There are several (overlapping) ones.
Overview
- Other lists:
- Glossaries
- IAPP
- OCEG
- CCSK
- Certified Infosec NIST CSF
- ISC2.org
- ISACA.org
- Zero Point Security CRTO
- Offensive Security
- SANS GIAC
- CompTIA
- Cisco
- INE eLearnSecurity
- EC-Council Penetration Tester
- APISec University
- IIBA Cybersecuity Analysis
- AWS Security
- Microsoft SC-900 & AZ-500
- SAP
- Secure Coding
- Networking (Firewall) certs
- TCM Academy
- OSIP (Open Source Intelligence Professional)
- References
- Movies
- More on Security
 For security professionals, there are several expensive overlapping certification exams, from competing agencies.
For security professionals, there are several expensive overlapping certification exams, from competing agencies.
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
This map from security techo thriller book reviewer Paul Jerimy at
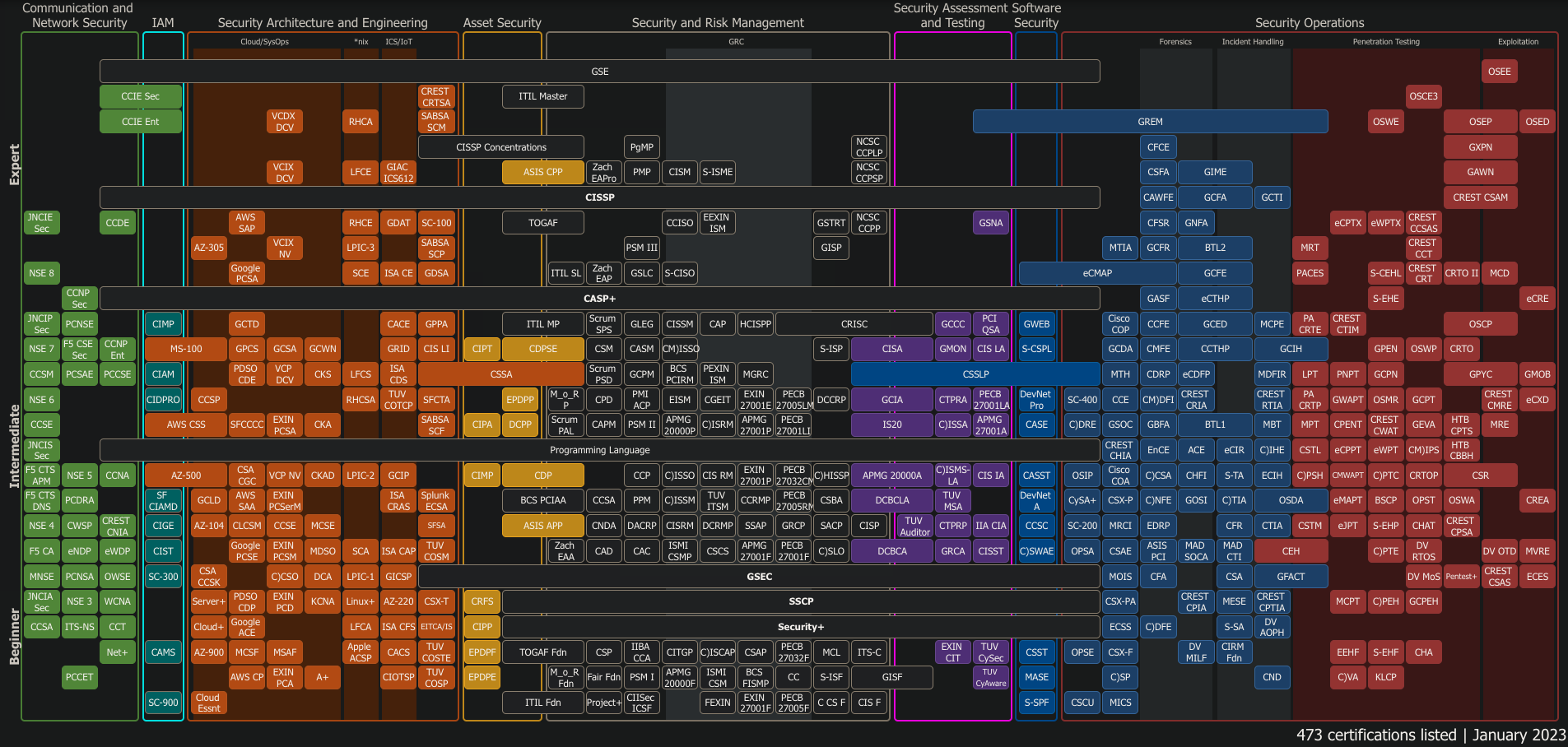
Click for full screen image.
cyberseek.org analyzed openings to identify the popularity of certifications requested:

- ISC2 CISSP
- CompTIA Security+
- ISACA CISA (Certified Information Systems Auditor)
- SANS GIAC (Global Information Assurance Certification)
- ISACA CISM (Certified Information Security Manager)
- CIPP (Certified Information Privacy Professional) answer 90 multiple-choice questions in 2.5 hours online or at a Pearson VUE test center. Its $550 plus a Maintenance Fee of $250/2 year. It assesses knowledge of U.S. privacy laws and regulations and legal requirements for transferring sensitive personal data to/from the United States, the EU and other jurisdictions.
Upon passing your exam, you will need to purchase a Certification Maintenance Fee to activate your certification, and again for each two-year certification term.
For IAPP members, the fee is built into membership benefits. Non-member test takers are encouraged to purchase the Certification Maintenance Fee at the time of exam purchase so it will activate automatically upon passing the exam.
Other lists:
- spreadsheet by Dean Bushmiller.
- h4cker by the legend Omar Santos
Glossaries
- My Acronyms in various industries
- https://github.com/deanbushmiller/CEH-bootcamp/wiki/CEH-Glossary
IAPP
The International Association of Privacy Professionals (iapp.org) costs $295/year ($100 for retired and non-profits) plus $550 per exam:
- AIGP (AI Governance Professional)
- CIPP (Certified Information Privacy Professional)
- CIPM (Certified Information Privacy Manager)
- CIPT (Certified Information Privacy Technologist)
- CDPO CDPO/BR CDPO/FR in Brazilian and French
OCEG
From oceg.org “from the global nonprofit think tank that invented GRC” (Governance, Risk, Compliance) standards:
- Glossary
- Red Book Capability Model
- Burgendy Book Assessment Tools
$499/year includes training on GRC strategy and audit: - GRCP (GRC Professional)
- GRCA (GRC Auditor)
CCSK
The Certificate of Cloud Security Knowledge (CCSK) is marketed as a complement to other credentials (CCAK, CISA, CISSP, CCSP) by the Seattle-based Cloud Security Alliance (CSA) which also markets training.
QUESTION: The CSA Cloud Trust Protocol Daemon protoype is inactive?
Whizlabs has sample tests but questionable quality with too many double negative questions and answers.
The CCSK is an open-book, online exam, completed in 90 minutes. Purchasing the exam costs $395 (free to veterans) for two test attempts, which you will have 2 years to use. The minimum passing score is 80% of the 60 multiple-choice vendor-neutral questions selected randomly from the CCSK question pool in v4 of the exam available December 1, 2017:
-
6% are based on the 2009 Cloud Computing report from the ENISA (European Network and Information Security Agency)
-
7% are based on CSA’s CCM (Cloud Controls Matrix) spreadsheet 3.0.1 which cross references the many other standard worldwide (AICPA, PIPEDA, CIS, COBIT, CSA, ENISA, FedRAMP, GAAP, HIPPA, HITRUST, IEC, NIST, PCI, etc.). It is the basis for CSA’s Consensus Assessments Initiative Questionnaire (CAIQ) industry-accepted way to document which security controls exist in IaaS, PaaS, and SaaS services, which inputs to “Level 1” of the STAR (CSA Security Trust Assurance and Risk) Registry of vendors.
-
87% are based on the CSA Guidance v4 at PROTIP: https://github.com/cloudsecurityalliance/CSA-Guidance – a masterwork providing a summary of terms and concepts which integrate the various worldwide standards.
