross-tenant user synchronization
-
Advanced security and usage reports
- Automated user provisioning to on-premises apps
-
Automated group provisioning to apps
- Self-service password reset (SSPR)
- Terms of use attestation
- Basic access certifications and reviews
- Basic entitlement management
-
Entitlement management – separation of duties
- Risk level and risk detail fields are hidden to those with just the Entra ID Premium P1 edition.
- Advanced detections (such as unfamiliar sign-in properties) not covered by license appear under the name Sign-in with additional risk detected.
- Privileged identity management (PIM)
Premium P2 (included in Microsoft 365 E5) includes all P1 features plus really cool “Identity Protection” with policies Assignment to all users.
- Identity governance/protection dashboard
- Risk-based Conditional Access (sign-in risk, user risk)
- Machine-learning-assisted access certifications and reviews
- Authentication context (step-up authentication)
- Device and application filters for Conditional Access
- Token protection
- Vulnerabilities and risky accounts
- Risk events investigation, security information and event management (SIEM) connectivity
- Self-service entitlement management (My Access)
- Entitlement management with Verified ID
- Lifecycle workflows
The new $7/person Microsoft Entra ID Governace offering adds:
- Identity governance dashboard
- Entitlement management with Verified ID
- Lifecycle workflows
-
Machine learning assisted access certifications and reviews
-
Multi-factor authentication registration policy to Require MFA
-
User risk remediation policy to require password change, with review of number of users impacted
-
Sign-in remediation policy to automate analysis of signals from each sign-in, both real-time and offline, and calculates a risk score based on the probability that the sign-in wasn’t performed by the user. Administrators can decide based on this risk score signal to enforce organizational requirements. Administrators can choose to block access, allow access, or allow access but require multi-factor authentication. If risk is detected, users can perform multi-factor authentication to self-remediate and close the risky sign-in event to prevent unnecessary noise for administrators.
-
Investigate risks using data in the portal.
- Export risk detection data to third-party utilities for further analysis.
Users on another Entra ID (B2B) or public IDP (B2C).
Office 365 SaaS Subscription
Microsoft 365 subscribers have additional AAD/Entra licensing options:
- Entra ID Free has a 500,000 object limit, which includes MFA for O365 services
-
- $1/mo./user Basic for group-base access management with SLAs
-
- $6/mo./user P1 for conditional access based on device/location & MFA for on-prem. services
-
- $9/mo./user P2 for Identity Protection, Access reviews, Privileged Identity Management
- $9/mo./user P2 for Identity Protection, Access reviews, Privileged Identity Management
-
Sign up for Office 365 Trial at
https://www.microsoft.com/en-us/microsoft-365/enterprise/office-365-e5?activetab=pivot:overviewtab
-
Click the “Try for free” link and go through the verification steps.
IMPORTANT: You are assigned an @onmicrosoft.com</strong> domain and individual account.
-
To view the time remaining within the free period, use your “work account” at:
https://admin.microsoft.com/adminportal/home?#/subscriptions
-
The administrator of the work account emails needs to configure DNS entry at the email server host: TXT name @, TXT value “MS=12234…” with TTL 3600.
portal.azure.com GUI
References:
- DOC:
-
Use your default internet browser (Apple Safari, Microsoft Edge, Google Chrome).
-
On the initial (first time) new Subscription entry pop-up: Azure Advisor
Azure Advisor
On initial entry into the portal, Azure greets you with a pop-up about Azure Advisor.
Azure Advisor provides recommendations by categories of the “Well-Architected (Cloud) Framework”:
- Cost
- Security
- Reliability
- Operational excellence
- Performance
(but not “monitoring”)
Dashboard
-
For Dashboard, hold down G and press D.
In the left menu, where is the menu item for Users (the one most often used by Administrators)?
- PROTIP: Click Dashboard to configure it with Users at the upper-left.
- Get rid of an item by clicking the “…” to “Remove from dashboard” or New Dashboard.
- To rearrange location, click the “…” on any item and select “Customize”.
- Click “Edit” from the command bar to search for Users, Add.
-
Click “Save” at the top.
Portal Settings
-
Click the “wheel” icon at the top for Portal Settings:
-
PROTIP: If you wear glasses on video calls, reduce glare by clicking “Black” for the dark theme. You may not like the putrid yellow font associated with High Contrast:
GUI Navigation Hubs, Panes, Blades
DEFINITION: A Hub is a category for navigation within the left Azure Portal menu that is opened by clicking the upper-left accordion icon alt.
Panes that appear on the right are called “blades”. A Blade is a portion of the page that pops up as you navigate in the portal. (Note: A Blade is contextual and tied to your navigation. This will become more intuitive as you use the portal.)
Opening a series of blades is called a journey.
Dock hamburger menu
-
Click the “hamburger” (home) icon at the upper-left corner for English descriptions of each icon on the left edge.
-
Click the “<” icon at top of the separator to collapse (“dock”) or expand the text of services listed on the left menu.
PROTIP: To set its expansion state permanently, click the ‘settings cog’ icon in the top right of portal and click the ‘Choose your default mode for the portal menu’ option. Setting that to docked or undocked.
Left Dock Keyboard Shortcuts
-
PROTIP: To keep things simple, I arrange the FAVORITES menu item alphabetically.
- App Services
- Advisor
- Entra ID
- Cost Management + Billing
- Function App
- Load balancers
- Monitor
- Security Center
- Storage Accounts
- (0) Virtual Machines
-
??? Click the
star icon so it is gold to enable the service to show on the menu or unselect to remove the service from the bar.
Home
-
Drag and drop the Categories in a stable sequence and position you can mouse to quickly:
Example: I drag the “Billing” icon to the top because I manage the money involved.
VIDEO PROTIP: If you memorize the number of your menu, you’ll never need to mouse to the “hamberger” menu again, avoid being distracted by menu text, and recover screen real estate.
-
Hold down G and press a number to view one of the first 10 menu items.
VIDEO: Many find themselves more productive when they don’t have to reach for the mouse. Keeping hands on the keyboard reduces a distraction. Thus, it’s impressive wizardry during demos.
-
Click the “?” at the top of the page to click Keyboard shortcuts.
In there and in DOCS, “G+.” means while holding down the G key, press the period key, which puts the focus on the “»” icon so you can press Enter to expand or contract the left menu. Press Tab to cycle down the menu.
PROTIP: You can use the G key as if it’s like the Command/Ctrl key because you’re not filling out a form. If you see G appear in a form fill field (such as the browser URL), backspace to clear the field, then press Tab off the form fields and try again.
-
Press Esc to escape from the help window.
-
A reminder of the G key is always present at the top of every Azure screen:
“Search resources, services, and docs (G+/)”, which means hold down G and press / to search.PROTIP: Azure DevOps uses more G keys (and M keys as well).
All Azure Services
-
For
All services, hold down G and press B.
-
Click “All” for a complete of all services Azure has to offer, arranged within the category order on the left menu.
PROTIP: This spreadsheet of each service offering in Azure from the txt file updated monthly from the Microsoft Azure Products Directory by User kobulloc-MSFT. Some services are not available in all regions. and some are in preview.
As of Oct 10, 2023, there are 285 Categories of Azure services (with the number of services in each):
- AI & machine learning - 32
- Analytics - 18
- Compute - 20
- Containers - 9
- Databases - 15
- Developer tools - 9
- DevOps - 10
- Hybrid + multicloud - 15
- Identity - 4
- Integration - 6
- Internet of Things - 22
- Management and governance - 23
- Media - 6
- Migration - 5
- Mixed reality - 5
- Mobile - 11
- Networking - 23
- Security - 17
- Storage - 18
- Virtual desktop infrastructure - 3
- Web - 14
PROTIP: The above gives you an idea of how vast the Azure offering is, and the product names certification aspirants should know.
Full screen toggle
-
To toggle a window to take up the whole screen on Windows PCs: press F11 or Alt+Enter or Windows key + up-arrow. On macOS: hold down the command on the right, control on the left, then F (control+command+F). Repeat the keys to un-maximize. This is equivalent to clicking the green “maximize” icon on the upper-left of each app window or double-clicking on the app’s title bar.
CAUTION: Any window maximized will not be brought up by the keyboard shortcut which cycles through various windows within the app (command+` on macOS; Alt+Tab on Windows PCs). To see the maximized window, you have to cursor near the top edge until the app’s menu appears, then pull down the browser’s Window menu.
QUESTION: How to toggle full screen in Azure like on Netflix, which removes menus, breadcrumbs, and command bar? Alt+Space+X on Windows.
- Switch among windows command+` (at the upper-left corner of the keyboard).
-
To find text on the page, press command+F.
License types of Subscriptions
BTW, billing is associated with Management Subscriptions with names such as “Pay-as-you-go…”
Enterprise discounts
Available to Enterprise customers only: 15% Discounts on Public Prices
First year free services
https://azure.microsoft.com/en-us/free/free-account-faq lists services which Microsoft offers free for the first year:
- Compute: 750 hours of B1S Linux VMs
- Compute: 750 hours of B1S Windows VMs
- Storage: Manage Disks 64 GB x 2
- Storage SQL: up to 250 GB
- Storage File: 5GB
- Storage Blobs: 5 GB
- Cosmo DB up to 5 GB 400 request units
- Network bandwidth: 15 GB outbound data transfer
- AI & Machine Learning services?
TODO: HANDS-ON: Make use of them without spending any money of your own!
PHASE 03. People Information
PROTIP: Python program generates an organization chart graphic from a csv spreadsheet file.
- Occupations for certs
- Azure URLs
- portal.azure.com GUI
- Subscriptions
-
Support
- Automation
- Bicep and GitHub Actions
- My data generator (departments, jobs, roles, groups, people, projects, etc.)
- IAM
-
IAM (Entra ID), groups, federation
- Futures Roadmap
- Resources
- More about Azure
Search for what to “REMEMBER” to pass Microsoft’s Azure professional certification exams.
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
PHASE 02. Administrators
In security, there is a distinction between “data owners” and “data custodians” (who manage the data). An inventory needs to be maintained about who has type of access to what data, for escalations and approvals.
- The Business Managers who own apps and the data they contain.
- The IT Managers who manage the infrastructure (servers, storage, network, etc.) on which the apps run.
- The Administrators who manage the apps and the data they contain.
In Azure, there is a distinction between “subscription owners” and “subscription administrators” (who manage the subscription).
Microsoft's "Security Service Edge (SSE)" solution facilitates applying Conditional access policies across organizational resources and apps.
REMEMBER: Azure itself does not allow Global Administrators to be used for production work. Instead, <strong>Conditional Access</strong> is used to grant permissions to users and groups.
![]() https://learn.microsoft.com/en-us/cli/azure/manage-azure-subscriptions-azure-cli
https://learn.microsoft.com/en-us/cli/azure/manage-azure-subscriptions-azure-cli
Technical Occupation Groups
Microsoft has defined their Azure certification exams based on these generic occupations:
- (Azure) Administrator (of IAM, etc.)
- (Azure) Developer
-
(Azure) Solution Architect
- Data Engineer
-
AI Engineer
- Business Analyst
- Business User (Dynamics, Salesforce, etc.)
PROTIP: This grouping is different from the Administrator role permissions in Entra (formerly Azure Active Directory).
MY OPINION: I think job roles should be multi-select checkboxes. This segregation also adds to duplicating material for each.
QUESTION: How can these occupational roles be added among properties for individual users?
Top-down strategy
To enable IT people to do their job safely, securely, and efficiently, below is what their management should do.
VIDEO: Azure Top Security Best Practices identifies these lifecycle stages:
- Sponsorship and Delegation
- Governance
- Readiness and Security Awareness
- Policy Enforcement
- Continuous Monitoring
Efforts by Organizational Level
VIDEO: Microsoft’s overarching Cybersecurity Reference Architecture (MCRA) contains an overwhelming number of diagrams in the PowerPoint file covered by videos in Microsoft’s CISO Workshop.
Each Cloud Service Provider (GCP, AWS, Azure, etc.) presents different, but similar, Cloud Adoption Framework (CAF) and Well-Architected Framework.
Tenants
The Azure SaaS service separates different customers into different tenants (like tenants in an apartment building). Each tenant is a dedicated, isolated instance of the AAD/Entra service, owned and managed by an organization.
“Isolated” = ISE
Entra ID supports auth protocols: OAuth, OpenID, SAML, WS-Federation.
-
For birthdate, make up an adult year: 2023 - 22 = 2001
PROTIP: Write it down for account recovery, such as in a 1Password entry. Also write down the date you created the account in a calendar entry when you’ll switch accounts.
-
You’ll need a phone number for multi-factor Authentication.
PROTIP: Microsoft does not accept VOIP number such as those from Googgle Voice. They require a cell number from a cell carrier (Verizon, ATT, etc.).
Global Administrators
Global Administrators are aka “Company Administrators” in Entra ID because they have access to almody all services that impact AAD/Entra identities (Microsoft 365 security center, Intune, Microsoft 365 compliance center, Exchange Online, SharePoint Online, Skype for Business Online, etc.).
VIDEO To prevent being locked out of accounts, have no MFA on Global Admin accounts.
-
Set another account for regular work so the Global Admin account is not used regularly.
-
Set at least two other Global Admin users.
-
Set an activity alert to replace them each when their account is made inactive or deleted (when they leave).
-
Set an activity alert to the SOC and other Global Admins when a Global Admin account is used.
-
Login to the Global Admin account
PROTIP: Global Admin privileges are needed to enable AD PIM (Privileged Identity Management) for a directory.
Set User Access Admin permissions
REMEMBER: Global Admins get access to Azure resources only after being granted User Access Admin role.
To work with Management Groups, in Azure RBAC the Global Administrator assigns him/herself the role “User Access Administrator” which has access to the root scope (/) with access to all Management Groups, Subscriptions, Resource Groups in the Tenant:
az role assignment list --role "User Access Administrator" --scope "/" az rest --method post --url "/providers/Microsoft.Authorization/elevateAccess?api-version=2016-07-01" az account management-group entities list az account management-group list
Alternately, in the Console GUI:
-
Get to the Entra ID service (formerly Azure Active Directory), Properties:
https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Properties - Click the slider “can manage access to all Azure subscriptions and management groups in this tenant” to “Yes”.
- Save.
- Log out and in again.
-
Get to your Subscription:
https://portal.azure.com/#view/Microsoft_Azure_Billing/SubscriptionsBlade - Click “Access Control (IAM)”, “View my access” to see “User Access Administrator” listed among Role Assignments.
-
Get to “Management groups”
https://portal.azure.com/#view/Microsoft_Azure_ManagementGroups/ManagementGroupBrowseBlade/~/MGBrowse_overview - Click “Start using management groups”.
- In Overview: your entities:
-
PHASE 02. Admins
Security Jobs To Be Done
How the concerns of each organizational role type/team relate with others, from Plan (Governance) to Build to Run (Operations) stages:
PROTIP: Who covers each of these concerns where you work? Not having an individual/department designated for each responsibility below is often the reason why it doesn’t get done and thus creates vulnerabilities not addressed.
- Board (of corporate directors)
- Management (Business Model, Vision, Strategies, Objectives, Policies, Budget: Staffing, Tools, Training)
Security Leadership:
- PMO (Program Management Office)
- Leadership and Culture
- Risk Management
- Policy & Standards
Compliance Management:
- Privacy & Compliance Requirements
- Compliance Reporting
- Technical Policy Monitoring
Security Architecture:
- Requirements Translation
- Architecture & Risk Assessments
- Technical Policy Authoring
Security Posture Management: Monitor & Remediate Risk
- User Education & Awareness, Insider Risk
- Dev Education & Awareness, App Security, Data Security
- Identity & Key Management: Admin. Security, Identity System Security
- IT Operations: Infra & Endpoint: Deploy tools, Mitigate Vulnerabilities
- OT (IoT) Operations
Security Operations Center (SOC):
- Incident Preparation: Risk Scenarios, Practice Exercises
- Incident Management: Incident Response, Threat Hunting
Other Departments:
- Threat Intelligence
PROTIP: Define abbreviations for each above.
Naming Abbreviations
REMEMBER: Resource names are limited to 64 characters.
PROTIP: Abbreviations are needed to keep names short. Abbreviations can serve as a way to inform policies, such as locking of production servers. Define abbreviations in different human languages if you have an international crew.
Based on Microsoft’s advice on naming conventions:
Use in this order:
-
fin, mktg, prd, it, sec, corp = Business division: organizational element that owns the subscription or workload the resource belongs to.
-
shared, central, client = Subscription type - the purpose of the subscription that contains the resource.
-
rg, vm, etc. = Resource type for each Microsoft service.
-
navigator, emissions, sharepoint, hadoop = Workload (Application or service name that the resource is a part of.
-
prd (production), dev, tst, qa1, stg (staging) = Environment for each phase in the lifecycle of the workload toward productive use. [Differences]
-
westus, eastus2, westeu = Region - The Azure region where the resource is deployed. Pick a region
-
001, 002, etc. Instance - A number or other identifier that distinguishes the resource from other resources of the same type in the same resource group and region.
- Additional fields are geographies: city, country, state, etc.
These are used within <Bicep, and other IoC. For example:
var vnetName= 'vnet-${env}-${region}-${instance}'
var subnetName = 'subnet-${env}-${region}-${instance}'
PROTIP: Stable names make for less rework and mistakes with Dynamic group membership rules used to automatically assign permissions to resources. Example:
(user.department -eq "it") and (user.city -eq "Manhattan") and (resource.type -eq "Microsoft.Compute/virtualMachines")
Bicep and ARM template module for keeping a consistent Azure resource naming convention:
- https://4bes.nl/2021/10/10/get-a-consistent-azure-naming-convention-with-bicep-modules/ using
https://github.com/Ba4bes/Bicep-NamingConvention - https://github.com/nianton/azure-naming
- https://piusdannyongesa.medium.com/implementing-a-consistent-naming-convention-with-azure-bicep-2d7c8611b523
Mindsets and Assumptions (Awareness)
PROTIP: Many don’t take security “seriously” because they haven’t fully grasped these realities: “Laws of Cybersecurity Risk” and Security:
-
Security success is ruining the attacker ROI - Security can’t achieve an absolutely secure state so deter them by disrupting and degrading their Return on Investment (ROI). Increase the attacker’s cost and decrease the attacker’s return for your most important assets.
- Not keeping up is falling behind – Security is a continuous journey, you must keep moving forward because it will continually get cheaper and cheaper for attackers to successfully take control of your assets. You must continually update your security patches, security strategies, threat awareness, inventory, security tooling, security hygiene, security monitoring, permission models, platform coverage, and anything else that changes over time.
- An out-of-date antimalware scanner is only marginally better than no scanner at all.
- An out-of-date antimalware scanner is only marginally better than no scanner at all.
-
Productivity always wins – If security isn’t easy for users, they’ll work around it to get their job done. Always make sure solutions are secure and usable.
-
Attackers don’t care - Attackers will use any available method to get into your environment and increase access to your assets, including compromising a networked printer, a fish tank thermometer, a cloud service, a PC, a Server, a Mac, a mobile device, influence or trick a user, exploit a configuration mistake or insecure operational process, or just ask for passwords in a phishing email. Your job is to understand and take away the easiest and cheapest options as well as the most useful ones (for example, anything that leads to administrative privileges across many systems).
-
Ruthless Prioritization is a survival skill – Nobody has enough time and resources to eliminate all risks to all resources. Always start with what is most important to your organization, most interesting to attackers, and continuously update this prioritization.
-
Cybersecurity is a team sport – Nobody can do it all, so always focus on the things that only you (or your organization) can do to protect your organization’s mission. For things that others can do better or cheaper, have them do it (security vendors, cloud providers, community).
- Your network isn’t as trustworthy as you think it is - A security strategy that relies on passwords and trusting any intranet device is only marginally better than no security strategy at all. Attackers easily evade these defenses so the trust level of each device, user, and application must be proven and validated continuously starting with a level of Zero Trust.
- If a bad actor has unrestricted physical access to your computer, it’s not your computer anymore.
- If a bad actor can persuade you to run their program on your computer, it’s not solely your computer anymore.
- If a bad actor can alter the operating system on your computer, it’s not your computer anymore.
- If you allow a bad actor to run active content in your website, it’s not your website anymore.
- Isolated networks aren’t automatically secure - While air-gapped networks can offer strong security when maintained correctly, successful examples are extremely rare because each node must be completely isolated from outside risk. If security is critical enough to place resources on an isolated network, you should invest in mitigations to address potential connectivity via methods such as USB media (for example, required for patches), bridges to intranet network, and external devices (for example, vendor laptops on a production line), and insider threats that could circumvent all technical controls.
- Absolute anonymity isn’t practically achievable, online or offline.
- Absolute anonymity isn’t practically achievable, online or offline.
- Encryption alone isn’t a data protection solution - Encryption protects against out of band attacks (on network packets, files, storage, etc.), but data is only as secure as the decryption key (key strength + protections from theft/copying) and other authorized means of access.
- Encrypted data is only as secure as its decryption key.
- Weak passwords trump strong security.
- Technology doesn’t solve people and process problems - While machine learning, artificial intelligence, and other technologies offer amazing leaps forward in security (when applied correctly), cybersecurity is a human challenge and will never be solved by technology alone.
- Technology isn’t a panacea.
- A computer is only as secure as the administrator is trustworthy.
What Does Security Want?
NOTE: Many land on this as part of their organization’s effort to transition to make use of the public cloud.
Major Objectives (What, Why, Who, How activities):
- People: Educate teams about the cloud security journey
-
People: Educate teams on cloud security technology
- Process: Assign accountability for cloud security decisions
- Process: Update incident response processes for cloud
-
Process: Establish security posture management
- Technology: Require passwordless or multifactor authentication
- Technology: Integrate native firewall and network security
-
Technology: Integrate native threat detection
- Architecture: Standardize on a single directory and identity
- Architecture: Use identity-based access control instead of keys
- Architecture: Establish a single unified security strategy
There is also “Zero Trust” (aka.ms/zerotrust, aka.ms/ztbizplan, aka.ms/ztguide)
- Verify identity, location, context explicitly (detect anomalies)
- Use least-privilege (JIT, Just Enough) access with adaptive policies
- Assume breach (segment access, encrypt, alert variation posture)
Out-sourcing
Not a lot of people talk about this, but a Cloud Management Platform (CMP) from a CSB (Cloud Service Broker such as AppDirect, Ensim, Gravitant, Jamcracker, Parallels, Ostrato, ServiceNow, BMC, etc.) is used by enterprises to provide provisioning governance, self-service, usage chargeback, and policy enforcement across multiple cloud vendors.
