Filter out annoying ads and malware sites on your home network using PiHole.
Overview
- DNS: Public and local (PiHole)
- Blocks needed
- Firewall Options
- Static IP on router
- AdGuard on Raspberry Pi
- PiHole on Raspberry Pi
- Get Raspberry Pi hardware
- Install PiHole on macOS
- Set Pi-hole Admin Password
- Log into the Pi-hole
- Pi-hole Dashboard and Menus
- Add Pi-hole Block Lists
- More Pi-hole Menu Settings
- Pi-hole Settings
- Configure DNS server
- Add blocklist from Firebog
- Temporarily Disable Pi-hole 23:45
- Configure other devices to use Pi-hole as DNS
- Audit log
- Backup
- Install Unbound DNS route proxy
- Test Pi-hole Ad Blocking
- Docker
- NAS drive on Raspberry Pi
- Chron jobs
- More
- References
- More on DevOps
- More on Security
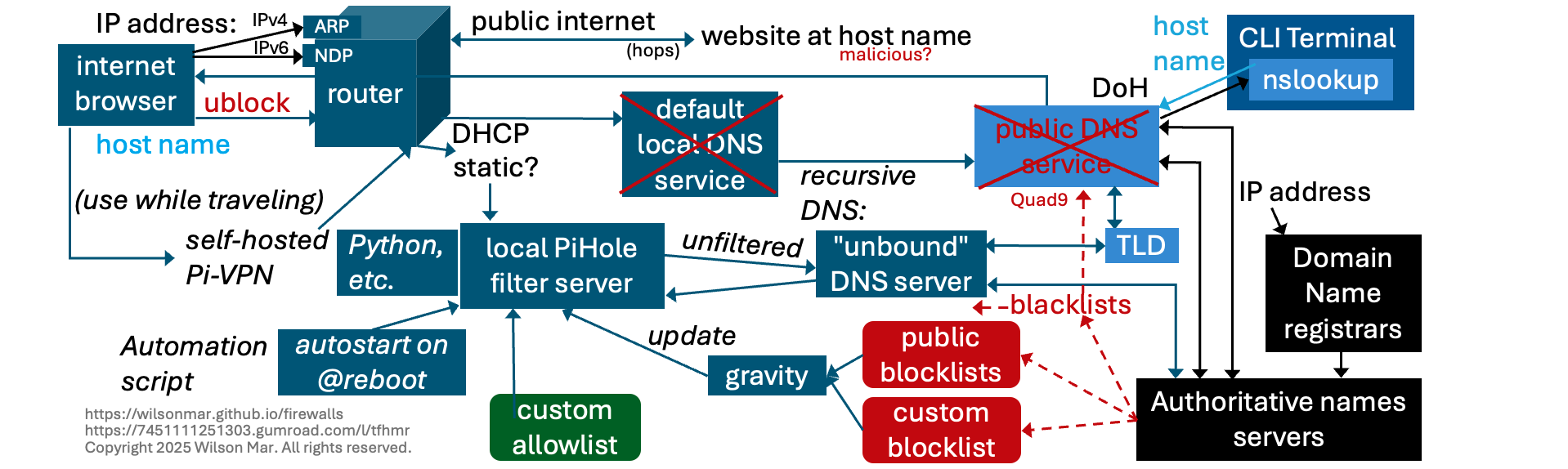
DNS: Public and local (PiHole)
- When on a CLI (Command Line Interface) Terminal,
- a nslookup command to lookup a
- host name,
- if your operating system is configured for it, to a Public DNS server which
- go through a Recursive DNS workflow that begins with a query to
- get the address of the service handling the TLD (Top-level Domain) at the end of the host name, such as “.com”, etc.
- That DNS server queries the TLD service which references its
- Authorative names servers which return the IP address for the domain.
-
The website for domain name owners to register domain names and associate IP addresses is maintained by Domain Name System registrars (such as GoDaddy).
- When an internet browser such as Google Chrome or Firefox,
- you give an IP address,
- the request goes through your local router.
