Run the deliberately insecure Java app within Docker with a Contrast Security agent reporting issues and trends over time.
Overview
This is a hands-on introduction to WebGoat, a deliberately insecure Java 11 Spring-Boot application maintained by volunteers affiliated with OWASP (Open Web Application Security Project).
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
WebGoat is used instead of sample apps which contain only unintended vulnerabilities, such as Microsoft’s Music Store .NET app, which is not updated anymore
WebGoat is one of the subjects in the VIDEO: CSSLP (Certified Secure Software Lifecycle Professional) exam.
WebGoat source is open sourced at:
NOTE: WebGoat uses almost 200 Java and JavaScript libraries.
Code for both Goat apps are being actively maintained up to the current time.
Alternatives
Other intentionally vulnerable apps are
-
WebSpoit learning environment within Kali Linux by Omar Santos (ohmrXr on redteamvillage.io/discord) https://github.com/The-Art-of-Hacking/h4cker (https://h4cker.org/learning-path)
Medium) proxmox.com/en/ virtual environments
Tutorials within WebGoat

The WebGoat server presents a list of common vulnerabilities as classified by OWASP Top 10. Note the WebGoat menu is missing (A6) Security Misconfiguration and (A10) Insufficient Logging.
For each vulnerability, it provides coding tutorials along with a UI to initiatie penetration attacks on itself. For example, to prove that it can use an Insecure Deserialization vulnerability to take over the machine running, it opens that machine’s calculator app (which a well-behaved app would not be able to do).
The goat apps are used to train and benchmark appsec scanner tools such as Fortify, Contrast Assess/Protect, etc.
CAUTION: While running this program your machine will be extremely vulnerable to attack. You should disconnect from the Internet while using this program.
Get WebWolf GUI from Docker Hub
There is an all-in-one WebGoat container on Docker Hub, with WebGoat and WebWolf running inside:
docker run -p 8080:8080 -p 9090:9090 -e TZ=Europe/Amsterdam webgoat/goatandwolf
NOTE: The lead contributor (nbaars), Googler Nanne Baars, lives in the Netherlands (where Amsterdam is the largest city).
The image contains a JRE.
HSQLDB server 2.5.0 is online on port 9001.
WebGoat’s default configuration binds to localhost to minimize the exposure.
-
Open browser for:
- First time on the WebGoat GUI, click “Register as new user”.
-
Check “Agree”.
- On the landing page, notice “your very own scapegoat”.
OWASP Benchmark App
The OWASP benchmark (at https://owasp.org/www-project-benchmark) is a sample Java application containing 1,415 vulnerabilities in 11 categories:
Injection vulnerabilities:
- Command Injection (cmdi)
- SQL Injection (sqli)
- LDAP Injection (Idapi)
-
XPATH Injection (xpathi)
- Cross Site Scripting - “Injection of javascript code” (xss)
- Path Traversal - “Injection of file paths” (pathtraver)
Weak Algorithms:
- Weak Cryptography (crypto)
- Weak Randomness (hash)
- Weak Randomization (weakrand)
Other:
- Secure Cookie Flag (securecookie)
- Trust Boundary Violation (trustbound)
Prioritize by Blast Radius
Vulnerability scanner vendor Snyck’s State of Open Source Security in DevSecOps Pipelines” 2020 report revealed this scatterplot of the number of vulnerabilities (CVEs) on the vertical scale compared against the number of projects impacted by them on the horizontal scale.
VIDEO:
Alyssa “There is nothing in the upper-right quadrant, and that was shocking. …we can have hundreds and hundreds of cross-site scripting vulnerabilities reported in packages, but the number of projects that those packages impact is fairly small. On the flip side, you have deserialization and prototype pollution which are more complex … and later to the game. For prototype pollution there were 3 vulnerability reports but the reason they had such massive impact is they were found in open source packages* that are widely used (lodash CVE-2019-10744*, jQuery CVE-2019–11358).”
VIDEO
“Malicious packages are more targeted.”
Code samples
Counterparts written in other languages:
Java
JavaScript
Ruby on Rails
C#/.Net/.Net Core
Drupal/PHP
Go
Terraform
Python
PL/SQL
Swift/Obj C
Kotlin/Java(Android)
Attack tools
There are several tools available to conduct penetration testing against the WebGoat app.