Security Baselines
A security baseline is a snapshot in time of a system’s current configuration (defining specific OS-level settings, installed apps, app configurations, users, etc.). Baselines are created as the basis for determining what settings were changed (and when).
Azure Security Benchmarks (ASB)
DEFINITION: A benchmark is an individual check (evaluation) of a system’s setting, such as the patch level of an application installed, to determine whether best practices (security controls) are employed (which in turn should reduce the attack surface of the system).
Several organizations have defined for the industry specific “controls” (improvement actions):
- CIS (Center for Internet Security) Controls v8 Benchmarks
- NIST SP 800-53 RC4
- PCI-DSS v3.2.1
With the aim of improving the security of cloud-centric workloads, data, and services on Azure, perhaps in multi-cloud environments, in 2021 Microsoft published its prescriptive best-practice framework in its MCSB (Microsoft Cybersecurity Security Benchmarks). Version 3 as of March 30, 2023 is here as the azure-security-benchmark-v3.0.xlsx Microsoft’s Excel spreadsheet file for download. It presents 85 Security Principles for each security control under 12 Control Domains corresponding to specific to each CIS, NIST, and PCI-DSS specification.
- Network security (NS)
- NS-1: Establish network segmentation boundaries
- NS-2: Secure cloud native services with network controls
- NS-3: Deploy firewall at the edge of enterprise network
- NS-4: Deploy intrusion detection/intrusion prevention systems (IDS/IPS)
- NS-5: Deploy DDOS protection
- NS-6: Deploy web application firewall
- NS-7: Simplify network security configuration
- NS-8: Detect and disable insecure services and protocols
- NS-9: Connect on-premises or cloud network privately
- NS-10: Ensure Domain Name System (DNS) security
- Identity Management (IM)
- IM-1: Use centralized identity and authentication system
- IM-2: Protect identity and authentication systems
- IM-3: Manage application identities securely and automatically
- IM-4: Authenticate server and services
- IM-5: Use single sign-on (SSO) for application access
- IM-6: Use strong authentication controls
- IM-7: Restrict resource access based on conditions
- IM-8: Restrict the exposure of credentials and secrets
- IM-9: Secure user access to existing applications
- Privileged Access (PA)
- PA-1: Separate and limit highly privileged/administrative users
- PA-2: Avoid standing access for user accounts and permissions
- PA-3: Manage lifecycle of identities and entitlements
- PA-4: Review and reconcile user access regularly
- PA-5: Set up emergency access
- PA-6: Use privileged access workstations
- PA-7: Follow just enough administration (least privilege) principle
- PA-8 Determine access process for cloud provider support
- Data Protection (DP)
- DP-1: Discover, classify, and label sensitive data
- DP-2: Monitor anomalies and threats targeting sensitive data
- DP-3: Encrypt sensitive data in transit
- DP-4: Enable data at rest encryption by default
- DP-5: Use customer-managed key option in data at rest encryption when required
- DP-6: Use a secure key management process
- DP-7: Use a secure certificate management process
- DP-8: Ensure security of key and certificate repository
- Asset Management (AM)
- AM-1: Track asset inventory and their risks
- AM-2: Use only approved services
- AM-3: Ensure security of asset lifecycle management
- AM-4: Limit access to asset management
- AM-5: Use only approved applications in virtual machine
- Logging and Threat Detection (LT)
- LT-1: Enable threat detection capabilities
- LT-2: Enable threat detection for identity and access management
- LT-3: Enable logging for security investigation
- LT-4: Enable network logging for security investigation
- LT-5: Centralize security log management and analysis
- LT-6: Configure log storage retention
- LT-7: Use approved time synchronization sources
- Incident Response (IR)
- IR-1: Preparation - update incident response plan and handling process
- IR-2: Preparation - setup incident notification
- IR-3: Detection and analysis - create incidents based on high-quality alerts
- IR-4: Detection and analysis - investigate an incident
- IR-5: Detection and analysis - prioritize incidents
- IR-6: Containment, eradication and recovery - automate the incident handling
- IR-7: Post-incident activity - conduct lessons learned and retain evidence
- Posture and Vulnerability Management (PV)
- PV-1: Define and establish secure configurations
- PV-2: Audit and enforce secure configurations
- PV-3: Define and establish secure configurations for compute resources
- PV-4: Audit and enforce secure configurations for compute resources
- PV-5: Perform vulnerability assessments
- PV-6: Rapidly and automatically remediate vulnerabilities
- PV-7: Conduct regular red team operations
- Endpoint Security (ES)
- ES-1: Use Endpoint Detection and Response (EDR)
- ES-2: Use modern anti-malware software
- ES-3: Ensure anti-malware software and signatures are updated
- Backup and Recovery (BR)
- BR-1: Ensure regular automated backups
- BR-2: Protect backup and recovery data
- BR-3: Monitor backups
- BR-4: Regularly test backup
- DevOps Security (DS)
- DS-1: Conduct threat modeling
- DS-2: Ensure software supply chain security
- DS-3: Secure DevOps infrastructure
- DS-4: Integrate static application security testing into DevOps pipeline
- DS-5: Integrate dynamic application security testing into DevOps pipeline
- DS-6: Enforce security of workload throughout DevOps lifecycle
- DS-7: Enable logging and monitoring in DevOps
- Governance and Strategy (GS)
- GS-01: Align organization roles, responsibilities and accountabilities
- GS-02: Define and implement enterprise segmentation/separation of duties strategy
- GS-03: Define and implement data protection strategy
- GS-04: Define and implement network security strategy
- GS-05: Define and implement security posture management strategy
- GS-06: Define and implement identity and privileged access strategy
- GS-07: Define and implement logging, threat detection and incident response strategy
- GS-08: Define and implement backup and recovery strategy
- GS-09: Define and implement endpoint security strategy
- GS-10: Define and implement DevOps security strategy
- GS-11: Define and implement multi-cloud security strategy
The “Kill Chain”
Here are the internal risks and external threats (exploits) we need to be vigilent aginst:
MS Defender offerings
![]() Microsoft has a “Defender” offering for each type of product:
Microsoft has a “Defender” offering for each type of product:
- MS Defender for Identity
- MS Defender for Office 365
- MS Defender for IoT (& OT) Internet of Things (and Operational Technologies)
- MS Defender for Endpoint
- MS Defender for DevOps
- MS Defender for Cloud Product [Intro video Security Solutions, Work Automation triggers]. Pricing (to each server, container, database, storage, app service).
References:
- Azure Security Center: https://github.com/Azure/Azure-Security-Center reroutes to
- GitHub community: https://github.com/Azure/Microsoft-Defender-for-Cloud
- Azure Defender: https://aka.ms/AzureDefenderForSQL
- Become an Azure Security Center Ninja: https://aka.ms/ascninja
- ASC in the Filed Show: https://aka.ms/ascinthefield
- ASC Labs: https://aka.ms/asclabs
- https://learn.microsoft.com/en-us/security/zero-trust/ten-laws-of-security#10-laws-of-cybersecurity-risk
“Sentinel” is Microsoft’s brand name for offerings in SIEM and SOAR.
az security CLI commands az security …
- adaptive-application-controls
- adaptive_network_hardenings
- alert
- alert-suppressions-rule
- allowed-connections
- assessment
- atp (Advanced Threat Protection)
- auto-provisioning-setting
- automation
- contact
- discovered-security-solution
- external-security-solution
- iot-alerts
- iot-analytics
- iot-solution
- jit-policy
- location
- pricing
- regulatory-compliance
- secure-score-control-definitions
- secure-score-controls, secure-scores
- security-solutions
- setting
- sub-assessment
- task
- topology
- va (Vulnerability Assessment)
- workspace-setting
Regulatory Compliance
Progress toward implementing security controls can be illustrated using this:
QUESTION: Interface to organize/track work in Jira or Azure DevOps Tasks?
Notice the regulatory compliance standards:
- ISO 27001
- PCI DSS (Payment Card Industry Data Security Standard) v3.2.1
- SOC TSP
- HIPAA HITRUST
- NIST SP 800 S3 R4
- SWIFT CSP CSCF v2020
- Azure CIS 1.10
- ISO 27001-2013
- CMMC Level 3
- AWS Foundational Security Best Practices
Secure Score Posture Action Categories
References:
Within M365 Defender is the Microsoft Secure Score survey app. It’s used to define a security posture score (over time) based on whether specific actions have occurred or not.
A breakdown of actions based on Microsoft’s categories for a Security Posture:
- Identity
- Data
- Device
- Apps
- Infrastructure
We need to begin with Infrastructure.
In Dev vs Prod
In Prod, Key Vault secrets are locked from deletion for 90 days.
In Dev, Key Vault values can be deleted at the discretion of developers.
In Dev, devs can access the Azure Portal interactively to create resources during CI/CD IaC pipeline construction.
In Prod, resources are deployed only by CI/CD pipelines and devs cannot access the Azure Portal interactively.
Devs are limited by policies to a limit of two regions to avoid runaway costs.
Prod configurations usually cover several regions for redundancy and performance to end-customers.
Azure Government environments
Microsoft runs separate/isolated Azure fed/state/local gov “sovereign DoD Level 5” cloud hardware on US soil operated by US citizens.
-
Specify the target cloud environment:
az cloud show --name AzureUSGovernment
AzureUSGovernment has its own Marketplace of apps.
-
Know that each service has different host names for US government work. For example, Speech Studio Speech translation has these API endpoints:
- Virginia: https://usgovvirginia.s2s.speech.azure.us
- Arizona: https://usgovarizona.s2s.speech.azure.us
References:
- What is gov?
- DOC: Compare Global vs. Gov
- VIDEO: Terraform Provider Azure.gov for standardized templates across clouds.
- Pulumi enables programmatic access (by a Python program) to Azure.
YouTube playlist on Azure (https://aka.ms/AzureGovVideos) by Steve Michelotti</a talking with experts from dev, from 2019+. Each is thorough. Much of their advice applies to commercial Azure as well. I list them after reversing the order of the playlist:
- Azure Friday - Azure Government
- Azure Government Security
- Real World Solutions on Azure Government with Machine Learning
- Mobile Apps Powered by Azure Government
- How to run containers with Kubernetes on Azure Government
- How to use Azure Monitor for Azure Government
- How to use GPUs by NVIDIA on Azure Government for Virtual Machines and AI
- Cloud Solution Provider Program for Azure Government
- What is Azure Government?
- How to get started with Azure Government Data Analytics
- How to get started with Azure Government Data Protection
- How to get started with Azure Government Iaas and PaaS
- How to access & get started with the Azure Government Portal
- How to publish your solutions to Azure Government Marketplace
- How to enable Central IT to become a Cloud broker
- How to use Machine Learning on Azure Government with HDInsight
- How to use containers for data science on Azure Government
- Learn about OpenShift on Azure Government
- Overview of Cosmos DB on Azure Government
- Overview of Service Health on Azure Government
- How to set up a secure environment on Azure Government- Part 1
- How to set up a secure environment on Azure Government - Part 2
- How to deploy the Azure Resource Manager template
- How to run the Azure Government PaaS sample
- How to run the Azure Government Functions sample
- Real-time data streaming with Event Hubs on Azure Government
- Build automated workflows with Logic Apps on Azure Government
- Learn about Serverless technology in Azure Government
- Overview of Managed Identities on Azure Government No secrets rotation.
- t=9m59s setup using CLI for kv.GetSecretAsync from within VM code to retrieve from Key Vault
- t=13m23s setup using portal add Web App. Enable Managed Identity. Publish. In Key Vaults, add Access Policy to Web App.
- Overview of Azure Database for MySQL in Azure Government
- DoD Impact Level 5 Expansion on Azure Government
- Advanced Data Security with Azure SQL Database in Azure Government
- Microsoft Azure Government Secret
- Data Science Virtual Machine on Azure Government
- Migrate and Modernize with Kubernetes on Azure Government
- Bot Service and LUIS on Azure Government
- Azure blueprints and compliance on Azure Government
- Azure DevOps Server in Azure Government
- Cloud Shell in Azure Government
- Azure Stream Analytics in Azure Government
- Azure Maps in Azure Government
- QnA Maker in Azure Government
- What’s new in Azure Government
URLs for Microsoft and Azure
URL Shortener
https://channel9.msdn.com/Shows/Azure-Friday/AzUrlShortener-An-open-source-budget-friendly-URL-shortener by Frank Boucher who created a one-click deploy your own. http://www.frankysnotes.com/2020/04/how-i-build-budget-friendly-url.html
https://medium.com/marcus-tee-anytime/create-your-own-url-shortener-host-in-azure-almost-free-for-cloud-infrastructure-a74c9cc29720
https://levelup.gitconnected.com/build-a-custom-url-shortener-using-azure-functions-and-cosmos-db-c20e59261375
Subscriptions
At the Subscription pane
A Subscription is a billing boundary linked to an Azure account AND A container for resource groups.
There can be multiple Subscriptions per tenant (e.g. for depts.).
- Non-prod (for devs)
- Production (for operations)
- Multi-region
Multiple subscriptions can be created under a single Azure account (Dev, Test, Staging, Production, Logging, Demo, Training, DR, etc.). This is particularly useful for businesses because:
DEFINITION: A Subscription is your “bank account” / credit card.
PROTIP: access control and billing occur at the subscription level, not the account level.
PROTIP: Each Subscription can only trust a single AAD/Entra directory.
Transfer ownership of a subscription, such as to a central accounting department.
Add additional subscriptions when you may exceed limits within a subscription: # VNets.
REMEMBER: The 2000 role assignments limit per subscription is fixed and cannot be increased.
Subscription types:
- Azure pass (e.g. with a course)
- MSDN (Developer Network)
- Azure trial
- Pay-as-you-go (most common)
- Enterprise (involves a minimum commitment)
Phase 05. Populate Groups Roles Users
- https://www.alitajran.com/create-azure-ad-users/ to add user info using PowerShell to Microsoft Graph.
- LEARN Create Azure users and groups in Microsoft Entra ID VIDEO
- Training for Bulk Create Users in Entra from CSV file.
- https://o365info.com/bulk-create-azure-ad-users/ proposes a PowerShell script to create users from a CSV file.
- https://www.youtube.com/watch?v=9wdjGqe_MdI
-
Define verified domain names in your Azure organization.
-
As a User Administrator, sign in to the account you want to use at
https://portal.azure.com/#home
-
Microsoft Entra admin center at:
https://entra.microsoft.com/#home
-
Select Microsoft Entra ID.
https://entra.microsoft.com/#view/Microsoft_AAD_IAM/TenantOverview.ReactView
-
In the left menu, select All users > Users > Bulk Operations > Bulk create for “Bulk create users” at the right.
-
Click the blue “Download” to download the “UserCreateTemplate.csv” file to your local computer’s Downloads folder.
-
Open the file using a text editor to see three lines in the file:
version:v1.0 Name [displayName] Required,User name [userPrincipalName] Required,Initial password [passwordProfile] Required,Block sign in (Yes/No) [accountEnabled] Required,First name [givenName],Last name [surname],Job title [jobTitle],Department [department],Usage location [usageLocation],Street address [streetAddress],State or province [state],Country or region [country],Office [physicalDeliveryOfficeName],City [city],ZIP or postal code [postalCode],Office phone [telephoneNumber],Mobile phone [mobile] Example: Chris Green, chris@contoso.com, myPassword1234, No
CAUTION: Leave the first two rows as is. Do not change the column headings.
Replace the 3rd row that starts with “Example” with actual data.
-
Double-click on the file, which will open the file in Excel, showing the column headings and a sample row.
A. Name [displayName] Required
B. User name [userPrincipalName] Required email address with valid host name (such as contoso.com)
C. Initial password [passwordProfile] Required
D. Block sign in (Yes/No) [accountEnabled] Required
E. First name [givenName]
F. Last name [surname]G. Job title [jobTitle]
H. Department [department]I. Usage location [usageLocation]
J. Street address [streetAddress]
K. State or province [state]
L. Country or region [country]
M. Office [physicalDeliveryOfficeName]
N. City [city]
O. ZIP or postal code [postalCode]P. Office phone [telephoneNumber]
Q. Mobile phone [mobile]CAUTION: Additional columns cannot be added.
-
Download my sample .csv file populated with specific user names who are later assigned groups and permissions:
“Azure-1000-Users.csv” from ???
-
In the “Bulk create users” page, click field contents “Select a file”.
-
Click the blue “Submit” button for validation of the CSV file starts. It starts with “In progress”.
-
When your file passes validation, select Submit to start the Azure bulk operation that imports the new users.
-
See the “Users Bulk operation result” page at: https://entra.microsoft.com/#view/Microsoft_AAD_UsersAndTenants/UserManagementMenuBlade/~/UserBackgroundTasks/menuId/
- If failed, click “Download tasks”
-
View in Downloads a file named “user create_11_24_2023-“ appended in front of your file name.
Status [status] Failed reason [failedReason] Account enabled [accountEnabled] Usage location [usageLocation] mailNickname passwordProfile passwordPolicies rolesEntity selectedRoleIds selectedGroupIds Street address [streetAddress] City [city] State or province [state] Country or region [country] Office phone [telephoneNumber] Mobile phone [mobile] Office [physicalDeliveryOfficeName] ZIP or postal code [postalCode] authenticationPhoneNumber authenticationAlternativePhoneNumber authenticationEmail strongAuthenticationDetail defaultImageUrl ageGroup consentProvidedForMinor legalAgeGroupClassification Object Id [objectId] objectType Name (example: Chris Green) [displayName] * User name (example: chris@contoso.com) [userPrincipalName] * thumbnailMediaContentType First name [givenName] Last name [surname] mail dirSyncEnabled alternativeSecurityIds signInNamesInfo signInNames ownedDevices Job title [jobTitle] Department [department] displayUserPrincipalName hasThumbnail imageUrl imageDataToUpload source sources sourceText userFlags deletionTimestamp permanentDeletionTime alternateEmailAddress manager userType isThumbnailUpdated isAuthenticationContactInfoUpdated searchableDeviceKey displayEmail creationType userState otherMails invitedAsMail proxyAddresses companyName employeeId
Fix errors before submitting again.
These appeared in the error response:
R. mailNickname
S. passwordProfile
T. passwordPolicies
U. rolesEntity
V. selectedRoleIds
W. selectedGroupIdsX. authenticationPhoneNumber
Y. authenticationAlternativePhoneNumber
Z. authenticationEmail
AA. strongAuthenticationDetaildefaultImageUrl
ageGroup
consentProvidedForMinor
legalAgeGroupClassification
Object Id [objectId]
objectTypeimageUrl
imageDataToUpload
source
sources
sourceText
userFlags
deletionTimestamp
permanentDeletionTime
alternateEmailAddress
manager
userType
isThumbnailUpdated
isAuthenticationContactInfoUpdated
searchableDeviceKey
displayEmail
creationType
userState
otherMails
invitedAsMail
proxyAddresses
companyName
employeeId -
When the import operation completes with “File uploaded successfully”, Status column should contain “Completed with no errors”.
-
Verify users in Entra ID > Users, Select All users (preview)
-
See https://www.alitajran.com/create-azure-ad-users/ to add user info using Microsoft Graph.
-
Notify users of their new accounts using PowerShell script
“You will need to change your password on first login.”
Phase 15. Devices - MS Authenticator app
- User-owned BYOD (Bring Your Own Device) or Org-owned Windows or mobile devices are “Registered” to Azure AD (not joined) to access cloud resources (not on-prem).
- Organisations with on-premises AD join org-owned Windows 10 (not Home) devices using Azure AD Connect. If worker is remote, set Group Policy or other AD requirements.
- “Hybrid Join” Windows 10 and down-level (8.1, 7)
-
Install the Microsoft Authenticator app on you smartphone and setup Two-factor authentication to approve access using your phone.
-
Get a unique profile image and add picture.
-
Setup password on your device.
-
https://azure.microsoft.com/en-us/features/azure-portal/mobile-app/
-
Open the store on your phone and search for “Microsoft Azure”:
On the Apple App Store: https://apps.apple.com/us/app/microsoft-azure/id1219013620?ls=1
On the Google Play Store: https://play.google.com/store/apps/details?id=com.microsoft.azure
-
Login. VIDEO
-
Setup MFA
Microsoft has its “Intune” offering to manage mobile and laptop devices and their endpoint. BTW: Intune is a separate MDM (Mobile Device Management) product from Entra ID.
Phase 01. Pick Region(s)
-
PROTIP: You’ll be soon asked to specify a region. Pick the region closest to you.
By combining several sources, I compiled this private Google Sheet of 53 regions:
- _Theater : a custom grouping (APJ, AMER, EMEA)
- _Geography : Africa, Asia Pacific, Canada, China, Europe, Middle East, South America, US
- _RegionName : the name of the region (e.g. “East US”)
- _Sovereignty : the country where the region is located (e.g. “United States”)
- _PhysicalLocation : the city where the region is located (e.g. “Chicago”)
- _Latitude : where 0 is the equator (e.g. “41.881832”)
- _Longitude : where 0 is the Prime Meridian (GMT) near London
- _AvailZones : if supported, the number of availability zones in the region (e.g. “3”)
- _PairedRegion : the name of the paired region (e.g. “West US”)
- _RestrictionStatus : “Enabled by default” or “Access Restricted”
-
This command lists all 83 Azure regions, which includes some not available for customer use.
az account list-locations | wc -l
{ "displayName": "Brazil Southeast", "id": "/subscriptions/7a0bbbfc-a36d-4d73-bbaf-e381b82397c6/locations/brazilsoutheast", "metadata": { "geography": "Brazil", "geographyGroup": "South America", "latitude": "-22.90278", "longitude": "-43.2075", "pairedRegion": [ { "id": "/subscriptions/7a0bbbfc-a36d-4d73-bbaf-e381b82397c6/locations/brazilsouth", "name": "brazilsouth" } ], "physicalLocation": "Rio", "regionCategory": "Other", "regionType": "Physical" }, "name": "brazilsoutheast", "regionalDisplayName": "(South America) Brazil Southeast", "type": "Region" } -
CAUTION: This command lists only 83 Azure regions with no Latitude and Longitude, data all mixed up:
az account list-locations --output tsv >locations.csv
-
Select a Geograph (country), then a Region from Microsoft’s list at:
https://azure.microsoft.com/en-us/explore/global-infrastructure/geographies/#geographies
At time of writing, Microsoft has over 60 regions around the world on their map:
-
There is also an interactive map showing a point for each region’s Longitude and Latitude with city name.
http://www.azurespeed.com measures current ping speeds between regions on Microsoft’s Azure cloud. To stop collection, click “uncheck all” or individual regions of interest:
-
There are differences in cost between regions. For example, the US East region is cheaper than the US West region.