https://www.meetup.com/Cloud-Security-Alliance-Northeast-Ohio-Chapter/events/275707693/ Cloud Security Alliance NorthEast Ohio chapter
Domain 1 Cloud Computing Concepts and Architectures
- Definitions of Cloud Computing
- Service Models
- Deployment Models
- Reference and Architecture Models
- Logical Model
- Cloud Security Scope, Responsibilities, and Models
- Areas of Critical Focus in Cloud Security
Domain 2: Governance and Enterprise Risk Management
- Tools of Cloud Governance
- Enterprise Risk Management in the Cloud
- Effects of various Service and Deployment Models
- Cloud Risk Trade-offs and Tools
Domain 3: Legal Issues, Contracts and Electronic Discovery
- Legal Frameworks Governing Data Protection and Privacy
- Cross-Border Data Transfer (GDPR)
- Regional Considerations (California)
- Contracts and Provider Selection
- Contracts
- Due Diligence (is the practice of Due Care)
- Third-Party Audits and Attestations (SOC, ISO)
- Electronic Discovery
- Data Custody
- Data Preservation
- Data Collection
- Response to a Subpoena or Search Warrant
Domain 4: Compliance and Audit Management
- Compliance in the Cloud
- Compliance impact on cloud contracts
- Compliance scope
- Compliance analysis requirements
- Audit Management in the Cloud
- Right to audit
- Audit scope
- Auditor requirements
Domain 5: Information Governance
- Governance Domains
- Six phases of the Data Security Lifecycle and their key elements
- Data Security Functions, Actors and Controls
Domain 6: Management Plane and Business Continuity
- Business Continuity and Disaster Recovery in the Cloud
- Architect for Failure
- Management Plane Security
Domain 7: Infrastructure Security
- Cloud Network Virtualization
- Security Changes With Cloud Networking
- Challenges of Virtual Appliances
- SDN Security Benefits
- Micro-segmentation and the Software Defined Perimeter
- Hybrid Cloud Considerations
- Cloud Compute and Workload Security
Domain 8: Virtualization and Containers
- Mayor Virtualizations Categories
- Network
- Storage
- Containers
Domain 9: Incident Response
- Incident Response Lifecycle
- How the Cloud Impacts IR
Domain 10: Application Security
- Opportunities and Challenges
- Secure Software Development Lifecycle
- How Cloud Impacts Application Design and Architectures
Domain 11: Data Security and Encryption
- Data Security Controls
- Cloud Data Storage Types
- Managing Data Migrations to the Cloud
- Securing Data in the Cloud
Domain 12: Identity, Entitlement, and Access Management
- IAM Standards for Cloud Computing
- Managing Users and Identities
- Authentication and Credentials
- Entitlement and Access Management
Domain 13: Security as a Service
- Potential Benefits and Concerns of SecaaS
- Major Categories of Security as a Service Offerings
Domain 14: Related Technologies
- Big Data
- Internet of Things
- Mobile
- Serverless Computing
Certified Infosec NIST CSF
While it develops a new Cybersecurity Certification Exam, ISACA’s 4-hour CSX-P (Cybersecurity Practitioner) exam, derived from the NIST Cyber Framework was sunsetted on 30 April 2023.
For $674.95 plus $100 annual membership and $399.95 for the required 3-day on-line class or $3,995 on-site class, get the “NIST Cybersecurity Framework Lead Implementer” certification by answering 75% of 65 questions in 70 minutes. Test content, training, and proctoring are all provided by a single profit-making organization: Certified Information Security (https://www.certifiedinfosec.com), founded by Allen Keele.
Domains covered by the test:
- Framework Core Functions of the NIST CSF
- Identify threats and vulnerabilities
- Protect systems from outside threats
- Detect threats and system vulnerabilities
- Respond to and mitigate cyber incidents
- Recover from incidents and disasters
- Framework Implementation Tiers (Cybersecurity Risk Management)
- Framework Profiles
- Converging NIST CSF into an ISO 27001 Information Security Management System (ISMS).
Crash SuperReview on OReilly.com covers 2 of the 3 day class.
https://learning.oreilly.com/library/view/cybersecurity-career-master/9781801073561/ Cybersecurity Career Master Plan
https://learning.oreilly.com/videos/nist-cybersecurity-framework/9781787782396/ NIST Cybersecurity Framework - A pocket guide
ISC2.org
ISC2.org (a non-profit), publishes a Code of Ethics at https://www.isc2.org/ethics
https://www.isc2.org/Certifications/Qualification-Pathfinder
Prices for exams taken at Pearson Vue test centers:
CC: Certified in Cybersecurity (CC)
This Certified in Cybersecurity (CC) is a new certification for entry-level cybersecurity professionals. $249 USD to get 70% of 100 questions in 2-hours. The domains:
- Security Principles - 26%
- Business Continuity (BC), Disaster Recovery (DR) & Incident Response - 26%
- Access Controls Concepts - 16%
- Network Security - 16%
- Security Operations - 16%
https://my.isc2.org/s/Candidate-Benefits/1MCC-Online-Self-Paced
Omar Santos (of Cisco), author of the comprehensive hackerrepo.org, prepared on OReilly.com a 3 hours 30 minutes video course. He also has a YouTube video on the CC exam.
SSCP
$249 USD SSCP (Systems Security Certified Practitioner)
“Similar to Security+. Prepares you to take the CISSP.”
CGRC
$599 USD CGRC (Certified Government Risk and Compliance) professional – previously CAP (Certified Authorization Professionl) until Feb 23, 2023 – is for individuals with 2+ years of experience being responsible for the implementation and management of information security risk management and compliance programs. Pass 70% of 125 questons over 3 hours at a Pearson VUE Testing Center.
CGRC Content maps to the NIST SP 800-37 RMF (Risk Management Framework) categories:
- “Left of boom”: Identify, Protect
- “Right of boom”: Detect, Respond, Recover
CGRC is taken from a broad spectrum of vendor-neutral topics in the CGRC Common Body of Knowledge (CBK®) over 7 domains:
- Information Security Risk Management Program
- Control Objectives for Information and Related Technology (COBIT)
- International Organization for Standardization (ISO) 27001,
- International Organization for Standardization (ISO) 31000,
- Federal Information Security Modernization Act (FISMA),
- Federal Risk and Authorization Management Program (FedRAMP),
- General Data Protection Regulation (GDPR),
- Health Insurance Portability and Accountability Act (HIPAA)
- Scope of the Information System:
- Federal Information Processing Standards (FIPS) 199,
- International Organization for Standardization/International Electrotechnical Commission (ISO/IEC) 27002,
- data protection impact assessment
- Selection and Approval of Security and Privacy Controls: baseline and inherited controls; control enhancements (e.g., security practices, overlays, countermeasures); continuous control monitoring strategy (e.g., implementation, timeline, effectiveness); Information Security Management System (ISMS)
- Implementation of Security and Privacy Controls
- Information Technology Security Guidance ITSG-33 – Annex 3A,
- Technical Guideline for Minimum Security Measures,
- United States Government Configuration Baseline (USGCB),
- National Institute of Standards and Technology (NIST) checklists,
- Security Technical Implementation Guides (STIGs)
- Center for Internet Security (CIS) benchmarks,
- General Data Protection Regulation (GDPR)
- Assessment/Audit of Security and Privacy Controls
- Risk treatment options (i.e., accept, avoid, transfer, mitigate, share)
- Authorization/Approval of Information System
- Continuous Monitoring
- https://www.isc2.org/certifications/References#
- https://www.isc2.org/Certifications/CAP/experience-requirements
- https://resources.infosecinstitute.com/overview/cgrc/ reports there are 4,157 CGRC/CAP holders
Gerald Auger, PhD (SimplyCyber.io, publisher of the $30 GRC (Governance, Risk management, and Compliance) Analyst Master Class. The first scholarly research on GRC was published in 2007 where GRC was formally defined as “the integrated collection of capabilities that enable an organization to reliably achieve objectives, address uncertainty, and act with integrity.” Good governance includes:
- Ethics and accountability
- Transparent information sharing
- Conflict resolution policies
- Resource management
CISSP
 Even at $749 USD, the Certified Information Systems Security Professional exam (pronouced “sis pee”) is a sought-after technical certification in cybersecurity leaders as the “gold standard” of vendor-neutral cybersecurity certifications. Earning it proves you understand cybersecurity from a management viewpoint -— a requirement if your organization is subject to PCI, GDPR, HIPAA, SOX, ISO 27001, or other regulations.
Even at $749 USD, the Certified Information Systems Security Professional exam (pronouced “sis pee”) is a sought-after technical certification in cybersecurity leaders as the “gold standard” of vendor-neutral cybersecurity certifications. Earning it proves you understand cybersecurity from a management viewpoint -— a requirement if your organization is subject to PCI, GDPR, HIPAA, SOX, ISO 27001, or other regulations.
The first version of the CISSP Common Body of Knowledge (CBK) was finalized in 1992 and the CISSP credential was launched in 1994. Since it’s an internationally recognized, there are questions about cybersecurity regulations in Canada, UK, EU, etc.
Rather than the previous 250 questions over 6 hourse, the CISSP exam is now adaptive, asking 100-150 questions, depending on whether answers are correct. PROTIP: With Adaptive Testing, your objective is to get hard questions. So study as if you’ll get all hard questions. The better you are, the harder the test is. If you aced the first 10 questions, you’ll be put into “brutal mode”. With CAT (Computer Adaptive Testing), the more one aces every question, the quicker she would get done before the 3 hours. VIDEO: This also means you won’t be able to go back and change answers in previous questions answered.
There is a 5 year experience requirement, attested by other professionals after you pass the exam.
The CISSP has 3 different concentrations:
- ISSAP = Architecture
- Architect for Governance, Compliance and Risk Management
- Security Architecture Modeling
- Infrastructure Security Architecture
- Identity and Access Management (IAM) Architecture
- Architect for Application Security
- Security Operations Architecture
- ISSEP = Engineering
- Systems Security Engineering Foundations
- Risk Management
- Security Planning and Design
- Systems Implementation, Verification and Validation
- Secure Operations, Change Management and Disposal
- ISSMP = Management Professional
- Leadership and Business Management
- Systems Lifecycle Management
- Risk Management
- Threat Intelligence and Incident Management
- Contingency Management
- Law, Ethics, and Security Compliance Management
You need to pass at least 70% on each CISSP domain.
CISSP Domains
- 16% Security and Risk Management - 334
- 10% Asset Security - 44
- 13% Security (Architecture and) Engineering - 268
- 13% (Communication and) Network Security - 114 on OSI model
- 13% Identity and Access Management (IAM) - 82 on biometrics
- 12% Security Assessment and Testing - 41 on NIST SP 800-92
- 13% Security Operations - 245
- 10%
Secure Software Security (Development Lifecycle) - 164 includes a demo of ZAP Proxy for fuzzing, Git & GitHub.
