How to get people to use products and processes that yield faster competitive speed AND improved Security Posture throughout a secure SDLC
Overview
- Do you have it covered?
- The Major brands
- Synopsys’s range
- A Mature Approach to Scanning
- BUILD: What to look for:
- What are Scanners looking for?
- DAST
- IAST
- RASP
- TL;DR: What it takes
- Where is the creativity?
- Empathetic, specific, and kind feedback?
- DevSecOps for SAP
- Professional certifications
- References
- More about DevOps
“DevSecOps is a set of software development practices that combines software development (Dev), security (Sec), and information technology operations (Ops) to secure the outcome and shorten the development lifecycle.”
Do you have it covered?
The diagram above identifies 14 processes (with a focus on automation and integration) to achieve a stronger secure posture across the various “pillars” of the software development lifecycle (SDLC): Develop, Build, Test, Release & Deploy, and Runtime.
What is the adoption completion percentage for each process/tool at your organization?
| # | Pillar | % | Process |
|---|---|---|---|
| 1. | PLAN: | __% | Threat Modeling |
| 2. | DEVELOP: | __% | Secure Coding (secrets in source code, OWASP Top 10, etc.) |
| 3. | DEVELOP: | __% | Security as Code (OPA processing Rego policies) |
| 4. | BUILD: | __% | SAST within CI/CD Jenkins & SonarQube) pipelines |
| 5. | TEST: | __% | DAST (and IAST) of each file type |
| 6. | TEST: | __% | (Network and app) Penetration Testing |
| 7. | RELEASE: | __% | Digital Signing (generate Hashes to identify changes) |
| 8. | DELIVER: | __% | Secure Transfer of (encrypted) data |
| 9. | DEPLOY: | __% | Security Configuration (IaC by declarative Terraform, declarative Pulumi) |
| 10. | DEPLOY: | __% | Security Scan - SBOM (Sofware Bill of Materials) for SCA (Sofware Component Analysis) |
| 11. | OPERATE: | __% | Security Patching NIST SP 800-40 SCA (Software Composition Analysis), Configuration Management |
| 12. | OPERATE: | __% | Security Audit (such as SOC2/ISO 27xxx) reference Run-time App Security Protection (RASP) to monitor and block production traffic. |
| 13. | MONITOR: | __% | Security Monitoring (and forwarding to central SIEM/SOAR system for alerting) NIST SP 800-92 |
| 14. | FEEDBACK: | __% | Security Trend Analytics Analysis; Bug Bounty programs |
The “%” column contains the current Percentage of Completion, within a trend line over time.