-
To display Microsoft’s own analysis of ping speeds between its regions (using data from the thousandeyes.com (Cisco) network analytics company, view:
https://docs.microsoft.com/en-us/azure/networking/azure-network-latency
PROTIP: In the above, the slowest is 400 ms round-trip between Cape Town (South Africa West) and Australia East.
NOTE: One big advantage of Azure over AWS is that AWS requires users to do their own backups and restores. But Microsoft does its own complete backups of all data in each zone, and when there is an outage, they take care of restoring it to a new zone. Where backups go is not public information, but it is likely that they are in a different zone in the same region, or in a different region.
-
These cross-region pairs are used for replication in Azure business continuity and disaster recovery. For example:
Geography Region pair A Region Pair B North America East US West US North America East US 2 Central US North America North Central US South Central US North America West US 2 West Central US North America West US 3 East US Europe North Europe (Ireland) West Europe (Netherlands) NOTE: The Microsoft Frontdoor service enables you to use a single global IP address for your application. Microsoft automatically routes traffic to the region closest to the user. This is similar to AWS CloudFront.
### Support Plans (with Pricing)
VIDEO “Microsoft Azure Pricing and Support Options”
Submit a support ticket at: https://portal.azure.com/#create/Microsoft.Support (email support@microsoftsupport.com)
-
Basic: Billing and Subscription support only. “Self-help” technical support.
-
Developer $29/mo. for 8-hour response to non-Prod. env. issues.
-
Standard $100/mo. for 4-hour response to Sev B issues for “Business Critical” when you file a business-critical issue with technical support, the earliest you can expect a response from technical support? Within 1 hour
-
Professional Direct $1000/mo. which adds a ProDirect Delivery Manager who provides architectural guidance, onboarding services, seminars.
-
Premier for “substantial dependence” with a TAM (Technical Account Manager).
Getting 403 ActiveDirectoryMenuBlade accessing AAD/Entra on Portal
-
Right-click on the “Help + Support” box on the Dashboard and select “unpin” because you now know you can reach it (in two places).
Social Support Forums about Azure
https://medium.com/microsoftazure
Filtered for Most Votes on Accepted answers:
-
Tuesdays with Corey (Sanders, VP of Azure Compute, now Corporate VP of Microsoft Solutions, about Azure on Microsoft’s Channel9 video site). #AzureTwC
Help + Support
-
There are 3 places you can reach “Help + Support”:
Click the question mark icon at the upper-right corner.

Support options are also listed behind the smiley face icon.
There is also a “Help + Support” box on the Dashboard.
Alternately, scroll down to click Help + Support (the person icon in blue).
-
Microsoft calls their business-level oriented collection of implementation guidance VIDEO: MS_LEARN: Microsoft Cloud Adoption Framework for Azure”.
Additional sites:
https://microsoft.github.io/AzureTipsAndTricks/blog/tip1.html
Categories to get support
In order to route your support to a specific team, here is a comprehensive list:
- Azure Active Directory (AAD/Entra)
- Microsoft Azure Stack
- Azure Stack Edge
- Blockchain [discontinued]
- Compute
- Databases
- Developer Tools
- Enterprise Integration [Arc]
- Intelligence & Analytics [AI & Machine Learning]
- Internet of Things
- Microsoft Graph
- Mixed Reality [Hololens, Mesh]
- Monitoring & Management
- Networking
- Security
- Storage
- Web & Mobile [Edge browser]
Lock Box for Support
For Microsoft people to access a customer’s unencrypted data, they are supposed to look into the “Lock Box” where a customer put files they want Microsoft to see.
Learning Hubs
PROTIP: Below I’ve added LinkedIn links to each Learn Room instructor.
- AI for Everyone - Arafat Tehsin (https://arafattehsin.com/blog)
- Analytics with Indira Polavarapu
- Entra ID from A to Z - Eric Woodruff (ex-AWS)
- Azure Centric Learning - Marcos Nogueira
- Azure Cloud Commanders - Luke Murray
- Azure Developer for AI, Data, and Cloud - Beginner to Expert - Usama Wahab Khan in NYC & Dubai
- Azure DevOps and .NET - Rodrigo Kono in Brazil
- Azure Fundamentals and Developer Technologies - blgorman (Brian Gorman)
- Azure Infrastructure by MTTs Learning Room
-
Azure Knowledge Base with Kazeem
- BizApps Pinoy - on Linkedin - “for Filipinos” by Doher Drizzle Pablo
- Certifications’ Training - Estelle
- Cloud Data Platform Learners - Armando Lacerda
- Compliance Learning Room - Raphael Koellner
-
Cybersecurity From Beginner to Expert - Dwayne Natwick
- Design & build with Jeeva and Dharani: D365 CE, Power Platform & DevOps
- GMDynamics365 - Goloknath Mishra
- Internet of Things, Digital Twins, and AI with Jorge Maia
- MB-Dynamics 365 and PL-Power Platform - Julian Sharp
- MCT Community Pakistan - Usman and Gulnaz
-
Microsoft Azure “Zero to Hero” - Hamid Sadeghpour Saleh
- Microsoft Dynamics 365 FO & SCM - Faisal Fareed
- MSIsGreat - Senthamil Selvan V
- M365 Learning Lounge with Nanddeep, Siddharth, and Smita
-
M365 Modern Work
- Power BI – Ashraf Ghonaim, Learning Expert
- Power Platform and Dynamics 365 with Nadeeja (Bomiriya) in Melbourne
- Power Platform Hub - Haniel Croitoru
- Power Platform with Rishona
- Swamy The Learner (Viswanatha Swamy)
- Tiago Costa - Your Azure Expert
Resource Naming conventions
PROTIP: Decide on naming conventions and abbreviations BEFORE you create any resources. Abbreviations are needed to keep names short. This is both to avoid re-dos and to help with less stressful collaboration and communication, especially if you have an international crew with different human languages and cultures.
PROTIP: Some abbreviations can inform policies, such as locking of production servers.
Based on Advice from Microsoft about naming conventions:
-
shared, central, client = Subscription type - the purpose of the subscription that contains the resource.
-
fin, mktg, product, it, corp = Business unit - organizational element that owns the subscription or workload the resource belongs to.
-
westus, eastus2, westeu = Location/Region - The Azure region where the resource is deployed.
-
prod, dev, qa, stage, test = Deployment environment - The stage of the development lifecycle for the workload that the resource supports.
-
rg, vm = Resource asset type.
-
navigator, emissions, sharepoint, hadoop = name of the application, workload, or service that the resource is a part of.
PROTIP: Keep the sequence of the abbreviations consistent, so that you can easily find the resource in the portal.
Phase 06. IaC (Infrastructure as Code)
Automation programmatically
There are many ways to automate the creation of resources within Azure:
- Portal GUI Cloud Shell
- JSON ARM Template with parameter files
-
CLI Bash scripts (az commands)
- Powershell ps1 scripts calling Az modules
- PowerShell DSC (Desired State Configuration) automation
-
Powershell running ARM template JSON files
- Microsoft Bicep (new from 2021)
- Terraform HCL *.tf files with templating features and advanced logic features)
- REST API (used within a VBScript, curl, C# .NET, Java, Python, NodeJs, etc.
- REST API calls in program generated from Swagger/OpenAPI JSON
- (Serverless) Functions
- Docker containers
- Helm charts referencing DockerHub or Azure Container Registry (ACR) images
- From Microsoft (Security) Defender Incident Playbook VIDEO
- Azure Power Automate
- Microsoft Power apps
-
From Visual Studio or Visual Studio Code
- PowerShell scripts running in CLI
My Azure-quickly repo on GitHub
My repo https://github.com/wilsonmar/azure-quickly contains automation scripts to invoke instead of manually operating the Azure Portal, so that you can save money by deleting Resource Groups because you can get resources back with just a few commands.
Automation also enables you to stand up resources in different regions/locations the same way.
Most scripts in the repo are Bash shell scripts that run natively on MacOS and thus familiar to most developers. PowerShell scripts are used in cases where they are the only solution, are more efficient, or covered in a tutorial.
Utility script code enable the scripts to run from Linux and Git Shell on Windows laptops.
The scripts are also useful for learning Azure.
Login to az CLI & PowerShell
- https://learn.microsoft.com/en-us/cli/azure/?view=azure-cli-latest#az_login
- https://learn.microsoft.com/en-us/cli/azure/authenticate-azure-cli-interactively
- https://learn.microsoft.com/en-us/cli/azure/authenticate-azure-cli
- https://learn.microsoft.com/en-us/cli/azure/manage-azure-subscriptions-azure-cli#change-the-active-tenant
- Open a Terminal.
-
The command to login to Azure is:
az login
-
In the browser window that opens, select the email account you want to use. Successful login would result in a list of subscriptions you have access to, such as:
... "name": "Azure Subscription 1", "tenantId": "11111234-aaaa-bbbb-cccc-dddeeefff111", ... "name": "Pay-As-You-Go", "tenantId": "22221234-aaaa-bbbb-cccc-dddeeefff111", ... "name": "Twilio SendGrid", "tenantId": "33331234-aaaa-bbbb-cccc-dddeeefff111", ...
Enterprise admins are likely to have multiple Azure accounts, so highlight and copy the tenant you want:
-
PROTIP: Define in ~/mac-setup.env secrets file the tenents so that you can specify which one to use each time.
The resulting login command would be like:
az login --tenant 11111234-aaaa-bbbb-cccc-dddeeefff111
Alternately, https://learn.microsoft.com/en-us/cli/azure/authenticate-azure-cli-interactively
read -sp "Azure password: " AZ_PASS && echo && az login -u
-p $AZ_PASS</pre> -
Close the browser window or read resources about AZ CLI from a Terminal:
- https://ss64.com/ps/ (A-Z index of PowerShell commands)
- VIDEO: Cloud Shell
REMEMBER: Each Azure account has a 5GB storage held in your file share.
-
Create a folder, substituting your own project name:
mkdir proj1; cd proj1
-
Download
git clone http://github.com/wilsonmar/mac-setup;cd mac-setup;chmod +x az-info.sh
-
Set permissions:
chmod +x az-info.sh
-
To avoid error “Stopping at filesystem boundary (GIT_DISCOVERY_ACROSS_FILESYSTEM not set).”
export GIT_DISCOVERY_ACROSS_FILESYSTEM=1 git remote add origin https://github.com/wilsonmar/mac-setup git fetch git pull origin master
-
Change permissions to enable execution by the specific script:
chmod +x az-info.sh
CAUTION: Avoid granting permissions for all scripts in a folder to limit “blast radius”.
-
Run the script file from GitHub:
bash -c "$(curl -fsSL https://raw.githubusercontent.com/wilsonmar/mac-setup/master/az-info.sh)"
That script is similar to the aws-info.sh script in my aws-quickly repo.
TODO: I’m also working on a PowerShell version of the script.
-
Install modules needed, Per https://wilsonmar.github.io/powershell-install-coding
pwsh; Install-Module azuread
Untrusted repository You are installing the modules from an untrusted repository. If you trust this repository, change its InstallationPolicy value by running the Set-PSRepository cmdlet. Are you sure you want to install the modules from 'PSGallery'? [Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"): Y
PROTIP: Azure CLI commands can be issued from within PowerShell (.ps1) script files. See ListUserAndPermissions.ps1
Here I list both CLI and PowerShell commands to get information:
- List Azure accounts, groups membership, role permissions
- List resources
- List storage accounts
- List compute instances
- List databases
- etc.
Before executing any script,
Set-ExecutionPolicy RemoteSigned
https://wilsonmar.github.io/azure-cloud-powershell/
Azure Power Automate
- Azure Automation
- Power Automate Add Entra ID users and managers
- Automation of Creating Users with Microsoft Power Automate and Graph API by Nick Romanek
- Employee on-boarding process using Microsoft Forms and Flow https://www.youtube.com/watch?v=vYnvQgKSWcg
Although deprecated by the Hybrid Runbook Worker feature, Azure Automation securely reaches inside VMs in private networks and on-premises to execute PowerShell scripts/commands. It makes use of Windows PowerShell Remoting feature.
However, PowerShell Remoting is not always a viable option. Where you have Azure-hosted VMs but cannot open a public WinRM port, This post presents a PowerShell extension runbook for on-premises VMs by utilizing the Azure VM Agent’s Custom Script Extension.
Python
https://learn.microsoft.com/en-us/azure/developer/python/?view=azure-python
- API calls such as Create User from custom programming languages C#, Go, Java, JavaScript, PHP, PowerShell BUT NOT Python
Editors:
- Visual Studio for Mac does not support Python.
- Visual Studio 2022 users: install PTVS (Python Tools for Visual Studio)
-
Visual Studio Code users: https://code.visualstudio.com/docs/languages/python
- https://code.visualstudio.com/docs/python/python-tutorial
- On macOS, make sure the location of your VS Code installation is included in your PATH environment variable. in your .bash_profile:
export PATH="\$PATH:/Applications/Visual Studio Code.app/Contents/Resources/app/bin"
Azure Blueprints
As of September 23, 2023, Azure has stopped development of its “Blueprints” which maintain versions of the relationship between what should be deployed and what was actually deployed. So it supports auditing of deployments over time. And, on its own, a Blueprint can be applied to several subscriptions at once. [VIDEO] Also, Azure Blueprints are stored in Azure Cosmos cloud DB, which is replicated globally to several regions for ultimate reliability.
NEWS: Microsoft announced that it is retiring Azure Blueprints on Sep 30, 2024. Microsoft recommends that customers use Azure Resource Manager (ARM) template specs and deployment stacks to manage their environments.
Notice in sample Blueprints files that it’s in JSON format:
Blueprints orchestrate deployment of resources/artifacts as policy.
In the Artifacts folder, Blueprints has these:
- Role assignments
- Policy assignments
- ARM templates
- Resource groups
Template Specs will be taking over for Blueprints?
- https://learn.microsoft.com/en-us/answers/questions/177308/index.html
Blueprints the only mechanism for assigning deny permissions to Resource Groups.
https://learn.microsoft.com/en-us/answers/questions/177308/index.html
HashiCorp’s Terraform, which completely controls and maintains changes.
- https://github.com/terraform-providers/terraform-provider-azurerm
This sample Blueprint deploys several Azure services to provide a secure, monitored, enterprise-ready foundation:
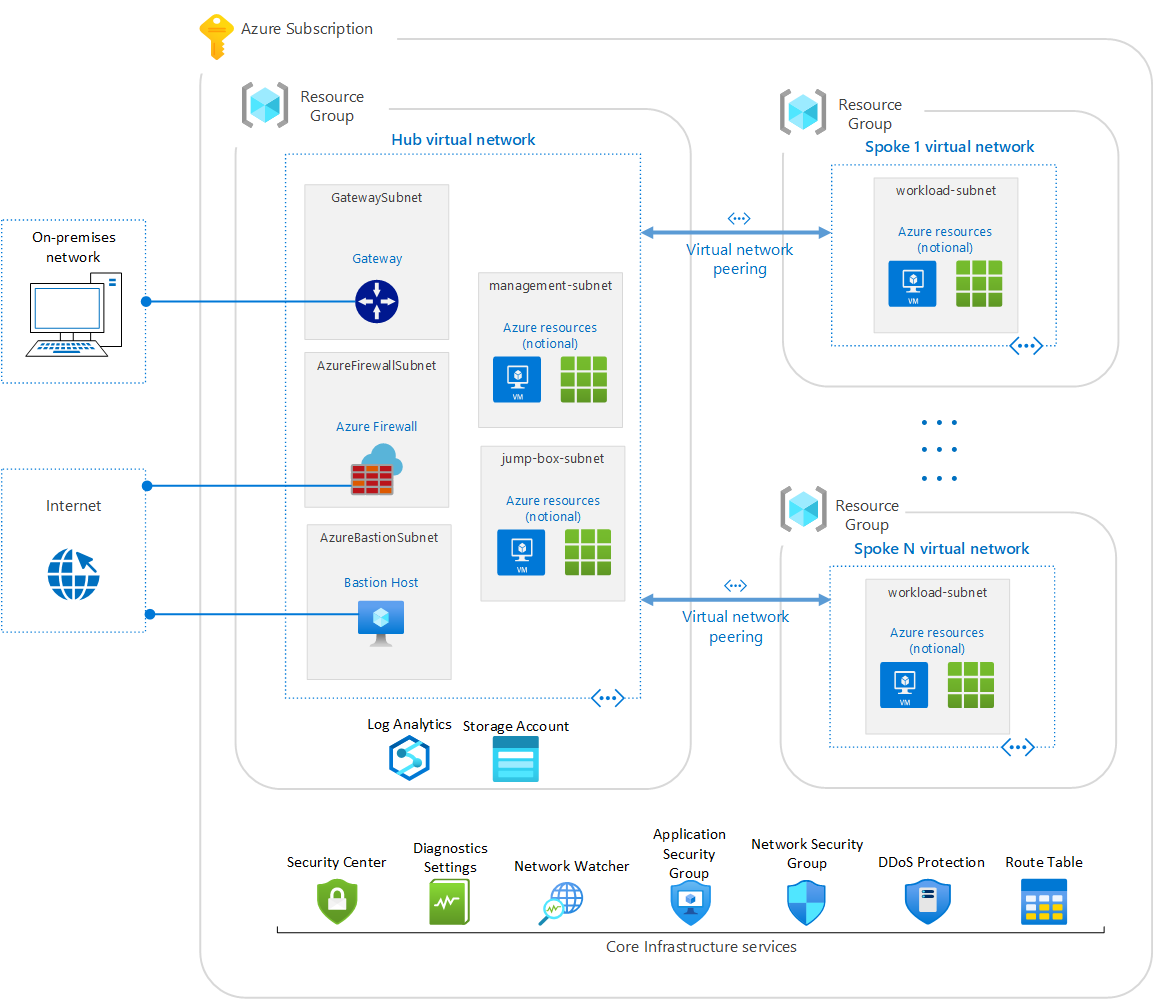
An important design of Azure Blueprints within enterprises is that it allows for separation of duties between technical teams responsible for creating and maintaining the blueprint and those (in Operations) responsible for deploying it. This is similar to the separation of duties between developers and operations in DevOps favored for compliance.
This presents the analysis that Azure Blueprints is a top-down approach to infrastructure management, while Terraform is a bottom-up approach.
IaC Stacks
https://learn.microsoft.com/en-us/cli/azure/stack?view=azure-cli-latest A deployment stack is a native Azure resource type that enables you to perform operations on a resource collection as an atomic unit.
Deployment stacks are defined in ARM as the type Microsoft.Resources/deploymentStacks.
- az stack group create –name StackName
–resource-group ResourceGroup
–delete-all
–template-spec TemplateSpecResourceIDWithVersion
–description description
–deny-settings-mode None -
az stack group list
- az stack sub create –name StackName
–template-file simpleTemplate.json
–location westus2
–description description
–deny-settings-mode None - az stack sub list
https://learn.microsoft.com/en-us/azure/active-directory/governance/create-lifecycle-workflow”> Create a workflow in Microsoft Entra admin center</a>
https://www.youtube.com/watch?v=d1AE8qLwBYw
https://github.com/johnthebrit/RandomStuff/blob/master/DeploymentStacks/demo.ps1
Azure Services
Bicep files are stored in https://github.com/wilsonmar/DevSecOps/tree/main/azure/bicep
.
├── README.md
├── account
│ ├── identities (Manage Azure Managed Identities) - Core
│ ├── login (Manage Azure subscriptions) - Core
├── ai
│ ├── find (Find Azure resources using AI robot) - Core
│ ├── ml (Manage Azure Machine Learning) - Extension
│ └── quantum (Manage Azure Quantum) - Extension
├── compute
│ ├── acr (Azure Container Registry) - Core
│ ├── acs (Azure Container Service) - Extension
│ ├── aks (Azure Kubernetes Service) - Core & Extension
│ ├── containerapp (Manage Azure Container Apps) - Extension
│ ├── container (Manage Azure Container Instances) - Core & Extension
│ ├── staticwebapp (Manage Azure Static Web Apps) - Extension
│ ├── stream-analytics (Manage Azure Stream Analytics) - Core
│ └── vm (Manage Linux or Windows virtual machines) - Core
├── data
│ ├── disk (Manage Azure Managed Disks) - Core
│ ├── disk-access (Manage disk access resources) - Core
│ ├── cosmosdb (Manage Azure Cosmos DB database accounts) - Core & Extension
│ ├── backup (Manage Azure Backup) - Extension
│ ├── mariadb (Manage Azure Database for MariaDB servers) - Core
│ ├── mysql (Manage Azure Database for MySQL servers) - Core
│ ├── postgres (Manage Azure Database for PostgreSQL servers) - Core
│ └── repos (Manage Azure Repos) - Extension
├── deploy
│ ├── advisor (Manage Azure Advisor) - Extension
│ ├── consumption (Manage Azure Consumption) - Core
│ ├── costmanagement (Manage cost an billing in Azure) - Extension
│ ├── bicep (Manage Azure Bicep) - Extension
│ ├── cloud (Manage registered Azure Clouds) - Core
│ ├── extension (Manage and update Azure extensions) - Core
│ ├── graph (Query the resources managed by Azure Resource Manager) - Core
│ ├── resource (Manage Azure resources) - Core
│ ├── role (Manage user roles for access control with Entra ID and service principals) - Core
│ └──
IAM
AuthA & AuthN
This pdf is how Azure’s various enterprise authentication and authorization mechanisms relate to each other:
A. Enterprise enrollment (to Dept, Account to Entra & on-prem. Active Directory)
B. Identity and access management
C. Management group and subscription organization
D. Management subscription (to on-premises systems)
E. Connectivity subscription
F. Landing zone subscription
G. VM templates
H. Sandbox subscription
I. Azure DevOps (vs. GitHub Actions)
Entra ID
AD = Active Directory (on-prem Windows server)
vs.
AAD = Azure AD = Azure Active Directory = Entra
vs.
AADC = Azure AD Connect = Entra Connect
vs.
ADDS = Active Directory DS = Domain Services
| - | on-prem. AD | AAD/Entra |
|---|---|---|
| Runs on: | Windows server | Internet |
| Use by: | Windows | Internet: Office 365, Azure services & apps, 3rd-party SaaS |
| Protocols: | RPC | REST API |
| Structure: | Forests, domains, Org. Unit | Tenents |
| Authentication: | Kerberos, NTLM, LDAP | SAML, OAuth, Open-ID, WS-Federation |
AD = Active Directory
Active Directory stores credentials for (older) run on Windows servers in on-prem data centers. This older on-prem AD provides “domain services” that include domain joins, group policies, LDAP, Kerberos / NTLM authentication. It uses the AD Admin Center GUI.