SecToolMarket.com ranks web application scanners’ pricing and features, as described in sectooladdict.blogspot.com, last updated Sep 18, 2016 by Shay Chen (@sectooladdict). http://sectooladdict.blogspot.com/2017/11/wavsep-2017-evaluating-dast-against.html
ShiftLeft.io
In this pdf, ShiftLeft.io notes that false positives found in just 3 snippets as due to “overtainting” collections and disabled branches of switch statements that are unreachable, which is a rare edge case.
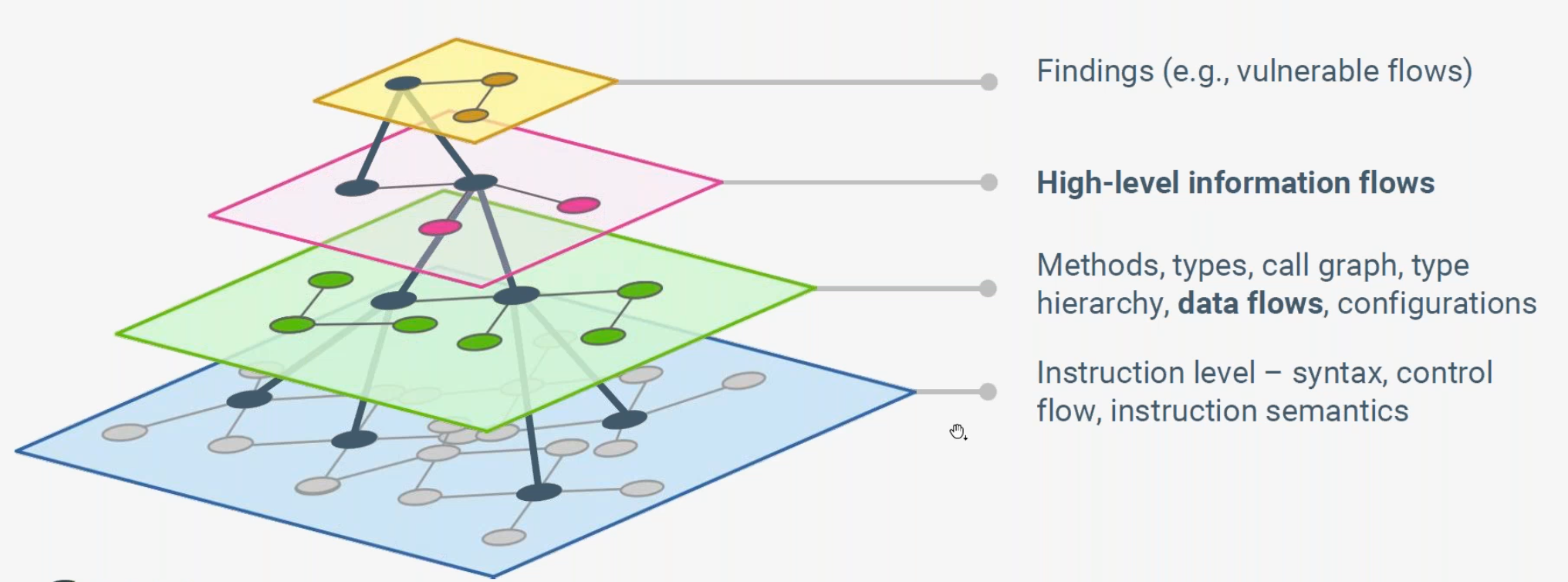
ShiftLeft claims that the accuracy of its “NG SAST” (Next Generation) utility is greater than traditional code analysis tools. NG SAST queries binaries and source code modeled by Code Property Graph (CPG) which combines many graphs. It combines graphs from the compiler (e.g., the abstract syntax tree, the program dependence graph, the control flow graph, etc.) to generate a single graph that contains all possible routes from all sources to all sinks, including all security transforms and sanitization steps.
The table above* compares how ShiftLeft augments existing techniques to identify vulnerabilities:
- Abstract Syntax Tree (AST) parsed from the stream of tokens scanned from source code
- Control Flow Graph (CFG) transformed from AST
- Program Dependency Graph (PDG) Data Flow Analysis operating on CFG
The combined Code Property Graph (CPG) provides a representation of app code under test (in a graph database) that is multifacted enough to deal with the complex combinations of program properties which can make it vulnerable.
CPG enables NG SAST to accurately determine when routes are actually vulnerable to dirty inputs vs. when the route is protected by sanitization.IEEE whitepaper “Modelling & Discovering Vulnerabilities with Code Property Graphs” by Fabian Yamaguchi.
