The Federal Risk and Authorization Management Program (FedRAMP) enables cloud services providers to meet one standard for all US fed govt agencies
Overview
- ATO to CSPs
- JAB (Joint Authorization Board)
- FISMA (Federal Information Security Modernization Act)
- Reports to obtain each FedRAMP Marketplace Designation
- Phases and Steps
- SSP (System Security Plan)
- SAP (Security Assessment Plan)
- SAR (Security Assessment Report)
- Continuous Monitoring
- CIS (Control Implementation Summary)
- FedRAMP Security Baseline Levels
- CMMC
- 872 Security Controls
- Each Control
- Authorized CSP web pages
- FedRAMP Consultants:
- 3PAO Assessors
- Certification of Individual Professionals
- GRC (Governance, Risk management, and Compliance)
- Courses
- Social Media
- Organizational Structure
- References
- More on Security
PROTIP: Acronyms here are in my Quizlet flashcards for Cyber Security for you to study more efficiently.
ATO to CSPs
In 2011 a “cloud first” policy was defined in the Federal Risk and Authorization Program (FedRAMP) [pdf] where federal agencies make use of cloud service providers (CSPs) given authority to operate (ATO) after receiving system authorization from a security assessment conducted by an independent 3PAO (Third-Party Assessor Organization).
FedRAMP was established to provide to all federal agencies using cloud services a common set of security requirements to store, process, and transmit data.
This presentation developed by MITRE estimates that the median cost for a CSP to obtain provisional authority to operate of around $2.25 million, with another $1 million yearly to maintain continuous monitoring.
JAB (Joint Authorization Board)
All agencies of the United States federal government accepts and ATO obtained through either one of two approaches to obtaining a FedRAMP Authority to Operate (ATO):
-
an authorization through an agency A-ATO (Agency Authority to Operate), or
-
a provisional authorization (P-ATO) through the JAB (Joint Authorization Board), who can issue a Provisional Authority to Operate (P-ATO) to a CSP after receiving via Federal Connect a business case showing government-wide demand for the CSO (Cloud Service Offering). The JAB consists of the Chief Information Officers (CIOs) from DOD, DHS, and GSA, supported by designated technical representatives (TRs) from their respective member organizations. The JAB is responsible for the overall management of the FedRAMP program, including the development of the FedRAMP security baseline, the development of the FedRAMP security assessment process, and the development of the FedRAMP continuous monitoring process.
The majority of organizations first obtains an ATO and then later obtain a P-ATO. JAB works only with 12 CSPs per year that have already obtained an ATO. The P-ATO process requires a Readiness Assessment.
FISMA (Federal Information Security Modernization Act)
FedRAMP (Federal Risk and Authorization Management Program) was established by OMB (Office of Management and Budget) to add to 2014 law FISMA (Federal Information Security Modernization Act) a standardized approach to security assessment, authorization, and continuous monitoring for cloud products and services.
Cyber Intelligence Sharing and Protection Act.
Reports to obtain each FedRAMP Marketplace Designation
After each below is submitted to the FedRAMP PMO and approved, the CSP will be designated as:
- Ready after a Readiness Assessment Report (RAR)
- In-Process after a Security Assessment Plan (SAP)
- Authorized after a Security Assessment Report (SAR)
Phases and Steps
- Readiness Assessment
- RAR (Readiness Accessment Report) Development
- FedRAMP PMO Review of RAR
- Remediation of RAR Findings (if needed)
- STATUS: FedRAMP Marketplace Designation - Ready
Pre-Authorization: - Partnership Establishment with 3PAO
- Authorization Planning
- Kickoff Meeting
- STATUS: FedRAMP Marketplace Designation - In Process
- Authorization of Security Authorization Package:
- SSP (System Security Plan)
- SAR (Security Authorization Package)
- POA&M (Plan of Action and Milestones)
Agency Authorization Process: - Agency Review of SAR (Security Authorization Package)
- SAR Debrief
- Remediation of SAR Findings (if needed)
- Agency Final Review
- FedRAMP PMO Review of Agency Final Review
- STATUS: FedRAMP Marketplace Designation - Authorized
- Continuous Monitoring
- CA-1 = Annual Assessment of procedures annually; of policies every 3 years
- Remediation of Annual Assessment Findings (if needed)
The FedRAMP Program Management Office (PMO) provides training, guidance, and advisory support to CSPs, helping them navigate the FedRAMP process and understand the requirements.