Entra = AAD = Azure Active Directory
Entra/Azure Active Directory (AAD) registers Users and Groups, plus apps and devices. AAD/Entra is a SaaS service, unlike “Active Directory” running on Windows servers in on-prem data centers. So AAD/Entra is also called an “Identity as a Service” (IDaaS).
-
Since Azure Microsoft Office 365 is SaaS, users are enrolled into AAD/Entra.
-
Because it’s SaSS, it’s also possible to use AAD/Entra for Federation SSO (Single Sign On) to manage third-party software applications (outside Microsoft), such as CRMs like Salesforce, SAP, Concur, etc.
AAD/Entra Connect
Entra Connect is a Windows service that synchronizes on-prem AD user metadata with the SaaS AAD. Key features of AAD Connect:
- Password hash sych with AAD/Entra
- Pass-through authentication which allows users to use the same password on-prem. and in the cloud.
- Federation integration with AD FS for certificate renewal
- Synchronization to ensure on-prem and cloud data matches
- Health monitoring in a central location
AD App Proxy instead of VPN
VIDEO: Traditional VPN enable users to access all ports on the entire network.
Apps configured to use AD App Proxy would limit user access to only the app configured, using what’s called “explicit user and device trust validation”.
Tenant Domains
DEFINITION: A domain is an area of a network organized by a single authentication database.
DEFINITION: An “Active Directory Domain” is a logical grouping of AD objects on a network.
DEFINITION: An Active Directory Domain Controller (DC) is a (Windows) server that authenticates user identities and authorizes their access to resources.
An Azure Domain is not the same as a domain (DNS) web host names.
At https://portal.azure.com/#settings/directory, the “Domain” text is a combination of the root account email address text in front of “.onmicrosoft.com”. For example, johndoe@whatever.com becomes Domain johndoewhatever.onmicrosoft.com (without the TLD such as “.com”).
Portal Search AAD/Entra
-
Press G and / to position the cursor to the Search field at the top.
-
Type Entra for the Services related to that name.
-
Click for the blade called Entra ID .
https://portal.azure.com/#view/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/~/Overview
Tenants in Entra ID
-
Highlight and copy the value of the Name field, such as “something.onmicrosoft.com”.
-
Notice the “Tenant ID” GUID below it.
-
Open another browser tab (temporarily) to find the Tenant ID based on DNS host/domain (web host) name such as “contoso.com” or “something.onmicrosoft.com”:
-
Paste the name and click “Find my tenant ID” to see the “Directory ID” (GUID), for example:
6babcaad-1234-5678-789a-9fd97c0b779f
- Click “Copy to clipboard”.
- Remember the last few characters of the GUID returned.
-
Switch back to the browser Portal tab.
Tenant Switching
-
To switch among tenants in the Portal GUI, use the “Directory + subscription” filter at the top menu of every screen:

Within PowerShell, define the default Tenant (if you need to sign into more than one Tenant):
Set-AzureRmContext
Tenant = Directory
-
Click the icon at the top bar that looks like a notebook with a funnel.
https://portal.azure.com/#settings/directory
Notice the Directory ID GUID is the same as the Tenant ID GUID.
DEFINITION: A Directory (as in AAD/Entra) is where your Tenant metadata is stored.
Everything you do in Azure must be under some Tenant.
Each tenant is independent of all other tenants.
A tenant represents an organization in AAD/Entra.
Users, Groups, Apps
At the right is a count of Users, Groups, Applications, and Devices managed under that Tenant. (From Tim Warner)
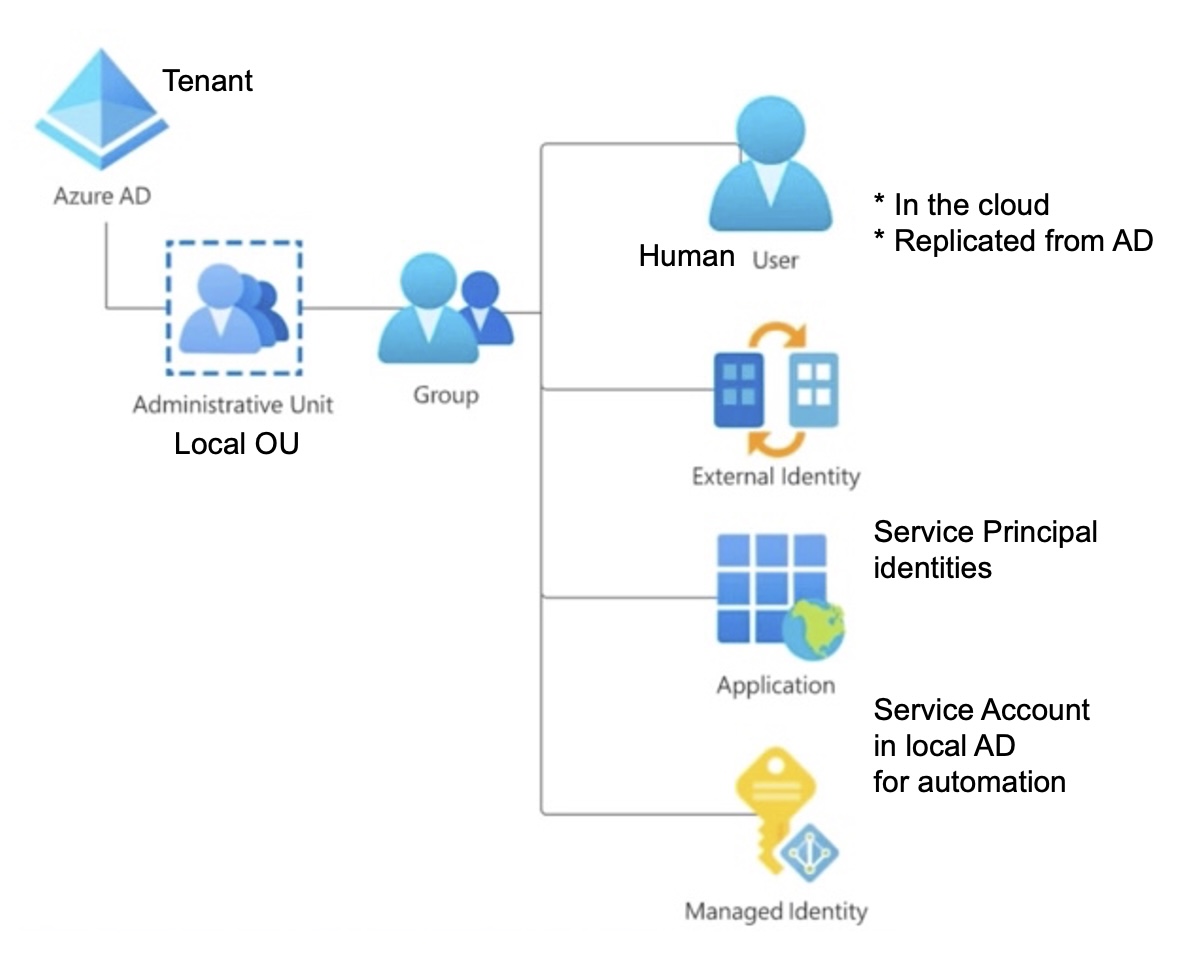
Federation
Microsoft has created integrations with Enterprise SaaS applications such as Dropbox, Google Docs, AWS, Salesforce, SAP, Concur, etc.
“External Identity” are Guest users with a credential federated from another Identity Store (Facebook, Google Gmail, GitHub, etc.) or a new SAML/WS-Fed IdP.
After an IdP is defined, define User flows (see AD B2C).
(from Tim Warner)
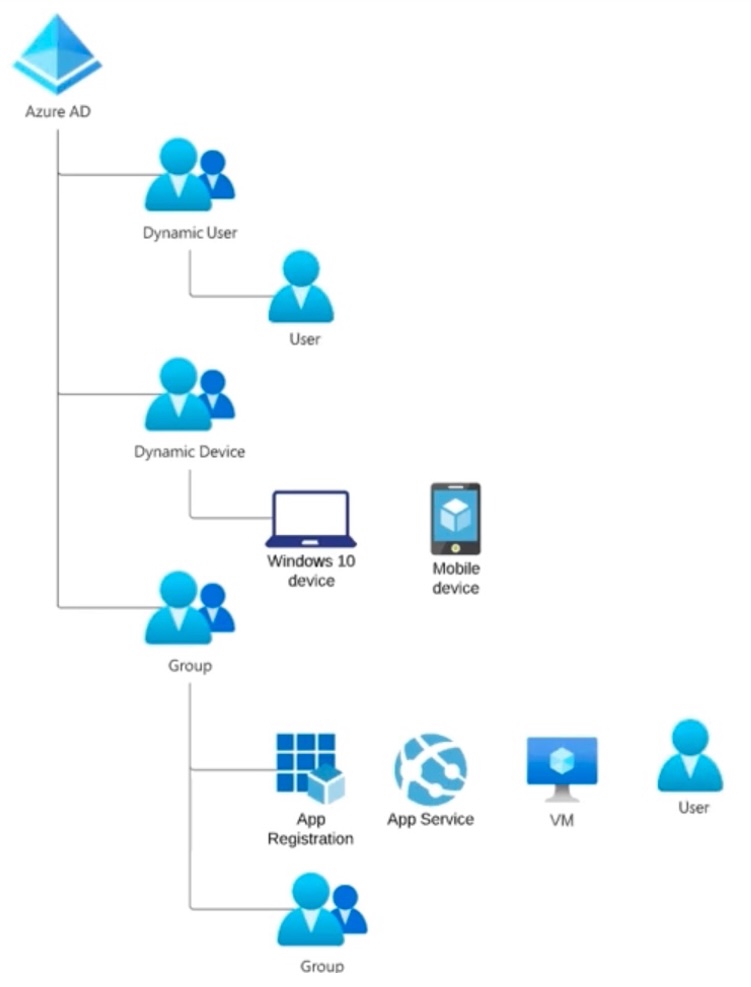
“Managed Identities” are also called “Service Accounts” used for authenticating automation services. Such accounts are assigned a GUID instead of email addresses for human users.
Invitation from Federation
(from Tim Warner)
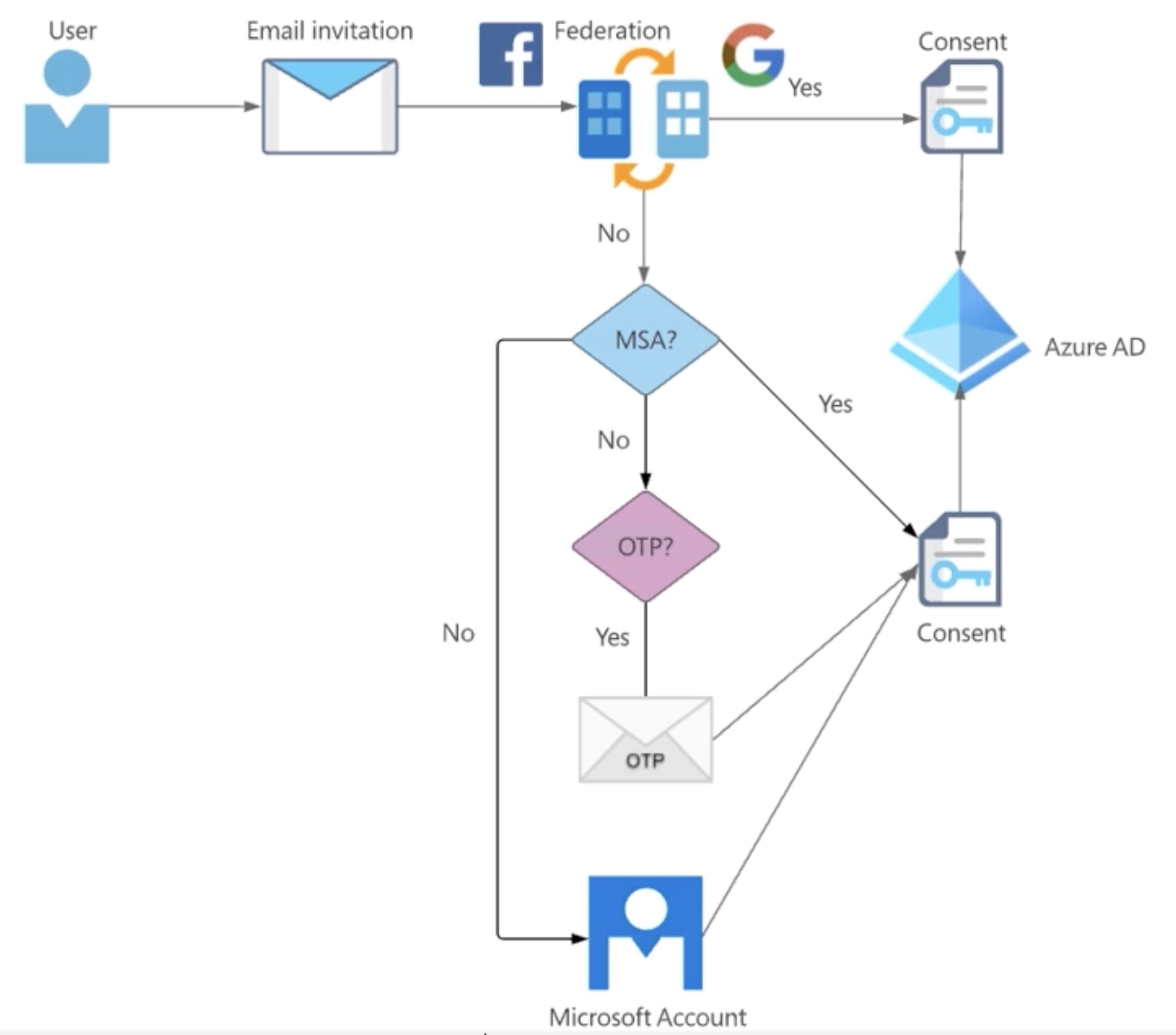
There are two types of Consent to Entra ID: a) Federation
b) Non-federated MSA (Microsoft Account from Skype, XBox)DEFINITION: OTP (One-Time Password) is emailed to the user.
Create New Group
Groups make authorization easier.
Groups can be nested under another Group.
- Select “All Groups”.
-
Select “New Group”.
Membership type “Assigned” are manually selected into each group.
Membership type “Dynamic” Users and Devices are completely (automatically) controlled by Azure AD, which populates membership based on user/device properties.
There are custom extension properties. Selecting Property: city Operator: Equals Value: Tampa yields Rule syntax:
(user.city -eq "Tampa")
-
Click “Create”.
Alternately, Powershell commands to create a group: VIDEO
Create-AzureADGroup -DisplayName "Tampa Users" -MailEnabled $false -SecurityEnabled $true -MailNickName "TampaUsers" -Description "Users in Tampa"
Licenses
Each license has its own options.
The license defaults to “Entra ID Free” to begin.
P1 provides Conditional Access.
“EMS (Enterprise Mobility + Security E5)” includes:
- AAD/Entra - the cloud-based IAM service to control access to internal and external applications
- Microsoft Intune for MDM (Mobile Device Management) but also PCs to remote reset and wipe. compliance status
- Azure Info Protection protects documents tagged to not be shared
- Microsoft Cloud App Security
- Microsoft Advanced Threat Analytics (ATA) is an on-prem. platform to protect against targeted cyber attacks along the “Cyber Kill Chain” attack process (Domain Dominance) by parsing network traffic to create a behavioral profile about user activities. It is a cloud-based triage tool that displays incidents on a timeline.
“Microsoft 365 E5 Developer (without Windows and Audio Conferencing)”
“Microsoft Power Apps Plan 2 Trial”
“Microsoft Power Automate Free”
“Power Virtual Agents Viral Trial”
License “Entra ID Premium P2” for production enterprises. P2 provides “Identity Protection” and “Identity Governance” features. P2 is needed for MFA (Multi-Factor Authentication) and PIM.
P2 PIM (Privileged Identity Management)
For those with a P2 license, Entra ID Privileged Identity Management (PIM) provides elevated access on a JIT (Just-in-Time) basis for a limited time. access. PIM provides audit logs to enable reviews of accesses.
Email is automatically sent when a role assignmnet is made outside of PIM. So do all access changes from the PIM UI, using “Privileged Authentication/Role Administrator” role assignments. Assignment can be permanent or based on time and date range.
-
REMEMBER: PIM must be enabled by the Global Admin after MFA sign-on.
-
Users search for PIM, Azure resources, to see assignments to activate yourself:
https://portal.azure.com/#view/Microsoft_Azure_PIMCommon/ActivationMenuBlade/~/azurerbac
- PROTIP: Bookmark the above URL
- Admins approve
- The user would see a Subscription with role “Specified access”.
-
User should Deactivate after using rather than letting the clock run out.
Policy Definition options: ???
- Allowed VM SKU’s
- Locations
- Allowed Resource Type
- Allowed Storage Account SKUs
Conditional Access Policy
Another P1 or P2 feature to limit granting of user access to only designated IPs, geographic regions, types of computer, etc..
Those under this require use of MFA.
MFA
MFA (Multi-Factor Authentication) is a P1 or P2 feature.
VIDEO: It’s at https://account.activedirectory.windowsazure.com/UserManagement/MultifactorVerification.aspx reached from
- Service: (Entra ID)
- Manage: Users on the left menu.
REMEMBER: VIDEO: There is no spanning between AAD/Entra and AD RBAC roles:

Built-in User Roles for RBAC
PowerShell command lists 75 user roles:
Get-AzureRMRoleDefinition
-
Application Administrators can create and manage all aspects of enterprise applications, application registrations, and application proxy settings.
-
Application Developers can create application registrations when the “Users can register applications” setting is set to No.
-
Authentication Administrators can set or reset non-password credentials for some users and can update passwords for all users.
-
Azure DevOps Administrators can manage the Azure DevOps policy to restrict new Azure DevOps organization creation to a set of configurable users or groups.
-
Azure Information Protection Administrators have all permissions in the Azure Information Protection service.
-
B2C User Flow Administrators can create and manage B2C User Flows (also called “built-in” policies) in the Azure portal.
-
B2C User Flow Attribute Administrators can add or delete custom attributes available to all user flows in the tenant.
-
B2C IEF Keyset Administrators can create and manage policy keys and secrets for token encryption, token signatures, and claim encryption/decryption.
-
B2C IEF Policy Administrators can create, read, update, and delete all custom policies in Entra ID B2C and therefore have full control over the Identity Experience Framework in the relevant Entra ID B2C tenant.
-
Billing Administrators can makes purchases, manages subscriptions, manages support tickets, and monitors service health.
-
Cloud Application Administrators have the same permissions as the Application Administrator role, excluding the ability to manage application proxy.
-
Cloud Device Administrators can enable, disable, and delete devices in Entra IAD and read Windows 10 BitLocker keys (if present) in the Azure portal.
-
Compliance Administrators have permissions to manage compliance-related features in the Microsoft 365 compliance center, Microsoft 365 admin center, Azure, and Microsoft 365 Security & Compliance Center.
-
Compliance Data Administrators have permissions to track data in the Microsoft 365 compliance center, Microsoft 365 admin center, and Azure. Users can also track compliance data within the Exchange admin center,
-
Conditional Access Administrators have the ability to manage Entra ID Conditional Access settings
-
Exchange Administrators have global permissions within Microsoft Exchange Online, when the service is present.
-
Directory Readers can read basic directory information.
-
Groups Administrators can create/manage groups and its settings like naming and expiration policies.
-
Security Administrators have permissions to manage security-related features in the Microsoft 365 security center, Entra Identity Protection, Azure Information Protection, and Microsoft 365 Security & Compliance Center.
BTW, after you follow instructions below on setting up CLI, this Bash command lists all the pre-defined roles:
az role definition list -o table --query [].roleName
For a count (260 at time of writing):
az role definition list --query [].roleName | wc -l
The basic categories of roles are owner, contributor, and reader:
- Owners have full access to all resources, including the right to delegate access to others.
- Contributors can create and manage all types of Azure resources but can’t grant access to others.
- Readers can view existing Azure resources.
Custom Roles
Examples of Custom-defined roles are:
- Reader Support Tickets
- Virtual Machine operator - can create and manage virtual machines
Let’s look at a custom role definition to clarify the terms:
{
"Name": "Virtual Machine Operator (Custom)",
"Id": null,
"IsCustom": true,
"Description": "Allows to start and stop (deallocate) Azure VMs",
"Actions": [
"Microsoft.Compute/*/read",
"Microsoft.Compute/virtualMachines/deallocate/action",
"Microsoft.Compute/virtualMachines/start/action"
],
"NotActions": [
]
"DataActions": [
]
"NotNotActions": [
]
"AssignableScopes": [
"/subscriptions/SUBSCRIPTION_ID"
]
}
Role definitions are at the center of this diagram about RBAC (Role-Based Access Control):
REMEMBER: There are four ways to assign resource rights to a user:
- Direct assignment of user to resources.
- Group assignment - all AAD/Entra group members access rights through user association with a group
- Rule-based assignment - when a resource owner creates a group and uses a rule to define which users are assigned to a specific resource, attaching a role definition to a user, group, service principal, or managed identity at a particular scope.
- External authority assignment - such as on-prem. directory of SaaS app.
DEFINITION: Each Service Principal can request an Entra ID token to access Azure resources and assign users and groups.
Role Assignment
Access is granted by creating a role assignment.
Access is revoked by removing a role assignment.
Resource Providers, Actions, Operations, Permissions, Scopes, Groups, Policies
https://learn.microsoft.com/en-us/azure/azure-resource-manager/management/azure-services-resource-providers
“Microsoft.KeyVault”, “Microsoft.Compute”, etc. are providers which provide the programming to respond or block APIs requesting some functionality.
Each line under Actions defines a set of Permissions permitted. Each line under NotActions defines what is denied.
Operations (such as read, write, delete, etc.) are carried out by providers.
PowerShell to process the custom role definition JSON (above):
wget https://...json
// Get the Subscription ID associated with the current user context:
$subscription_id = (Get-AzContext).Subscription.id
// Replace SUBSCRIPTION_ID within JSON file:
(Get-Content -Path $HOME/customRoleDefinition.json) -Replace 'SUBSCRIPTION_ID', $subscription_id |
Set-Content -Path $HOME/customRoleDefinition.json
// Grant assess by creting a role assignment:
New-AzRoleDefinition -InputFile ./customRoleDefinition.json
// Confirm:
Get-AzRoleDefinition -Name 'Virtual Machine Operator (Custom)'
PHASE 21. Scopes
The “AssignableScope” in the JSON is illustrated at the lower-right of the diagram.
VIDEO: After assignment, the SUBSCRIPTION_ID is replaced with the Subscription ID GUID assigned.