Who does what?
The Major brands
Gartner lumps the various activities together into their 2023 Gartner’s Magic Quadrant for Application Security Testing:
Synopsys’s range
Synopsys [on LinkedIn] operates in two seemingly different markets: EDA (Electronic Design Automation) used to build SoC (Systems on a Chip), and “Software Integrity”.
Synopsys achieved its upper-right leader position through corporate acquisitions, which assembled a full set of tools to enhance security at each step in a secure software development lifecycle:
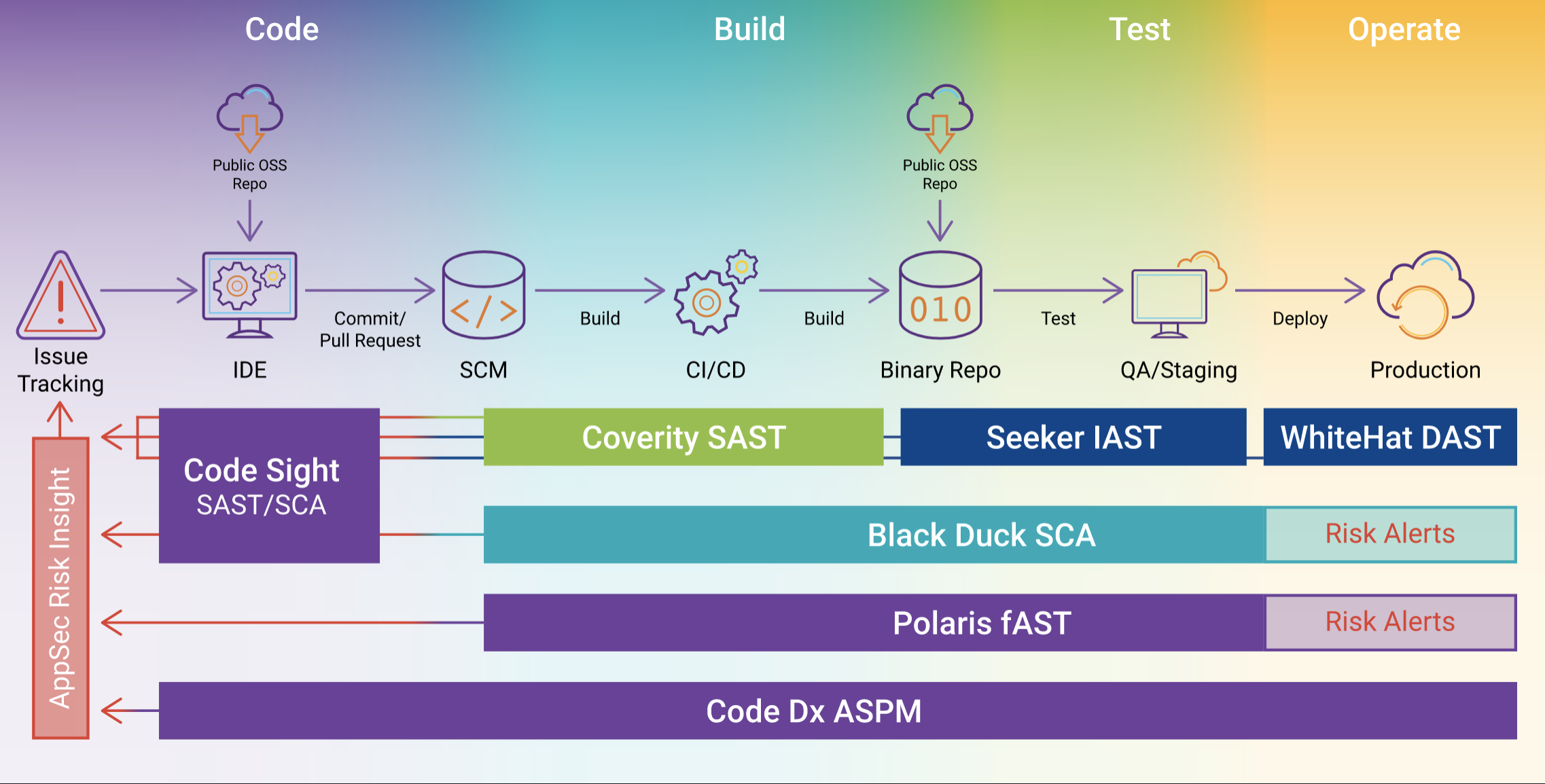
A Mature Approach to Scanning
Gartner is concerned about complex UI to what is sold as “all-in-one” but in reality, what can be a “patchwork” of products combined from different teams and thus work differently from each other.
However, Synopsys users have a single support organization versus needing to coordinate among various vendors on their own.
Synopsys has six products that span the same middle stages of the SDLC:
- Coverity SAST (Static Application Security Testing) looks at code (as stored statically in GitHub) [review]
- WhiteHat DAST (Dynamic Application Security Testing) looks at running code
- Seeker IAST (Interactive Application Security Testing) looks at agents running code dynamically [review]
- Black Duck SCA (Software Composition Analysis) identifies open source packages which have been flagged with vulnerabilities in the US National Vulnerability Database (NVD).
Synopsys combined separate tools into its Polaris fAST (Application Security Testing) offering – a cloud-based web/SaaS based on Synopsys Coverity® SAST, which includes services:
- Onboarding and adoption services, which help teams bring new applications and team members onto the platform quickly
- Triage services to help tune and remove noise from scan results
-
Troubleshooting services that provide automatic monitoring and fixing of interrupted scans
- Code Dx ASPM
- Defensics (formerly Codenomicon)
- Code Sight has a plugin that searches for vulnerabilities in dependencies used, so that they can be fixed while developers are working with them in the JetBrains IDE.
Other offerings:
-
OpenText purchased Fortify and other software quality tools in its acquisition of Micro Focus on January 2023. Micros Focus acquired those products from HP, who acquired them from Mercury Interactive. Fortify is the earliest available enterprise software scanners.