- Routers that use IPv4 send ARP (Address Resolution Protocol) requests and routers using IPv6 send NDP (Neighbor Discovery Protocol) requests through
- hops through the public internet (Data Link layer) until
-
the website at the IP address is reached. If it’s listening, you get sent its response.
- In today’s hostile world, we are concerned whether websites we visit have become malicious.
- Public DNS servers are suspect because they are run by private interests. So they have been caught selling logs of your traffic history, even if you say they don’t.
- The Quad9 DNS service is run by Scotland Yard and other law enforcement.
- They maintain their own blocklists of domain names which they don’t serve to their users. So by configuring Quad9 as your local DNS, you get some protection from known criminal websites.
- But many don’t think that is enough protection because public blocklists collected by others contain millions of websites deemed malicious or serve annoying ads.
-
It is recommended that you maintain your own private blocklist for parental control.
Here is how you do that.
- An add-in such as ublock (by Raymond Hill) can be installed on Firefox browsers to block ads based on its own private blocklist. But each browser and app has its own add-in.
- So we want protection on all apps looking up all host name lookups.
- We need to get away from the typical default configuration of a local DNS server using sketchy public DNS service.
- Instead of DHCP, we change the configuration to use
- static IP address to the local server you setup, called PiHole to filter traffic according to
- updates of blocklists by the “gravity” utility.
-
A private allowlist is also maintained.
-
Traffic that have not been filtered out are passed to a local DNS service called “unbound” instead of either the default sketchy public DNS services to do the TLD and Authorative lookups.
- That service needs to be invoked automatically upon reboot, and be controlled by a
-
automation CLI script that installs Python and other services such as DoH (DNS over HTTPS) protocol for better privacy by encrypting communications.
- To use your custom private blocklists while traveling, install a
- self-hosted VPN.
Blocks needed
Those with a connection to the public internet need to:
- Block annoying ads
- Block malicious websites
- Block ports
See my notes on DNS
The Pi-Hole server provides a recursive DNS server called “UnBound”.
VIDEO: Unifi Ad Blocker.
blocking ads makes for quicker browsing.
ECS (Extended Client Subnet) defines a mechanism for recursive solvers to send partial client IP address information to authoritative DNS name servers. ECS may result in reduced privacy when it is used by CDNs (Content Delivery Networks) and latency-sensitive services to give geo-located responses when responding to name lookups coming through public DNS resolvers. However, SNI headers also send such information.
Firewall Options
Large businesses install firewalls in their corporate networks such as from Palo Alto or Cisco.
Homes and small businesses use “consumer-grade” firewalls from brands such as Linksys, Netgear, or Draytek.
-
VIDEO: OPNSense
-
VIDEO: UniFi Dream Machine Pro (UDM-Pro) by Crosstalk Solutions
-
Firewalla is a consumer-grade firewall that is also a router. It comes assembled with software installed. Firewalla has a Purple and Gold editions. The Gold edition adds Intrusion Detection.
If you have the time and geeky inclinations, the least-cost and most customizable option is to buy a Raspberry Pi micro computer and install and configure utility software Pi-Hole.
-
Technitium DNS Server
-
AdGuard uniquely can be scheduled for a specific block of time each day with parental blocking. AdGuard can use DNSSEC (DNS over HTTPS). AdGuard can also be configured with wildcard specification. AdGuard can enable encryption using a certificate pulled from a CA every 3 months. VIDEO But assumes less advanced configurations than PiHole.
Which is better? PiHole vs AdGuard Home?
- https://www.youtube.com/watch?v=c3XMAz–_Us by Hardwood
- https://www.youtube.com/watch?v=nV5dKpGMGx4 by Tobi Teaches
- https://www.youtube.com/watch?v=O15RD_gPz-s by Barmine
PiHole
Static IP on router
To make this work, you first need to get into your internet router to set a static (fixed) IP address instead of using one dynamically assigned by DHCP.