Roles can be scoped at several levels (from the Tenant Root Group):
-
Management group (containers)
-
Subscription
-
Resource group
-
Resource
Permissions at one level are inherited to child scopes, so
Permissions are additive: the sum of roles at various levels is what a user can do.
A user inherits permissions from the management group to which the user has been assigned.
Management Group Policies
- Navigate to the “Policy” blade.
-
Definitions
In Azure, policies are for evaluating compliance among Resources and their properties, not to control access to resources.
VIDEO: Policies can be assigned to scopes to limit what can be assigned to management levels and change what has been assigned:
Policy effects include Append, Audit, Deny, Modify, etc. Also: Enforce OPA (Open Policy Agent) Constraint and Enforce Rego Policy.
-
Select a category from Categories dropdown.
For example: Require a tag and its value on resources
See the Tags section above.
To do remediation, define a Managed Identity.
Devices on AAD/Entra
A “Registered” device is personally owned and signed in with a personal Microsoft or local account. It can access mobile and Windows 10 but not Windows Servers.
A “Joined” device exists only in the cloud to access Windows 10 and Windows Server 2019 VMs.
A “Hybrid” AAD/Entra joined device can access on-prem Windows 7, 8.1, 10 and Server 2008 or newer.
Role Assignments
REMEMBER: Actions are also called “Operations” at different Scopes.
-
See “Your role”? (avoid using “Global Admin”)
-
VIDEO: Click “+ Add” to create a new Tenant.
PROTIP: Tenant Type “Entra ID” by itself is actually “B2B” = Business to (2) Business. “B2C” means Business to (2) Consumers, or connection to External Identities on LinkedIn, Google, Facebook, etc.
-
Cancel out by searching for AAD/Entra again.
Various roles can be can be defined for a tenant - LIMIT: Up to 2,000 roles per individual tenant.
READ: Role Assignments on Azure Resources from Azure Pipelines
ASG (Application Security Groups)
ASGs are wrapped by a NSG (Network Security Group) which route traffic.
- Admins can RDP.
- Users cannot RDP.
Resources
Phase 10. Resource Groups
Each resource lives in one (and only one) Resource Group.
Each resource must be in a resource group. So before provisioning any resource, create a resource group for it to be placed in – for provisioning, monitoring, and maintenance.
From ASM to ARM
On July 1, 2019, Microsoft fully transitioned from the “classic” (older) Azure Service Management (ASM) when Multi-factor authentication (through the PhoneFactor Web (PFWeb) portal), API Management, BizTalk, and Managed Cache became available to the Azure Resource Manager (ARM).
ASM had “Cloud Services” and “Affinity Groups” which is structured with Resource Groups (logical containers) providing a single-resource point-of-view [i.e. manage a single resource at a time].
Also, instead of 2 racks on ASM, ARM resources can span 3 racks of computers.
ARM tokens
- A user (or service principal) acquires a token for Azure Resource Manager (ARM).
- The token includes the user’s group memberships (including transitive group memberships).
- The user makes a REST API call to Azure Resource Manager with the token attached.
- ARM retrieves all the role assignments and deny assignments that apply to the resource upon which the action is being taken.
- ARM narrows the role assignments that apply to this user or their group and determines what roles the user ahs for this resource.
- ARM determines if the action in the API call is included in the roles the user has for this resource.
- If the user doesn’t have a role with the action at the requested scope, access is not granted. Otherwise, ARM checks if ta deny assignment applies.
- If a deny assignment applies, access is blocked. Otherwise access is granted.
ARM includes parallelization when creating resources for faster deployment of complex, interdependent solutions. ARM also includes granular access control, and the ability to tag resources with metadata.
ARM handles Authentication for access to back-end Web App, Data Store, Virtual Machines, etc.
REMEMBER: The az deployment CLI command is used to deploy ARM templates.
#!/usr/bin/env bash
az login
az account set --subscription $subscription-name-or-id
az deployment group create \
–-subscription $subscription-name-or-id
--resource-group $resource-group-name
--template-file $path-to-arm-template.json
After this command, pass in the parameters to complete the command. Specify the type of deployment scope using one of four keywords:
- group for resource group deployments
- sub for subscription deployments
- mg for management group deployments
- tenant for tenant deployments
Instead, to use PowerShell, use the New-AzResourceGroupDeployment cmdlet:
Connect-AzAccount
Set-AzContext -Subscription "xxxxxxxx-xxxx-xxxx-xxxx-xxxxxxxxxxxx"
New-AzResourceGroupDeployment
-ResourceGroupName $resource-group-name
-TemplateFile $path-to-template
Verify the deployment:
az deployment group list –output table
Create Resources: Automation options
- Azure portal GUI
- Azure Bash CLI (az commands)
- Azure Cloud Shell which enable: Azure PowerShell (Az modules)
- JSON Templates IaC templates (by custom REST API clients)
- Azure Bicep (like Terraform)
- Azure programmatic SDKs using programming languages C# .NET, Java, Python, NodeJs (JavaScript), etc. calling APIs
PROTIP: A resource group can contain resources from multiple regions.
PROTIP: When naming Resource Groups, keep in mind that they are used to organize resources so that’re easier to delete. So limit the number of resources under each one so that you’re not blocked from deleting the group because you still need that one resource. So using Resource Groups for each point in the lifecycle makes sense (dev, qa, stage, green, blue, etc.).
If no dashes are in the name, double-clicking on that name would select the entire name.
A Resource Group name can be a single character. It can begin with a number.
PROTIP: In production, design Resource Groups for work groups to have the permissions they need. For example, core infrastructure such as Networking. The destination of logs and metrics should be viewed and managed using a whole different account than accounts used to create the data.
-
After you get CLI setup, list resource groups created:
az group list -o table
For more details (SSH, Managed By), remove “-o table”. See https://docs.microsoft.com/en-us/cli/azure/manage-azure-groups-azure-cli and https://docs.microsoft.com/en-us/azure/azure-resource-manager/management/manage-resource-groups-cli
A resource cannot be split among several resource groups, each be a member of a single resource group.
References on naming conventions:
- https://daniel-lumb.medium.com/azure-resource-group-structure-measure-twice-cut-once-565c50e13c9
Your own cloud shell
-
PROTIP: Click the browser profile icon and select the identity you need (if you have multiple accounts). You’ll likely have an account based on your Gmail, another for school email, a work email, etc.
Azure brings up the account based on what it stored the last time you logged in. If you don’t use browser profiles, you’ll have to log off and back again, which is a hassle.
BTW within each browser profile, you can login to GitHub, Pocket, or other service so your bookmarks is available on all profiles.
-
Go to https://shell.azure.com

-
Click “Bash” (since we’re using CLI scripts). Or “PowerShell”.
If this is the first time, you’ll see “You have no storage mounted”:

-
PROTIP: Instead of clicking “Create storage” (which will cause Azure to assign its own names), click “Show advanced settings” to specify the Resource Group name for your storage account:
- For “Cloud Shell region”, select your favorite location, such as “West US”.
- For “Resource group”, follow your naming convention.
- For “Storage account”, follow your naming convention.
- For “File share”, follow your File naming convention.
- Click “Create storage”.
PROTIP: Files in your CLI clouddrive folder is stored in that Storage account, beginning from CLI history, etc.
- In Portal: Resource Groups notice default names created:
- cloud-shell-storage-westus
- NetworkWatcherRG
az feedback
PROTIP: If your command doesn’t come back, press command+R to reset the browser page.
Cursor up to retrieve previous commands.
To open an issue, run:
az feedback
az interactive
-
VIDEO: There is a nifty code completion facility for az commands:
az interactive

-
Press Enter to bypass the “Error loading command module” messages.
-
az » is a reminder that within interactive you don’t have to type the “az” command, just the sub-command and other parameters.
Home folder commands
-
To see your current folder:
pwd
If your first name is “wilson” then you’ll see:
/home/wilson
-
REMEMBER: The above path is represented by both “~” (tilde) and the variable $HOME:
cd $HOME; pwd
CLI Proper Prompt
-
List all files and folders, using to see hidden files as well:
ls -al
-al enables display of hidden files such as .bashrc
It’s a Linux convention to put a period in front of file names so the operating system knows to treat them as hidden.
-
Copy and paste this string to have the prompt always appear in a consistent place where you have room to type:
export PS1="\n \w\[\033[33m\]\n$ "
Let’s change it to your taste so it shows up every time you get a Cloud Shell prompt.
And you will be opening a lot of new sessions.
Time out recovery
If there is no response in CLI, you probably were timed out (disconnected) automatically.
-
Press Ctrl+R (command+R on a Mac) to refresh, confirm Reload, then click the Cloud Shell again.
PROTIP: See if the time it takes to do that is about the same as to az login again from your local Terminal/Console.
Edit .bashrc
-
Open the file in a text editor (an instance of Visual Studio Code):
code .bashrc
Alternately, click the squigly brackets on the line where you select Bash or PowerShell.
-
Edit the string (near the bottom of the file):
PS1=${PS1//\\h/Azure} -
Optionally: althrough Terraform is pre-installed in Azure Cloud Shell, define an alias so you can type just tf instead of terraform:
alias tf="terraform $1" # provide a parameter
-
TODO: There are other aliases for your productivity. They save a few microseconds a time, but their advantage is to keep your mind focused, avoid task-switching.
-
Near the last line, navigate into the clouddrive:
cd clouddrive
That’s where it’s better to git clone repos into.
-
PROTIP: At the bottom of the file, add a # sign. This is because Azure automatically adds to the bottom a line:
PS1=${PS1//\\h/Azure}Since that line does not add a new line, the line is interpreted as a comment line.
-
To save and quit, press Ctrl+Q or click the “…” at the top right of the edit box.
Notice there is now a tilde to display the pwd (present working directory):
-
List all files and folders, using to see hidden files as well:
ls -al
-al enables display of hidden file .bashrc
clouddrive -> /usr/csuser/clouddrive shows a redirect to another path
-
PROTIP: Notice that clouddrive is a redirect to the physical folder at:
ls -al /usr/csuser/clouddrive
Git clone my Bash CLI scripts
Several utility programs come pre-installed in Azure Cloud Shell. Git is one of them.
-
Obtain a copy of my repository containing Bash CLI scripts for use in Azure:
git clone https://github.com/wilsonmar/azure-quickly cd azure-quickly
NOTE: If you work with a private repo, you’ll need to create a SSH key, paste the contents of the public key in GitHub GUI, and use a different command, such as:
git clone git-123456@wilsonmar/azure-quickly cd azure-quickly
-
To obtain recent changes:
git pull
Encrypted Passwords
PROTIP: It’s better to use Azure Key Vault, but this is better than storing cleartext in GitHub.
-
In a PowerShell CLI terminal, manually encrypt a secret under your account:
$password = 'Super@Secret3Passwordx' $securePassword = ConvertTo-SecureString -Force -AsPlainText -String $password
CAUTION: Run the above manually. Do not put the above commands in a script stored in GitHub.
https://www.pdq.com/blog/secure-password-with-powershell-encrypting-credentials-part-1/
NOTE: There is no CLI Bash equivalent for this.
-
The value of $securePasswords can now be saved in a file which exports an environment variable. You still should not hard-code encryption keys in code so that it can be cracked over a long period of time by powerful computers.
-
To unencrypted secret (under the same account) within a sample command:
$myapp = New-AzADApplication -DisplayName '...' -HomePage 'http://...' -IdentifierUris 'http://...' -Password $securePassword
NOTE: You don’t have to unencrypt first. Microsoft’s commands handle that for you. Cool, eh?
https://www.guardicore.com/cyber-security-platform/
Terraform on Azure
A Terraform client is pre-installed in Azure Cloud Shell.
terraform version
Ignore the version upgrade message. Azure keeps it up to date as appropriate.
https://cloudskills.io/courses/terraform-azure https://github.com/lukeorellana/terraform-on-azure https://github.com/CloudSkills/Terraform-In-Azure-Workshop
https://www.facebook.com/CloudSkills.io/ https://blog.cloudskills.io/getting-started-with-terraform-on-azure-tips-and-tricks/
https://www.udemy.com/course/terraform-on-azure/ Terraform on Azure
https://www.udemy.com/course/azure-kubernetes-service-with-azure-devops-and-terraform/ Azure Kubernetes Service with Azure DevOps and Terraform
Bash shell script coding
az vm list -g QueryDemo \
--query "sort_by([].{Name:name, Size:storageProfile.osDisk.diskSizeGb}, &Size)" --output table
–query is described https://docs.microsoft.com/en-us/cli/azure/query-azure-cli
To customize a column name, specify it on the left side before a colon within curly braces:
az container list --query "[].{Name:name,Location:location}" --output table
The empty brackets indicate the entire set. Put in a number for a specific row. A range from 0:3.
More query techniques are decribed here.
NOTE: Azure Citadel has a deep tutorial on –query parameters
Create Resource Groups
DEFINITION: A resource group is a logical container for resources deployed on Azure: virtual machines, Application Gateways, CosmosDB instances, etc. Many resources can be moved between resource groups.
Resource groups also define a scope for applying role-based access control (RBAC) permissions which limit access to allow only what is needed.
-
Create resource group (under a subscription) for location, after viewing briefings on CLI Bash or Storage (if you haven’t already):
az group create --name $MY_RG --location $MY_LOC Alternately, for more commentary, use the portal GUI:
- Optionally: Drag and drop “Resource Groups” Home menu item to the bottom of the list. That’s because you can …
- PROTIP: Hold down G and press R for Resource Groups.
- PROTIP: Hold down G and press , (comma) to focus on the command bar.
- If “+ Create” is highlighted, press Enter to invoke it.
- Select the appropriate Subscription.
-
Type your Resource group name using your organization’s naming conventions:
PROTIP: Include the region code in the Resource Group Name.
Subscription code, etc.
PROTIP: Resource groups have a flat structure: they cannot be nested like Management Groups.
Deleting a resource group results in deletion of all resources contained within it. So resource groups make it easy to remove a set of resources at once. That’s great for non-production environments.
Region = Location jmespath queries
View an interactive map of Azure data centers around the world.
-
If you already know how to use CLI Bash and jmespath queries, get a count of Azure’s regions:
az account list-locations --query "[].name" -o tsv | wc -l
68 is the response at time of writing.
In 2021, Microsoft is building 100 data centers a year.
-
PROTIP: Beware that some regions are “(stage)”, such as this table of regions with “westus” in its name, so this command and its results are not reliable:
az account list-locations --query "[?contains(name, 'westus')]" -o table
Name DisplayName RegionalDisplayName ------------ ----------------- ---------------------- westus2 West US 2 (US) West US 2 westus3 West US 3 (US) West US 3 westus West US (US) West US westusstage West US (Stage) (US) West US (Stage) westus2stage West US 2 (Stage) (US) West US 2 (Stage)
-
PROTIP: To list regions, use github.com/blrchen/azure-data-lab/blob/main/Regions.json which contains metadata about each region shown on AzureSpeed.com. For example:
"availabilityZoneCount": 3, "availabilityZoneStatus": "3 zones", "displayName": "West US 2", "geography": "US", "latitude": "47.233", "longitude": "-119.852", "pairedRegion": "West Central US", "physicalLocation": "Washington", "regionalDisplayName": "(US) West US 2", "regionName": "westus2", "storageAccountName": "azsptwestus2", "regionAccess": true
-
blrchen’s response goes beyond what Azure returns in its list all properties (metadata) for the “westus2” region:
az account list-locations --query "[?name == 'westus2']" -o json
[
{
"displayName": "West US 2",
"id": "/subscriptions/32f0f1ee-690d-4b02-9e58-baa3715aabf7/locations/westus2",
"metadata": {
"geographyGroup": "US",
"latitude": "47.233",
"longitude": "-119.852",
"pairedRegion": [
{
"id": "/subscriptions/32f0f1ee-690d-4b02-9e58-baa3715aabf7/locations/westcentralus",
"name": "westcentralus",
"subscriptionId": null
}
],
"physicalLocation": "Washington",
"regionCategory": "Recommended",
"regionType": "Physical"
},
"name": "westus2",
"regionalDisplayName": "(US) West US 2",
"subscriptionId": null
}
]
-
TODO: Select the Region (aka Location) closest to intended users, for pricing, and have features available.
PROTIP: There are differences in prices among regions. “WestUS” is generally the least expensive among US regions.
PROTIP: Speaker Recognition is currently only supported in Azure Speech resources created in the westus region.
Individual resources created within a Resource Group are placed in the same region.
CLI Naming convensions
PROTIP: Since so many az commands refer to an Azure Resource Group, my scripts specify Resource Group or Location as the last item, using these naming conventions for environment variables:
MY_LOC="eastus" MY_RG="azuremolchapter2" az group create --name "${MY_RG}" \ --location "${MY_LOC}"PROTIP: Me standardizing means that you can use a different name safely by doing a “Change All” across all files.
TOOL: Lookup nearest city given Longitude & Latitude using the GeoDB API.
PHASE 11. Tags
PROTIP: Even while during individual development, take a few seconds to add tags in resource creation scripts to enable not just security, accounting, and logging processes, which may provide troubleshooting tools for developers from the beginning.
-
To create a Tag using CLI:
MY_TAG_NAME="$ DELETE_DATE="2023-12-31"
az resource tag \ --name "$MY_TAG_NAME" \ --resource-group "$MY_RG" \ --resource-type "Microsoft.Network/virtualNetworks" \ --tags Department=Finance DeleteDate="${DELETE_DATE}" Env=TRG Company=MyCo Sovereignty=Germany Project=Advance1 Dept=FIN Sensitivity=HIGH Customer=A3C2132 Usage=DailyREMEMBER: Each tag is for a specfic region, Resource Type, Resource Group.
REMEMBER: Tags do not cascade via inheritance like permissions unless a policy allows that. Child resources don’t inherit tags from group level.
NAMING CONVENTION: Tags are named with Title Case. Each tag is a “name=value” pair such as </pre>
PROTIP: CAUTION: Customer name can be considered confidential, so mask its value with a synonym value in Tags. The same goes for any sensitive value.
### Sensitivity
DEFINITION: “Sensitivity” refers to the security classification of data tagged.
PROTIP: The Sensitivity value should be the same SENSITIVITY CLASSIFICATION RANK as used in classifying within MS-SQL: NONE, LOW, MEDIUM, HIGH, CRITICAL
Classification label should also correspond to Azure Information Protection (AIP) which uses Azure Rights Management service (Azure RMS) to protect data with uses encryption, identity, and authorization policies:
- Personal
- Public
- General
- Confidential
- Highly Confidential
-
Using portal GUI:
-
Get to “Tags” service:
https://portal.azure.com/#view/HubsExtension/TagsBlade
- Click “Review + create” if you are not using Tags or if the resource doesn’t support tags.
-
Click “Next: Tags” if you can specify one according to your Tag Naming Convention:
LIMIT PROTIPS: Up to 50 Tags can be associated with each resource.
Tag names are limited to 512 characters.
Tag names for storage accounts have a limit of 128 characters.
Tag values can be up to 256.Tags are your own metadata for:
- Searching
- Viewing
- Billing
Each tag value is limited to 256 characters for all types of resources.
- Environment=Production or Staging or “NPT” (Non-Production/Test)
- Department or Accounting / cost center Charge Code
- Geography
- shutdown=6PM and startup=7AM for automation
Tags are not inherited from parent resources.
A resource be associated with up to 50 tags.
-
Click “Create” after “Validation passed”.
Lock RG to prevent deletion
- Select each production resource group.
- Click “Locks” menu.
- Type a name according to naming conventions.
-
Select a Lock Type: “Delete”.
More Policies
- Click Policies in the menu within a Resource Group blade.
- Click Definitions in the menu for a list of pre-defined policies under each scope (Subscription + Resource Group).
- Click “Policy definition” in the command bar.
- Field “Definition location” is the Subscription.
- Each rule is JSON syntax with “if”, “not”, “then”, etc. logic
-
Click the blue button to the right of “Policy definition” field for Available Definitions dialog where you can select a Type and Search filter text.
A common policy is Allowed locations.
- Each policy can be set to Enforced or Disabled.
- Optionally, define a Managed Identity for remediation.
-
Create.
Policies can also be defined under each Subscription. VIDEO: All Services -> Management Groups to apply governance conditions (access & policies) above.
To group policies under an initiative:
-
Click “Assign initiative” in the command bar.
Management Group hierarchy
- Search All Services for “Management groups”.
-
Add Management Group.
An initiative describes a group of policies across different management groups, subscriptions, resource groups.
- Click the group created and add more groups (up to 6 levels in hierarchy).
-
Under each leaf management group, add a Subscription.

Also create management group by using PowerShell, or Azure CLI. PROTIP: Currently, Resource Manager templates can’t be used to create management groups.
Policy creation
-
Select the Policy service.
Policies are rules stating which resources can be deployed to which locations
- Microsoft provides a number of built-in policies
- Create custom policies using JSON
Assign at resource level or resource group level
- Child resources don’t inherit tags from group level
PROTIP: All resources in a resource group should share the same lifecycle.
-
In the left menu select the Definitions pane under the Authoring section.
You should see a list of built-in policies that you can use.
-
Click G+ for focusing on “+ Policy” to press Enter to create a custom policy in the New policy definition dialog.
-
Set the Definition location, click the blue …. and select the Subscription for the policy to be stored in, which should be the same subscription as our resource group. Click Select.
-
Back on the New Policy definition dialog, type Name value of Enforce tag on resource.
-
For the Description, enter This policy enforces the existence of a tag on a resource.
-
For Category select Use existing and then select the General category.
- For the POLICY RULE, select all text in the box (command+A), then delete it.
-
Copy and paste the following into the box:
{ "mode": "Indexed", "policyRule": { "if": { "field": "[concat('tags[', parameters('tagName'), ']')]", "exists": "false" }, "then": { "effect": "deny" } }, "parameters": { "tagName": { "type": "String", "metadata": { "displayName": "Tag Name", "description": "Name of the tag, such as 'environment'" } } } } -
Click “Save”.
Uses for policy:
- restrict which Azure regions you can deploy resources to.
- restrict which types of virtual machine sizes can be deployed.
- enforce naming conventions to keep a consistent standard across all Azure resources.
Assign policy
To enable the policy, create an assignment. Assign it to the scope of your resource group, so that it applies to anything inside the resource group.
- In the policy pane, under the Authoring section on the left, select Assignments.
-
Select Assign policy at the top command bar.
-
In the Assign policy pane, click the blue …. for Scope. Select Resource Group. Click Select.
-
For Policy definition, click the blue …. In the Type drop-down, select Custom, select the Enforce tag on resource policy you created, then click Select.
-
Select Next to go to the Parameters pane.
-
On the Parameters pane, for Tag name enter Department.