- https://www.fedramp.gov/training/
-
DFARS (Defense Federal Acquisition Regulation Supplement) 204.73 (c) (2) (ii) requires that all cloud services be FedRAMP authorized.
OMB (Office of Management and Budget) Circular A-130 states that when agencies implement FISMA, they must use National Institute of Standards and Technology (NIST) standards and guidelines.
SSP (System Security Plan)
-
VIDEO & PDF: 200-A: FedRAMP System Security Plan (SSP) Required Documents (Revised July 2021)
VIDEO PDF: A System Security Plan (SSP) – submitted in both Word and PDF formats – is required by the PDF: “OMB Security Authorization of Information Systems in Cloud Computing”.
Each SSP authorization package can be in a machine-readable (JSON or XML format) https://github.com/usnistgov/OSCAL Open Security Controls Assessment Language - based on templates created based on this Excel xlsx file which defines fields (extensions), identifiers, and values in the FedRAMP Registry at https://github.com/GSA/fedramp-automation. The template is from FedRAMP PMO and NIST.
Sections within the usual 700 pages of the SSP include:
- Identifies information system name and title
- Identifies the system categorization and digital identity and authentication (DIA) requirements
- Identifies the system owner and contact information
- Identifies the authorizing official and contact information
- Identifies other designated officials and contact information
- Identifies the assignment of security responsibilities
- Identifies the information system’s operational status
- Identifies the type of information system
- Describes the functions and purposes of the information system
- System Function and Purpose
- Roles and Responsibilities
- Types of Users
- Information System Components & Boundaries
- Network Architecture (VPN, subnets, DNSSEC, DMZ, etc.)
- Describes the information system environments and inventory (with dataflows, ports, protocols, services)
- Identifies interconnections between othere other information systems
- Laws, regulations, policies, standards, and guidance that apply to the information system
- Minimum security controls for the information system
- Acronyms and abbreviations
- Attachments
- SSP ATTACHMENT 1: Information Security Policies and Procedures (covering all control families)
- SSP ATTACHMENT 2: User Guide
- SSP ATTACHMENT 3: Digital Identity worksheet and Authentication (DIA) Guide
- SSP ATTACHMENT 4: Privacy Threshold Analysis (PTA) Report and Privacy Impact Assessment (PIA)
- SSP ATTACHMENT 5: Rules of Behavior (RoB) and Acceptable Use Policy (AUP)
- SSP ATTACHMENT 6: Information System Contingency Plan (ISCP), which links to the Contingency Plan Test Report in Appendix G of the ISCP
- SSP ATTACHMENT 7: Configuration Management Plan (CMP)
- SSP ATTACHMENT 8: Incident Response Plan (IRP)
- SSP ATTACHMENT 9: Control Implementation Summary (CIS)
- SSP ATTACHMENT 10: FedRAMP Information Processing Standard (FIPS) 199 Security Categorization
- SSP ATTACHMENT 11: Separation of Duties (SOD) Matrix
- SSP ATTACHMENT 12: Laws and Regulations (such as HIPPA)
- SSP ATTACHMENT 13: Integrated Inventory Workbook
-
SSP ATTACHMENT 14: SSP Certification and Accreditation (C&A) Package
- Plan of Action and Milestones (POA&M)
- Continuous Monitoring Strategy (required by CA-7)
-
Continuous Monitoring Monthly Executive Summary
- Authorization Boundary Diagram
- Data flow diagram
- Types of inheritance from other FedRAMP leveraged systesm
- External services in use by the system not FedRAMP authorized (corporate services such as email, etc.)