I gave a fixed private IP on my network where I’m redirecting all my DNS queries.
AdGuard on Raspberry Pi
with OpenWRT
Firebog List Generator
Portainers
PiHole on Raspberry Pi
https://www.wikiwand.com/en/Pi-hole
https://en.wikipedia.org/wiki/DNS_Sinkhole protects devices on a subnet from unwanted content, without installing any client-side software.
The Pi-hole® impliments a DNS sinkhole https://pi-hole.net/
PiHot optionally functions as a DHCP server, ensuring all your devices are protected automatically
over both IPv4 and IPv6
- https://crosstalksolutions.com/raspberry-pi-4-boot-with-usb
- https://www.youtube.com/watch?v=xtMFcVx3cHU by TechHut
- https://www.youtube.com/watch?v=roYduABVjo8 by CoreElectronics
Get Raspberry Pi hardware
If you are having difficulty getting a Raspberry Pi:
- Clones of Raspberry Pi
- RPilocator.com notifies you when one comes into stock.
- VIDEO: https://www.crosstalksolutions.com/the-worlds-greatest-pi-hole-and-unbound-tutorial-2023/ has a
Alternately, you can run Pi-hole within a Docker container.
YouTube Videos:
by Crosstalk Solutions:
- VIDEO: “Raspberry Pi 4 Getting Started</a> by Crosstalk Solutions
-
VIDEO: “World’s Greatest Pi-hole Tutorial - Easy Raspberry Pi Project!”
- VIDEO: “How to Block Ads Using a Pi-Hole With A Raspberry Pi” by Micro Center
- VIDEO: “The Ultimate Pi-Hole Installation Guide for 2025!” by Mackey Tech IT Solutions
-
VIDEO: “Pi-hole Setup on Raspberry Pi Zero W Step-by-Step Guide” by CyberMaxLab -
VIDEO: “How to install Pi-hole and PiVPN on a Raspberry Pi Must Have for Home Lab” by Barmine Tech - VIDEO: “How to Install Pi-Hole on Raspberry Pi” by Vincent Humble
- VIDEO:
- VIDEO: “Pi-hole Made EASY - A Complete Tutorial” by Tech Craft
Install PiHole on macOS
https://docs.pi-hole.net/main/basic-install/
curl -sSL https://install.pi-hole.net | bash
- See my articles:
-
Navigate to a folder where you want the new repo downloaded.
-
Deploy the software directly to a supported operating system via our automated installer:
git clone --depth 1 https://github.com/pi-hole/pi-hole.git Pi-hole cd "Pi-hole/automated install/" sudo bash basic-install.sh
-
Type your laptop’s OS password requested by the sudo command. The Pi logo should appear.
[✓] Root user check .;;,. .ccccc:,. :cccclll:. ..,, :ccccclll. ;ooodc 'ccll:;ll .oooodc .;cll.;;looo:. .. ','. .',,,,,,'. .',,,,,,,,,,. .',,,,,,,,,,,,.... ....''',,,,,,,'....... ......... .... ......... .......... .......... .......... .......... ......... .... ......... ........,,,,,,,'...... ....',,,,,,,,,,,,. .',,,,,,,,,'. .',,,,,,'. ..'''.If you see this, verify you have a working connection to the Pi.
[i] SELinux not detected [✗] No supported package manager found
-
Block ads everywhere, even on the go. By pairing your Pi-hole with a VPN, you can have ad blocking on your cellular devices, helping with limited bandwidth data plans.
https://docs.pi-hole.net/guides/vpn/overview
Set Pi-hole Admin Password
Log into the Pi-hole
Pi-hole Dashboard and Menus
Add Pi-hole Block Lists
-
Configure your router’s DHCP options to force clients to use Pi-hole as their DNS server, or manually configure each device to use the Pi-hole as their DNS server.
https://docs.pi-hole.net/main/post-install
More Pi-hole Menu Settings
Pi-hole Settings
-
Set a static IP address within your subnet for the PiHole. 8:58
sudo nano -w /etc/dhcpcd.conf
Un-comment under # Example static IP configuration and specify your subnet:
interface eth0 static ip_address=192.168.200.52/24 static routers=192.168.200.1 static domain_name_servers=192.168.200.1 1.1.1.1
sudo reboot
-
On the new IP address:
Configure DNS server
Some internet service providers (ISPs) return ads instead of 404.