Click on “»” in front of each link to reach my notes at https://wilsonmar.github.io/cyber-security
Numbers to the right of his videos are counts of questions in the OReilly/Pearson bank:
Links under each domain title are to Mike Chapple’s 33-hour LinkedIn Learning videos (and on YouTube). He provides detailed, sequenced lectures, updated for the May 2021 BOK. He includes demos of the most popular software. Links to each CISSP domains contains a link to his tutorial on that domain.
Parentheses in domain names contain words removed in the 2023 version of CISSP.
“Every domain is interconnected. It’s swimming with overlap.”
Official flash cards of definitions:
- The Information Security Environment - 18 items
- Information Asset Security - 17 items
- Identity and Access Management (IAM) - 24 items
- Security Architecture and Engineering - 48 items
- Communication and Network Security - 88 items
- Software Development Security - 101 items
- Security Assessment and Testing - 18 items
- Security Operations - 62 items
- Putting it All Together - 34 items
https://learning.oreilly.com/search/?q=cissp&type=*&rows=10 Search on OReilly.com
Dean Bushmiller (of ExpandingSecurity.com) has a live CISSP Bootcamp on OReilly.com where he goes over his wiki on GitHub. It contains his glossary, notes, and proprietary visual “mind maps”. 888.225-0888
- SRM = Security and Risk Assessment
- ANT = Asset Security
- SAE = Security Architecture and Engineering
- CNS = Communication and Network Security
- IAM = Identity and Access Management
- KAS = Security Testing and Assessment = Knowledge Asset Security?
- OPS = Security Operations
- DEV = Security Development Security
Quizzes on CloudAcademy.com by exam domain:
Written References:
-
$58 Sybex BOOK: “(ISC)2 CISSP Certified Information Systems Security Professional Official Study Guide & Practice Tests Bundle Second Edition” by Mike Chapple, who has a video course on LinkedIn Learning which is deep yet concise, with effective sequencing of topics. He also shows demos of security-related Windows programs where appropriate, such as Windows Firewall Log Viewer.
-
Joseph Delgadillo’s cissp-testprep-cheatsheet provides a PowerPoint file.
-
My notes on cyber security highlights what to remember.
-
PROTIP: The toughest questions among samples is @ITDojo VIDEO: Question of the day, 100+ of them explained by Colin Weaver from 2017.
-
CloudAcademy.com “CISSP Prep.” [subscription] has a timed (40 minute) Knowledge Check of about 20 questions for each domain, available on mobile phones.
-
VIDEO at studynotesandtheory.com by Luke Ahmed, who is dedicated to CISSP education (since 2013). (@securityengineer on Facebook, Telegram). PROTIP: I found his native-sounding English excellent. I think his videos, flash cards, and practice questions are worth the $49 per month (less when buying for a year) because his focus is on how to study and remember content for the exam. He helps by providing memorable conceptual hooks. He is the only one I know who compares differences between content in Shon Harris 7th vs. Sybex books. He provides detailed analysis of why each answer is correct or not. But I can do without the 10 seconds of intro music each module. And it’s annoying to have to reset speed and quality every module.
-
https://learning.oreilly.com/videos/cissp-certification-training/9781771373753/9781771373753-video212908
-
cbtnuggets 11 hrs 56 mins $599.00 USD/year by Keith Barker
-
Michael Gregg’s CISSP Practice Questions on OReilly 2016 are in text.
Not yet updated to CISSP 01 May 2021 changes:
- CBTNubbets by Keith Barker and Ben Finkel.
Video prep courses view:
-
OReilly Live and LiveSessions book by Sari Greene (sarigreene.com) provides a deep dive of all video courses I’ve viewed. 26 hours. A quiz of terms at the end of each video. From 2018.
-
FreeCodeCamp has a single 13 hour video FREE on YouTube to cover all topics. From 2020.
-
YouTube playlist on CISSP FREE by “Skillset” provides a good overview, but it’s from 2016.
-
Pearson CSSLP practice test provides questions. The PearsonTestPrep.com software enables display of individual domains from all 4 tests at once, showing only questions you missed before. Explanations are given as to why each response is correct or not.
-
$599 USD CSSLP (Certified Secure Software Lifecycle Professional) is the secure software development certification. The 15 Sep 2020 edition is NOT covered in the All-in-One book by Wm. Arthur Conklin, Daniel Paul Shoemaker.
Jerod Brennen created video courses (on LinkedIn Learning) for each domain:
-
Secure Software Concepts Released Feb 12, 2020 (Confidentiality, Integrity, Availability triad, IAM, design)
-
Secure Software Design 1h 48m
-
Secure Software Implementation/Programming
-
Secure Lifecycle Management
-
Secure Deployment, Operations, and Maintenance
-
Supply Chain and Software Acquisition
Quizzing Tests:
-
Kelly Handerhan, the “Mister Rogers of CISSP” “Why you will pass the CISSP” video among her YouTube playlist on cybrary.it which include accompanying mp3 for listening.
-
Official 20-item CSSLP Flashcards on Quizlet vs. 89-item
-
https://github.com/deanbushmiller/CISSP-Bootcamp
-
Pluralsight video courses by Kevin Henry (kevinmhenry at msn) is from 2017 and is too high general for me.
-
On Udemy, McK Thor Pederson courses and 3 sets of 125 questions in 3 hours. Has a Facebook Groups to join: ThorTeaches
-
8 YouTube videos from The Cloud Tech Guy Joe Jan, 2020 talks about the subject rather than taking a deep dive.
-
Practice Exams 2020 by Chandrika Patel
-
Mindmap videos: https://www.youtube.com/channel/UCXk6…
-
$24.99 Cissprep.net Memorisation sheet calls itself “The Best and Most Accurate CISSP Practice Exams” provides Study tips, 28 30-minute quick quizzes, four 1-hour exams, StudyGroup
-
CISSP MasterClass™ Mission by Sagar Bansal
-
https://www.sageknowsit.com/product/ebook-infosec-brain-dump-template$14.99 eBook: InfoSec Brain Dump Template w/Study Schedule
YouTube videos with content index (and ads) by Rob Richa, with John Berti of Destination Certifications:
-
Identity and Assess Management
- Security Architecture and Engineering:
- Models and Frameworks: https://www.youtube.com/watch?v=qZB6_lp9M30&t=30s
- Evaluation Criteria: https://www.youtube.com/watch?v=WqHmDL7YAvw&t=30s
- Trusted Computing Base: https://www.youtube.com/watch?v=fwU7n_3h058&t=30s
- Vulnerabilities in Systems: https://www.youtube.com/watch?v=fPUypU7ysMw&t=30s
- Cloud: https://www.youtube.com/watch?v=-rWQ7YuxiLY&t=30s
- Cryptography: https://www.youtube.com/watch?v=LLRaa0kOMDM&t=30s
- Digital Certificates, Digital Signatures & PKI: https://www.youtube.com/watch?v=8XKdFSG3ua4&t=30s
- Cryptanalysis: https://www.youtube.com/watch?v=pnITDgs63M4&t=30s
- Physical Security: https://www.youtube.com/watch?v=7ESQwNJ9HXU&t=30s
-
Access Control Overview: https://www.youtube.com/watch?v=BUcoABZzeQ4&t=30s Single Sign-on & Federated Access: https://www.youtube.com/watch?v=_U4QMIxVk8M&t=30s
- Security Assessment and Testing Overview: https://www.youtube.com/watch?v=eDVZvw5NziA&t=30s
- Vulnerability Assessment and Penetration Testing: https://www.youtube.com/watch?v=vZ0S8GdWiIk&t=30s
- Logging & Monitoring: https://www.youtube.com/watch?v=cwcARccyWyY&t=30s
- Security Operations:
- Investigations: https://www.youtube.com/watch?v=Urev5cZgny8&t=30s - Locard’s Principle: perp. will leave something behind and take something
- Incident Response: https://www.youtube.com/watch?v=PwxFwndQ7Jk&t=30s
- Malware: https://www.youtube.com/watch?v=SVbrRozyIpo&t=30s
- Patching & Change Management: https://www.youtube.com/watch?v=xX4U6Lz82Bk&t=30s
- Recovery Strategies: https://www.youtube.com/watch?v=DrrfrJBnx28&t=30s
- Business Continuity Management (BCM): https://www.youtube.com/watch?v=oAjNL3I_3-E&t=30s
- Secure Software Development (Lifecycle)
- https://youtu.be/fS5WWjuyFmQ&t=30s
- Databases: https://youtu.be/-70DBd6cNDw&t=30s
Bootcamp: 13 day 2 hours each from April 13, 2020 FRSecure CISSP Mentor Program (12th year) streaming by @evanfrancen. S2me.io
8-hour VIDEO CISSP Exam Cram from Pete Zerger’s Inside Cloud and Security (2022 edition)
Posted by SANS Blue Team Ops:
- CISSP Cram Session Jun 28, 2020. Slides at EricConrad.com, author of MGT414.com: SANS Training Program for CISSP® Certification, as well as the CISSP® Study Guide (Syngress).
- Test-Taking Tactics
Flash cards:
- https://quizlet.com/343215416/csslp-exam-guide-flash-cards/
Suggestions:
-
Ignore the Orange Book. Focus on 15408 Common Criteria on how to build computers based on Bella-Padua.
CCSP
$599 USD CCSP (Certified Cloud Security Professional).
The Aug 2022 upgrade went to 150 questions in 4 hours (from 3). Results are Pass/Fail, but you must score at least 70% in EACH separate vendor neutral domain:
- 17% Cloud Concepts, Architecture and Design
- 19% Cloud Data Security
- 17% Cloud Platform & Infrastructure Security
- 17% Cloud Application Security
- 17% Cloud Security Operations
- 13% Legal, Risk and Compliance
This PDF has the details.
ccsp.alukos.com is a GitBook-formatted listing with glossary of terms, laws by country, standards by each body, frameworks.