- Federally-noted pieces that should be adequately described and secured:
- Development and test environments
- Transport services
- Multi-factor authentication
- Alternate storage and processing sites
Documentation of the CSO:
- System boundary diagram and all data flows internal and external to the system traversing the boundary
- Dataflow diagram that have NIST FIPS 140-2-validated cryptographic modules, or other cryptographic modules that are not FIPS 140 validated, but are approved by the FedRAMP PMO
- Customer responsibilities for each control defined in the system baseline and what the leveraging partner is responsible for to implement controls
- System diagrams that show the cloud service offerings and multi-factor authentication plus authentication methods for:
- Network access by customer accounts that are not privileged or non-privileged
- Network access by cloud server privileged administrators
- Local access by cloud server privileged administrators
- Scanning capabilities for operating systems, databases, web applications, IaC (Terraform), containers, etc.
- Inventory of hardware, software, and firmware assets
FedRAMP.gov does not provide a template for:
- Incident response plan
- Configuration Management Plan
- Policies & Procedures
SAP (Security Assessment Plan)
VIDEO PDF: 200-B: Security Assessment Plan (SAP)
- APPENDIX A: Security Test Case Procedures
- APPENDIX B: Penetration Testing Plan and Methodology (attack vectors, sampling methodology, etc.)
- APPENDIX C: 3PAO Supplied Deliverables (Penetration Testing Rules of Engagement, Sampling Methodology, 3PAO Assessment Report Template)
SAR (Security Assessment Report)
VIDEO PDF: 200-C: Security Assessment Report (SAR) residual risk accepted analysis and mitigation plan
- APPENDIX A: Risk Exposure Table (RET)
- APPENDIX B: Security Test Case Procedures
- APPENDIX C: Infrastructure Scan Results
- APPENDIX D: Database Scan Results
- APPENDIX E: Web Scan Results
- APPENDIX I: Auxiliary Documents (evidence artifacts)
- APPENDIX J: PenetratonTest Report
Continuous Monitoring
VIDEO PDF: 200-D: Continuous Monitoring
CIS (Control Implementation Summary)
VIDEO PDF: 201-B: How to Write a Control Implementation Summary (CIS) (Revised July 2021) for a CSP pursuing a JAB Authorization with a 3PAO, or a 3PAO conducting an assessment of the cloud system.
FedRAMP Security Baseline Levels
FedRAMP categorizes CSOs into three levels according to the potential impact of a data breach. The three security baselines for controls are based on the Federal Information Processing Standard (FIPS) 199 standards from the National Institute of Standards and Technology (NIST). These controls are required to achieve the CIA “triad” of security objectives:
- Confidentiality - Protections for personal privacy and proprietary information
- Integrity - Protections against the destruction or modification of stored information
- Availability - Timely and reliable access to information
FedRAMP defines 3 security baseline levels to set the risk for each category based on the target’s value to adversaries and/or the consequences of a compromise on organizational operations, organizational assets, or individuals:
-
Low - The loss of confidentiality, integrity, or availability could be expected to have a “limited adverse” effect on organizational operations, organizational assets, or individuals.” Low-Impact Software-as-a-Service (LI-SaaS) are “systems that are low risk for uses like collaboration tools, project management applications, and tools that help develop open-source code.”
-
Moderate - “serious adverse” consequences of a compromise.
-
High - “catastrophic” adverse effects
NOTE: FIPS 199 & DOD-IL 4 defines 5 impact levels, including:
- Very High - “disastrous” effect
- Critical - “catastrophic” effect
Most are moderate. The FedRAMP Marketplace Designations for Cloud Service Providers document lists the security baseline level for each CSP.
294 page PDF: NIST SP 800-160 Vol 2 defines the level for various types of data.
