How to setup Google IDS to send your VM traffic to Palo Alto’s Unit 42 security pros who alert your SIEM based on their malware signatures
Overview
Why an Intrusion Detection System?
If even the NSA, Equifax, and others (with a lot of people protecting their data) have been hacked, it’s a question of time before someone accesses your data without permission. Even if you have proven that your backups can be restored in a timely manner, you need alerts from an Intrusion Detection System to know when to reset passwords and fall back on backups.
This is about immediately identifying and responding to threats on your network.
Among PCI compliance validation PDF are:
- \5. Protect all systems against malware and regularly update anti-virus software.
\10. Track and monitor all access to network resources and cardholder data.
\11. Regularly test security systems and processes.
Cloud IDS provides the evidence that auditors review as the basis for issuing an annual Report on Compliance (ROC), which include:
- Examine documentation
- Interview personnel
- Examine/observe live data
- Observe processes being performed (of quarterly scan results)
- Observe the physical environment
- Interactive testing
What’s This?
Here is a hands-on introduction to Intrusion Detection on the Google Compute Platform (GCP). TODO: In the future I’ll add here how other cloud vendors implement their IDS, for comparison.
PROTIP: Included are Organizational Change Management tips to minimize resistance.
NOTE: Content here are my personal opinions, and not intended to represent any employer (past or present). “PROTIP:” here highlight information I haven’t seen elsewhere on the internet because it is hard-won, little-know but significant facts based on my personal research and experience.
My contributions under construction:
- A Bash shell file (gcpinfo.sh) that installs what’s needed for
- A multi-cloud Python program interacting across GCP, Azure, AWS
- A Terraform repo (gcp-tf) containing HCL to create GCP resources safely within enterprises
- A Google Sheet providing metadata about APIs collected over several Google websites and commands
Comparing IDS in Clouds
Here is a comparison of intrusion detection and/or prevention based on payload inspection within major clouds:
https://www.g2.com/categories/firewall-software#grid
The Config Server Firewall (CSF) application for Linux servers references Iptables. It secures servers against SYN flood, port scan, and brute force attacks by blocking IP addresses when wrong attempts are detected in the log files it monitors.
Azure Firewall with Sophos
Sophos Firewall in the Azure Marketplace: https://azuremarketplace.microsoft.com/en-us/marketplace/apps/sophos.sophos-xg-firewall-solution?tab=overview
Azure Web Application Firewall block malicious attacks to protect apps from common web-hacking techniques such as SQL injection, security vulnerabilities such as cross-site scripting (OWASP).
NOTE: “Azure Firewall with Threat Intelligence” alerts and denies traffic to and from known malicious IP addresses and domains. It does not do payload inspection.