-
Click “Review + create” then “Create” to create the assignment.
New Individual Resource
DEFINITION: Each Azure resource is an instance of a service you have already provisioned.
-
For a New Resource, hold down G and press N to select a new resource from Azure’s Marketplace of services.
NOTE: This is also reached by clicking “+ Create a resource” or Home icon then “+ Create a resource”.
Favorites
-
Within the Marketplace of services/resources, clicking the star icon labeled “Favorites” adds the item to the Dashboard (described in a section below).
New Web App
PROTIP: Launching a “Web App” means that you provision a VM (Virtual Machine) which incur charges continuously (until you go broke). A server is used to generate HTML and CSS files as needed (real-time) based on requests from users.
DOC: “Launching a Simple Web App in Azure”
New Static Web App
“Static web apps” serve the same (static) HTML and CSS files to all users pre-generated when saved (pushed) to GitHub. This means that users don’t have to wait for them to be generated.
-
In another browser tab, sign into GitHub and create a repository containing Nuxt.js or other template to generate HTML and CSS files.
- Scroll down the “Azure Marketplace” menu to click “Web”.
- Click “Static Web App (preview)”.
- Select the Resource Group created already.
- Type a Name that follows your Naming Convensions. For example, “msftlearn-core-infra-rg-dev” consists of
- “msftlearn” for the types of resources
- “hr” for Human Resources, “fin” for finance, etc.
- “core-infra” for what is contained within,
- “dev” or “prod” for environment
- “rg” for the type of resource it is (resource group)
- PROTIP: WARNING: Select a Region that’s the same as your Resource Group or you’ll incur inter-region network charges.
- For Deployment details: Source, select “GitHub” the default.
- Click “Sign in with Github” for a pop-up screen to enter the email address you used to create the GitHub account you want to associate.
- Type the code shown on your mobile 2FA (Authentication) mobile app to Verify.
- Click “Grant” each additional organization/account.
-
Click “Authorize …” to dismiss the pop-up.
-
You should get an email with subject:
[GitHub] A third-party OAuth application has been added to your account
-
Select the Organization, Repository, Branch created in the step above.
All Resources
-
Drag and drop All resources in the menu to the bottom of the list because you can reach it without a mouse by holding down G and pressing A.
That brings up a list of all resources you have already brought to life.
Region = Location
-
Go to Azure Resource Explorer:
-
To provides API calls and responses. Under your subscription / locations is JSON with logitude and latitudes of each location (region):
"id": "/subscriptions/.../locations/westus3", "name": "westus3", "displayName": "West US 3", "longitude": "-112.074036", "latitude": "33.448376"
-
On Google Maps, type in Search as “33.448376, -122.074036”.
Alternately, construct a URL such as:
-
Click to see it’s in downtown Phoenix. (For security, that is not the exact location so Amazon can’t drop a bomb on it).
Install Entra ID Module
-
In Windows, right-click run as Administrator.
-
On PowerShell:
install-module -name azuread -Force
PROTIP: Module names are not case sensitive.
Untrusted repository You are installing the modules from an untrusted repository. If you trust this repository, change its InstallationPolicy value by running the Set-PSRepository cmdlet. Are you sure you want to install the modules from 'PSGallery'? [Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "N"):
-
Type “A” to response above.
-
On PowerShell: Load the module (no response expected):
get-module azuread
-
Sign in:
Connect-AzureAD
PROTIP: User Role “Global Administrator” can do anything.
There are many “Limited administrator” roles.
get-azureaduser
Access Control (IAM) Roles
Role Scope of Security Principal (from narrowest)
- Container within Blob Service
- Queue
-
Storage Account
- Resource Group
- Subscription
VIDEO Add Role Assignment Role
- Owner
- Contributor - Backup Contributor & Operator
- Reader’
- Avere Contributor & Operator
- etc.
Assign access to:
- Entra ID user, group, or service principal
- User assigned managed identity
- System assigned managed identity
- App Service
- Container instance
- Container Registry Task
- Data Factory
- Function App
- Logic App
- Remote Rendering Account
- Virtual Machine
- Virtual Machine Scale Set
Management Certificates
Azure uses Management (x509 v3) Certificates (.cer file containing a public key) to access resources in an Azure Subscription.
There is a limit of 100 Management certs per Azure subscription (administrator).
- Development
- Test
- Pre-prod (Staging)
- Prod
Management Group for RBAC
Each Management Group is a container for one or more subscriptions
- You can build a hierarchy of these
- You can assign policies to a management group
for RBAC (Role-Based Access Control) Inheritance Scope: Management Groups are above Subscriptions above Resource Group container for Resources
Roles: Owner, Contributor, Reader (Observer), User Access Admin
- User
- Group in AD
- Service Principal - security identity used by app services
- Managed by Azure Identity
Role Assignment of Role Definitions which list operations that can be performed by the Security Principal.
See https://docs.microsoft.com/en-us/azure/role-based-access-control/troubleshooting
Limits = Quotas
REMEMBER: Quotas (Limits) cannot be increased in FREE subscriptions!
REMEMBER: Azure supports up to 15 tags per Resource Group.
Pricing Calculator
Estimate costs of various services.
https://azure.microsoft.com/en-us/pricing/calculator/
Cloud Shell
-
VIDEO Azure provides contextual prompts in their:
az interactive
Response:
This command is in preview and under development. Reference and support levels: https://aka.ms/CLI_refstatus Installing the Interactive extension... The installed extension 'interactive' is in preview. Do you agree to sending telemetry (yes/no)?
Create AZ Role
-
To create an AZ role in PowerShell, define a JSON file then:
az role definition create --role-definition "~/CustomRoles/ReaderShpportRole.json"
AZ API
-
Use the automation bash script for MacOS at
https://github.com/wilsonmar/mac-install-all
The “mac-install-all.sh” script places a secrets.sh file in your machine’s home folder.
The script takes care of installing the azure CLI
-
Edit the file there (not in the repo directory).
If in the secrets.sh file the TRYOUT string is edited to contain a known value for a module, that would be executed.
To execute all modules:
TRYOUT=”az-vm”
Alternately, to execute only one or a few modules, for example:
TRYOUT=”az-vm”
… the Bash script has been programmed to create an instance using az cli commands rather than manually copied and pasted onto a
Azure Cloud Shell instance launched on an internet browser as described (using command+shift+V) at:
https://docs.microsoft.com/en-us/cli/azure/azure-cli-vm-tutorial?view=azure-cli-latest
- Log in
- Create a resource group
- Create a virtual machine
- Get VM information with queries
- Set environment variables from CLI output
- Create the new VM on an existing public subnet (contoso.ws)
- Verify public access to one-page static page (like isitchristmas.com)
- Cleanup (remove vm instance if TRYOUT_KEEP is not specified)
- Display cost of above
Alternately, if in the secrets.sh file the TRYOUT string is edited to contain this:
TRYOUT=”az-func”
This creates an Azure (Serverless) Function, as described in commands listed at:
The unique aspect of the mac-install-all.sh script is that it does NOT require you to go from screen to screen typing steps by step starting from
https://azure.microsoft.com/en-us/services/functionsThe script executes a set of commands for you automatically so you get past the installation and configuration confusion, bringing your laptop to a point where you can work on changing the sample to the app you want. You can then re-run the script, and any changes to the underlying framework would be upgraded if needed.
Since Azure provides a small amount of free time to all accounts each month under their Consumption Plan, you can do several runs each month without spending any cash. See their Pricing.
The RYOUT does the following:
Account Password > Login > Tenant > Principal > APP_ID > Roles > Template > stop
Login
-
For attended manual log in:
az login
The response expected is a new tab to appear in your default browser window asking for your account.
Alternately, for unattended log in:
az login -u "$AZ_USER" -p "$AZ_PASSWORD"
If you have not signed up for a subscription, you’ll get an error such as: “No subscriptions were found for ‘None’. If this is expected, use ‘–allow-no-subscriptions’ to have tenant level accesses”
Set subscription
There can be more than one subscription, so set to just to use:
-
The JSON that comes back from az login can be retrieved again by:
RESPONSE=$( az account list)
-
Pick out the subscription from the list:
TODO:
-
Set the subscription:
az account set --subscription=
-
Set the cloud:
az cloud set --name AzureUSGovernment # or AzureChinaCloud, or AzureGermanCloud.
NOTE: Azure China cloud (azure.cn) is operated by 21 Vianet.
Permissions
CAUTION: Logging in online imbues you with a full set of permissions that a login using the az command does not fully possess.
Tenant ID
-
Once you have logged in, when you sign up for a Microsoft cloud service, Microsoft assigns to your account a Tenant ID. To obtain it:
AZ_TENANT=$(az account show --query 'tenantId' -o tsv)
echo $AZ_TENANT to yield something like: a7a02378-1e4b-4017-972e-9dfe53bc2b2f
See: Multi-tenant architecture
Resource groups (RGs) are used for RBAC, Automated Deployments, and Billing/Monitoring.

-
Put the Tenant ID value in the secrets.sh file so that future script runs can check whether that value has already been created.
-
Also note that before getting here the script created a pem file PROTIP: Create a .pem file from the rsa.pub file named $SSH_USER created for GitHub:
ssh-keygen -f ~/.ssh/$SSH_USER -m 'PEM' -e > $SSH_USER.pem chmod 600 $SSH_USER.pem
This is recommended instead of the alternative of asking Azure to –create-cert in command:
Service Principal
-
We next Create a Service Principal using Conventions for naming principals under RBAC (role-based access control):
This Azure CLI (command az) has the subcommand ad (for Active Directory) to create Service Principals (sp’s). We capture the response (in JSON format) in the variable return.
return=$(az ad sp create-for-rbac --name "$AZ_PRINCIPAL" \ --role owner \ --create-cert \ --query ['fileWithCertAndPrivateKey, appId, tenant] )
This JSON file the command puts in your $HOME folder:
{ "appId": "username", "displayName": "ServicePrincipalName", "name": "http://your app address", "password": passkey, "tenant": "XXXXXXXX-XXXX-XXXX-XXXX-XXXXXXXXXXXX" }The additional –query attribute makes
The first of three fields (fileWithCertAndPrivateKey) requested in the query is parsed using this command:
echo return | tr -d "[ ] \" \"" | awk -F, '{ print $1 }'To obtain the first part of the response, “/user/wisdom/tmpf14zjme.pem”, which is used in subsequent commands.
AZ_PEM_LOC=”echo return | tr -d “[ ] " "” | awk -F, ‘{ print $2 }’”
The second item in the query in the command above yields the APP_ID:
AZ_APP_ID=”echo $return | tr -d “[ ] " "” | awk -F, ‘{ print $2 }’”
The third item is the Tenant ID. Both of these are GUIDs.
The command has additional options:
az ad sp create-for-rbac -n "lnx" \ --role contributor \ --scopes /subscriptions/ssssssss-ssss-ssss-ssss-ssssssssssss
Login for sure
-
Now we take the NOTE:
az login --service-principal -u "$AZ_APP_ID" \ -p "$AZ_PEM_LOC" --tenant "$AZ_TENANT"
https://msdn.microsoft.com/en-us/library/azure/ad/graph/api/api-catalog is the older version of Microsoft Graph at https://developer.microsoft.com/en-us/graph https://dev.office.com/blogs/microsoft-graph-or-azure-ad-graph
BLAH: The name of the file created contains something like “tmpcgzysdch”, a random set of characters. So the script needs to figure out that file name. Thus we create the pem file and tell Azure.
-
TODO: Obtain the password text from within the file
Create a folder $HOME/certs/
-
Put the contents in a file name containing the value in $AZ_APP_ID, in the $HOME folder so that it won’t have a chance to get pushed to GitHub.
-
Login using credentials built above:
az login --service-principal $AZ_PRINCIPAL \ --username "$AZ_APP_ID" \ --role owner \ --tenant "$AZ_TENANT" \ --password "$HOME/certs/$SSH_USER.pem"
BLAH: The APP_ID and username are the same. Whatever.
-
Assign a role named “Reader” to the APP ID (username):
az role assignment create \ --assignee "$AZ_APP_ID" \ --role reader
-
List what resources were assigned to a APP_ID:
az role assignment list --assignee $AZ_APP_ID
If your APP_ID has not already been created:
-
To specify a module to run (not just install): If in the secrets.sh file the TRYOUT string is edited to contain “az”:
TRYOUT=”az”
QUESTION: limits to total concurrent executions across all functions within a given region to 100?
### Regional Zones for Egress
Regions are grouped into 4 zones for pricing network Egress:
- US, US Gov, Canada, Europe, UK, France, Switzerland
- East Asia, Southeast Asia, Japan, Australia, India, Korea
- Brazil, South Africa, UAE
- (DE Zone 1) Germany
Subscriptions
https://www.hashicorp.com/blog/go-big-or-go-small-building-in-azure-caf-with-terraform-cloud Microsoft’s Cloud Adoption Framework enterprise-scale landing zone architecture based on an Azure Virtual WAN network topology. The connectivity subscription uses a Virtual WAN hub.
Entra ID B2B (Business-to-Business)
allows an organization to securely share company applications and company services with guest users from other orgs, while retaining control over company data. Auth policies protect corp. data.
- Portal Menu > Entra ID. Select yours.
- Users. +New guest user. Type email. Invite.
- Guest user clicks “Get Started” in emai;.
Entra ID B2C (Business to Consumer)
enables customers can use a registered app with the Identity Experience Framework defines interacting with external multi-party Identity Providers (IdP’s) such as Facebook.
It makes use of SYN cookies and rate & connection limits defined by a Trust Framework policy.
- +Create a resource: Entra ID B2C
- Create.
- An additional B2C Tenant is created
- Create.
- Link to subscription.
ARM Templates
A parent template can launch nested templates.
Concise, yet comprehensive
Azure Bicep > ARM > Terraform
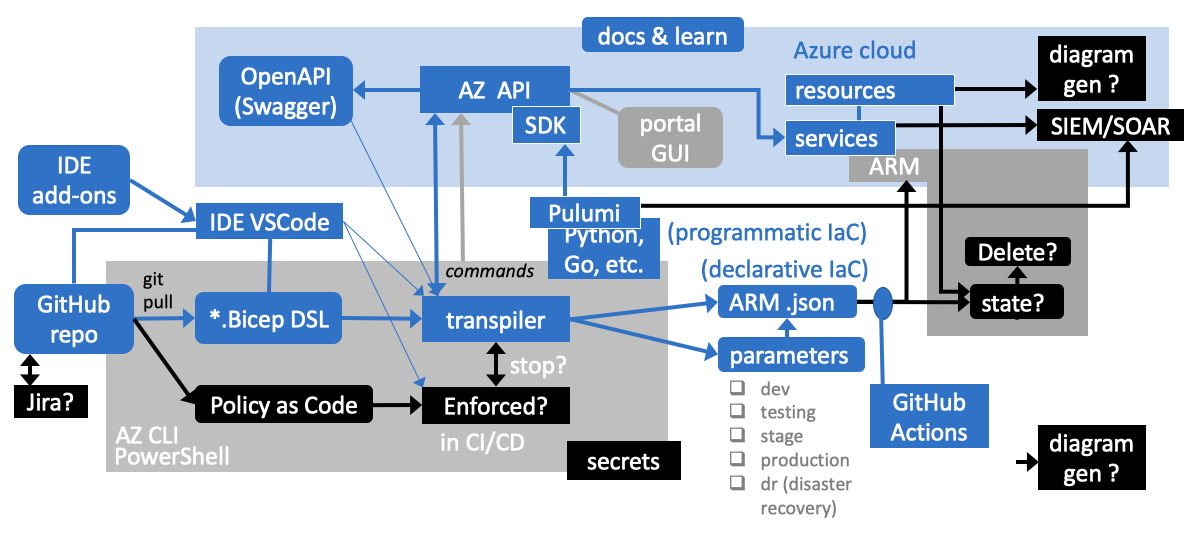 Click image for full screen. from a PowerPoint file.
Click image for full screen. from a PowerPoint file.
This diagram summarizes content in several docs and learn.
For a specific subscription within a Management Group (deployment scope) in Microsoft’s Azure cloud, the Azure portal GUI can be used to create resources interactively.
Behind the scenes, an Azure API calls the ARM services to create, modify, and delete resources.
Microsoft’s docs also talk about commands issued from az CLI and PowerShell terminals. These commands are also making calls to the same Azure API to create, modify, and delete resources. Additional commands can access services (such as Azure Key Vault) to manage secrets such as passwords and API keys.
Other security mechanisms include encryption, verifying identity, and strong authentication. To detect threats and intrusions, send logs to a central SIEM/SOAR system, such as Sentinel inside Azure or Splunk outside Azure. When anomalies are found, raise alerts by escalating emails, text messages, Slack, SMS, or other media.
When these security mechanisms are not created along with resources when created, it can be just a matter of minutes before bots discover vulnerabilities and hack your system. So Microsoft created the ARM (Azure Resource Manager) to create resources with tags and security controls based on JSON files processed together in a CI/CD (Continuous Integration/Continuous Deployment) pipeline run by GitHub Actions (or Azure DevOps). Several files can be linked together at deployment.
ARM works like Terraform and Ansible (from Red Hat), which have accompanying parameter files to enable different environments to be created from the same JSON-format files.
This approach, called “Declarative IaC, (Infrastructure as Code) is where the ARM service compares state and makes changes and deletions as necessary to achieve the desired state specified. Such “idempotent” logic achieves the same result each time the file is deployed. Duplicates are not created.
The alternative approach, called Imperative or Programmatic IaC, is where application programming code written in Python, Go, C#, etc. call the Azure SDK (Sofware Development Kit). One such program is Pulumi. Such programs need to create resources in the proper sequence, check whether resources have already been created, recognize errors, etc. Although more complex and thus difficult to maintain and debug, programming code has the flexibility to do anything, such as sending logs to a SIEM/SOAR system.
For better developer experience (DX), in 2021 Microsoft created the Bicep DSL (Domain Specific Language) read by a Transpiler that creates ARM JSON and parameters files. But the Bicep DSL code is also validated based on Azure API and OpenAPI (Swagger) files.
Note that, unlike Terraform, Bicep has no state file, so it doesn’t alter and delete resources based on changes in the Bicep file. Instead, Bicep creates ARM JSON files that are processed by the ARM service to create, modify, and delete resources.
Pulling Bicep code from GitHub enables versioning, and coordination with Jira or other product management tools. Highlighting and linting of Bicep code is automated by ARM and Bicep add-ons Microsoft has created for VSCode and other popular IDE text editors. Added “Integrations” enable the IDE to invoke the Bicep Transpiler to create ARM JSON files with parameters.
Perhaps the most important security feature is the use of Policy as Code that can identify vulnerabilities in resources created by Bicep and ARM JSON. Issues found would stop the CI/CD pipelines, with alerts to the developer. This is called Shift Left because it is done before the resources are created.
Lastly, graphic diagrams can be generated from either the resources created or, better yet, from Bicep or ARM JSON for better visualization to speed understanding and troubleshooting.
Current status: As of this writing (August 12, 2023):
-
Unlike Terraform, Bicep currently does not have additional providers for 3rd-party offerings such as Databricks, Snowflake, etc.
-
Bicep is not yet integrated into the Azure Portal, which has a “See in JSON” link for each resource.
Bicep PSRule
PSRule at https://github.com/Azure/PSRule.Rules.Azure leverage 270+ rules to validate Bicep code according to best practices and security requirements as defined in the Azure Well-Architected Framework.
-
Click the green “Use this template” to “Create a new repository” under your own GitHub account and repo name.
I recommend a name such as “rnd-bicep-psrule-play-01” to describe the purpose of the repo, to end up with:
https://github.com/wilsonmar/rnd-bicep-psrule-play-01
-
Provide a Description such as “Playground for Bicep and PSRule”.
-
Fix the .gitignore
-
Add a .gitattributes file to prevent CRLF line endings.
-
Click the green “Create repository from template” button.
CODEOWNERS
-
Change the CODEOWNERS file to point to your GitHub account, repo name, branch name, and owner accounts.
See https://help.github.com/articles/about-codeowners/
-
Customize the PULL_REQUEST_TEMPLATE.md file.
markdownlint
-
Configure .markdownlint.json at
https://github.com/wilsonmar/rnd-bicep-psrule-play-01/blob/main/.markdownlint.json
based on
https://github.com/DavidAnson/vscode-markdownlint#configurehttps://azure.github.io/PSRule-Rules-Azure/en/rules/module/
https://github.com/DavidAnson/markdownlint/blob/main/README.md
https://marketplace.visualstudio.com/items?itemName=DavidAnson.vscode-markdownlint
PSRule samples
-
In .ps-rule folder, review files Org_Rule.ps1 (PowerShell) and Org_Rule.md (Markdown).
Org.Rule.yaml defines the rule to require storage.
.devcontainer
ps-rule.yaml
https://aka.ms/ps-rule/options
https://aka.ms/ps-rule-azure/options
-
Schedule a future time when versions of requires: PSRule, etc.
.github/workflows/azure-analyze.yaml
.github/workflows/ms-analyze.yaml
-
It runs in GitHub Actions workflows (https://aka.ms/ps-rule-action), Azure Pipelines, and Visual Studio Code.
VIDEO by Bernie White, Microsoft MVP, on Azure Bicep. and Azure Bicep - The future of ARM templates by Kevin Oliver at Azure Thursday on Aug 12, 2021. and VIDEO: PSRule for testing Azure Bicep code references
VIDEO: Azure Bicep Native Parameter Files
Bicep Docs and Videos
The menu of Microsoft’s documentation on Bicep is at:
https://learn.microsoft.com/en-us/azure/azure-resource-manager/bicep/
3hr 18min Microsoft Learn: Fundamentals of Bicep:
Part 1 - 30min Microsoft Learn Module: Introduction to infrastructure as code using Bicep
- First look at Bicep file
Deploy Azure resources by using Bicep and:
Option 1: Azure Pipelines
Option 2: GitHub Actions
Part 2: Intermediate Bicep
Part 3: Advanced Bicep
-
Microsoft Learn Module on Bicep is the basis for
15-episodes on YouTube: - Azure Friday by Scott Anselman
- Deploy Bicep files by using Github Actions by Jay Gordon. Create an AKS cluster with secrets from Azure Key Vault.
- VIDEO:
- https://github.com/Azure/bicep
-
VIDEO: Bicep vs Terraform. which one should I use? by Jonathan D’Aloia at Adatis London
- BLOG: Pros & Cons
- Bicep Advanced Deployments - Part 1 by Kevin Oliver
-
Bicep Advanced Deployments - Part 2 by Kevin Oliver
- BLOG: Getting Started with Azure Bicep (Step-by-Step) by Nick Rimmer
Better developer experience (DX)
Creating a JSON ARM template requires complicated expressions, and the final result might be verbose.