Until FedRAMP was created in 2016, federal government agencies were only allowed to contract with CSPs for work at the low and moderate impact levels. The high impact level was reserved for the Department of Defense (DoD) and other agencies with special security requirements. The high impact level is now available to all agencies.
A FedRAMP Moderate authorization enables CSPs to obtain an Impact Level 2 (IL2) authorization while a FedRAMP High authorization enables them the CSP to gain an IL4 with the DoD. See the DoD Cloud Security Requirements Guide (SRG) introduced in 2012.
CMMC
The Cybersecurity Maturity Model Certification (CMMC) program is for industrial-based companies, such as automobile and aerospace manufacturers, that want to provide products to the DoD. The CMMC program uses NIST SP 800-171 as a reference for it’s baseline. This initiative requires compliance to continue any existing contracts with the Department of Defense.
872 Security Controls
Coalfire
came up with this count of controls:
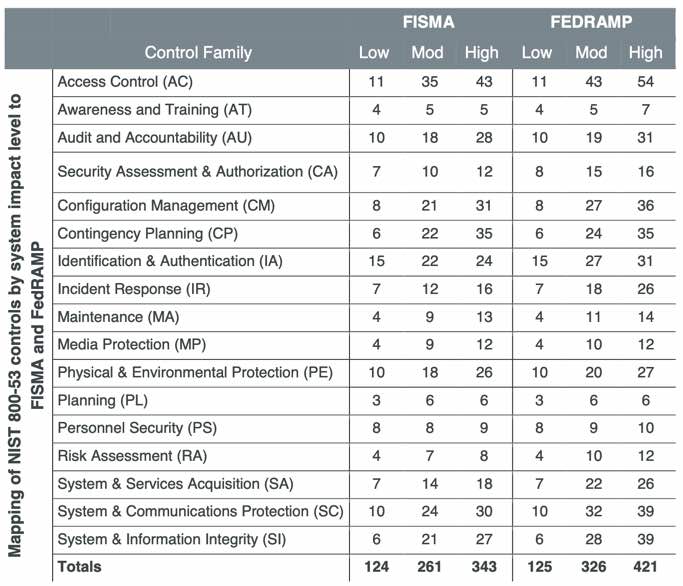
FedRAMP added 144 cloud controls to 728 in FISMA, for a total of 872 controls in 17 Control Families:
| Family of Controls | Title | Abbr. | High | Moderate | Low |
|---|---|---|---|---|---|
| 1 | AC | Access Control | 54 | 43 | 11 |
| 2 | AU | Audit and Accountability | 31 | 19 | 10 |
| 3 | AT | Awareness and Training | 7 | 5 | 4 |
| 4 | CM | Configuration Management | 36 | 26 | 8 |
| 5 | CP | Contingency Planning | 35 | 24 | 6 |
| 6 | IA | Identification and Authentication | 31 | 27 | 15 |
| 7 | IR | Incident Response | 26 | 18 | 7 |
| 8 | MA | Maintenance | 14 | 11 | 4 |
| 9 | MP | Media protection | 12 | 10 | 4 |
| 10 | PS | Personnel Security | 10 | 9 | 8 |
| 11 | PE | Physical and environmental protection | 27 | 20 | 10 |
| 12 | PL | Planning | 6 | 6 | 3 |
| 13 | RA | Risk Assessment | 12 | 10 | 4 |
| 14 | CA | Security Assessment and Authorization | 16 | 15 | 8 |
| 15 | SC | System and Communications protection | 39 | 32 | 10 |
| 16 | SI | System and Information integrity | 39 | 28 | 7 |
| 17 | SA | System and Services Acquisition | 26 | 22 | 6 |
| TOTALS | 421 | 325 | 125 | ||
REMEMBER: “Security Assessment and Authorization” is abbreviated “CA” because “SA” is already taken by “System and Services Acquisition”. The memomic is that the two A’s in “Security Assessment and Authorization”.
QUESTION: “Supply Chain Management” is not included among the 872 controls?