BUILD: What to look for:
-
Exposure of secrets in source code (such as passwords, API keys, etc.) and in configuration files (such as database connection strings, etc.)
-
Use of deprecated libraries (such as jQuery, etc.)
-
Use of vulnerable libraries (such as OpenSSL, etc.)
-
Use of vulnerable versions of libraries (such as OpenSSL, etc.)
-
Use of vulnerable versions of frameworks (such as Spring, etc.)
-
Use of vulnerable versions of operating systems (such as Windows, Linux, etc.)
-
Use of vulnerable versions of containers (such as Docker, Kubernetes, etc.)
-
Use of vulnerable versions of cloud services (such as AWS, Azure, etc.)
-
Use of vulnerable versions of databases (such as MySQL, Oracle, etc.)
-
Use of vulnerable versions of programming languages (such as Java, Python, etc.)
-
Use of vulnerable versions of compilers (such as GCC, etc.)
-
Use of vulnerable versions of build tools (such as Maven, Gradle, etc.)
-
Use of vulnerable versions of web servers (such as Apache, Nginx, etc.)
-
Use of vulnerable versions of application servers (such as Tomcat, etc.)
-
See if password is among the 1,000 most common passwords (dictionary attack)
-
See if login page detects a brute force attack (by trying all combinations of characters)
PostgreSQL has a pg_hba.conf file that can be configured to limit the number of login attempts.
-
Monitor logs for attack signatures (such as SQL injection, etc.)
What are Scanners looking for?
See my OWASP Top 10 items (with videos)
API Top 20
CWE Top 25
PCI DSS
MISRA®
CERT C/C++, CERT Java, CERT Python?
DISA STIG,
ISO 26262
ISO/IEC TS 17961
AUTOSAR®
DAST
DAST (Dynamic App Security Testing) analyzes how the program binary runs, dynamically. So source code is not needed. So it can be used by hackers. Tool vendors:
- White Hat
- OWASP ZAP proxy
- Qualys
- Veracode
- Arachni web application security scanner framework
https://juice-shop.herokuapp.com
IAST
IAST (Interactive App Security Testing) instruments software after installing an agent. Runs based on access to code, HTTP traffic, library, back-end connections.
- Synopsys
- Checkmarx
- Acunetix
RASP
RASP (Run-time App Security Protection) combines DAST and IAST. It can be configured to block or monitor traffic.
- Arxan
- Imperva
- Wallarm
TL;DR: What it takes
Here are the various tools and processes a fully mature secure-minded organization would adopt:
-
The ultimate objective is for secure and efficient coding techniques to be applied while code is created rather than having security “inspected into” products.
PROTIP: Professional-level skill cannot be obtained alone but requires mentoring and sharing of techiques from several others as part of life-long apprenticeships free of competition.
Scanners are good at finding “low hanging fruit” (obvious ones that are easy to identify), but commonly fail to find many false negatives in custom code.
To “nip bad quality code in the bud”, developers can invoke static code scanners on their local machine before committing their code to the team gauntlet.
The number of “false positives” are a key metric of a vendor’s effectiveness because time is needed to investigate each one, which can be frustrating.
https://ustelecom.org/research/2023-cybersecurity-culture-report/
-
The explosion of code generation “co-pilots” since 2022 will inevitably change the way programmers work.
Code generated by either manual or automated means are still subject to defects (functional and security).
So masterful “Prompt Engineering” from training of both computer models and human users is necessary – to recognize when requirements are not being satisfied,
Ongoing audits are needed to identify wayward models to identify different aspects of base data and how they impact algorithms.
-
PROTIP: Creating a culture of zealousness at refining and adopting security requires #blameless psychological safety.
It’s been said that DevOps is about culture. That also applies even more to DevSecOps.
An inclusive and friendly culture would have issues shared among employees, which reduces effort of each worker discovering the same issues on their own.
Like firemen practicing drills, developers can practice recognizing and fixing sample known-bad coding containing OWASP Top 10, API Top 20, etc.
-
Inclusion of security considerations within the IDE (Integrated Development Environment), such as coding CoPilot AI code generators (using GPT, etc.)
Security alerts within the IDE provides a safe (individualized) way to reveal criticisms without public shaming.