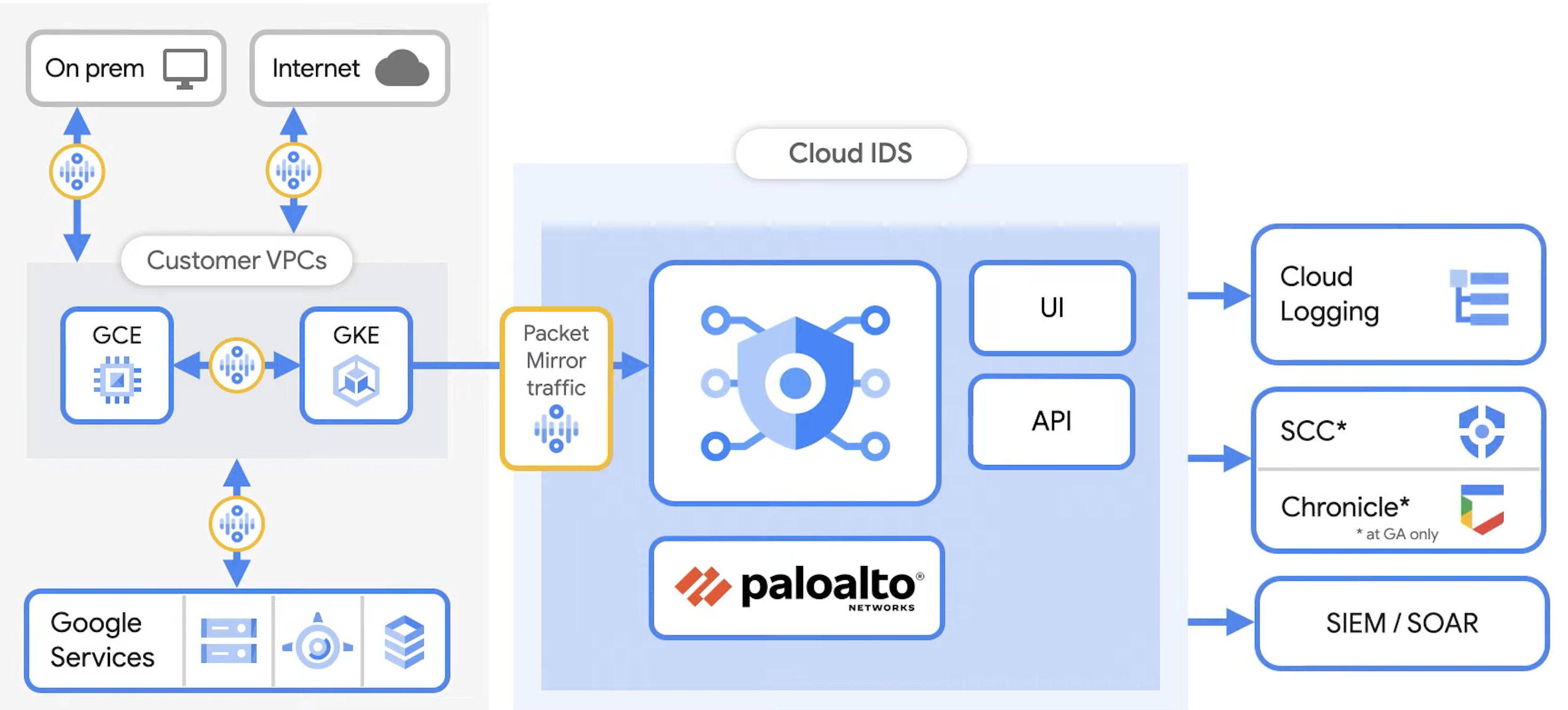
Google Cloud IDS with Palo Alto
-
Google’s Intrusion Detection System’s marketing page is at
https://cloud.google.com/intrusion-detection-system- https://cloud.google.com/blog/products/identity-security/announcing-general-availability-of-google-cloud-ids
CAUTION: Cloud IDS billing is $36 USD per-day for each Cloud IDS endpoint running, plus $0.07 per-GB of traffic inspected.
- https://cloud.google.com/blog/products/identity-security/announcing-general-availability-of-google-cloud-ids
-
Click “Go to console for
https://console.cloud.google.com/marketplace/product/google/ids.googleapis.comIndicators of intrusion attempts:
- Lateral movement
- malware
- spyware
- command-and-control attacks
Google’s Cloud IDS is network-based. It works by sending a copy (packet mirror) of ALL traffic out your VM Compute Engine instances to Palo Alto Networks to analyze (in real-time). That’s both Noth/South and East/West traffic.
The Compute Engine instance can be in or outside of Kubernetes, even on-prem.
Palo Alto
Palo Alto’s “Unit 42” of security specialists (a member of the Joint Cyber Alliance and other collaborations) make use of the “signatures” they have collected.
BTW: One testament to the prowess of Palo Alto’s Unit 42: In 2023, their analyst Yuval Avrahami earned the highest Bug Bountry from Google.
Unit 42’s 2022 Threat Trends Research Report concludes a 3X increase in attacks vs. prior to the uptick in remote work due to COVID-19. Remote code execution is the most exploited vulnerability type.
NOTE: I don’t see Palo Alto listed among Approved Scan Vendor (ASV) for PDF
- Create a completely separate test environment with its own Google Project ID
-
Instead of an operational custom application, install a example app with known issues that the IDS should catch, so people can experience the IDS working.
-
Under your Google project, enable Cloud IDS:
-
In your test Project, navigate to where git will create a folder.
-
Download my shell script based on the Google IDS tutorial
git clone https://github.com/wilsonmar/gcp-samples/master/bash/setup-ids.sh cd gcp-quickly chmod +x setup-ids.sh
- Edit file env file to customize values in the script:
- PROJECT_ID
- etc.
-
Run the script to setup Cloud IDS, Configure packet mirroring policies to an Endpoint resource:
./setup-ids.sh
-
Get the PROJECT_ID:
export PROJECT_ID=$(gcloud config get-value project | sed '2d')
Your active configuration is: [cloudshell-670]
- echo $PROJECT_ID
- gcloud services enable servicenetworking.googleapis.com –project=$PROJECT_ID
-
gcloud services enable ids.googleapis.com –project=$PROJECT_ID gcloud services enable logging.googleapis.com –project=$PROJECT_ID
Operation “…” finished successfully
-
gcloud compute networks create cloud-ids –subnet-mode=custom
-
Google achieves Private Service Access to Palo Alto using VPC Peering via Private Connection. That means traffic is not sent through the public internet.
-
Create a Cloud IDS endpoint zonal resource that can inspect traffic from any zone in its region. Each IDS endpoint receives mirrored traffic and performs threat detection analysis.