StackArmor breaks down the 325 controls for moderate further:
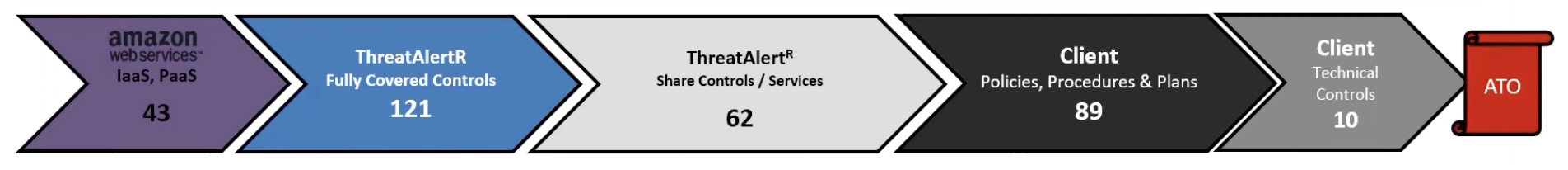
- 43 built-in controls within AWS services
- 121 controls covered by StackArmor’s ThreatAlert controls
- 52 shared controls in StackArmor’s ThreatAlert controls
- 89 client Policies, Procedures, and Plans
- 10 client Technical Controls
Notice that Amazon services not accredited for High (Govclound) include Amazon: Batch, Chime, Connect, CloudFront, EKS, WorkSpaces, WorkDocs/WorkMail/WorkLink.
Each Control
FedRAMP utilizes PDF: >NIST SP 800-53B Rev 5 “Control Baselines for Information Systems and Organizations”, which is a catalog (dictionary) of all 281 security controls. Note the “B” for Baseline. A few can be “tailored” out for specific needs.
PDF: NIST 800-18 rev 1 Feb 2006 “Guide for Developing Security Plans for Federal Information Systems” on how to implement controls and prepare security plans for FISMA systems.
PROTIP: Use the Security Compliance Quizlet to memorize for the FedRAMP certification exam.
https://csrc.nist.gov/CSRC/media/Publications/sp/800-53/rev-5/final/documents/sp800-53r5-to-iso-27001-mapping.docx, Mappings between 800-53 Rev. 5 and other frameworks and standards: ISO/IEC 27001
58 reports need to be prepared at least once a year, some monthly or weekly.
The CSP must remediate:
- high risks within 30 days;
- medium risks within 90 days;
- low risks within 180 days. Or the agency can accept the risk and move forward with the contract.
Authorized CSP web pages
FISMA requires that agencies authorize the 300+ CSOs (Cloud Solution Offerings)/products they use.
Here’s how CSPs announce their “FedRAMP Ready” status, with CRM (Customer Responsibility Matrix), and CIS (Controls Implementation Summary), and CCGs (Customer Compliance Guides) under NDA:
-
AWS is FedRAMP Ready at Medium on US West & East regions, and High on GovCloud (US).
- https://www.box.com/fedramp
- https://qualtrics.com/platform/fedramp
- https://www.salesforce.com/products/fedramp/
FedRAMP Consultants:
To be clear, concise, consistent, and complete - who, what, when, where, and how
-
StackArmor provides, Landing Zones (for AWS, Azure, and GCP) and pre-filled ATO doc SSP procedures.
- https://www.egnyte.com/
- Mindpoint Group
- https://www.nccgroup.com/ UK
- https://www.pwc.com/us/en/technology.html
3PAO Assessors
https://www.fedramp.gov/assessors/
Accreditation of 3PAOs are governed by A2LA (American Associate for Laboratory Accreditation) based on coformative assessment.
PDF: FedRAMP Marketplace Designations for Cloud Service Providers FEDRAMP MARKETPLACE website
Accessors (how many they’ve done, with contact info).