TODO: Don’t have to use Unbound.
The list of supported DNS servers and their primary and secondary IP addresses (V4 and V6) are defined in the .sh script:
DNS_SERVERS=$( cat <<EOM Google (ECS, DNSSEC);8.8.8.8;8.8.4.4;2001:4860:4860:0:0:0:0:8888;2001:4860:4860:0:0:0:0:8844 OpenDNS (ECS, DNSSEC);208.67.222.222;208.67.220.220;2620:119:35::35;2620:119:53::53 Level3;4.2.2.1;4.2.2.2;; Comodo;8.26.56.26;8.20.247.20;; Quad9 (filtered, DNSSEC);9.9.9.9;149.112.112.112;2620:fe::fe;2620:fe::9 Quad9 (unfiltered, no DNSSEC);9.9.9.10;149.112.112.10;2620:fe::10;2620:fe::fe:10 Quad9 (filtered, ECS, DNSSEC);9.9.9.11;149.112.112.11;2620:fe::11;2620:fe::fe:11 Cloudflare (DNSSEC);1.1.1.1;1.0.0.1;2606:4700:4700::1111;2606:4700:4700::1001 EOM )1.1.1.3 & 1.0.0.3 blocks phising/malware/adult content filtering.
8.8.8.8 from Google was rated as the quickest, probably because it doesn’t block as comprehensively.
Add blocklist from Firebog
-
Into Pi-Hole’s Adlist Group Management, add URLs of sites that Firebog knows to be suspicious, advertising, tracking & telemetry, malicious, etc.
-
Click “Update Gravity”.
Temporarily Disable Pi-hole 23:45
-
Create a shell file to call to obtain password cache:
cat /etc/pihole/setupVars.conf | grep WEBPASSWORD
-
Bookmark this URL on your browser or Stream Deck to temporarily disable Pi-Hole by authenticating with the hashed value of WEBPASSWORD.
http://192.168.200.52/admin/api.php?disable=300&auth=PWHASH
for 300 seconds
Configure other devices to use Pi-hole as DNS
- In Settings, Interface settings, uncheck default “Allow only local requests”.
-
Check “Respond only on interface eth0”.
-
Instead of changing each device (laptop), set the DNS to the Pi-Hole DNS, set the DHCP: DNS 1 and DNS 2.
Audit log
-
Click the “Audit Log” menu item.
Backup
- In Tools, click “Backup”.
- Copy the backed up file to a USB drive and/or cloud.
-
If you’re running 2 Pi-Holes, install the backup onto the 2nd Pi-Hole. Sync using:
https://github.com/vmstan/gravity-sync
Install Unbound DNS route proxy
-
Install Unbound service to make DNS queries anonymously:
sudo apt install unbound -y
-
Download the text
??? pi-hole.conf
-
Edit wall of text:
sudo nano -w /etc/unbound/unbound.conf.d/pi-hole.conf
-
Start Unbound service:
sudo service unbound start
-
View Unbound service status (active?):
sudo service unbound status
-
Test DNS lookup:
dig crosstalksolutions.com @127.0.0.1 -p 5335
-
30:36 Setup firewall rules to ignore DNS queries to the DNS set on individual devices.