But Bicep was designed to provide a syntax that’s easier to understand, better support for modularity and reusable code, and improved type safety.
Reference parameters and variables directly, without using complicated functions.
String interpolation is used in place of concatenation to combine values for names and other items.
Reference properties of a resource directly by using its symbolic name instead of complex reference statements.
Bicep automatically detects dependencies between resources. This process removes some of the work involved in template authoring.
Break down complex template deployments into smaller module files and reference them in a main template. This makes for easier management, greater reusability (easier sharing).
https://marketplace.visualstudio.com/items?itemName=ms-azuretools.vscode-bicep
CLI to create storage account
VIDEO: The imperative approach to create a storage account using CLI commands:
#!/usr/bin/env bash az login az group param location string = resourceGroup().location \ --location eastus az storage account create --name storagelearnlive \ --resource-group storage-resource-group \ --location eastus \ --sku Standard_LRS \ --kind StorageV2 \ --access-tier Hot \ --https-only true
Bicep File to create storage account
For example: a Bicep file to create a storage account and virtual network:
param resourceGroupLocation string = resourceGroup().location
param storageAccountName string = 'store${uniqueString(resourceGroup().id)}'
param vnetName string = 'vnet${uniqueString(resourceGroup().id)}'
resource storageAccount 'Microsoft.Storage/storageAccounts@2022-09-01' = {
name: storageAccountName
location: resourceGroupLocation
kind: 'StorageV2'
sku: {
name: 'Standard_LRS'
}
}
resource virtualNetwork 'Microsoft.Network/virtualNetworks@2022-11-01' = {
name: vnetName
location: resourceGroupLocation
properties: {
addressSpace: {
addressPrefixes: [
'10.0.0.0/16'
]
}
subnets: [
{
name: 'Subnet-1'
properties: {
addressPrefix: '10.0.0.0/24'
}
}
{
name: 'Subnet-2'
properties: {
addressPrefix: '10.0.1.0/24'
}
}
]
}
}
output storageAccountId string = storageAccount.id
“2022-09-01” is the API version.
Example: To create an appServicePlan and appServiceApp:
resource appServicePlan 'Microsoft.Web/serverFarms@2022-03-01' = {
name: 'toy-product-launch-plan'
location: 'eastus'
sku: {
name: 'F1'
}
}
resource appServiceApp 'Microsoft.Web/sites@2022-03-01' = {
name: 'toy-product-launch-1'
location: 'westus3'
properties: {
serverFarmId: appServicePlan.id
httpsOnly: true
}
}
To transpile a Bicep template to a corresponding JSON template using CLI commands:
bicep build main.bicep
The result is an ARM JSON file:
{
"$schema": "https://schema.management.azure.com/schemas/2019-04-01/deploymentTemplate.json#",
"contentVersion": "1.0.0.0",
"metadata": {
"_generator": {
"name": "bicep",
"version": "0.14.6.61914",
"templateHash": "1685474528138924530"
}
},
"parameters": {
"location": {
"type": "string",
"defaultValue": "[resourceGroup().location]"
},
"namePrefix": {
"type": "string",
"defaultValue": "storage"
}
},
"variables": {
"storageAccountName": "[format('{0}{1}', parameters('namePrefix'), uniqueString(resourceGroup().id))]",
"storageAccountSku": "Standard_RAGRS"
},
"resources": [
{
"type": "Microsoft.Storage/storageAccounts",
"apiVersion": "2023-06-01",
"name": "[format('stg{0}', uniqueString(resourceGroup().id))]",
"location": "[parameters('location')]",
"kind": "StorageV2",
"sku": {
"name": "[variables('storageAccountSku')]"
},
"properties": {
"accessTier": "Hot",
"supportsHttpsTrafficOnly": true
}
}
],
"outputs": {
"storageAccountId": {
"type": "string",
"value": "[resourceId('Microsoft.Storage/storageAccounts', format('stg{0}', uniqueString(resourceGroup().id)))]"
}
}
}
main.bicep
In the main.bicep file, defining resources under Microsoft.Resources/deploymentStacks makes them “managedResources” – managed by policies associated with that top-level stack.
See https://learn.microsoft.com/en-us/azure/templates/microsoft.resources/deployments?pivots=deployment-language-bicep
The actionOnUnmanage behavior property of a stack can apply to the entire collection of resources under the stack - across all scopes (management groups, subscriptions, and resource groups).
Indeed, this enables one command to manage all resources (across several scopes) as a single atomic unit. When the actionOnUnmanage property is set to Delete, all resources would be automatically deleted when the stack is deleted. That’s convenience!
Conversely, when actionOnUnmanage is set to Detach (the default), resources are disassociated from the deployment stack but not deleted. This has the effect of protecting resources from accidental deletion, and thus a key benefit of using deployment stacks. It provides guard rails.
IMPORTANT: Deployment stacks entered public preview on July 1, 2023.
For example, to create a deployment stack at the “sub” (subscription) scope with deny setting of “DenyDelete” and actionOnUnmanage of “Detach”:
az stack sub create \ --name "storageStack-DevEnv" \ --template-file "testStorageAccounts.bicep" \ --location "eastus" \ --deny-settings-mode "DenyDelete"
To verify:
az stack sub show --name "storageStack-DevEnv"
"actionOnUnmanage": {
"managementGroups": "detach",
"resourceGroups": "detach",
"resources": "detach"
}
PSRule Policy as Code
VIDEO: PSRule Policy as Code runs are defined in .github/workflows/bicept-psrule.yml:
name: Analyze
on:
push:
branches: [main, 'release/*']
pull_request:
branches: [main, 'release/*']
schedule:
- cron: '24 22 * * 0' # At 10:24 PM, on Sunday each week
workflow_dispatch:
permissions: {}
jobs:
oss:
name: Analyze with PSRule
runs-on: ubuntu-latest
if: github.repository != 'Azure/PSRule.Rules.Azure-quickstart'
permissions:
contents: read
security-events: write
steps:
- name: Checkout
uses: actions/checkout@v3
- name: Run PSRule analysis
uses: microsoft/ps-rule@main
uses: Microsoft/ps-rule@v2.0.0
with:
modules: PSRule.Rules.MSFT.OSS
prerelease: true
outputFormat: Sarif
outputPath: reports/ps-rule-results.sarif
- name: Upload results to security tab
uses: github/codeql-action/upload-sarif@v2
with:
sarif_file: reports/ps-rule-results.sarif
The “schedule: - cron:” lines can be removed so you don’t want runs recurring automatically.
At the Resource Group level
I’ve parameterized the CLI script:
export THIS_LOCATION="eastus" export THIS_RESC_GROUP="demoRg" export THIS_STACK_NAME="demoStack" az group create \ --name "$THIS_RESC_GROUP" \ --location $THIS_LOCATION az stack group create \ --name $THIS_STACK_NAME \ --resource-group "$THIS_RESC_GROUP" \ --template-file './main.bicep' \ --deny-settings-mode 'none' az stack group show \ --resource-group "$THIS_RESC_GROUP" \ --name $THIS_STACK_NAME
Because the deployment stack is a native Azure resource, all typical Azure Resource Manager (ARM) operations can be performed on the resource, including:
- Azure role-based access control (RBAC) assignments
- Security recommendations surfaced by Microsoft Defender for Cloud
- Azure Policy assignments
References:
- https://github.com/Azure/deployment-stacks
- https://learn.microsoft.com/en-us/azure/templates/microsoft.resources/deployments?pivots=deployment-language-bicep
- https://learn.microsoft.com/en-us/azure/azure-resource-manager/bicep/deployment-stacks?tabs=azure-cli
-
https://learn.microsoft.com/en-us/azure/azure-resource-manager/bicep/deployment-stacks?tabs=azure-powershell
-
BLOG and VIDEO: May 8, 2022 Streamline Your Deployment Process with Azure Bicep & Azure Functions by Andrew Connell using Bicep CLI version 0.6.1.
- BLOG and VIDEO: CI/CD for Azure Functions: Automating Deployment with Bicep and ARM May 8, 2022 by Andrew Connell
Microsoft Learn Sandbox
Playground
Alternately, transpile by copying and pasting into the Bicep Playground:
https://bicepdemo.z22.web.core.windows.net
Click the Sample Template button to see a list of sample Bicep and JSON files side-by-side.
Decompile
Click “Decompile” from the ARM JSON template to a Bicep.
-
View sample Bicep code:
https://github.com/Azure/bicep/tree/main/docs/examples
More examples: This contains Azure Resource Manager templates contributed by the community.
https://github.com/AzureIaCBook/book-templates and
https://github.com/PacktPublishing/Infrastructure-as-Code-with-Azure-Bicep is provided with Manning BOOK: “Azure Infrastructure as Code” by Eduard Keilholz, Erwin Staal, Henry Been https://learning.oreilly.com/library/view/azure-infrastructure-as/9781617299421/OEBPS/Text/04.htm#heading_id_5 -
Install in VSCode the Bicep extension: VIDEO
-
Install the Bicep CLI. VIDEO
Terraform for Azure
-
On a Mac, install using Homebrew instead of Download from HashiCorp website or using brew install terraform:
brew install tfenv tfenv install latest
AAD/Entra Connect
Entra ID Join
Azure Policy
Azure Role-Based Access Control (RBAC)
Entra ID Roles
Azure Policy
Resources:
1. VIDEO: Azure Policy for Azure Security Center
* Microsoft Learn: Configure Azure Policy 1hr 30min
* https://learn.microsoft.com/en-us/azure/governance/policy/overview provides the most detail
* VIDEO: Anatomy of Azure Policy by John Savill.
Using Azure Policy is free for Azure resources, but there’s a fee for Arc resources on-premises or in other clouds.
Popular governance actions enforced with Azure Policy include:
- Enforcing the consistent application of taxonomic tags
- Ensuring the team deploys Azure resources only to allowed regions
- Requiring resources to send diagnostic logs to a Log Analytics workspace
- Enforcing the use of encryption in transit and at rest
- Enforcing the use of approved Azure resource types while in TST
- Enforcing the use of approved VM images in production
Cost Control:
- Restrict the SKU’s of virtual machines allowed to be created
- Avoid using Azure regions where the cost of a resource is higher
- Restrict the usage of solutions from Azure Marketplace that can increase your costs
Security:
- Enforce SSL connection to Azure MySQL database
- Ensure authentication on Linux machines should require SSH keys
- Ensure Windows machines should meet requirements for Windows Firewall Properties
Monitoring:
- Activity logs should be retained for at least one year
- Log Analytics Agent should be enabled for listed virtual machines images
- An activity log alert should exist for specific Security operations
Backup:
- Make sure all your virtual machines have Azure Backup enabled
- Ensure that geo-redundant backup is enabled on Azure Database for MySQL or PostgreSQL
- Ensure that long-term geo-redundant backup is enabled on Azure SQL Database
Governance:
- Ensure the proper tag usage as well tag enforcement on resources
- Audit virtual machines with a pending reboot
- Manage your organizational-compliance requirements by specifying whether an SSL certificate lifetime action is triggered at a specific percentage of its lifetime or at a certain number of days prior to its expiration
Actions at scale:
- Deploy Azure Monitor agent to all your virtual machines
- Enable Azure Backup for virtual machines
- Ensure auditing is enabled to all your Azure SQL Database instances
- Ensure secure connections (HTTPS) to storage accounts
- Prevent inbound RDP from internet on your virtual machines
REMEMBER: Even if an individual has the Role access to perform an action, if the result is a non-compliant resource, Azure Policy still blocks the create or update.
-
 Get to the “Policy” blade in the Azure Portal.
Get to the “Policy” blade in the Azure Portal.https://portal.azure.com/#view/Microsoft_Azure_Policy/PolicyMenuBlade/~/Overview
-
Click the “Definitions” menu link on the left to see hundreds of pre-defined Policy definitions.
REMEMBER: Each Policy is assigned to an Azure Subscription.
-
Click “Definition type”. Individual Policies can optionally be grouped into “Initiatives”.
-
Click “Category”. The list is NOT SORTED! So I prepared this Google Sheet to sort them:
-
Click “Policy type”. The default is “Built-in”. Custom Policies can be created. There is also “Static”.
-
Click the “Assignments” menu link to see the “ASC Default” Initiative for your current Subscription Scope.
“ASC” is Azure Security Center, which consolidates security alerts from multiple sources.
-
Click on that Assignment to see 335+ Parameters listed along with metrics status.
Notice that you already have “Non-compliant policies” even though you yourself have not assigned any Policies to your Subscription.
Maximums: 500 Policy definitions per Scope.
“Exempt compliance state indicate resources covered by an exemption. VIDEO: Azure Policy Exemptions by John Savill.
-
Click on “Non-compliant resources” to see resources that do not conform to the policy rule in the policy definition.
Types of compliance: Customer, Microsoft, Shared. Regulatory.
Enforcement Effects are defined within the Policy Rule portion of the policy definition:
- Deny the resource change
- Log the change to the resource
- Alter the resource before the change
- Alter the resource after the change
- Deploy related compliant resources
- Block actions on resources
A JSON-defined object can, when triggered, correct resources violating policies with
COOL: deployIfNotExists or modify effects can be remediated automatically by a triggered remediation task.
-
Click “Change History. Click an entry to see a before/after copy of an ARM Template for your Subscription in the “Change details” blade.
If you had entered Entra to elevate the Global Administrator to the “User Access Admin” role, you would see it here.
-
View the JSON.
Maximum: 1GB in Policy definition body
Parameters can be defined in Policy definitions.
Notice some are “[Deprecated]”. The “Parameter value” of each shows its status.
-
Click “Compliance” at the top menu for metrics similar to
Notice the “Initiative” is “Not started” because it has not been assigned to any resources.
An Initiative is sometimes called a policySet.
Many Policies recommend installing Defender services (for additional charge).
-
Click “+ Initiative definition” to create a new Initiative.
PROTIP: It takes careful “Organizational Change Management” to impose Policies on busy developers. Busy developers rightly see it as an imposition (overreach) unless it’s introduced very carefully over a period of time. My team specializes in this. are often seen by developers as
- Microsoft offers DSC packages to install built-in Policy Packages.
Use Azure Resource Graph to run queries to get information about compliance details by assignments and resource types, list all noncompliant resources, summarize resource compliance by state, and more. https://learn.microsoft.com/en-us/azure/governance/policy/samples/resource-graph-samples
https://learn.microsoft.com/en-us/security/benchmark/azure/baselines/azure-policy-security-baseline
https://github.com/MicrosoftDocs/SecurityBenchmarks/blob/master/Azure%20Offer%20Security%20Baselines/3.0/azure-policy-azure-security-benchmark-v3-latest-security-baseline.xlsx
To find the right Azure Policy definitions for your Azure resources, see https://www.azadvertizer.net/index.html by Julian Hayward in Germany. AzAdvertizer tracks updates of Governance policies (BuiltIn, ALZ (Azure Landing Zone), AMBA (Azure Monitor Baseline Alerts), Community), including Preview and Deprecated policies. Provides the definition of each Policy.
at Azure Security Center has a VIDEO on Azure Policy for Azure Security Center.
Futures Roadmap
PROTIP: The minimum prior notification will Microsoft give before ending support for products governed by the Modern Lifecycle Policy is 12 months.
-
Azure Blog for Official announcements
-
azure.microsoft.com/updates in now timing out. It has filters for GA vs. futures.
-
Azure This Week by Lars Klint and GPS at ACloudGuru.com.
Product Features
“Public preview” means the feature is available for all Azure customers for beta testing.
GA (General Availability) means
VIDEO: https://azurecharts.com/status provides clickable “heatmap” status, timeline, a quiz, etc.
Videos
Microsoft Azure: The Big Picture 1h 50m Mar 10, 2016 by Matt Milner makes use of VS 2010, which is rather obsolete now.
- Install in VSCode Azure Resource Manager Tools for Template language support for Azure Resource Manager JSON files.
Live events to meet people
WARNING: The “Global Azure Bootcamp April 27, 2019” experience website global.azurebootcamp.net has converted to Vue and Google stuff.
Podcasts
-
Azure Friday with videos by Scott Hanselman
-
The Azure Podcast by Sujit D’Mello
-
Channel 9 for all things Microsoft.
-
Azure Tuesdays with Corey by Rick Claus
-
Azure Ninjas (Microsoft Global Black Belts)
azcopy in Windows
azcopy is a command-line utility designed for copying data to/from Microsoft Azure Blob, File, and Table storage, using simple commands designed for optimal performance. You can copy data between a file system and a storage account, or between storage accounts.
- Install azcopy on your local machine.
- Set Authorizations
- To download: “Storage Blob Data Reader”.
- To upload: “Storage Blob Data Contributor” & “Storage Blob Data Owner”.
- Gain access via Active Directory or Shared Access Signature (SAS):
azcopy login
- Enter the code (for example) A1B2C3D4 to authenticate.
- Upload blobs from the command line to Azure Blob storage.
Azure Import/Export Service
Azure Import/Export Service is used to transfer large amounts of data to and from Azure Blob storage and Azure Files by shipping disk drives to an Azure datacenter.
Download command-line tool WAImportExport.exe to prepare disk drives and copy data on Windows only.
Each order can be up to 5 SSD disk drives with 40TB total per order.
Delete Subscription, Directory, Tenant
az group delete --name $MY_RG
https://docs.microsoft.com/en-us/azure/cost-management-billing/manage/cancel-azure-subscription
https://docs.microsoft.com/en-us/azure/active-directory/enterprise-users/directory-delete-howto
Resources
https://olohmann.github.io/azure-hands-on-labs/labs/07_iac/iac.html
https://docs.microsoft.com/en-us/windows-server/identity/ad-fs/deployment/how-to-connect-fed-azure-adfs ADFS (Azure Directory Federated Services)
https://azurelessons.com/
http://www.frankysnotes.com/2019/05/how-to-make-your-deployment-successful.html
https://azurefabric.com/azure-monitor-for-paas-services-where-is-the-ai-and-how-do-i-arm-it/ blog https://azidentity.azurewebsites.net/archive
https://www.linkedin.com/events/introtoarm-biceptemplates7091472660878028800/about/ by Brian Gorman
“Get Started” videos by Eric Boyd responsiveX
Microsoft Preva Privacy Risk Management
https://www.microsoft.com/en-us/security/business/microsoft-purview https://learn.microsoft.com/en-us/purview/purview Microsoft Purview data protection and governance for “Unified Data Governance”
https://www.youtube.com/watch?v=m1VWSWlrJa8 https://www.aGuideToCloud.com
Trainer Tim Warner (at timw.info) has been, over the years, been updating his “Frankenstein” diagram that connects together as many Azure services as he can cram in:

https://www.youtube.com/watch?v=kmmuCapzX8I John Savill’s Azure Master Class v2 - Module 9 - Database & A.I.
https://www.youtube.com/watch?v=CzPeD7sR-ng Azure Active Directory - Tenant Basics for those that never knew
https://www.youtube.com/watch?v=Q1GogsFkX-s How Azure subscriptions and tenant are related and how to manage permissions at different levels Michael Lord Nov 22, 2019
- https://ea.azure.com (Azure enrollment under Enterprise Agreements)
https://www.youtube.com/watch?v=nHVqbtcUH_I Understanding Azure Subscriptions CloudStrategist 6.7K views 3 years ago
https://www.youtube.com/watch?v=-BD5rlMyLUY
BLAH: https://www.youtube.com/watch?v=IGTWEcTTWkQ Understanding Azure: Subscription, Tenant, Active Directory and Accounts by Frank Liu
https://www.youtube.com/watch?v=FAbqJqr93v8 Azure Tutorial - Tenants, Subscriptions & Resource Groups Explained Nerdio 49K views 4 years ago
https://www.youtube.com/watch?v=-BD5rlMyLUY&t=33s Understanding AZURE Tenants and Subscriptions Taste of Premier 46K views 4 years ago
https://www.youtube.com/watch?v=mVV_4O_QPI0 Azure Active Directory - Tenant, Subscription and Directory - हिंदी में Tech learning 141K views 3 years ago
https://www.youtube.com/watch?v=LMAC0IIYSJM How to setup your Azure Subscriptions the right way KnowOps 20K views 4 years ago
https://www.youtube.com/watch?v=MgTUYIiPn2g learn azure subscription types Paddy Maddy 11K views 3 years ago
End-to-End projects https://github.com/madebygps/projects/tree/main/az-104
- Onboard Automator (Manage Azure identities and governance)
- ShareSafely - File Share Web App (Implement and manage storage)
- VM Fleet Commander (Deploy and manage Azure compute resources)
- NetMaze Explorer (Implement and manage virtual networking)
- InsightScape (Monitor and back up Azure resources)
More about Azure
This is one of a series about Azure cloud:
- Azure cloud introduction
- Azure Cloud Onramp (Subscriptions, Portal GUI, CLI)
- RDP client to access servers
- Bash Windows using Microsoft’s WSL (Windows Subsystem for Linux)
- Microsoft PowerShell ecosystem
- Azure Cloud Powershell
- PowerShell DSC (Desired State Configuration)
- PowerShell Modules
- Azure Networking
- Azure Storage
- Azure Compute
- Azure cloud DevOps
- Dockerize apps
- Kubernetes container engine
- Hashicorp Vault and Consul for keeping secrets
- Hashicorp Terraform
- Ansible
- Microsoft AI in Azure cloud
- Azure Monitoring
- Azure KSQL (Kusto Query Language) for Azure Monitor, etc.