ShiftLeft Security achieves less false positives in static SAST and less false negatives in dynamic DAST because it has a data-flow tracker which “is interprocedural, flow-sensitive, context-sensitive, field-sensitive, and operates on an intermediate code representation. The engine performs on-the-flypoints-to analysis to resolve call sites and is able to benefit from the results of constant propagation, control flow graph pruning, and framework analysis passes.”
Many CWE are for C/C++ code. Joern is a vulnerability research platform for robust analysis of C/C++ code.*
Back reference to underlying code enables ShiftLeft running in production to finely report on data inputs triggers and output destinations (variable names from code):
NOTE: The above is no longer sold.
Contrast
Contrast Security can determine whether attacks are occurring on WebGoat (the “Protect” portion of its offering). It also can assess whether the app code is vulnerable to attacks.
You can run WebGoat from DockerHub with the Contrast Security agent added by quickly triple-clicking the command below and pasting it on your macOS or Linux server Terminal:
bash -c "$(curl -fsSL https://raw.githubusercontent.com/wilsonmar/DevSecOps/master/bash/sample.sh)" -W -k -a -o -s -v -K -D -M
The script installs all that is needed, including Docker Desktop. It downloads docker-compose.yml from:
Contrast Security is what Gartner calls “RASP (Runtime Application Self-Protection)”. Fashionable in the era of “self-protecting” software (philosophy of “Zero Trust”).*
The Contrast agent intercepts all calls from the app, and analyzes the stream of calls to make sure they’re secure, and validates data requests directly inside the app. The continuous interception essentially provides a chance to “innoculate” apps from vulnerabilities such as struts2. Without it, apps are “sitting ducks” while time is taken to add CVEs to scanners, then more time to replace, retest app code.
At time of writing, the image contains OpenJDK 8 (not 11). The agent analyzes Java byte code. So it works with Scala as well as Java code. And it works with both custom code and libraries. It protects both web and non-web apps. From the inside out.
The agent emits issues found to a an on-prem. or SaaS collector by Contrast Security.
The Contrast server can then send alerts to Slack.
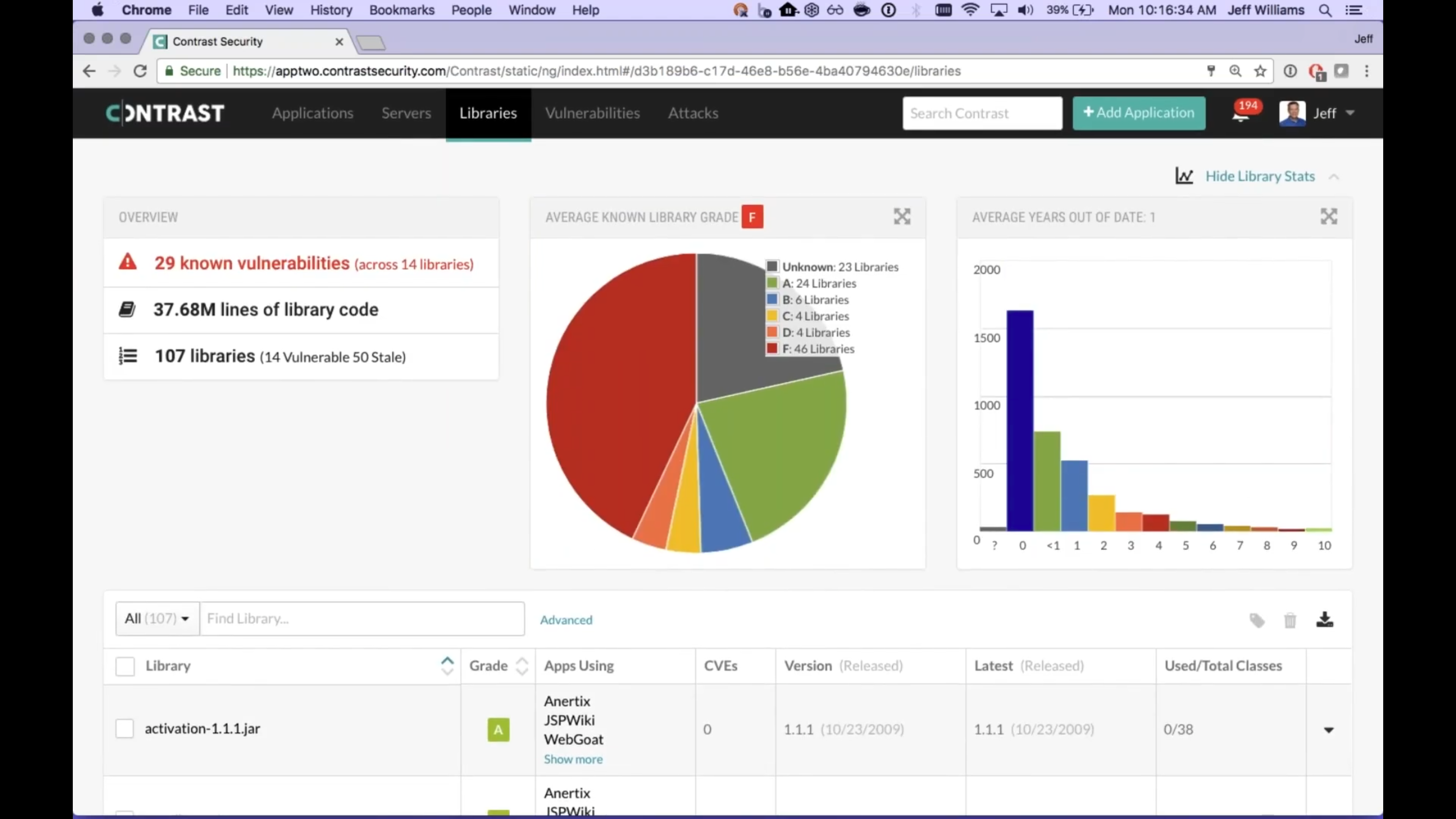
The Contrast dashboard visualizes the count of Vulnerabilities and Attacks seen over a period of time.
The Contrast Policy Management GUI enables specification of Protect Rules specific to an environment: Dev, or QA, or Prod.
The agent calculates the number of logical paths through the application code. So it knows when a library loaded by the app is not even used. And it provides context not understood by external blocking-mode WAF. Contrast enables database queries fully formed (not just the way it looks at the firewall).