-
Create a virtual attack machine.
- Create a Cloud IDS packet mirroring policy.
View in the Console GUI
-
-
Navigation menu, click MORE PRODUCTS, Network Security > Cloud IDS.
https://console.cloud.google.com/net-security/ids
https://console.cloud.google.com/net-security/ids/list?authuser=1&project=???&initialSelectedIntervalIndex=0
-
Click the Threats tab.
-
Locate a vulnerability (such as “Bash Remote Code Execution Vulnerability”) to click More, and then select View threat logs.
-
In the new Cloud Logging tab opens that displays the same details, send the logs to Cloud Storage, Chronicle, or other SIEM/SOAR system.
TODO: Also create custom workflows to take remediation action based on alerts, like creating a Cloud Function that triggers on an alert and creating or updating a firewall rule to block the IP address, or creating or updating a Google Cloud Armor policy.
https://www.cloudskillsboost.google/catalog_lab/4381 Detecting Attacks with Cloud IDS then Block with Cortex XSOAR
https://www.cloudskillsboost.google/focuses/27161?parent=catalogCloud Network Security with Cloud IDS and VM-Series .
-
To limit the “blast radius” of administrator credentials being compromised, invoke separation of duties by allowing only managers to perform methods “DeleteEndpoints” and “DeleteOperation”.
PROTIP: Establish a procedure for requesting and processing deletion with a way to track speediness trends.
-
Estimate maximum usage per day/week/month as the basis for setup Quota alerts.
-
Simulate attack traffic from a virtual machine by injecting fake security conditions that trigger alerts:
TODO: Examples of alerts from Palo Alto recognizing Indicators of Compromise.
Eicar File Detected
EICAR is an acronym for “European Institute for Computer Antivirus Research”. Along with the Computer Antivirus Research Organization, EICAR created the “Eicar file” for testing anti-virus software features without resorting to installing harmful real malware. The Eicar file should be recognized among other signatures of virus infection, even when stored in a compressed file.
The EICAR file is executable. When run, it simply prints out “EICAR-STANDARD-ANTIVIRUS-TEST-FILE!”.
Like some real malware, it makes use of self-modifying code.
The “Eicar file” is referenced by Testing Protocol Standards developed by the Antimalware Testing Standards Organization of security vendors and expert test labs from around the world.
AMTSO Feature Settings Checks.
Not all virus scanners recognize it, though.
-
Define and configure automated escalations if responses are not timely.
-
View threat details in the Cloud console and Cloud Logging.
Review metrics collected:
-
Overall latency
- Traffic by response code
- Traffic by API method
-
Traffic by credential
- Latency by response code (median)
- Latency by API method (median)
-
Latency by credential (median)
- Errors by API method
- Errors by credential
-
-
Verify that indicators of compromise result in alerts sent to the SIEM system accessed by the SOC (Security Operations Center).
-
Practice Incident Management response during chaos engineering exercises.
-
Management Review automated escalations if responses are not timely.
-
Schedule a review every month.
PROTIP: Confirm the ability to automatically save previous versions of configurations deleted. Verify that they can be retrieved.
PROTIP: Review usage levels and revise quota limits accordingly.
More on cloud
This is one of a series on cloud computing:
- Dockerize apps
- Kubernetes container engine
- Hashicorp Vault and Consul for keeping secrets
- Hashicorp Terraform
- Ansible server configuration automation
- Serverless software app development
- Terraform (declarative IaC)
- Build load-balanced servers in AWS EC2
- AWS On-boarding (CLI install)
- AWS MacOS instances in the cloud)
- AWS Certifications
- AWS IAM admin.
- AWS Data Tools
- AWS Security
- AWS VPC Networking
- AWS X-Ray tracing
- AWS server deployment options
- AWS Lambda
- AWS Cloud Formation/cloud-formation/)
- AWS Lightsail
- AWS Deeplens AI
- AWS Load Balanced Servers using CloudFormation
-
Microtrader (sample microservices CI/CD to production Docker within AWS)
-
AWS Data Processing: Databases, Big Data, Data Warehouse, Data Lakehouse
- Google Cloud Platform
-
Bash Windows using Microsoft’s WSL (Windows Subsystem for Linux)
- Azure cloud introduction
- Azure Cloud Onramp (Subscriptions, Portal GUI, CLI)
- Azure Cloud Powershell
- PowerShell GitHub API programming
- PowerShell DSC (Desired State Configuration)
- PowerShell Modules
- Microsoft AI in Azure cloud
- Azure cloud DevOps
- Azure Networking
- Azure Storage
- Azure Compute
- Dynatrace cloud monitoring
- Digital Ocean
- Cloud Foundry