- Dynatrace cloud monitoring
- Cloud Performance testing/engineering
- Cloud JMeter


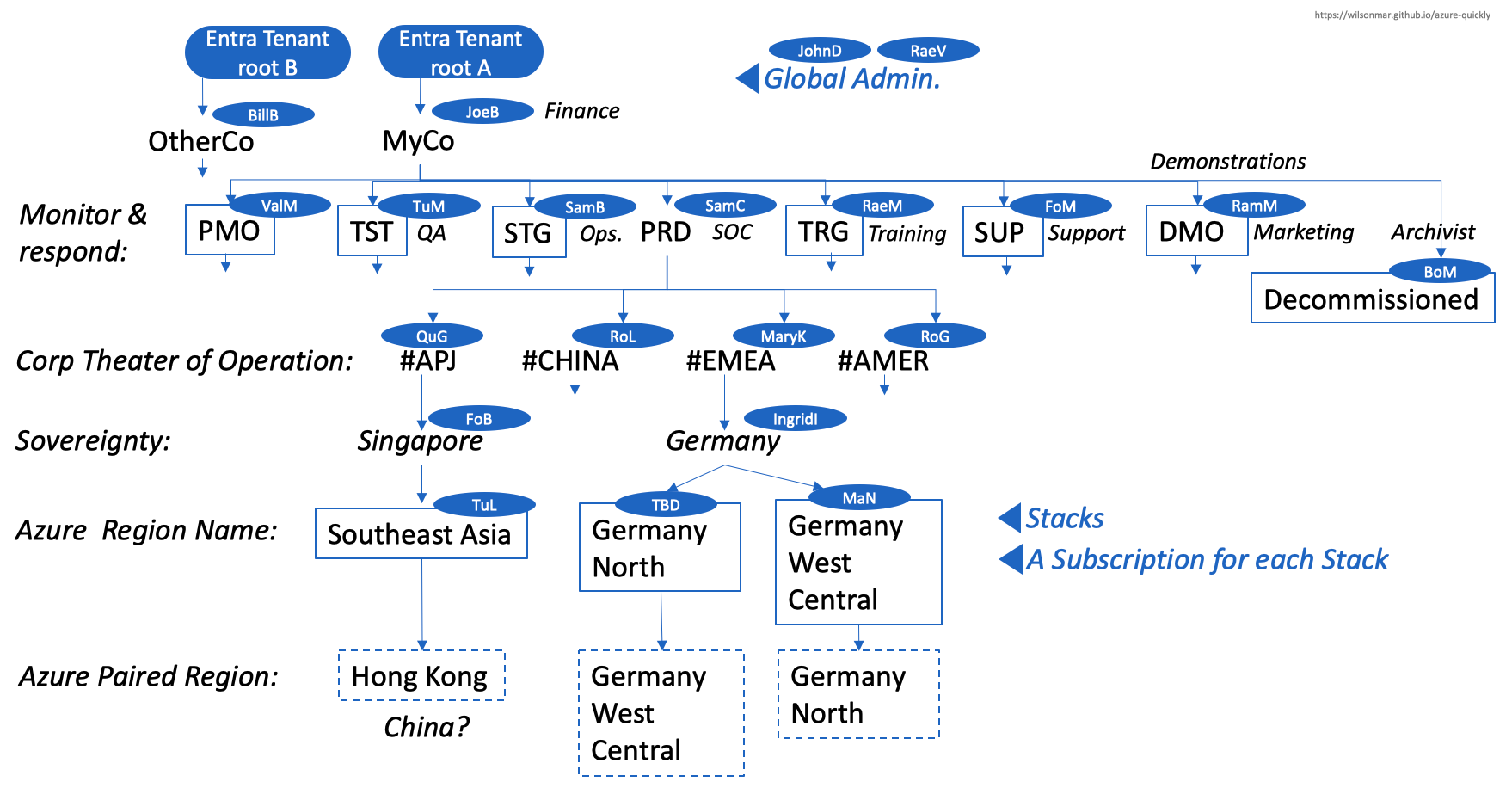

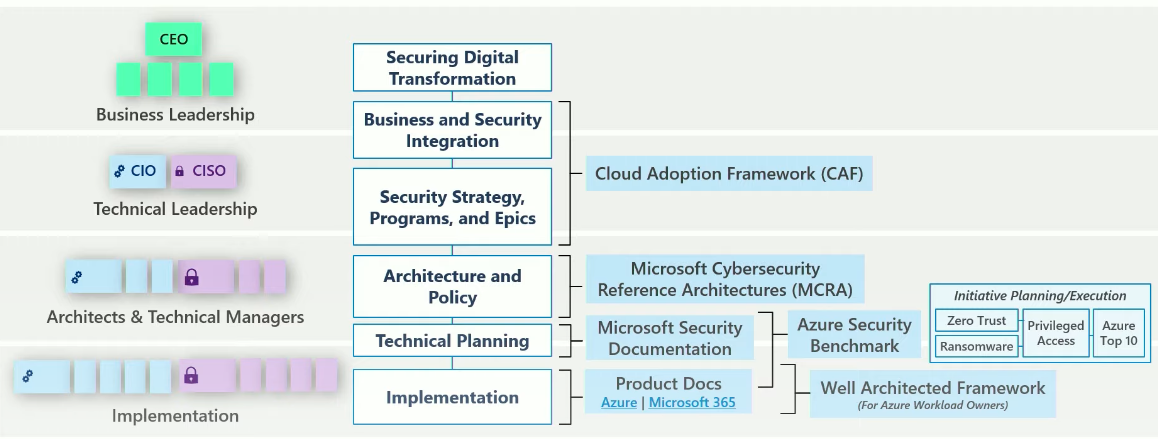
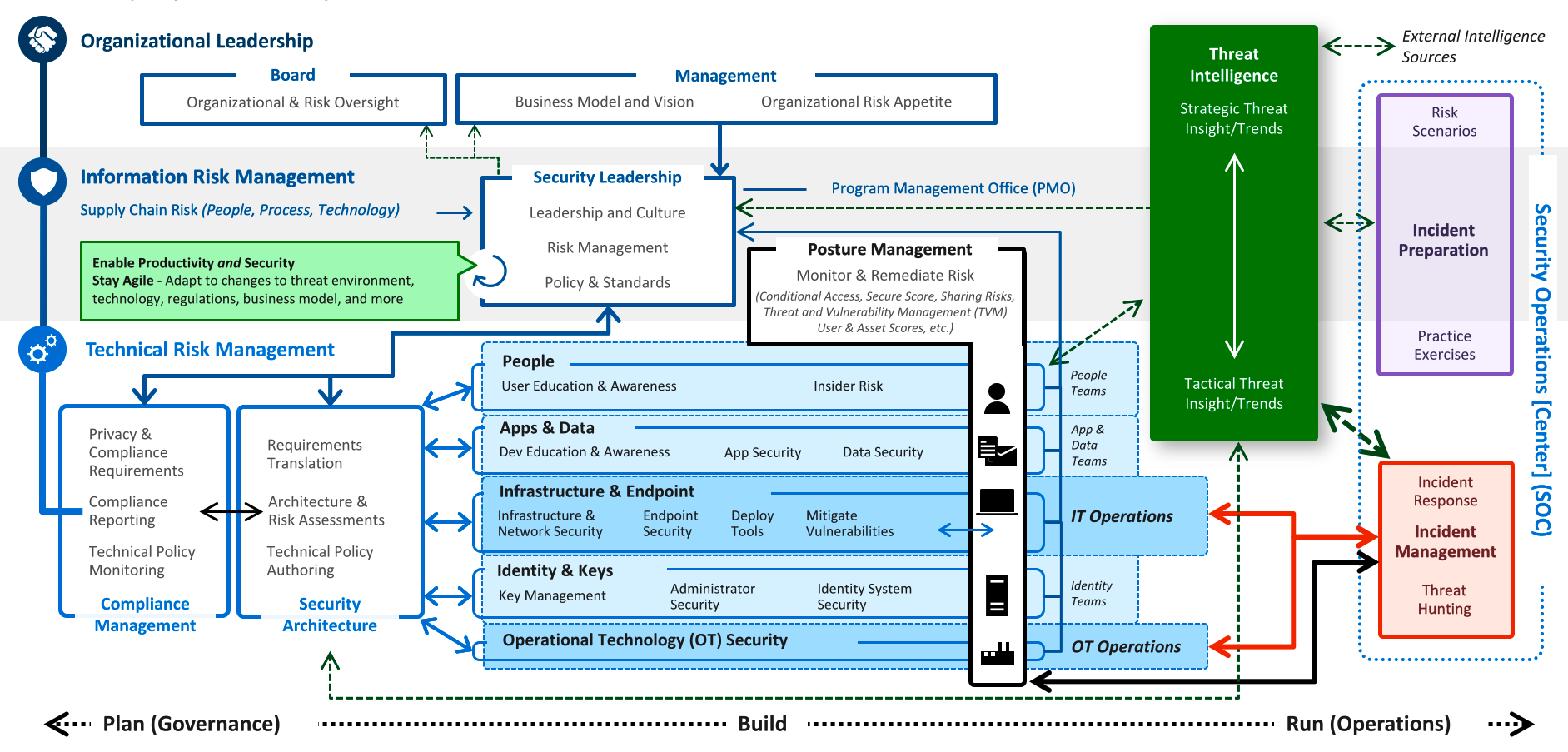
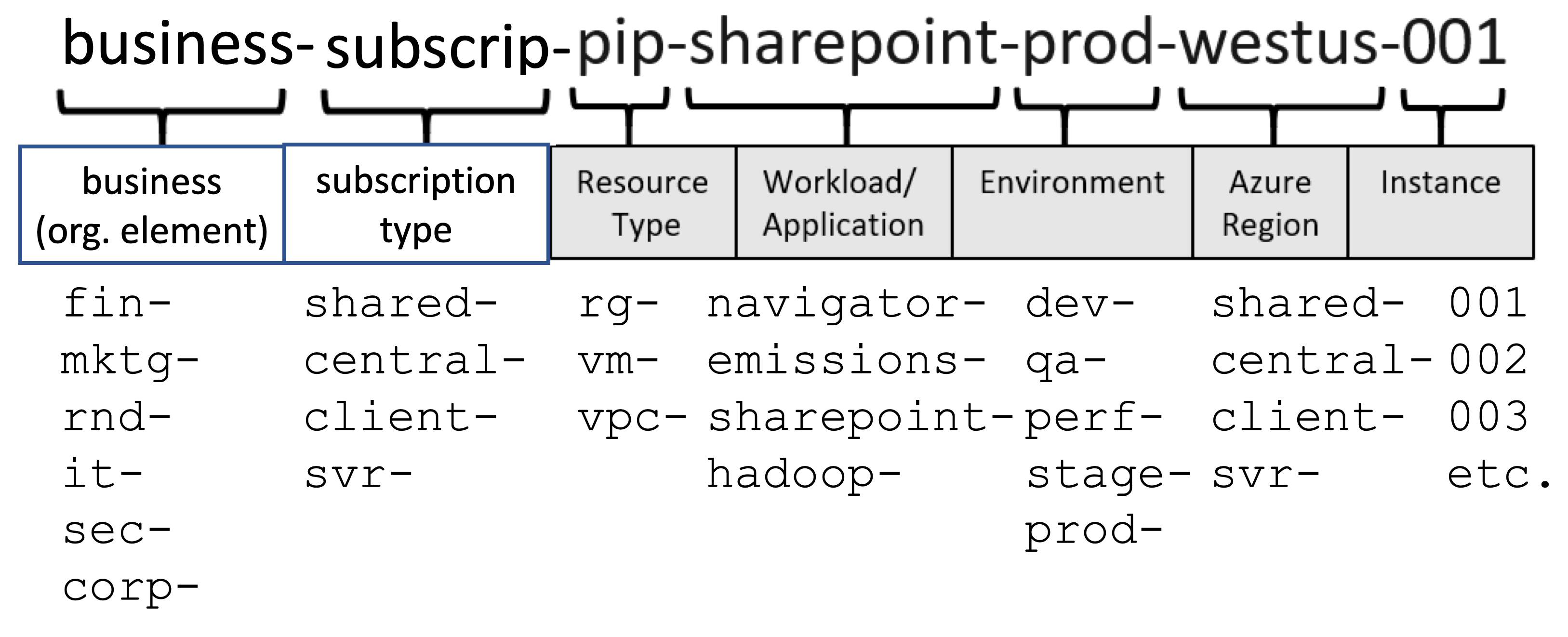
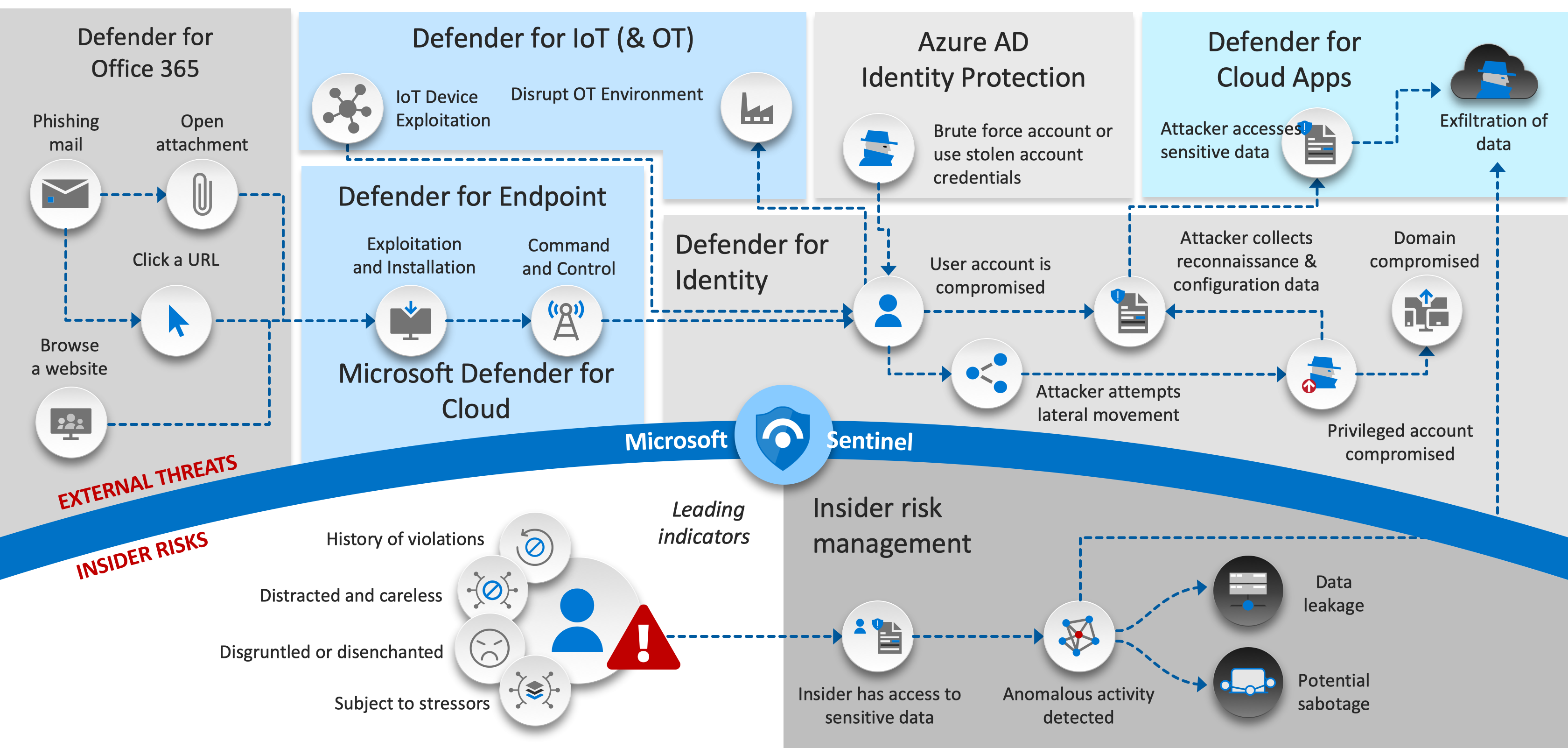
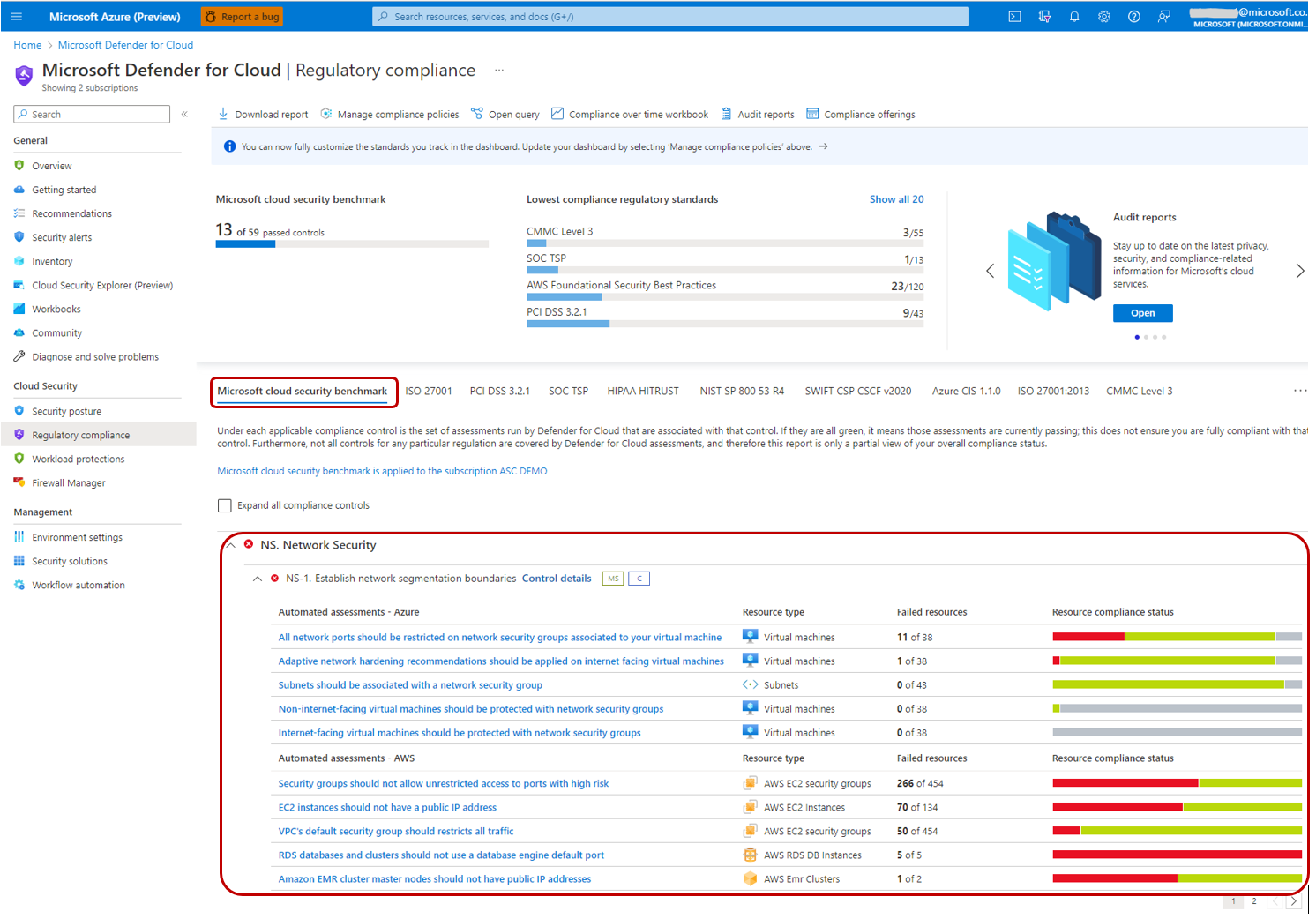
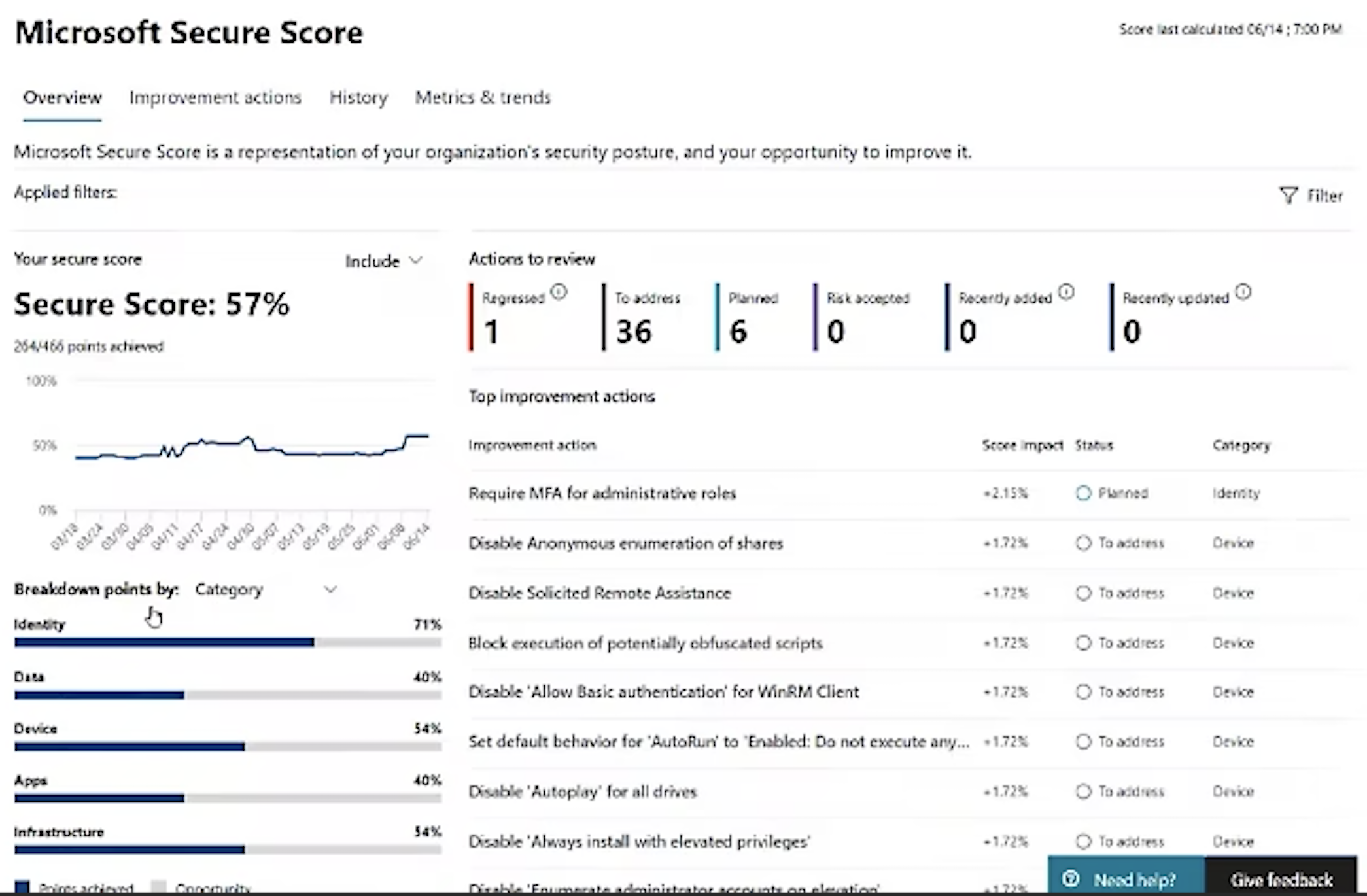

 https://build5nines.com/map-azure-regions/
https://build5nines.com/map-azure-regions/