The down side of this approach is that business process (end-to-end) test automation scripts are needed to exercise the app fully. So scripts written for running by WebInspect, Burp Suite, and other Dynamic (DAST) pentration testing tools are still useful.
-s among shell script parameters specifies that the script read secrets from the default file secrets.env on your $HOME user folder. But before running the script, populate values for variables after you get a trial account at Contrast Security.com:
CONTRAST__API__URL="?" CONTRAST__API__API_KEY="?" CONTRAST__API__SERVICE_KEY="?" CONTRAST__API__USER_NAME="?" CONTRAST__APPLICATION__NAME="?"
-o opens the web page to show the WebGoat GUI.
The port (8080) is hard-coded in variable APP1_PORT in the sample.sh script.
Videos:
- Contrast Protect Demo Jun 9, 2020 [9:48] by Jeff Williams, Contrast CTO
- Contrast IDE Plugins for VSCode, Eclipse, IntelliJ
- Contrast Security Demo Feb 20, 2019 [59:41]
Rapid7
SonarQube/SonarSource
FBwFindSecBugs
https://find-sec-bugs.github.io is the SpotBugs plugin for security audits of Java web applications. It claims to detect 135 different vulnerability types with over 816 unique API signatures.
PMD
https://pmd.github.io/latest/
https://en.wikipedia.org/wiki/PMD_(software)
DAST
There are several:
ZAP
In General > HTTP Basics page, it mentions installing and running the Zed Attack Proxy (ZAP) the latest using (on a Mac):
brew install --cask owasp-zap
Burp Suite
Burp Suite from https://portswigger.net/burp has a Community Edition.
Installing Burp Suite And WebGoat [10:01, turn off volume] on Windows.
Dependency Check Lab
John Marx has 1 hour hands-on video course about how to run the OWASP Dependency Check Lab (run-depchedk.sh) as example of a SAST (Static Application Security Test) for both build-time and run-time use against the webgoat.jar file from the Linux command line (after get-webgoat.sh).
The Dependency Check is run from a Docker Container containing an Apache Web Server. The run outputs HTML reports. It is reviewed and methods for use of these reports by production monitoring applications.
- Run the get-webgoat.sh shell script
- Run the run-depcheck.sh shell script
- Copy the HTML reports produced to the Apache Web Server root Directory
- Use the Browser to view the Dependency Check Reports which links to the National Vulnerabilities Database at https://nvd.nist.gov.
$ ls -l
Once you have verified that the instance is fully operational, use the get-webgoat.sh shell script to pull the webgoat .jar file from github.com
$ sh get-webgoat.sh
Once the .jar file is downloaded to the cloud_user home directory, run the shell script that uses docker to pull the OWASP Dependency Check program from Docker Hub and execute it.