- PROTIP: My notes on GitHub and Microsoft CoPilot
- Black Duck CoPilot,
- Code Sight,
- Microsoft’s Visual Studio Code add-on
-
Priorities of what is coded is driven using an Issues Tracker that balances time on various objectives.
Synopsys AppSec Risk Insight. Atlassian Jira, ServiceNow, etc.
PROTIP: Transparency about defects and other debt is an indicator of organizational maturity, not a driver of it.
-
Provide advanced training and automation to manage complex code as a team SCM (Source Code Management) using a common repository
- write commit messages in GitHub (GitLab) to make troubleshooting easier
- reconcile conflicts in code from different times and locations and people
- use a central vault to store and retrieve secret values (rather than plain text on laptops waiting to be stolen)
PROTIP: Common and disciplined application of coding standards requires a social contract as well as a technical one. The book High Tech, High Touch popularized the concept (as I understand it) that more real personal physical attention is needed with heightened technology use.
The new darling in 2023 is Graphine.dev which enables faster collaboration among developers through enabling smaller “stackable” changes in code. VIDEO The company brings together the founders of GitHub, Docker, and Netlify and is backed by Andreessen Horowitz, Sequoia Capital, and Kleiner Perkins.
-
Build tools (Maven, Gradle, Scala Build Tool, NuGet, etc.) run within CI/CD pipelines (Jenkins, Travis CI, Circle CI, AppVeyor, GitHub Actions, etc.)
https://www.synopsys.com/software-integrity/integrations.html
-
Code linters and scanners (for each type of file) in CI/CD that stops a branch from being deployed if that branch doesn’t meet all the rules.
- SonarQube, Perforce
- Terraform HCL IaC scanned using tfsec, Checkov, Sonatype, etc.
- IaC https://github.com/configu/docs
- Python code scanned using PEP8, Bandit, etc.
- Java Qulice (quality police) combines several scanners to apply over 900 rules on just Java code.
- etc.
PROTIP: Even if develpers can catch all vulnerabilities, one advantage of feeback from automated scanners is that their criticism cannot be perceived as a personal attack and thus cause animosity within the team. Feedback from scanners is impartial, and does not take into account personality conflicts and prejudices.
-
Make it easy to use a private store of binary files (installers, Docker container images for Kubernetes, and other binary files)
-
Run policy-as-code checkers (using <a target=”_blank” href=”Open Policy Agent (OPA)</a>):
- How to enforce use of tags
- How to enforce use of tags
-
Verify that unauthorized changes have not occurred by referencing assets using hashes of file contents rather than file names and versions.
-
Provide an easy way to create documents - (writing docstrings in code, tags, etc.) so indexes of functions can be automatically generated; blogs
References:
-
VIDEO: Static code analysis: pattern matching, procedural, data flow, and statistical analysis. Also included are examples of common software vulnerabilities such as memory corruption, buffer overflow and over reads, script injection, XSS and CSRF, command injection, and misconfigurations.
-
AppSec Decoded: the worst DevSecOps practices by RSA keynoter Tanya Janca (SheHacksPurple Academy), with Taylor Armerding, Security Advocate.
Where is the creativity?
Some may bristle at this “take it or leave it” approach from some.
Does that stifle creativity?
When all code is known to follow a certain set of rules, the code is more maintainable.
There’s another, perhaps future benefit.
Automated refactoring of the entire code base at once can occur with less worry and work.
What’s more, when code is inevitably generated by machines, the scanners will be there to catch their errors, and thus accelerate results.
Thus, scanners ensure the conditions for speed and rapid adoption of innovation.
The source of coding violations can often be attributed to the training provided. In an effort to simplify concepts for learning, examples provided in tutorials are often not “production-worthy”. Nevertheless, those examples are used out of habit.
In order for the automatic scanner to be a patient tutor, it needs to explain how to do it correctly – how to correct the errant code given – rather than simply complaining and dismissing errant code.
And that’s where live human tutoring is helpful – to provide the nurturing, the explanation of “why” in a way that the learner would best understand.
MY PROPOSAL: A wiki with an entry that explains each rule, with links to explanations of underlying knowledge. Such a public forum is where debates about the merits of each rule.
“Where understanding abounds, acceptance will flourish.”