Test Pi-hole Ad Blocking
- Test Ad-Blocking
Docker
curl -sSL https://get.docker.com | sh
-
Add user pi to docker group:
sudo usermod -aG docker pi
-
Setup portainer.io to manage Docker containers on default port 9000:
sudo docker run --restart always -d -p 9000:9000 \ -v /var/run/docker.sock:/var/run/docker.sock \ -v portainer_data:/data portainer/portainer-ce:linux-arm
NAS drive on Raspberry Pi
https://www.youtube.com/watch?v=gyMpI8csWis
Chron jobs
Update the Pi-hole
Run a chron (crontab) job to Once a week or month to apply updates (if one becomes available):
-
Edit in /etc/cron.d/pihole
30 2 * * 1 root /usr/bin/curl -sSl https://raw.githubusercontent.com/mmotti/pihole-regex/master/install.py | /usr/bin/python3 >> /var/log/piholeupdate 2>&1 30 2 * * 1 root cd /usr/local/src/whitelist/scripts && git pull&& ./whitelist.sh >> /var/log/piholeupdate 2>&1
Do regular speedtests
-
Every hour run:
VIDEO: openspeedtest.com server run within a Docker image downloaded.
sudo docker run --restart=unless-stopped \ --name=openspeedtest -d -p 80:8080 openspeedtest/latest
Change the port to something other than 8080 if your prefer.
-
Display
https://github.com/Brandawg93/Pi-Hole-Monitoring
-
Run on browser at URL http://192.168.200.122
Record to a file.
Instead of a chip, get an SSD drive.
-
View analysis: Are evenings more overloaded?
More
VIDEO: “Is adding 3 MILLION domains to your Pi-Hole Block List a good thing?” by Techno Tim
References
https://docs.pi-hole.net/
https://www.reddit.com/r/pihole/
https://www.youtube.com/watch?v=jlHWnKVpygw
More on DevOps
This is one of a series on DevOps:
- DevOps_2.0
- ci-cd (Continuous Integration and Continuous Delivery)
- User Stories for DevOps
- Git and GitHub vs File Archival
- Git Commands and Statuses
- Git Commit, Tag, Push
- Git Utilities
- Data Security GitHub
- GitHub API
- Choices for DevOps Technologies
- Pulumi Infrastructure as Code (IaC)
- Java DevOps Workflow
- AWS DevOps (CodeCommit, CodePipeline, CodeDeploy)
- AWS server deployment options
- Cloud services comparisons (across vendors)
- Cloud regions (across vendors)
- Azure Cloud Onramp (Subscriptions, Portal GUI, CLI)
- Azure Certifications
- Azure Cloud Powershell
- Bash Windows using Microsoft’s WSL (Windows Subsystem for Linux)
- Azure Networking
- Azure Storage
- Azure Compute
- Digital Ocean
- Packer automation to build Vagrant images
- Terraform multi-cloud provisioning automation
-
Hashicorp Vault and Consul to generate and hold secrets
- Powershell Ecosystem
- Powershell on MacOS
- Jenkins Server Setup
- Jenkins Plug-ins
- Jenkins Freestyle jobs
- Docker (Glossary, Ecosystem, Certification)
- Make Makefile for Docker
- Docker Setup and run Bash shell script
- Bash coding
- Docker Setup
- Dockerize apps
- Ansible
- Kubernetes Operators
- Threat Modeling
- API Management Microsoft
- Scenarios for load
- Chaos Engineering
More on Security
This is one of a series on Security:
- Security actions for teamwork and SLSA
- Code Signing on macOS
- Git Signing
- GitHub Data Security
- Azure Security-focus Cloud Onramp
- AWS Onboarding
- AWS Security (certification exam)
- AWS IAM (Identity and Access Management)
- SIEM (Security Information and Event Management)
- Intrusion Detection Systems (Goolge/Palo Alto)
- SOC2
- FedRAMP
-
CAIQ (Consensus Assessment Initiative Questionnaire) by cloud vendors
- AKeyless cloud vault
- Hashicorp Vault
- Hashicorp Terraform
- SonarQube
- WebGoat known insecure PHP app and vulnerability scanners
- Security certifications
- Quantum Supremecy can break encryption in minutes
- Pen Testing
- Threat Modeling
- WebGoat (deliberately insecure Java app)