$ sudo sh run-depcheck.sh
*Note: You will need the cloud_user password to run as a sudo user.
After the Dependency Check program has completed, you can use an ls command to view the reports created.
$ ls -l owreport/*
Once created, use the copy.sh script to copy the .html reports to the apache web server root.
$ sudo sh copy.sh
After the files have been copied to the apach root, check that they are there with an ls command.
$ ls -l /var/www/html
Now view the reports from your browser usiing the following URL addresses:
HTTP://[Public IP Address]/dependency-check-report.html
and…
HTTP://[Public IP Address]/dependency-check-vulnerability.html
YouTube Videos
krypt0mux of https://github.com/ethicalhackingplayground
https://www.facebook.com/EthicalHackingPlayground/
OWASP Webgoat 8 : Setting up the environment Jan 30, 2019 [5:14]
-
Identify the latest version:
-
Download
wget https://github.com/WebGoat/WebGoat/releases/download/v8.0.0.M23/webgoat-server-8.0.0.M23.jar
-
Within Docker, WebGoat is started by:
java -jar webgoat-server-8.0.0.M23.jar [--server.port=8080] [--server.address=localhost]
OWASP Webgoat 8 : SQL Injection Attack / Mitigations Jan 31, 2019 [11:13]
-
OWASP Webgoat 8 : XXE (XML External Entity Injection) Feb 1, 2019 [9:53]</a>
-
OWASP Webgoat 8 : XSS (Cross-Site-Scripting) Feb 19, 2019 [20:25]
Podcasts
https://soundcloud.com/owasp-podcast/2016-appsec-usa-an-update-on-the-webgoat-project 2016 AppSec USA - An Update on the WebGoat Project Bruce Mayhew, Nanne Baars and Jason White,
WebWolf
http://127.0.0.1:8080/WebGoat/start.mvc#lesson/WebWolfIntroduction.lesson
-
Open another browser for:
http://127.0.0.1:9090/WebWolf
-
Register as new user.
CWE
Cross-Site Scripting (XSS) Web Attack (Demo for AppSec) Fortify Unplugged 1 year ago
More on DevOps
This is one of a series on DevOps:
- DevOps_2.0
- ci-cd (Continuous Integration and Continuous Delivery)
- User Stories for DevOps
- Git and GitHub vs File Archival
- Git Commands and Statuses
- Git Commit, Tag, Push
- Git Utilities
- Data Security GitHub
- GitHub API
- Choices for DevOps Technologies
- Pulumi Infrastructure as Code (IaC)
- Java DevOps Workflow
- AWS DevOps (CodeCommit, CodePipeline, CodeDeploy)
- AWS server deployment options
- Cloud services comparisons (across vendors)
- Cloud regions (across vendors)
- Azure Cloud Onramp (Subscriptions, Portal GUI, CLI)
- Azure Certifications
- Azure Cloud Powershell
- Bash Windows using Microsoft’s WSL (Windows Subsystem for Linux)
- Azure Networking
- Azure Storage
- Azure Compute
- Digital Ocean
- Packer automation to build Vagrant images
- Terraform multi-cloud provisioning automation
-
Hashicorp Vault and Consul to generate and hold secrets
- Powershell Ecosystem
- Powershell on MacOS
- Jenkins Server Setup
- Jenkins Plug-ins
- Jenkins Freestyle jobs
- Docker (Glossary, Ecosystem, Certification)
- Make Makefile for Docker
- Docker Setup and run Bash shell script
- Bash coding
- Docker Setup
- Dockerize apps
- Ansible
- Kubernetes Operators
- Threat Modeling
- API Management Microsoft
- Scenarios for load
- Chaos Engineering
More on Security
This is one of a series on Security in DevSecOps:
- Security actions for teamwork and SLSA
- Code Signing on macOS
- Git Signing
- GitHub Data Security
- Azure Security-focus Cloud Onramp
- AWS Onboarding
- AWS Security (certification exam)
- AWS IAM (Identity and Access Management)
- SIEM (Security Information and Event Management)
- Intrusion Detection Systems (Goolge/Palo Alto)
- SOC2
- FedRAMP
-
CAIQ (Consensus Assessment Initiative Questionnaire) by cloud vendors
- AKeyless cloud vault
- Hashicorp Vault
- Hashicorp Terraform
- SonarQube
- WebGoat known insecure PHP app and vulnerability scanners
- Security certifications
- Quantum Supremecy can break encryption in minutes
- Pen Testing
- Threat Modeling
- WebGoat (deliberately insecure Java app)