Empathetic, specific, and kind feedback?
Some time back, a book named High Tech, High Touch popularized the concept (as I understand it) that more real personal physical attention is needed with heightened technology use.
When one introduces a know bad piece of code, the other doesn’t have to say a word, and just let the scanner do the rejection.
This way, feeback cannot be perceived as a personal attack and thus cause animosity.
Discussions about code can then transcend from whether someone is a good person depending on whether they use spaces or tabs.
DevSecOps for SAP
In the past few years, organizations have seen a constant increase in cyberattacks targeting business-critical applications and the data within because that data is particularly lucrative to sell or trade.
I can see that organizations running SAP software are especially vulnerable to cyberattacks. SAP systems are complex because they are
- are implemented within large bureaucracies, which make changes difficult and slow to coordinate
- were architected in the 90s when security was not a priority. DevSecOps tools developers need to validate source code for security flaws has not been built into SAP’s transport management system.
- are highly customized, so vulnerable coding can creep in
- are highly interconnected with other systems, which makes segmentation difficult
- are easy to patch, so many users delay upgrades
- are implemented by specialized teams not integrated with cybersecurity teams
Onapsis is SAP’s chosen partner for cybersecurity. https://rev-trac.com/articles/sap-security-a-devsecops-solution/
https://www.youtube.com/watch?v=dmmdooJmN_E Rev-Trac SAP Transport Security
Julie Hallet - A Practical Guide to Cybersecurity in SAP
SecurityBridge platform for SAP, Christoph Nagy CEO
https://blogs.sap.com/tag/devsecops/
https://sapinsider.org/event-presentations/why-sap-customers-need-devsecops-now-more-than-ever/
Professional certifications
Synposys hands out “badges” on Codity for each of its paid classes taken (with a 85% pass rate). https://training.synopsys.com/learn/signin
References
Rather than repeating others, let me link to the most influencial pieces about DevOps:
- http://continuousdelivery.com
- 12factor.net (The Twelve Factor App)
- 12 Factor App in plain english
- The acronym CAMS (Culture, Automation, Measurement, Sharing) was coined by Damon Edwards (@damonedwards) and John Willis (@botchagalupe), authors of DevOps Cafe, in the early 2010s. *
- Google’s what is Site Reliability Engineering?
- SRE and the Value of Treating Operations as a Software Problem
- The Site Reliability Workbook
- DevOps Team Types
- DevOps Anti-Types
- BOOK: Team Topologies: Organizing Business and Technology Teams for Fast Flow
- Practice of Cloud System Administration: Designing and Operating Large Distributed Systems
- Microsoft’s Release Pipeline Model - Download PDF is a high-level description before Azure DevOps appeared.
- https://continuousdelivery.com/implementing/patterns/
More about DevOps
- DevOps_2.0
- ci-cd (Continuous Integration and Continuous Delivery)
- User Stories for DevOps
- Git and GitHub vs File Archival
- Git Commands and Statuses
- Git Commit, Tag, Push
- Git Utilities
- Data Security GitHub
- GitHub API
- Choices for DevOps Technologies
- Pulumi Infrastructure as Code (IaC)
- Java DevOps Workflow
- AWS DevOps (CodeCommit, CodePipeline, CodeDeploy)
- AWS server deployment options
- Cloud services comparisons (across vendors)
- Cloud regions (across vendors)
- Azure Cloud Onramp (Subscriptions, Portal GUI, CLI)
- Azure Certifications
- Azure Cloud Powershell
- Bash Windows using Microsoft’s WSL (Windows Subsystem for Linux)
- Azure Networking
- Azure Storage
- Azure Compute
- Digital Ocean
- Packer automation to build Vagrant images
- Terraform multi-cloud provisioning automation
-
Hashicorp Vault and Consul to generate and hold secrets
- Powershell Ecosystem
- Powershell on MacOS
- Jenkins Server Setup
- Jenkins Plug-ins
- Jenkins Freestyle jobs
- Docker (Glossary, Ecosystem, Certification)
- Make Makefile for Docker
- Docker Setup and run Bash shell script
- Bash coding
- Docker Setup
- Dockerize apps
- Ansible
- Kubernetes Operators
- Threat Modeling
- API Management Microsoft
- Scenarios for load
- Chaos Engineering