-
BOOK: (ISC)2 CCSP Certified Cloud Security Professional Official Study Guide & Practice Tests Bundle by Mike Chapple and David Seidl Nov 1, 2022
On YouTube:
- 12-hour VIDEO CCSP Exam Cram from Pete Zerger’s Inside Cloud and Security (2022 edition)
- YOUTUBE: CCSP Exam Cram series by Prabh Nair
- LinkedIn audio review with practice questions. By Mike Chapple. I recommend this because it has quizzes and shows use of apps such as WebGoat.
- Pluralsight CCSP by Lyron H. Andrews CISSP/CCSP/SSCP/CISM/CCSK
If you have an OReilly.com subscription:
- Live Lessons Video Course
- Video Crash Course by Shannon. “Get the CISSP first”.
-
LiveLessons May 2023 (11 hours) by Shannon
- Audio book by Ben Malisow
- Practice tests 2nd Edition by Ben Malisow
I think ISC2 is too clever with their questions, past the point of making the test as much about knowing the twisted mind of the test maker rather than understanding the underlying material. I wich that ISC2 test writers see “Advanced” level of “knowledge” as higher order thinking (such as evaluation) rather than teasing out twisted meaning of words in tests.
Bragging:
- https://charbelnemnom.com/passed-official-ccsp-exam-certified-cloud-security-professional/
ISACA.org
ISACA.org was created by CISA, a consortium of cloud companies who also maintains a Vulnerability Catalog, the CAIQ, and hold the Digital Trust World conference. It asks for a $50 test application processing fee in addition to USD $145 annual membership fee plus up to $50 monthly local chapter dues. Members get a $185 discount to the $760 online, remotely-proctored exam fee to Pearson Vue. Its website uses Salesforce Authenticator for 2FA. There’s also a $45 annual maintenance fee for each certification, plus $50 for each recertification. And costs for continuing education.
-
CRISC (Certified in Risk and Information Systems Control)</a>
-
CISM (Certified Information Security Manager) VIDEO: Crash SuperReview by Allen Keele of a 40-hour class at certifiedinfosec.com
- 17% Information Security Governance
Organizational Culture
Legal, Regulatory, and Contractual Requirements
Organizational Structure, Roles, and Responsibilties - 20% Information Security Risk Management
- 33% Information Security Program
- 30% Incident Management
Pearson Complete Course for CISM Certification by Sari Greene
- 17% Information Security Governance
Organizational Culture
-
ISO 31000 Internal Controls Risk Analyst (CICRA) VIDEO: Crash SuperReview by Allen Keele
- Certified ISO 22301 Business Continuity Manager
-
Certified ISO 22301 Business Continuity Strategist (CBCS)
-
Certified ISO 37301 Certified Compliance Professional (CCP)
https://www.certifiedinfosec.com/258-44-3-108.html
-
Certified ISO 27001 Lead Implementer, Internal Controls Architect, Lead Auditor (LI/CICA/CLA)
https://www.certifiedinfosec.com/258-35-3-86.html
- CDPSE (Certified Data Privacy Solutions Engineer) covers privacy governance, privacy architecture, data lifecycle
Exec Order 14028 update of 13366
ISACA CSX
ISACA’s Cybersecurity Nexus (CSX) Certificates
Zero Point Security CRTO
The Certified Red Team Operator (CRTO) course and certification is 48 hours of lab time spread across a 4 day event where the student has to find and submit 8 flags (6 flags to pass) within Snap Labs.
https://medium.com/@adamgoss/certified-red-team-operator-crto-review-71ea4edef62a
Offensive Security
Offensive Security is a for-profit company offering courses with labs and certifications:
They offer a $5,499/year bundle for unlimited labs and exam attempts.
-
PEN-300 Advanced Evasion Techniques and Breaching Defenses class to prep for OSEP
-
PEN-103 class to prep for KLCP exam
-
PEN-210 class to prep for OSWP (Wireless Penetration) exam
-
PEN-200 Kali Linux class to prep for $495 OSCP (Certified Professional) is one of the most difficult to pass because it is part “hazing ritual” and part proctored via webcam. It is a 24-hour time-boxed test where you penetrate of as many machines as you can within a massive virtual environment (which includes Active Directory), using Kali Linux. That’s followed by another 24-hour time frame to write (with screenshots) an exam report. You must also pass a background check. The PWK prep course is $1,295. More
-
WEB-200 Kali Linus class for OSWA.
-
OSEE (Offensive Security Exploitation Expert) covers DEP, ASLR evasion, heap spraying, function pointer overwrites. OSEE holders must complete the Advanced Windows Exploitation (AWE) course by Offensive Security held in a live hands-on environment at a Black Hat conference in Las Vegas, NV.
That plus pass a rigorous 72-hour practical exam that includes preparing a comprehensive penetration test report. So this certificate indicates a level of expertise far beyond that of most penetration testers.
Topics tested include: 64-bit Exploitation, Debugging, DEP ByPass, Disarming EMET Mitigations, Exploit Development, Heap Spray, Kernel Driver Exploitation, Kernel Pool Exploitation, Memory Protection Bypass, NX/ASLR Bypass, ROP Chain, Sandbox Escape, Shellcode, WinDBG, Windows Kernel Exploitation. -
Take their web-300 class to get OffSec Web Expert designation. It covers web security testing: XSS attacks, SQL injection, XML external entity injection, Weak random token generation, DOM XSS, Server side template injection, Command injection via websockets (black box material)
-
SOC-200 Foundational Security Operations and Defensive Analysis class for OSDA.
-
EXP-312 Advanced macOS Control Bypasses for OSMR.
-
OSCE was retired. It covered exploits used by attackers to breach security infrastructures.
SANS GIAC
SANS formed the Global Information Assurance Certification (GIAC) program to act as the certification arm for its training courses. GIAC has a roadmap to dozen of exams across eight focus areas. Remote proctoring is offered through ProctorU.
- A. Cybersecurity and IT Essentials
B. Security Management, Legal, and Audit
C. Cyber Defense
D. Cloud Security
E. Digital Forensics, Incident Response & Threat Hunting
F. Offensive Operations, Pen Testing, and Red Teaming
G. Operating System & Device In-Depth
H. Industrial Control Systems Security
GIAC offers two levels: First attempts at the Practitioner level are $979. At the Applied Knowledge level are “GX” or “Experienced” level exams, it’s $1,299 or $499 if a GIAC is active. Retakes are $100 less. Renewals ar $479 at all levels. The exams and classes by 8 focus areas (Cyber Specialities), listed alphabetically:
| Cert | Description | Class | Seq | A. Ess | B. SM | C. CD | D. Cloud | E. IR | F. PT | G. OS | H. ICS |
|---|---|---|---|---|---|---|---|---|---|---|---|
| GASF | Advanced Smartphone Forensics | FOR585: Smartphone Forensic Analysis In-Depth | ? | - | - | - | - | X | - | X | - |
| GAWN | Assessing and Auditing Wireless Networks | SEC617: Wireless Penetration Testing and Ethical Hacking | ? | - | - | - | - | - | X | - | - |
| GBFA | Battlefield Forensics and Acquisition | FOR498: Digital Acquisition and Rapid Triage | ? | - | - | - | - | X | - | X | - |
| GCCC | Critical Controls Certification | SEC566: Implementing and Auditing Security Frameworks and Controls | ? | - | X | - | - | - | - | - | - |
| GCDA | Certified Detection Analyst | SEC555: SIEM with Tactical Analytics | ? | - | - | X | - | - | - | - | - |
| GCED | Certified Enterprise Defender | SEC501 | ? | X | - | X | - | - | - | - | - |
| GCFA | Certified Forensic Analyst | FOR508: Advanced Incident Response, Threat Hunting, and Digital Forensics | ? | - | - | - | - | X | - | - | - |
| GCFE | Certified Forensic Examiner | FOR500: Windows Forensic Analysis | ? | - | - | - | - | X | - | - | - |
| GCFR | Cloud Forensics Responder | FOR509 | ? | - | - | - | X | X | - | - | - |
| GCIA | Certified Intrusion Analyst | SEC503 | ? | - | - | X | - | - | - | - | - |
| GCIH | Certified Incident Handler | SEC504: Hacker Tools, Techniques, and Incident Handling | 3 | X | - | X | - | X | X | - | - |
| GCIP | Critical Infrastructure Protection | ICS456: Essentials for NERC Critical Infrastructure Protection | ? | - | - | - | - | - | - | - | X |
| GCLD | Cloud Security Essentials ? | SEC488 | ? | - | - | - | X | - | - | - | - |
| GCPN | Cloud Penetration Tester | SEC588 | ? | - | - | - | X | - | - | X | - |
| GCPM | GIAC Certified Project Manager | MGT525: Managing Cybersecurity Initiatives & Effective Communication | ? | - | X | - | - | - | - | - | - |
| GCSA | Cloud Security Automation | SEC540 | ? | - | - | - | X | - | - | - | - |
| GCTD | Cloud Threat Detection | SEC541 | - | - | - | X | - | - | - | - | - |
| GCTI | Cyber Threat Intelligence | FOR578 | - | - | - | - | X | - | - | - | </td>- |
| GCWN | Certified Windows (Security) Administrator | SEC505 | ? | - | - | X | - | - | - | - | - |
| GDAT | Defending Advanced Threats | ? | - | - | - | X | - | - | - | - | - |
| GDSA | Defensible Security Architect | SEC530: Zero Trust | ? | - | - | X | - | - | - | - | - |
| GEVA | Enterprise Vulnerability Assessor | - | ? | - | - | - | - | - | X | - | - |
| GFACT | Foundational Cybersecurity Technologies | SEC275 | 1 | - | - | - | X | - | - | - | - |
| GICSP | Global Industrial Cyber Security Professional | ICS410: ICS/SCADA Security Essentials | ? | - | - | - | - | - | - | - | X |
| GIME | iOS and macOS Examiner | FOR518: Mac and iOS Forensic Analysis and Incident Response | ? | - | - | - | - | X | - | - | - |