-
https://www.vaultes.com/compliance-audits/fedramp/
-
VIDEO: StackArmor reduces the time and cost of achieving assessments “by 50%” with their FedRAMP-Ready AWS Landing Zones of automation, pre-filled ATO doc SSP procedures, and FedRAMP Ready templates.
Certification of Individual Professionals
$599 USD CGRC (Certified Government Risk and Compliance) professional – previously CAP (Certified Authorization Professionl) until Feb 23, 2023 – is for individuals with 2+ years of experience being responsible for the implementation and management of information security risk management and compliance programs. Pass 70% of 125 questons over 3 hours at a Pearson VUE Testing Center.
GRC (Governance, Risk management, and Compliance)
CGRC Content maps to the NIST RMF (Risk Management Framework) and is taken from a broad spectrum of vendor-neutral topics in the CGRC Common Body of Knowledge (CBK) over 7 domains.
The first scholarly research on GRC was published in 2007 where GRC was formally defined as “the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty, and act with integrity.”
AWS says Good Governance includes:
- Ethics and accountability
- Transparent information sharing
- Conflict resolution policies
- Resource management
“Definitive Guide to RMF (Actionable plan for FISMA Compliance)”
PDF: Risk Management Framework NIST 800-37
Gerald Auger, PhD (SimplyCyber.io, published $30 GRC (Governance, Risk management, and Compliance) Analyst Master Class.
A GRC course is accredited by the ISACA (Information Systems Audit and Control Association).
Courses
https://www.udemy.com/course/certified-cybercop-cloud-security-fedramp-part-1/ https://www.udemy.com/course/certified-cybercop-cloud-security-fedramp-part-2/ $85 “Certified Cybercop – Cloud Security & FedRAMP Part 1 (Get free Mock Exam and Flash Cards)” Prepared and Developed by CertCop Certified Trainers & Professionals.”
Social Media
- YouTube channel from info.fedramp.gov
- https://twitter.com/fedramp?lang=en
Organizational Structure
Under the CISO (Chief Information Security Officer) are:
- Risk & Compliance (identifying and mitigating risks, auditing)
- Cybersecurity Operations (including the SOC) has Security Analysts dealing with incidents
- Enterpise Security (Security tooling)
- Identity & Access Management (IAM)
The GRC team includes the CISO’s GRC Analyst, GRC Engineer, and GRC Architect.
EO 14028 for Zero Trust
UK Government G-Cloud is a cloud computing certification for services used by government entities in the United Kingdom.
References
- https://en.wikipedia.org/wiki/FedRAMP
- https://resources.infosecinstitute.com/topic/building-your-fedramp-certification-and-compliance-team/
- https://www.pivotpointsecurity.com/services/fedramp/
https://www.unifiedcompliance.com/ (UCF) offers their Common Controls Hub SaaS to compile for your company a master list of controls from a library of 700+ standards assembled from around the globe from PCI DSS, SP800-53 (FISMA), ISO 27001:2013, CobiT, etc.
* https://www.isaca.org/resources/news-and-trends/isaca-now-blog/2021/five-considerations-for-leveraging-the-unified-compliance-framework
More on Security
This is one of a series on Security in DevSecOps:
- Security actions for teamwork and SLSA
- Code Signing on macOS
- Git Signing
- GitHub Data Security
- Azure Security-focus Cloud Onramp
- AWS Onboarding
- AWS Security (certification exam)
- AWS IAM (Identity and Access Management)
- SIEM (Security Information and Event Management)
- Intrusion Detection Systems (Goolge/Palo Alto)
- SOC2
- FedRAMP
-
CAIQ (Consensus Assessment Initiative Questionnaire) by cloud vendors
- AKeyless cloud vault
- Hashicorp Vault
- Hashicorp Terraform
- SonarQube
- WebGoat known insecure PHP app and vulnerability scanners
- Security certifications
- Quantum Supremecy can break encryption in minutes
- Pen Testing
- Threat Modeling
- WebGoat (deliberately insecure Java app)