| GISF | Information Security Fundamentals | SEC301 | 2 | X | - | X | - | - | - | - | - |
| GISP | Information Security Professional | LDR414: SANS Training Program for CISSP® Certification | ? | X | - | X | - | - | - | - | - |
| GLEG | Law of Data Security & Investigations | LEG523 | ? | - | X | - | - | - | - | - | - |
| GMLE | Machine Learning Engineer | SEC595 | ? | - | - | X | - | - | - | - | - |
| GMOB | Mobile (Device Security Analyst) | SEC575: iOS and Android Application Security Analysis and Penetration Testing | ? | - | - | - | - | - | X | - | - |
| GMON | (Continuous) Monitoring | SEC511 | ? | - | - | X | - | - | - | - | - |
| GNFA | Network Forensic Analyst | FOR572: Advanced Network Forensics: Threat Hunting, Analysis, and Incident Response | ? | - | - | - | - | X | - | - | - |
| GOSI | Open Source Intelligence | SEC487 | 4 | - | - | X | - | - | - | - | - |
| GPCS | Public Cloud Security | SEC510 | ? | - | - | - | X | - | - | - | - |
| GPEN | Penetration Tester | SEC560 | ? | - | - | - | - | - | X | - | - |
| GPYC | Python Coder | SEC573: Automating Information Security with Python | ? | - | - | - | - | - | X | - | - |
| GREM | Reverse Engineering Malware | FOR610 | ? | - | - | - | - | X | - | - | - |
| GRID | Response and Industrial Defense | ICS515: ICS Visibility, Detection, and Response | ? | - | - | - | - | X | - | - | X |
| GRTP | Red Team Professional | SEC565: Red Team Operations and Adversary Emulation | ? | - | - | - | - | - | X | - | - |
| GSEC | Security Essentials | SEC401 | 3 | X | - | X | - | - | - | - | - |
| GSLC | Security Leadership | MGT512: Leadership Essentials for Security Managers | ? | - | X | - | - | - | - | - | - |
| GSNA | Systems and Network Auditor | AUD507: Auditing Systems, Applications, and the Cloud | ? | - | X | - | - | - | - | - | - |
| GSOC | Security Operations Certified | SEC450: Blue Team Fundamentals: Security Operations and Analysis | ? | - | - | X | - | - | - | - | - |
| GSOM | Security Operations Manager | LDR551: Building, Leading, & Managing (SOC) Security Operations Center | ? | - | - | X | - | - | - | - | - |
| GSTRT | Strategic Planning, Policy, and Leadership | MGT514 | ? | - | X | - | - | - | - | - | - |
| GWAPT | Web Application Penetration Tester | SEC542 | ? | - | - | - | - | - | X | - | - |
| GWEB | Web Application Defender | SEC522 | ? | - | - | - | X | - | - | - | - |
| GXPN | Exploit Researcher and Advanced Penetration Tester | SEC660: Advanced Penetration Testing, Exploit Writing, and Ethical Hacking | ? | - | - | - | - | - | X | - | - |
https://www.sans.org/cyber-academy/vetsuccess/ 100% scholarship for US veterans - 9 months to complete 3 courses
foundation & SAN275
“Applied Knowledge” level exams are named with “GX-“ and “Experienced” in their name:
| Cert | Description | Class | A. Ess | B. SM | C. CD | D. Cloud | E. IR | F. PT | G. OS | H. ICS |
|---|---|---|---|---|---|---|---|---|---|---|
| GX-PT | Experienced Penetration Tester | - | - | - | - | - | - | X | - | - |
| GX-FA | Experienced Forensic Analyst | - | - | - | - | - | X | - | - | - |
| GX-IH | Experienced Incident Handler | - | - | - | X | - | - | - | - | - |
| GX-CS | Experienced Cyber Security | - | - | - | X | - | - | - | - | - |
| GX-IA | Experienced Intrusion Analyst | - | - | - | - | - | - | X | - | - |
Based on the NICE framework
-
GEVA (GIAC Enterprise Vulnerability Assessor) requires 71% correct from among 75 questions over 2 hours. It covers Vulnerability assessment framework planning and methodology in an enterprise environment; Discovery and validation of vulnerabilities using tactics like network scanning and PowerShell scripting; Remediation and reporting techniques utilizing proper data management
-
GCIH (GIAC Certified Incident Handler) requires an undeterminate correct from among 100-150 questions over 4 hours. It covers Incident Handling (Response) and Computer Crime Investigation; Computer and Network Hacker Exploits; Hacker Tools (Nmap, Nessus, Metasploit, Netcat). A single chapter on NIST800-61.
-
GCED (GIAC Certified Enterprise Defender) requires 70% correct from among 115 questions over 3 hours. It covers Incident handling and computer crime investigation; Computer and network hacker exploits; Hacker tools (Nmap, Nessus, Metasploit and Netcat)
-
GSE (GIAC Security Expert) is the premier security-related certification available today. After you score at least the gold level in 2 of 3 tests above, you take a multiple-choice test, then a hands-on lab (not available due to COVID). The proctored Exam has Minimum Passing Score of 64% to 24 VM-based Hands-On Questions with a 3-Hour Time Limit.
CompTIA
So compliance with DoD 8570-2005 retired by NIST DoD Directive 8140.01 means job candidates need to have passed to it to just apply for some government jobs. DoD 8140 expands on DoD 8570 to leverage the Defense Cybersecurity Workforce Framework (DCWF), which draws from the original National Initiative for Cybersecurity Education (NICE) Cybersecurity Workforce Framework (NCWF) and DoD Joint Cyberspace Training and Certification Standards (JCT&CS).
CompTIA certifications were designed for compliance with ISO 17024 standards and approved by the US DoD to meet directive 8140/8570.01-M requirements. Regulators and government rely on ANSI accreditation, because it provides confidence and trust in the outputs of an accredited program. Over 2.3 million CompTIA ISO/ANSI-accredited exams have been delivered since January 1, 2011.
Security+
Security+ exam SY0-601 at comptia.org/certifications/security is described an “entry level” exam. But its detailed coverage of some obscure encryption protocols and tricky questions make it difficult even for professionals.
NOTE: I first answered over 75% the 90-question Security+ March 2020 after studying literally 4 years, on and off. I held off due to its $392 test fee plus annual renewal fees. PROTIP: They offer a $49 annual Club for a $78 discount (20% off all CompTIA products). Students get a 40% discount at a different website.
What helped me get over the intimidation is to seek out the trick questions and delight in them as an intellectual curiosity.
- CompTIA Security+ SY0-601 Cert Guide, 5th Edition by Omar Santos, Ron Taylor, Joseph Mlodzianowski.
PROTIP: If you have an OReilly subscription, Pearson Practice Test provides filtering to individual exam topic category objectives:
- Social Engineering Techniques - 17
- Attack Basics - 23
- Application Attacks - 20
- Network Attacks
- Threat Actors, Vectors, and Intelligence Sources
- Vulnerabilities
- Security Assessment Techniques
- Penetration Testing Techniques
- Enterprise Security Concepts
- Virtualization and Cloud Computing
- Secure Application Development, Deployment, and Automation
- Authentication and Authorization Design
- Cybersecurity Resilience
- Embedded and Specialized Systems
- Physical Security Controls
- Cryptographic Concepts
- Secure Protocols
- Host and Application Security Solutions
- Secure Network Design
- Wireless Security Settings
- Secure Mobile Solutions
- Cloud Cybersecurity Solutions
- Identity and Account Management Controls
- Authentication and Authorization Solutions
- Public Key Infrastructure
- Organizational Security
- Incident Response
- Incident Investigation
- Incident Mitigation
- Digital Forensics
- Control Types
- Regulations, Standards, and Frameworks
- Organizational Security Policies
- Risk Management
- Sensitive Data and Privacy
PROTIP: Security+ is vendor-neutral, but to be useful on the job, get trained in specific tools and in cloud computing as well.
Concepts in the five exam objectives are covered in videos by Professor Messer on YouTube:
- VIDEO: Threats, Attacks, and Vulnerabilities
1.1 – Social Engineering
1.2 – Attack Types
1.3 – Application Attacks
1.4 – Network Attacks
1.5 – Threat Actors and Vectors
1.6 – Vulnerabilities
1.7 – Security Assessments
1.8 – Penetration Testing - VIDEO: Architecture and Design
2.1 – Enterprise Security
2.2 – Virtualization and Cloud Computing
2.3 – Secure Application Development
2.4 – Authentication and Authorization
2.5 – Resilience
2.6 – Embedded Systems
2.7 – Physical Security Controls
2.8 – Cryptographic Concepts - VIDEO: Implementation
3.1 – Secure Protocols
3.2 – Host and Application Security
3.3 – Secure Network Designs
3.4 – Wireless Security
3.5 – Mobile Security
3.6 – Cloud Security
3.7 – Identity and Account Management
3.8 – Authentication and Authorization Services
3.9 – Public Key Infrastructure - VIDEO: Operations and Incident Response
4.1 – Security Tools
4.2 – Incident Response
4.3 – Investigations
4.4 – Securing an Environment
4.5 – Digital Forensics - VIDEO: Governance, Risk, and Compliance (GRC)
5.1 – Security Controls
5.2 – Regulations, Standards, and Frameworks
5.3 – Organizational Security Policies
5.4 – Risk Management
5.5 – Data Privacy
Josh Madakor of Seattle (a 2020 Western Governors University graduate) offers visitors to his YouTube free 1000 question deck presented by the free Anki Q&A app. NOTE: There is an brew install anki-beta
It references Professor Messer. Also, it’s a teaser for his $497 SOC Analyst video training using Azure cloud hands-on (built using ChatGPT). Topics include building a mini-SOC and other aspects of your security portfolio of NIST 800-53 policies, to apply for a job.
VIDEO: 20-hour CompTIA Security+ Exam Cram - SY0-601 (Full Training Course - All 5 Domains) by Pete Zerger
Among OReilly.com’s prep resources
CompTIA PenTest+
https://www.whizlabs.com/comptia-pentest/
CompTIA CASP+
For those who have pass CompTIA Network+ and Security+ certifications:
CompTIA CASP+ (CompTIA Advanced Security Practioner) exam CAS-004 is for practitioners — not managers — at the advanced skill level of cybersecurity – implementing solutions policies and frameworks.
CASP+ satisfies Baseline Certification for DoD IAT (Information Assurance Technical) Level III, IAM (Information Assurance Management) Level II, and IASAE (Information Assurance Security Architecture and Engineering) level I and II jobs.
Performance-based questions (PBQs) test a candidate’s ability to solve problems in a simulated environment that approximates a virtual environment with a firewall, network diagram, terminal window, or operating system.
At $396 for CompTIA members or $466 USD (or $799 with retake and $849 with Labs), you’ll have 165 minutes (2.5 hours) to answer 90 multiple-choice and “hands-on, performance-based” questions, for pass/fail grading. The domains:
- 19% Risk Management
- 25% Enterprise Security Architecture
- 20% Enterprise Security Operations
- 23% Technical Integration of Enterprise Security
- 13% Research, Development, and Collaboration
-
Risk Management
1: Business and Industry Influences and Risks
2: Organizational Security Privacy Policies and Procedures
3: Risk Mitigation Strategies and Controls
4: Risk Metric Scenarios for Enterprise Security
-
Enterprise network and Security Architecture
5: Integrating Network and Security Components, Concepts, and Architectures
6: Integrating Security Controls for Host Devices
7: Integrating Controls for Mobile and Small Form Factor Devices
8: Selecting Software Security Controls
-
Enterprise Security Operations
9: Conducting Security Assessments
10: Selecting the Proper Security Assessment Tools
11: Implementing Incident Response and Recovery
-
Technical Integration of Enterprise Security
12: Integrating Hosts, Storage, and Applications in the Enterprise
13: Integrating Cloud and Virtualization Technologies in the Enterprise
14: Integrating and Troubleshooting Advanced AAA Technologies
15: Implementing Cryptographic Techniques
16: Secure Communication and Collaboration Solutions
-
Research, Development and Collaboration
17: Applying Research Methods for Trend and Impact Analysis
18: Implementing Security Activities Across the Technology Life Cycle
19: Interacting Across Diverse Business Units
PROTIP: 12 Flash cards Sample:
-
To check config on RedHat 5.5:
chkconfig --test
-
Services to disable on DNS:
http, mysqld, lopd, bluetooth, wpa supplicant
-
To stop service:
service httpd stop
CASP+ Practice Tests by Nadean H. Tanner (at Puppet, Metasploit)
- Exploit-Exercises.com provides virtual machines, documentation, and challenges covering a wide range of security issues.
- hacking-lab.com/index.html provides capture-the-flag (CTF) exercises in a variety of fields.
- www.owasp.org/index.php/OWASP_Hacking_Lab OWASP Hacking Lab provides excellent web application–focused exercises.
- PentesterLab provides subscription-based access to penetration testing exercises
O’Reilly Live Video Crash Course by Dean Bushmiller of expandingsecurity.com. Refrence: https://github.com/deanbushmiller/O-CASPv3/wiki from https://github.com/deanbushmiller/O-CASPv3
video 18+ hours released Jan. 2018 by Michael J. Shannon:
Kelly Handerhan’s Cybrary videos
CASP CAS-003 help on Reddit (archived)
Ucertify has good labs
Sybex book has labs as well
Udemy video “Prepatory course for the exam CAS-003”
- Understanding Risk Management - 2hr 22min QUIZ
- Network and Security - 1hr 55m QUIZ
- Implementing Advanced Authentication and Cryptographic Techniques - 1hr 46min QUIZ
- Implementing Security for Systems, Applications, and Storage - 2hr 23min QUIZ
- Implementing Security for Cloud and Virtualization Technologies - 1hr 45min QUIZ
- Utilizing Security Assessments and Incident Response - 1hr 42min QUIZ
The Official CompTIA CASP+ Self-Paced Certification Study Guide (Exam CAS-003) Paperback by Jason Nufryk is $219.00
Notes:
Memory dump tools: Memdump, KnTTools on Windows, FATKit
Runtime Debugging: AddressSanitizer, C# Deleaker, Software Verify
Attestation provides evidence about a target to an appraiser so that policy compliance can be determined prior to authorization of access.
The Annualized Loss Expectancy (ALE) is the product of the Annual Rate of Occurrence (ARO) multiplied by the Single Loss Expectancy (SLE).
Bluesnarfing is the unauthorized access of a device by an attacker who is trying to access information on the device.
Hyperconvergence takes convergence a step further by utilizing software to perform integration without requiring hardware changes.
CompTIA CySA+
CompTIA CySA+ “Security Analyst” exam launched April 21, 2020 on Vue & Pearson online $359 to answer 75% of 85 questions in 165 minutes.
- Version CSO-002 was retired December 2023
- Version CSO-003 launches June 6, 2023
-
Threat and vulnerability management:
- Explain the importance of threat data and intelligence.
- Given a scenario, utilize threat intelligene to support organizatoinal security.
- Given a scenario, perform vulnerability management activities.
- Given a scenario, analyze the output from common vulnerability assessment tools.
- Explain the threats and vulnerabilities associated with operating in the cloud.
- Given a scenario, implement controls to mitigate attacks and software vulnerabilities.
- Software and systems security
- Given a scenario, apply security solutions for infastructure management
- Explain software assurance best practices
- Explain hardware assurance best practices
- Security operations and monitoring:
- Given a scenario, analyze data as part of security monitoring activities.
- Given a scenario, implement configuration changes to existing controls to improve security.
- Explain the importance of proactive threat hunting.
- Compare and contrast automation concepts and technologies.
- Incident response
- Explain the importance of the incident response process.
- Given a scenario, apply the appropriate incident response procedure.
- Given an incident, analyze potential indicators of compromise.
- Given a scenario, utilize basic digital forensics techniques.
- Compliance and assessment
- Understand the importance of data privacy and protection
- Given a scenario, apply security concepts in support of organizational risk mitigation
- Explain the importance of frameworks, policies, procedures and controls.
Training:
- https://app.cybrary.it/browse/course/comptia-cysa is 35 hours FREE but $59/mo
- Udemy course
Cisco
Cisco (the networking company) has several certifications attained by 4,000 people world-wide:
- CCNA Associate
- Cisco CyberOps: Associate, Professional (no Expert yet)
-
Cisco DevNet: Associate, Professional, Expert
- CCNP Enterprise and CCIE (Expert level) Enterprise Infrastructure, Enterprise Wireless
- CCNP and CCIE: Security, Collaboration, Data Center, Service Provider
The prerequisite is earning the Cisco Certified Specialist - Security Core certification by passing the their 120-minute $400 350-701 SCOR Cisco Security Core Technologies exam.
- https://learningnetwork.cisco.com/s/scor-exam-topics
-
Cisco has a FREE Implementing and Operating SCOR 1.0 prep. class:
- Network Security Concepts 1h 15m
- Network Security Controls 8h 45m
- Endpoints and Systems 2h 30m
- Identity Access Management 1h
- Secure Transport 8h 45m
- Secure Network Infrastructure and Telemetry 3h
- Cloud Security Concepts 1h 30m
- Security Automation 1h
Talos (formerly Thousand Eyes) Intelligence Group</a> security intelligence feed [Wikipedia]
- 22-hour YouTube course by Ratner Part 1
- 30-hour $50 video course by Sikandar Shaik on Udemy
- 36-hour $50 CBTNuggets video class
- https://www.linkedin.com/learning/paths/ccnp-security-prepare-for-the-implementing-and-operating-cisco-security-core-technologies-350-701-scor-exam
INE eLearnSecurity
INE offers several certifications:
- eJPT
- eCDFP $199.50
- eCIR $200
- eCPPT $200
- eCTHP $200
- eMAPT $200
- eWPTX $200
eJPT
eJPT (eLearnSecurity’s Junior Penetration Tester) is an entry-level hands-on exam to prove that the individual has the knowledge, skills, and abilities required to be a junior Red Team penetration tester on real-world engagements. For $299, candidates have two-attempts at using their 5 machines over 48 hours (two days) to answer 35 questions about enumerating, exploiting, pivoting, and possibly escalating privileges. One candidate said he passed in 6 hours. The fee includes a course with 145+ hours of video content and 121 labs.
- Locate endpoints on a network
- Identify open ports and services on a target
- Identify operating system of a target
- Extract company information from public sources
-
Gather email addresses from public sources
- Gather technical information from public sources
- Identify vulnerabilities in services
- Evaluate information and criticality or impact of vulnerabilities
- Compile information from files on target
-
Enumerate network information from files on target
- Enumerate system information on target
- Gather user account information on target
- Transfer files to and from target
- Gather hash/password information from target
-
Identify and modify exploits
- Conduct exploitation with metasploit
- Demonstrate pivoting by adding a route and by port forwarding
- Conduct brute-force password attacks and hash cracking
-
Identify vulnerabilities in web applications
- Locate hidden file and directories
- Conduct brute-force login attack
-
Conduct web application reconnaissance
- OSSTMM vs OWASP
- https://security.ine.com/certifications/ejpt-certification/
EC-Council Penetration Tester
EC-Council (International Council of E-Commerce Consultants) is based in Malaysia. Since 2001 it offers 3 levels of certification. See https://cert.eccouncil.org/faq.html
- CEH = Certified Ethical Hacker
- CPENT / ECSA
- Expert Level is LPT: Licensed Penetration Tester [Master]
33% off until Dec 31.
CEH Certified Ethical Hacker
Now at v12, as defined by https://www.eccouncil.org/programs/certified-ethical-hacker-ceh asks 125 multiple-choice questions in 4 hours. Most questions is select from 4 options.
The $1,100 exam is proctored by ECC EXAM (as 312-50) and Pearson VUE (as 312-50), courseware is discounted to $850, with upgrade for VUE exam for $100. from “Aspen iLabs”.
NOTE: The CompTIA PenTest+ is cheaper and doesn’t require 2 years of experience.
Before applying for the exam, ask for a “direct exam” when providing who will verify your experience at https://cert.eccouncil.org/Exam-Eligibility-Form.html and pay $100 to apply at https://store.eccouncil.org/product/eligibility-application-fee/
The form needs to be printed, signed, scanned to a PDF, then emailed.
Don’t pay for the exam until you get approval.
Exam Brochure: https://www.eccouncil.org/wp-content/uploads/2016/07/CEHv10-Brochure.pdf
CEH Candidate Handbook: https://s3-us-west-2.amazonaws.com/edm-image/documents/CEH-Handbook-v2.2.pdf
Blueprint: https://cert.eccouncil.org/images/doc/CEH-Exam-Blueprint-v2.0.pdf
Dean Bushmiller’s “in 2 week” Live Video Course on OReilly.com with GitHub
“Footprinting” is a term EC-Council invented as aka for “reconnaissance”.
CPENT / ECSA
The Advanced level is ECSA: Security Analyst https://www.eccouncil.org/programs/certified-security-analyst-ecsa-practical/ is being phased out in Oct. 2020 in favor of the CPENT (Certified Penetration Testing Professional).
Covers “double pivoting”.
$2199 w/ training, $799 for challenge.
LPT
At the Expert Level is LPT: Licensed Penetration Tester [Master] https://www.eccouncil.org/programs/licensed-penetration-tester-lpt-master/ with training via CPENT.
EC-Council
EC-Council built the Advanced Penetration Testing Cyber Range (ECCAPT).
APISec University
APISec.ai launched from San Francisco August 2022 at +1 415.236.0601 (Twitter: apisecu, LinkedIn, YouTube, Discord) provides FREE training on a list of security-related tools that includes their own API scanner running a sample netbanking app [demo].
APIsec Con with APIDays Paris, France in December 8, 2023. shelby@apisec.ai.
Register to attend at https://university.apisec.ai/library. Each course has quizzes and a certificate of completion.
By Dan Barahona (founder):
-
2 CPE API Security Fundamentals
VIDEO:
If you’re new to API security, this is the place to start. Learn about the OWASP API Top 10, real-world API breaches and more.
-
2 CPE OWASP API Top 10 & Beyond! - Build your API security foundation with a strong understanding of the OWASP API Top 10.
-
1 CPE (60-minute) API Security for PCI Compliance examines the new PCI DSS (Data Security Standard) v4.0 requirements and details the API security obligations for compliance.
By Jason Harmon of #APIIntersection podcast:
-
2 CPE API Documentation Best Practices - Strong API security starts with great API documentation. Learn the best practices, tools & techniques.
Webinar: Why API Documentation Drives API Security 2 by Dan Barahona with Jason Harmon of Stoplight and Alex Savage.
-
2 CPE Securing API Servers by Anthony Arague - Learn key concepts for keeping API servers secure - from CORS to error handling to rate limiting and more.
VIDEO: PCI DSS 4.0 Requirements for API Security
VIDEO: API Security Requirements for PCI-DSS 4.0
Sample API configuration (for Node.js Express server by Helmet taught at FreeCodeCamp InfoSec):

By Corey Ball (author of Hacking APIs:
-
12 CPE API Penetration Testing - Learn how to hack APIs like a professional penetration tester and find vulnerabilities.
VIDEO: Lab Setup and API Reconnaissance
The course covers use of VMWare player playing a 4GB VMWare image containing Kali Linux VM bridged for direct connect. Default credentials kali/kali. Burp Suite, and Postman.
-
1 CPE (60 minute) API Security for Connected Cars and Fleets - Understand why attackers are targeting connected car and fleet APIs (telematics) and how to keep them secure. Includes real-world examples and quiz. Developed by Tom Kaplan @UpstreamAuto (XDR).
CASA
The $150 CASA (Certified API Security Analyst) exam from APISec University is 100 questions online to “demonstrate your API security expertise.”
ASCP
The $650 API Security Certified Professional exam from APISec University is earned by capturing 6 of 8 flags to “prove your API hacking skills. Perform a penetration test of two API-driven applications by discovering vulnerabilities, exploiting weaknesses, and reporting your findings.”
Prepare for it by taking APISec University’s API Penetration Testing course.
IIBA Cybersecuity Analysis
IIBA, the International Institute of Business Analysis (Pickering, Ontario, Canada), has an affiliation with the IEEE. Membership costs $139/year. For $250 until Oct 31, 2022 then $400/$475 for members/non-members, it offers the CCA (Certification in Cybersecurity Analysis) among its 6 other certifications administered online by PSI. IIBA does not disclose the score needed to pass, scores attained, nor scoring percentages.
As of Aug 2022, 266 CCA attendees had 90 minutes to answer 75 multiple-choice questions in these Knowledge Areas:
- Cybersecurity Overview and Basic Concepts 14%
- Enterprise Risk 14%
- Cybersecurity Risks and Controls 12%
- Securing the Layers 5%
- Data Security 15%
- User Access Control 15%
- Solution Delivery 13%
- Operations 12%
AWS Security
See my notes at https://wilsonmar.github.io/aws-security
Microsoft SC-900 & AZ-500
PDF: Updated Jan 21, 2021 Microsoft’s AZ-500 Azure Security Technologies Associate online exam for people who maintain security posture, identify and remediate vulnerabilities by using a variety of security tools, implement threat protection, and respond to security incident escalations. Domains:
- Manage Identity and Access (30-35%)
- Implement Platform Protection (15-20%)
- Manage Security Operations (25-30%)
- Secure data and applications (20-25%) (Policy and Data Infrastucture & Data at Rest, App Security, Key Vault)
It costs $165 to Pearson Vue, less if you’re a certified trainer or in the esi.microsoft.com/getcertification, which has practice tests from MeasureUp.
Prequisite is certification as either:
or
- Microsoft Certified: Azure Developer Associate exam AZ-204 “Developing Solutions for Microsoft Azure”.
Microsoft’s learning paths for AZ-500 :
-
Secure your cloud applications in Azure 6 Modules - 5 hr 36 min
- Microsoft Azure Well-Architected Framework - Security - 1 hr 2 min
- Top 5 security items to consider before pushing to production - 45 min
- Create security baselines - 1 hr
- Manage secrets in your server apps with Azure Key Vault - 46 min
- Secure an ASP.NET Core web app with the Identity framework - 1 hr 8 min
- Control authentication for your APIs with Azure API Management - 55 min
-
Implement resource management security in Azure 6 Modules - 3 hr 27 min
- Protect against security threats on Azure - 25 min
- Build a cloud governance strategy on Azure - 48 min
- Control and organize Azure resources with Azure Resource Manager - 46 min
- Secure your Azure resources with Azure role-based access control (Azure RBAC) - 37 min
- Manage access to an Azure subscription by using Azure role-based access control (Azure RBAC) - 21 min
- Create custom roles for Azure resources with role-based access control (RBAC) - 30 min
-
Implement network security in Azure 5 Modules - 5 hr 8 min
- Secure network connectivity on Azure - 32 min
- Configure the network for your virtual machines - 1 hr 34 min
- Secure and isolate access to Azure resources by using network security groups and service endpoints - 43 min
- Encrypt network traffic end to end with Azure Application Gateway - 1 hr 17 min
- Monitor and troubleshoot your end-to-end Azure network infrastructure by using network monitoring tools - 1 hr 2 min
-
Implement virtual machine host security in Azure 6 Modules - 6 hr 4 min
- Microsoft Azure Well-Architected Framework - Security - 1 hr 2 min
- Create security baselines - 1 hr
- Create a Linux virtual machine in Azure - 1 hr 26 min
- Create a Windows virtual machine in Azure - 51 min
- Secure your Azure virtual machine disks - 1 hr 1 min
- Protect your servers and VMs from brute-force and malware attacks with Azure Security Center - 44 min
-
Manage identity and access in Azure Active Directory 9 Modules - 5 hr 17 min
- Protect against security threats on Azure - 25 min
- Create an Azure account - 39 min
- Manage users and groups in Azure Active Directory - 50 min
- Create Azure users and groups in Azure Active Directory - 41 min
- Secure your application by using OpenID Connect and Azure AD - 50 min
- Secure Azure Active Directory users with Multi-Factor Authentication - 38 min
- Manage device identity with Azure AD join and Enterprise State Roaming - 25 min
- Allow users to reset their password with Azure Active Directory self-service password reset - 31 min
- Add custom domain name to Azure Active Directory - 18 min
-
Manage security operations in Azure 8 Modules - 6 hr
- Protect against security threats on Azure - 25 min of tailwindtraders.com. Its security posture is monitored using Azure Security Center adaptive application controls to define rules for secure score. Azure Logic Apps and Security Center connectors. Azure Sentinel SIEM using Common Event Format (CEF) messaging standard, Syslog, or REST API.
- Create security baselines - 1 hr
- Identify security threats with Azure Security Center - 43 min
- Resolve security threats with Azure Security Center - 44 min
- Protect your servers and VMs from brute-force and malware attacks with Azure Security Center - 44 min Security Center uses network security group (NSG) rules to restrict access to management ports when not in use.
- Analyze your Azure infrastructure by using Azure Monitor logs - 36 min
- Improve incident response with alerting on Azure - 53 min
- Capture Web Application Logs with App Service Diagnostics Logging - 55 min
https://microsoft.github.io/AzureTipsAndTricks/
https://cloudacademy.com/learning-paths/az-500-exam-preparation-microsoft-azure-security-technologies-650/
VIDEO: DOCS: Microsoft Threat Modeling Tool
Well Architected Framework
The Microsoft Azure Well-Architecture Framework 5 pillars are the same as Amazon’s:
- Cost Optimization - Managing costs to maximize the value delivered.
- Operational Excellence - Operations processes that keep a system running in production.
- Performance Efficiency - The ability of a system to adapt to changes in load.
- Reliability - The ability of a system to recover from failures and continue to function.
- Security - Protecting applications and data from threats.
Peter Zerger (@pzerger) :
CloudAcademy.com 16h video series by Thomas Mitchell
McK Udemy.com “updated 2020” 15.5h videos by Alan Anthony Rodrigues
Other videos:
-
https://zimmergren.net/passing-az-500-microsoft-certified-azure-security-engineer-associate/
-
https://www.pluralsight.com/courses/microsoft-azure-incident-response-remediation
-
https://blog.ahasayen.com/az-500-azure-security-engineer-exam/
Google Professional Cloud Security Engineer, for $200 for 50 questions in 120 minutes, will have obtained the skills to “enable organizations to design and implement a secure infrastructure on Google Cloud Platform. Through an understanding of security best practices and industry security requirements, this individual designs, develops, and manages a secure infrastructure leveraging Google security technologies. Topics and skills:
- Configure access within a cloud solution environment
- Configure network security
- Ensure data protection
- Manage operations within a cloud solution environment
- Ensure compliance
SAP
First, memorize SAP Acronyms using my flashcards on Quizlet.com
SAP has two levels of certifications for Security pros. Both costs $242 USD to answer 65% of 80 multiple-choice questions in 3 hours.
-
C_SECAUTH_20 SAP Certified Technology Associate - SAP System Security and Authorizations Domains:
- Authorization and Role Maintenance - >12%
- SAP Fiori Authorizations and S/4HANA - >12%
- Access Governance and Compliance in SAP - 8%-12%
- Infrastructure Security and Authentication - 8%-12%
- User Administration8% - 12%
- Security Monitoring and Security Assessment8% - 12%
- Data Privacy Governance and Cybersecurity8% - 12%
- Security Audit - 8%-12%
-
P_TSEC10_75 SAP Certified Technology Professional - System Security Architect is the most popular among all SAP exams.
- SAP System Security Fundamentals - >12%
- Authorization Concept for SAP Business Suite - >12%
- Authorization Concept for SAP S/4HANA - >12%
- Secure SAP System Management - >12%
- SAP Netweaver Application Server Security - >12%
- Authorization, Security and Scenarios in SAP HANA8% - 12%
-
Security in SAP Gateway and SAP Fiori System Landscape - < 8%
- https://myerp-training.com/sap-security-certification/
- After passing, post your cert on Credly
- $606 USD CER006 C_GRCAC_12 SAP GRC (Governance, Risk, and Compliance) AC certification exam
- https://training.sap.com/trainingpath/Applications-Governance,+Risk+and+Compliance+(GRC)-SAP+BusinessObjects
- https://training.sap.com/trainingpath/Applications-Governance,+Risk+and+Compliance+(GRC)-SAP+BusinessObjects
- SAP provides a 14 day free trial of their $25/month Learning Hub (using an “S-account”) at https://learninghub.sap.com/. 800-872-1727
Elsewhere:
- https://www.udemy.com/course/sap-security-and-authorizations/
- https://www.udemy.com/course/sap-hana-installation-operation-and-administration/
Secure Coding
CodeBashing.com (by security tools vendor Checkmarx) has gamified tutorials on identifying and mitgating vulnerabilities in code for many languages: Hacking Headlines, Source Code (for each language): Android (Java), iOS, C/C++, C# .NET, .NET Backend, .NET Advanced, Go, Java, Java Backend, Java Advanced, Scala NodeJS, PHP, Python Django, Ruby on Rails,
Networking (Firewall) certs
Network software vendors have affordable certifications:
- $100 Palo Alto Networks Certified Cybersecurity Associate (PCCSA)
- $140 Palo Alto Networks Certified Network Security Administrator (PCNSA)
-
$400 Palo Alto Networks Certified Network Security Engineer (PCNSE)
- $135 F5 Big-IP Certified Solution Expert - Security (F5 CSE Sec)
- $135 F5 Big-IP Certified Technical Specialist - Access Policy Manager (F5 CTS APM)
-
$135 F5 Big-IP Certified Technical Specialist - Domain Name Services (F5 CTS DNS)
- $200 Juniper Networks Certified Internet Associate Security (JNCIA Sec)
- $400 Juniper Networks Certified Internet Professional Security (JNCIP Sec)
-
$300 Juniper Networks Certified Internet Specialist Security (JNCIS Sec)
- $250 Checkpoint Certified Security Administrator (CCSA)
- $250 Checkpoint Certified Security Expert (CCSE)
- $400 NSE 4 - FortiNET Network Security Professional (NSE 4)
- $400 NSE 7 - FortiNET Network Security Architect (NSE 7)
-
$2,050 Cisco Certified Implementation Expert - Security (CCIE Sec)
- $130 Splunk Enterprise Security Certified Administrator (Splunk ECSA) - 61 questions in 60 minutes
TCM Academy
TCM Academy is a for-profit entity which makes money by providing both training and certification on generic security topics, from $24.99/month, plus the cost of online certification exams:
Entry-Level Certifications:
-
$199 PJPT (Practical Junior Penetration Tester) assesses the ability of a beginner-level student’s ability to perform an internal network penetration test at an associate level. Students have two (2) full days to complete the assessment and an additional two (2) days to write a professional report.
-
$199 PJWT (Practical Junior Web Tester) assessing a beginner-level student’s ability to perform a web application penetration test at an associate level.
-
$199 PJMT (Practical Junior Mobile Tester) assesses a student’s ability to perform mobile application penetration tests at a junior level.
Intermediate-Level Certifications:
-
$999 PNPT (Practical Network Penetration Tester) simulates a real-world pentest engagement from start to finish.
-
$199 PJMR (Practical Junior Malware Researcher) is focused on Malware Analysis, Research, and Triage, assessing the mastery of the art and science of malware analysis.
-
$199 PCRP (Practical Career-Ready Professional) is a real-world job application and interview experience. Students will learn practical soft and communication skills that employers are looking for combined with personal branding and stand-out skills.
OSIP (Open Source Intelligence Professional)
The OSIP (Open Source Intelligence Professional) Certification on OSINT (Open Source Intelligence) by inteltechniques.net is offered for $300 or $949 which includes their $649/year videos and 600+ page pdf.
by Michael Bazzell, blogger. Previously FBI, Technical Advisor/Writer for the television show Mr. Robot and host to the now-defunct podcast inteltechniques.com
References
On Udemy: McK Security Product Lifecycle 101 (SPLC) by Implementing Security. Voiced by an enthusiastic voice pro. References SAMM 2.0, OWASP Top 10.
-
Data-Driven Security (Pearson) by Jacobs and Rudis
Podcast: Evan Francen’s Unsecurity
TOP 5 Cyber Security Projects to go on Your Resume! by Josh Madakor
- Simple REST API
- SIEM in Azure Sentinel
- Active Directory environment
- File Integrity Monitor
- Vulnerability Management Lab
Azure Service Operator (ASO) Fabrikam Fabric Store
Movies
https://www.magellantv.com/series/secret-wars
More on Security
This is one of a series on Security and DevSecOps:
- Security actions for teamwork and SLSA
- Code Signing on macOS
- Git Signing
- GitHub Data Security
- Azure Security-focus Cloud Onramp
- AWS Onboarding
- AWS Security (certification exam)
- AWS IAM (Identity and Access Management)
- SIEM (Security Information and Event Management)
- Intrusion Detection Systems (Goolge/Palo Alto)
- SOC2
- FedRAMP
-
CAIQ (Consensus Assessment Initiative Questionnaire) by cloud vendors
- AKeyless cloud vault
- Hashicorp Vault
- Hashicorp Terraform
- SonarQube
- WebGoat known insecure PHP app and vulnerability scanners
- Security certifications
- Quantum Supremecy can break encryption in minutes
- Pen Testing
- Threat Modeling
- WebGoat (deliberately insecure Java app)


